
LAX and Generali Database Leaks, US Credit Card Sales, Unauthorized Accesses, and Recruitment Posts
Discover the latest revelations from the SOCRadar Dark Web Team, exposing a myriad of security breaches. From leaked databases of prestigious organizations like Los Angeles International Airport and the Generali Group to the sale of unauthorized access to critical systems, including the Indian Election Duty Management System and a United Kingdom holding company, the threat landscape intensifies. Additionally, discover the threats of the latest credit card sales, POS machine access, and recruitment for clandestine activities.
Receive a Free Dark Web Report for Your Organization:
Database of Los Angeles International Airport (LAX) is Leaked
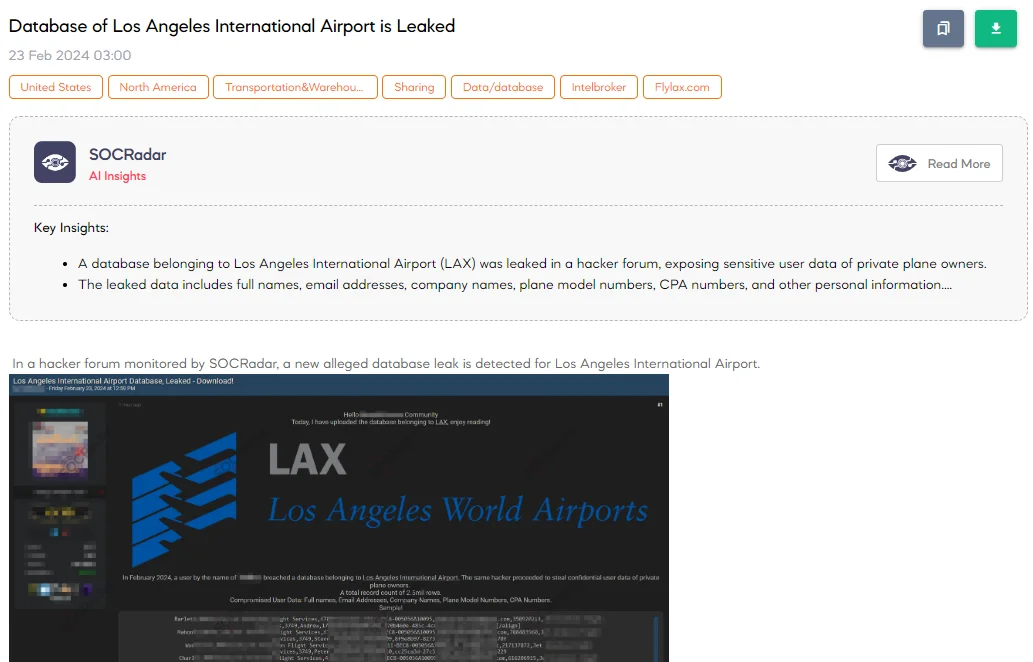
On February 23, a SOCRadar Dark Web Analyst detected a post on a dark web forum, shared by a prominent member of the CyberNiggers gang, claiming to have leaked a database allegedly belonging to Los Angeles International Airport (LAX). According to the threat actor, the breach occurred in February 2024, perpetrated by another threat actor resulting in the theft of confidential user data belonging to private plane owners. The compromised database reportedly contains 2.5 million rows of records, including sensitive information such as full names, email addresses, company names, plane model numbers, and CPA (Certified Public Accountant) numbers.
