
Latest Dark Web Sales: Exploits, 0-Days, Financial & Government Data Leaks, DarkVR Service
The SOCRadar Dark Web Team’s recent discoveries reveal a range of concerning cyber threats. These include a high-value 0-day exploit aimed at Microsoft Office, a significant 20 GB email breach from the Mexico City government, and a $15,000 0-day exploit designed for a popular WordPress plugin. Reports also indicate a new WinRAR exploit circulating online.
Furthermore, there’s the emergence of the DarkVR IP stresser service and the introduction of the Bank and Business Fullz Service, providing comprehensive personal and financial data access.
Receive a Free Dark Web Report for Your Organization:
0-Day Vulnerability Sale is Detected
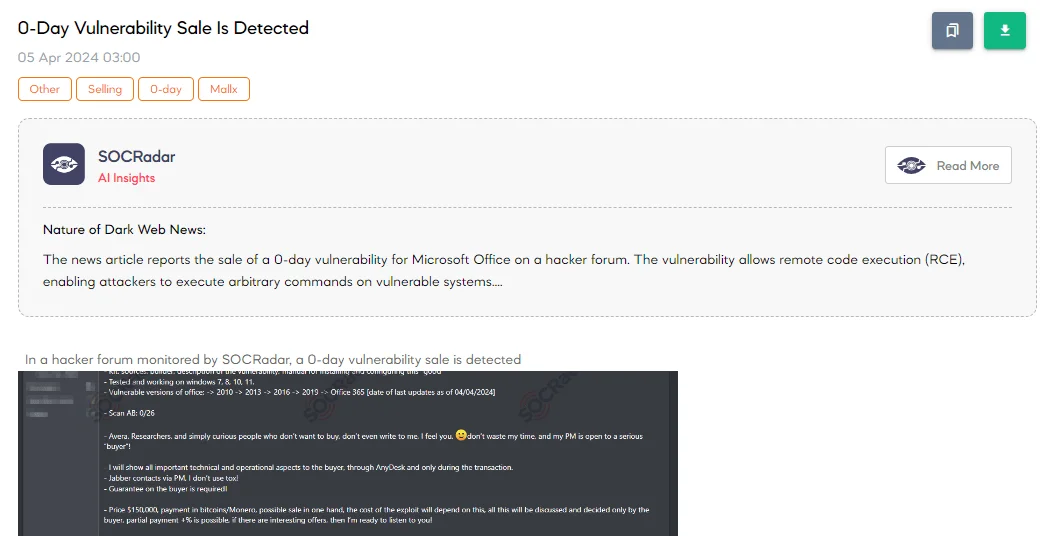
0-Day Vulnerability Sale is Detected
The SOCRadar Dark Web Team has uncovered a concerning post on a hacker forum where a threat actor is advertising the sale of a 0-day vulnerability targeting Microsoft Office, enabling Remote Code Execution (RCE). This vulnerability allows attackers to execute commands and various file types on victim machines. The exploit package, priced at $150,000 payable in Bitcoin or Monero, includes source code, a builder tool, documentation, and is claimed to be effective on Windows 7 to 11 and Office versions from 2010 to Office 365.
Email Data of Government of Mexico City are Leaked
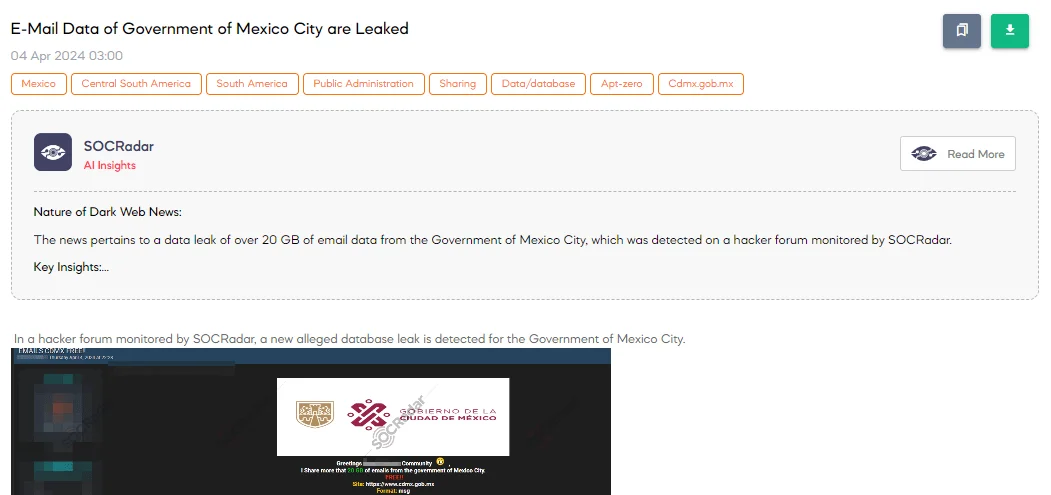
Email Data of Government of Mexico City are Leaked
The SOCRadar Dark Web Team has detected a claim on a hacker forum about a leak involving over 20 GB of email data from the government of Mexico City. The data, available for free and in “.msg” format, indicates a significant security breach that could expose sensitive government communications.
