
What Do You Need to Know About the Linux XZ Utils Vulnerability, CVE-2024-3094?
A researcher has identified a critical vulnerability in Linux’s XZ Utils, a command line tool for XZ format compression. Tracked as CVE-2024-3094, this security vulnerability can allow unauthorized users to compromise sshd authentication, potentially opening the door to full remote access to systems.
Here are 10 important questions and answers about the XZ Utils backdoor:
1. What is CVE-2024-3094?
CVE-2024-3094 is a vulnerability that involves malicious code being discovered in the upstream tarballs of the XZ data compression library, starting with version 5.6.0.
Andres Freund, a PostgreSQL developer and Microsoft software engineer, identified the CVE-2024-3094 vulnerability. He noticed unusual behavior in ‘liblzma’, a component of the XZ package on Debian sid installations.
These anomalies, such as excessive CPU usage during SSH logins and errors detected by Valgrind, prompted a thorough investigation. Eventually, Freund discovered that both the XZ repository and the downloaded tarballs had been compromised, allowing a backdoor to be introduced into the software.
The insertion of malicious code into XZ Utils’ source code was carefully concealed to avoid detection within the regular Git repository. During the build process, this malicious code injects a pre-compiled file that modifies critical components of the liblzma library.
As a result, certain Linux distributions unintentionally incorporate a compromised liblzma library into their SSH implementations, making them vulnerable to exploitation by remote attackers.
2. What is the impact of CVE-2024-3094?
The malicious code allows an attacker to potentially intercept and modify data interactions of any software linked against the affected liblzma library.
3. What is the CVSS score for CVE-2024-3094?
The severity of this vulnerability is at its peak, as evidenced by its CVSS score of 10. This means it carries the potential to jeopardize the integrity of the systems it affects, causing severe repercussions in the sphere of cybersecurity.
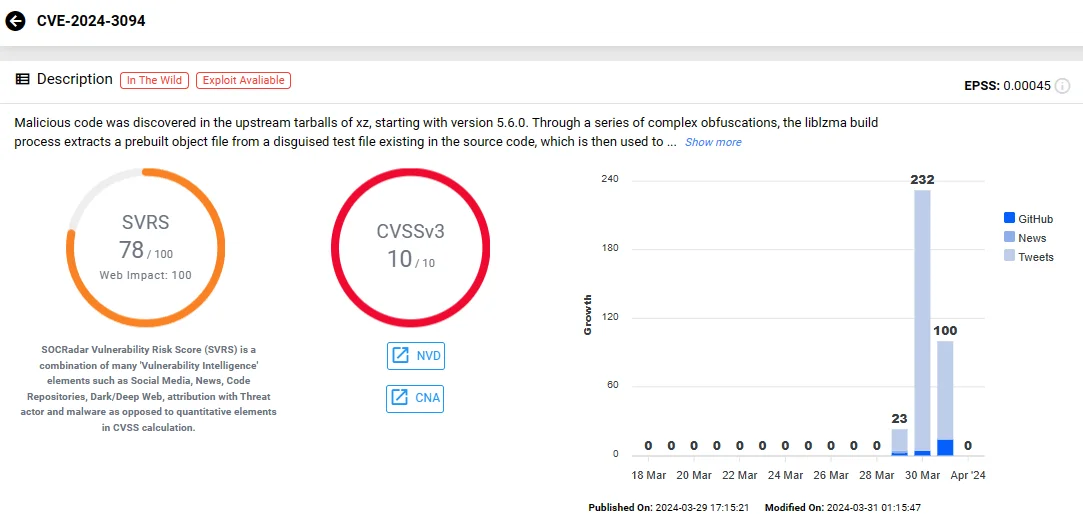
Vulnerability card of CVE-2024-3094 (SOCRadar Vulnerability Intelligence)
4. When was the malicious code introduced?
The malicious code has existed since early February 2024, so it is possible that threat actors have already attempted to use this vulnerability.
Timeline of Events Leading Up to CVE-2024-3094
An article by Evan Boehs provides a detailed timeline of events surrounding the discovery of the CVE-2024-3094 vulnerability in Linux XZ Utils. It all began with the creation of the GitHub account by “Jia Tan” in 2021, who initially made commits to libarchive, later found to be suspicious due to their potentially malicious nature.