Database of Generali Group is Leaked
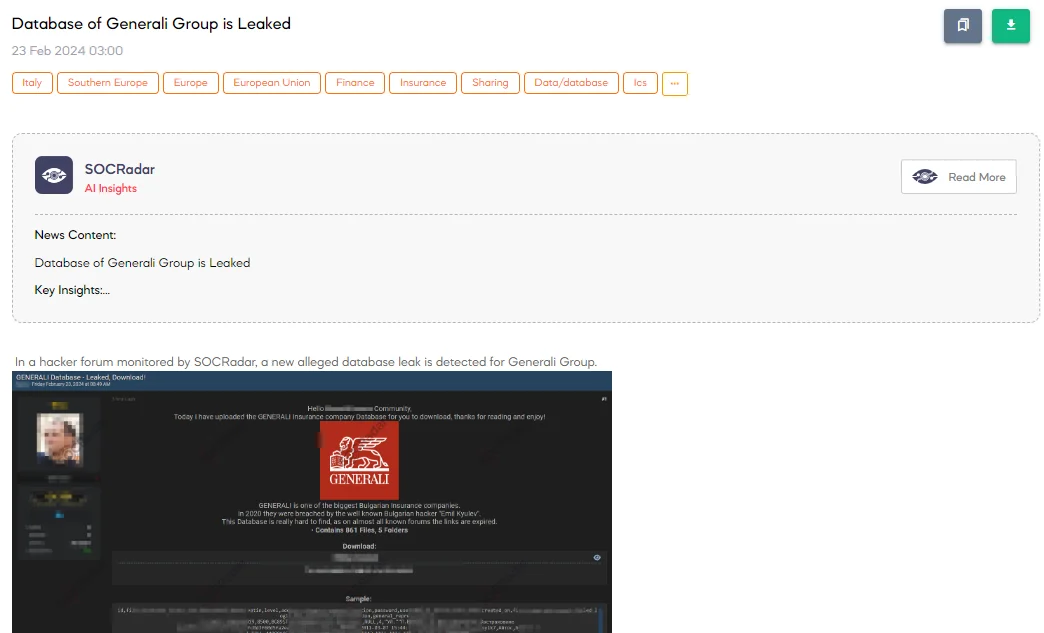
The SOCRadar Dark Web Team has identified a post on a hacker forum indicating the alleged leak of a database belonging to the Generali Group, an insurance company. The threat actor claims to have uploaded the database, citing a breach that occurred in 2020 by a well-known Bulgarian hacker. According to the post, this particular database is challenging to find, as links to it on other forums have expired.
The leaked database allegedly contains 861 files organized into 5 folders, with fields including IDs, file IDs, parent IDs, UCC (Uniform Commercial Code), ZIP codes, IBANs (International Bank Account Numbers), email addresses, phone numbers, VAT identification numbers, address details, company information, password and username data, activation statuses, last names, creation dates, first names, patronymic names, failed login attempts, new passwords, and representation details.
1.6K Credit Cards Belonging to the United States Are on Sale
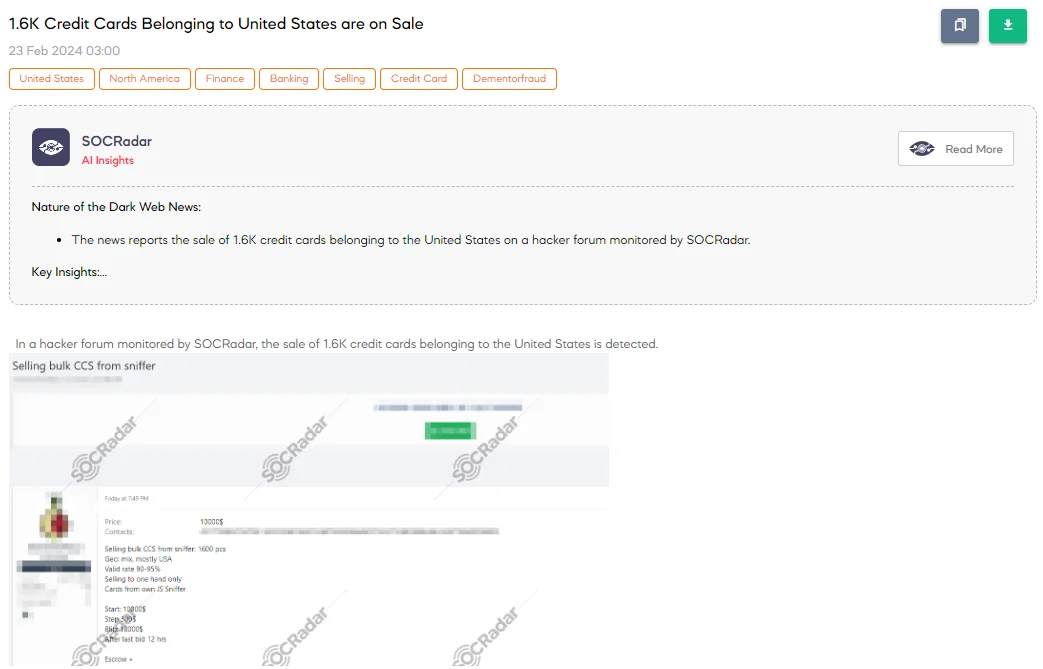