0-Day Exploit for a WordPress Plugin is on Sale
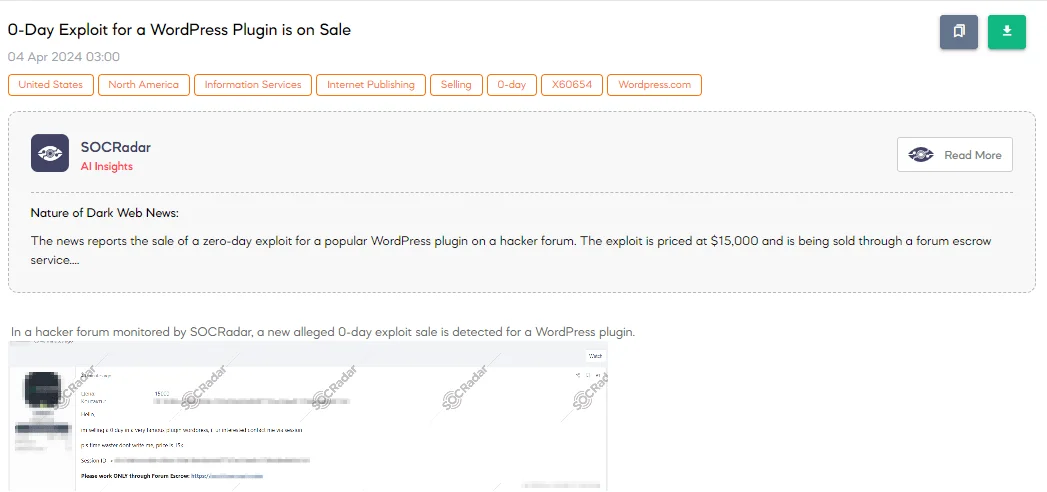
0-Day Exploit for a WordPress Plugin is on Sale
The SOCRadar Dark Web Team has detected a post on a hacker forum where a threat actor is advertising a new alleged 0-day exploit for sale, targeting a very popular WordPress plugin. The actor has set the price for this exploit at $15,000, indicating the seriousness and potentially widespread impact of the vulnerability.
Exploit for WinRAR is Shared
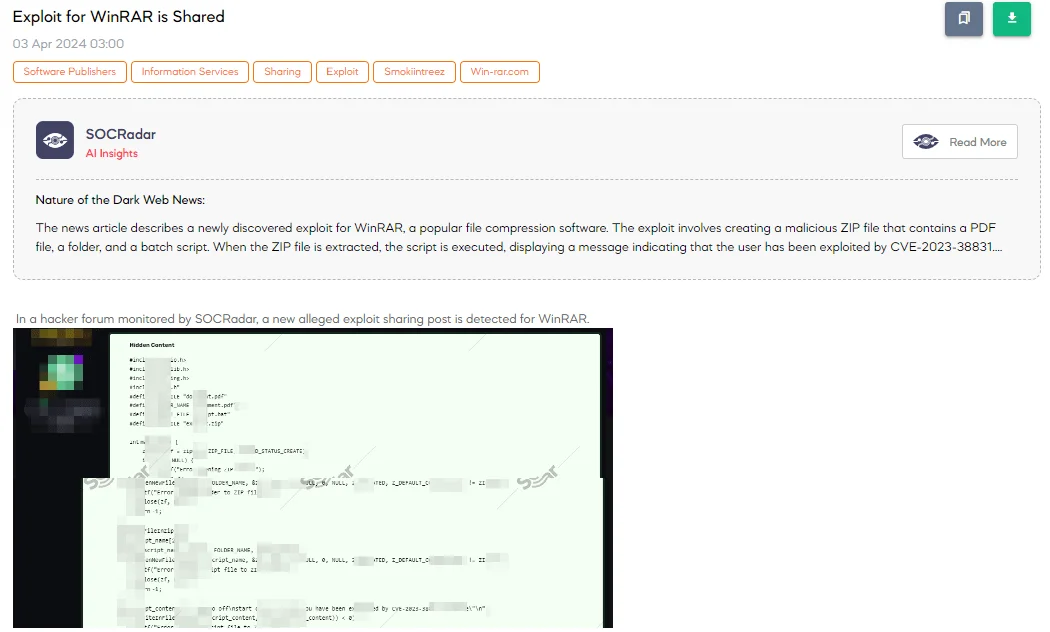
Exploit for WinRAR is Shared
The SOCRadar Dark Web Team detected a post on a hacker forum detailing a new exploit targeting WinRAR, a popular file compression and archive utility. This exploit demonstrates a sophisticated method for attackers to potentially execute arbitrary code on a victim’s computer by manipulating the way WinRAR processes ZIP files.