The SOCRadar Dark Web Team has detected a post on a hacker forum revealing the sale of 1,600 credit cards purportedly belonging to the United States. The threat actor behind the post claims to be selling these credit cards in bulk, with a price tag of $10,000. The cards are said to have been obtained using a JavaScript (JS) sniffer, with a valid rate of 90-95%. The seller specifies that they will only sell to one buyer, and the bidding starts at $10,000 with increments of $500. There is also an option for a Blitz (instant buy) purchase at $18,000. Additionally, the seller mentions that Escrow services will be utilized for secure transaction processing.
Unauthorized Access Sale is Detected for Indian Election Duty Management System
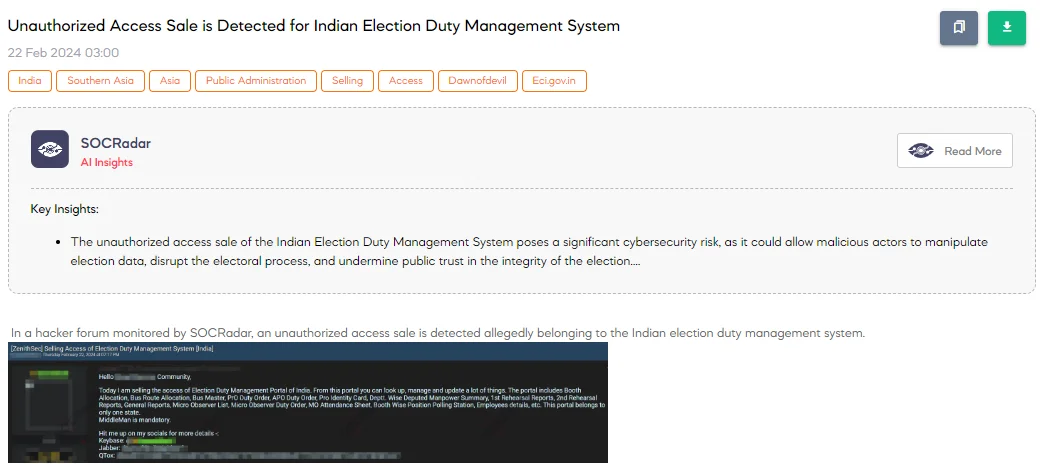
On February 22, a SOCRadar researcher uncovered a concerning post on a hacker forum, where a threat actor was claiming to sell unauthorized access allegedly belonging to the Indian Election Duty Management System. According to the post, the seller offers access to a portal that allows users to look up, manage, and update various aspects of election duties. The portal reportedly includes booth allocation, bus route allocation, bus master, duty orders for Presiding Officers (PrO) and Assistant Presiding Officers (APO), identity card generation for election officials, a department-wise summary of deployed manpower, first rehearsal reports, and more.
Unauthorized Domain Admin Access Sale is Detected for a United Kingdom Holding
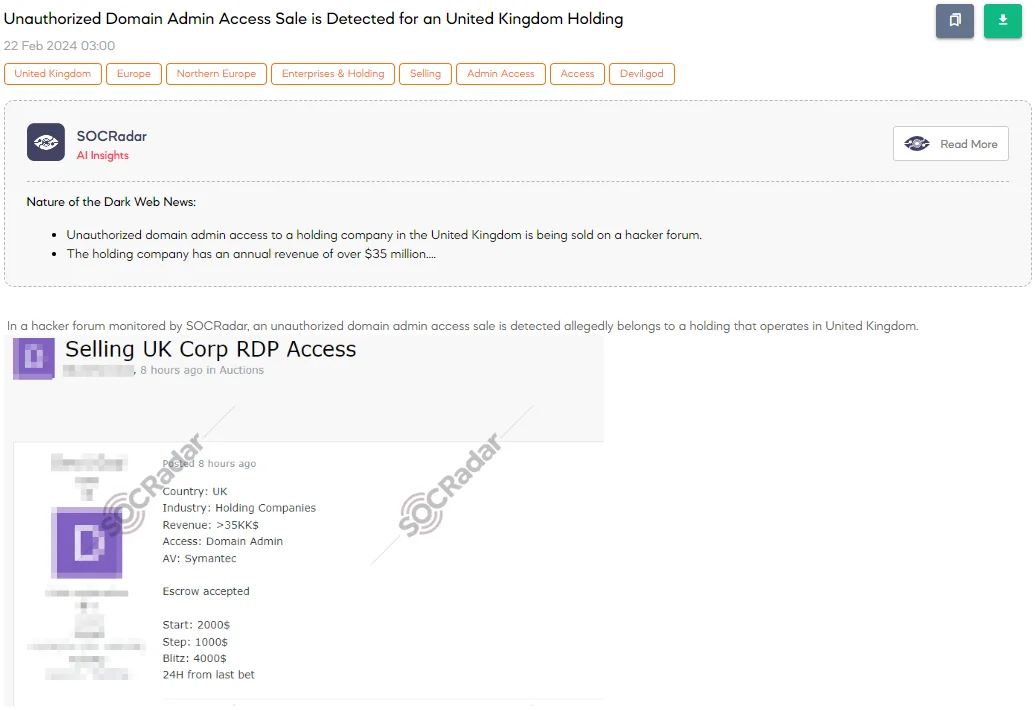
The SOCRadar Dark Web Team has uncovered a post on a hacker forum where a threat actor is advertising the sale of unauthorized domain admin access allegedly belonging to a holding company operating in the United Kingdom. According to the post, the company’s revenue is approximately $45 million. The advertised access level is Domain Admin, indicating complete control over the organization’s domain infrastructure. The threat actor specifies that the company’s antivirus protection is Symantec, indicating potential challenges for traditional security measures in detecting and preventing unauthorized access.
The threat actor offers an Escrow service for a more secure transaction process. The starting price for the access is $2,000, with increments of $1,000 for each subsequent bid. There’s also an option for a blitz purchase at $4,000, likely indicating a higher bid for immediate purchase.