This exploit’s description includes using the C programming language to create the ZIP archive, with specific calls to the “zip.h” library for manipulating ZIP files. The code aims to demonstrate how an attacker could embed a harmless-looking PDF file and a malicious batch script (script.bat) in a single ZIP file (exploit.zip). When the archive is opened, and the content is interacted with by an unsuspecting user, the batch script could be executed automatically due to the vulnerability in WinRAR, identified here as CVE-2023-38831.
DarkVR IP Stresser Service is on Sale
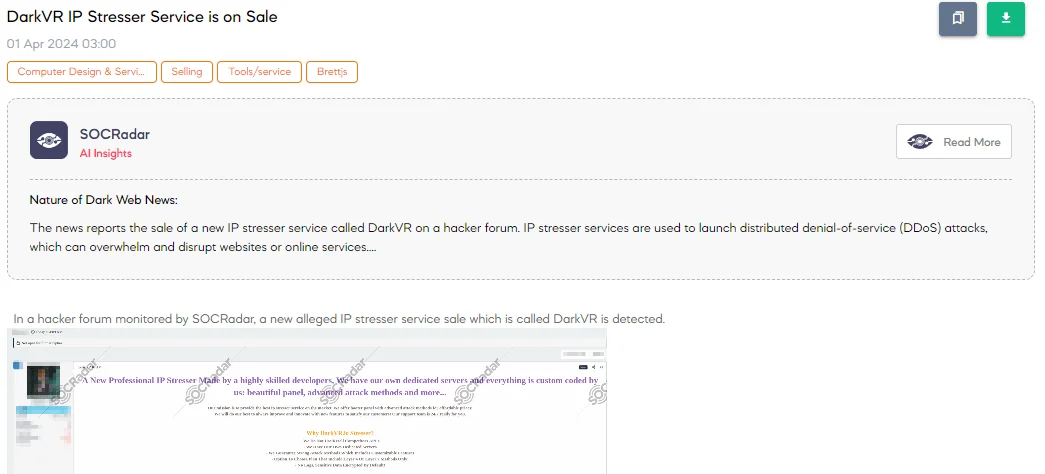
DarkVR IP Stresser Service is on Sale
The SOCRadar Dark Web Team discovered a hacker forum post announcing DarkVR, a newly launched IP stresser service. According to the threat actor, this service is designed by expert developers and features a platform that is entirely custom-coded, including dedicated servers and sophisticated attack methods.
The service distinguishes itself with claims of having powerful, customizable attack options, guaranteeing privacy with a strict no-logs policy, and ensuring all sensitive data is encrypted by default. Potential customers are offered a variety of service plans, tailored to either Layer 4 or Layer 7 attack methods, backed by round-the-clock support.
Bank and Business Fullz Service is Detected
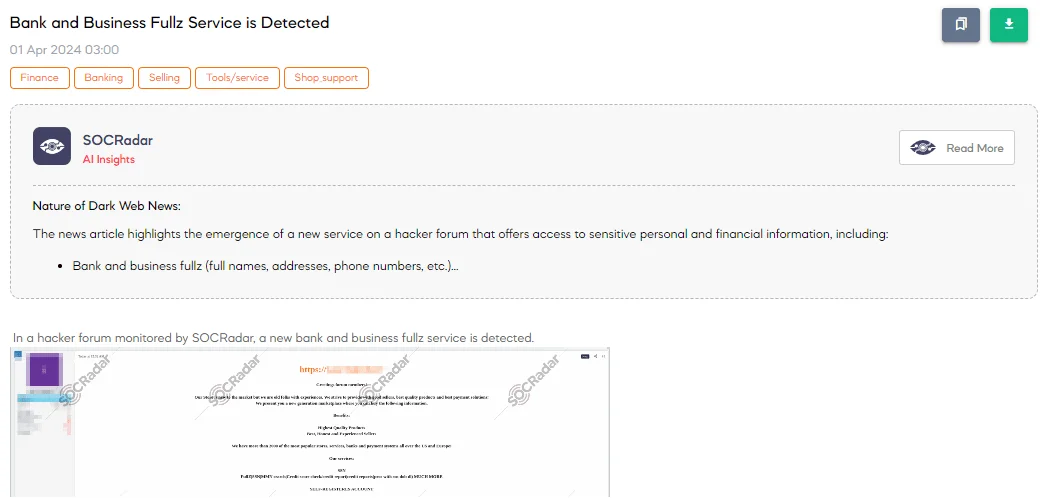
Bank and Business Fullz Service is Detected
The SOCRadar Dark Web Team detected a post on a hacker forum about a new service offering comprehensive personal and financial data, referred to as “fullz.” This service claims to include Social Security numbers, full personal details, credit scores, and more.
It also offers registered bank accounts from major US banks and mobile banking services with the option to send debit cards, cryptocurrency accounts, and even real documents like driver’s licenses and passports. The post boasts about having access to over 2,000 popular stores, services, banks, and payment systems in the US and Europe, emphasizing daily updates and around-the-clock customer support.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