Unauthorized POS Machine Access Sale is Detected for Many American Shops
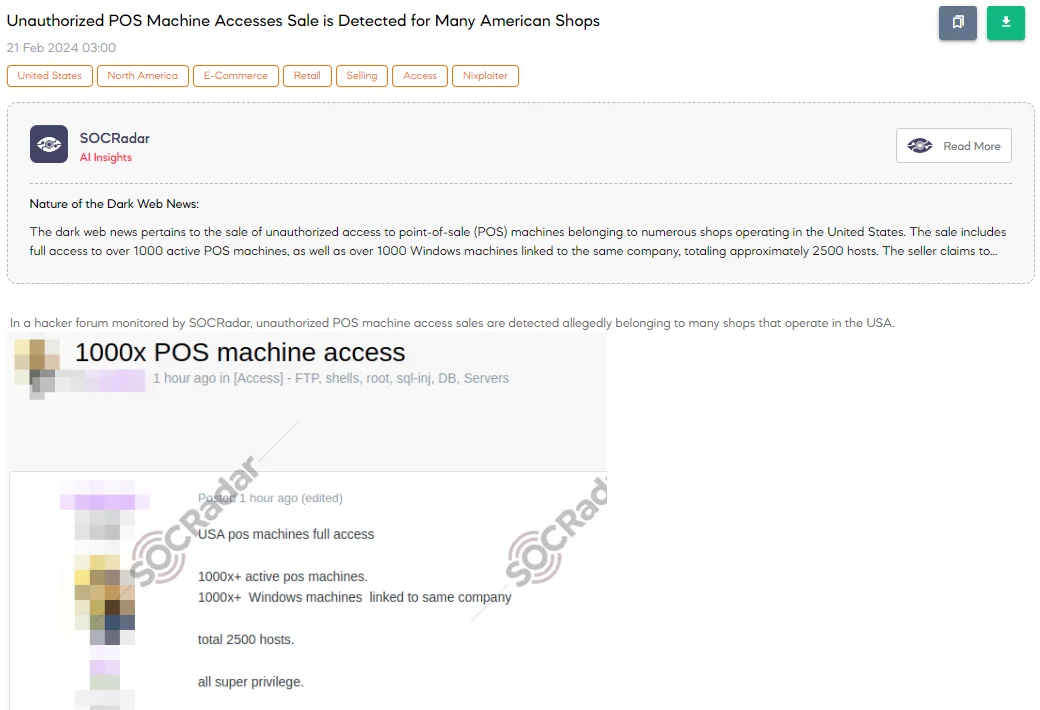
The SOCRadar Dark Web Team identified a concerning post on a hacker forum, where a threat actor is advertising the sale of unauthorized POS (Point of Sale) machine access allegedly belonging to numerous shops operating in the US. According to the post, the access includes full control over POS machines in over 1,000 shops, with each shop having multiple Windows machines linked to the same company. The access encompasses approximately 2,500 hosts, all of which grant superuser privileges.
Stealer Logs are on Sale
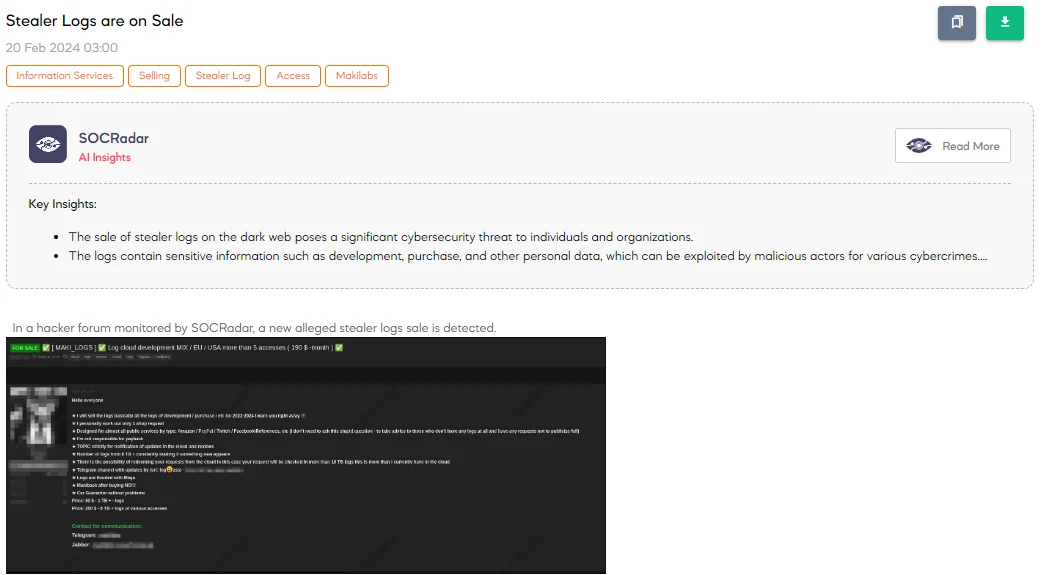
The SOCRadar Dark Web Team identified a post on a hacker forum where a threat actor offers logs purportedly acquired through various means, covering activities like development, purchases, and other interactions from 2022 to 2024. These stealer logs claim to contain data from various public services, including well-known platforms like Amazon, PayPal, Twitch, and Facebook.
The threat actor indicates that the stealer logs are continuously updated and stored in a cloud service, with a substantial amount of data available, totaling over 6 TB. They mention the availability of a Telegram channel for updates and the use of Mega for hosting the logs.
Mega is a cloud storage and file hosting service that allows users to store, access, and share files securely over the internet. The post also suggests the possibility of fulfilling specific requests from the cloud, offering customization options for potential buyers.
The price for accessing these stealer logs varies based on the amount of data, with $80 charged for 1 TB and $200 for 6 TB or more. The threat actor states that they do not offer refunds after purchase and provide assurances of a smooth transaction process through a guarantor service.
New Recruitment Post is Detected for Employees of Public Services and Commercial Organizations
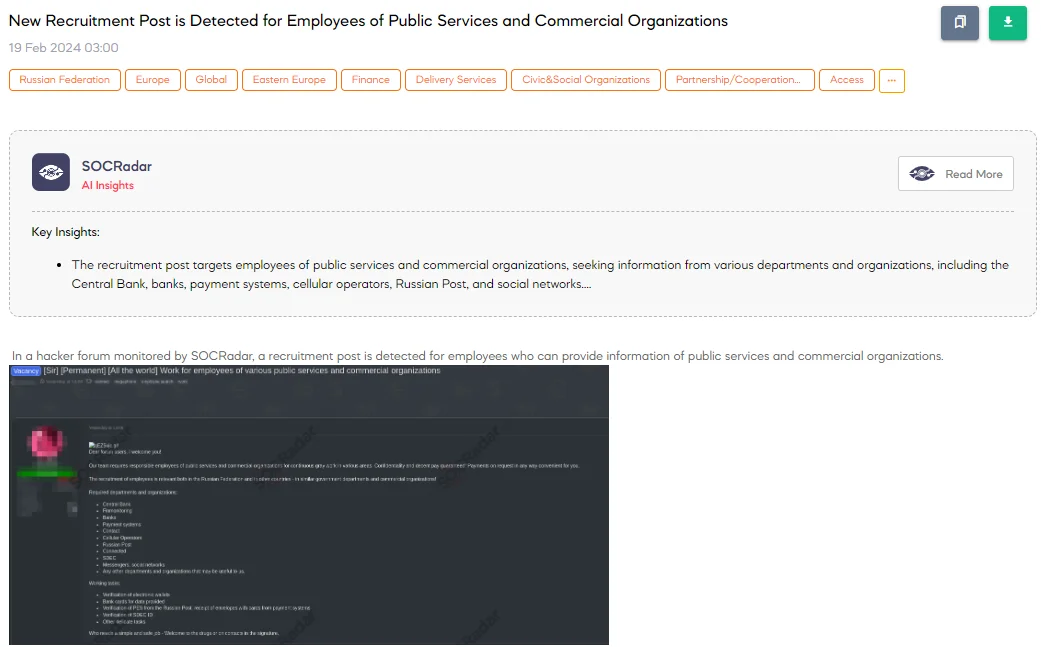
The SOCRadar Dark Web Team identified a concerning recruitment post on a hacker forum, seeking employees from public services and commercial organizations to engage in illicit activities. The threat actor behind the post is soliciting individuals for “gray work” in various sectors, promising confidentiality and decent pay. The recruitment is open to individuals both within the Russian Federation and in other countries, targeting government departments and commercial organizations alike.
The post specifies a range of required departments and organizations, including the Central Bank, financial monitoring agencies, banks, payment systems, cellular operators, postal services, and courier companies. The tasks assigned to recruited employees involve verifying electronic wallets, bank cards, postal service data, and courier identifications. Additionally, employees are expected to undertake other delicate tasks as instructed.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