In 2022, Jia Tan submitted a patch via a mailing list, marking the entry of a new persona, Jigar Kumar, who was pressured for the patch’s inclusion. Subsequently, Jia Tan became a regular contributor to XZ, while Jigar Kumar disappeared.
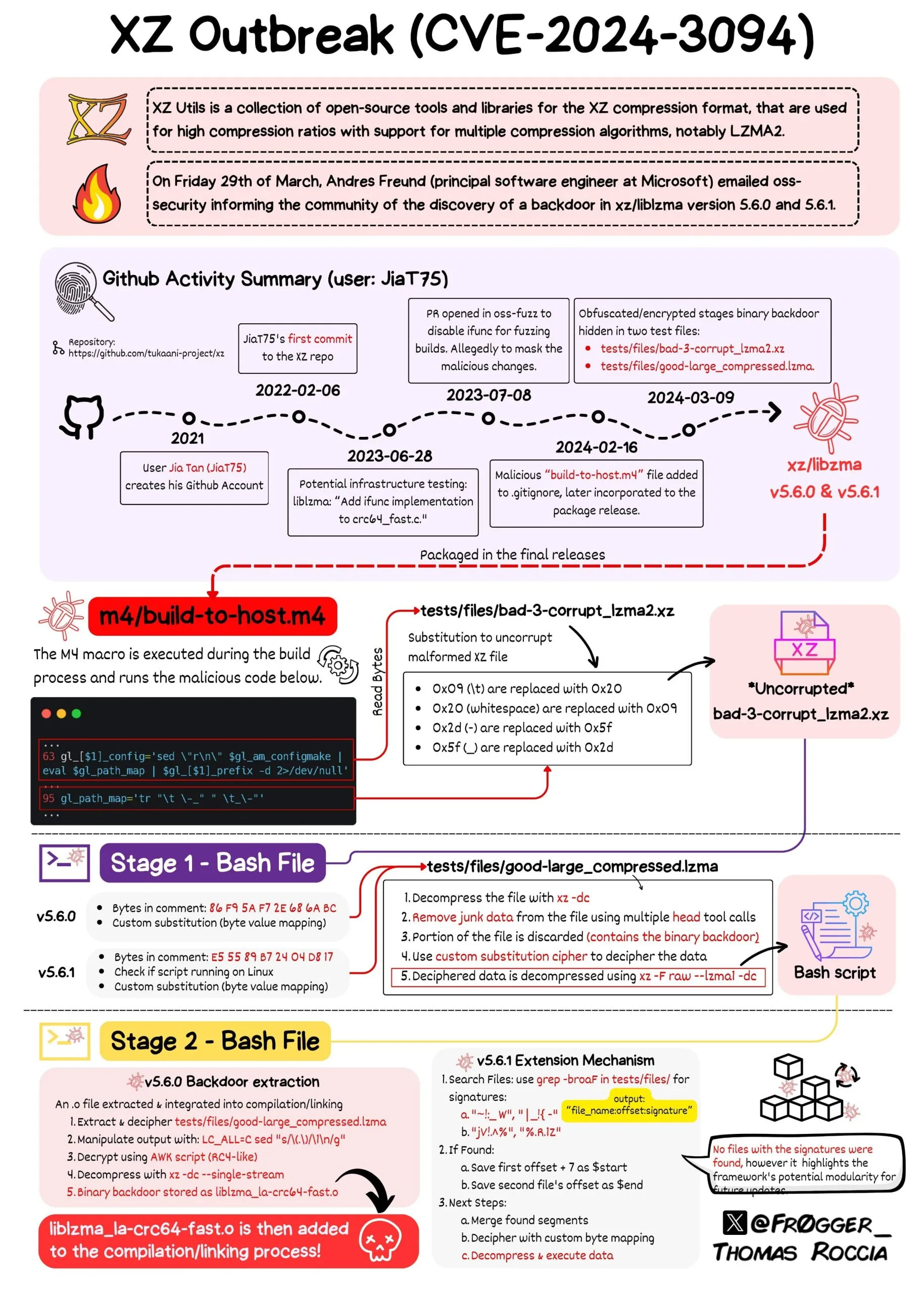
Origin of the XZ Utils Vulnerability (@fr0gger_ on X)
The article reveals attempts to conceal malicious activities through source code disguise, obfuscation techniques, and evasion tactics targeting the ‘oss-fuzz’ code testing project. It highlights significant updates made to Google’s oss-fuzz project and the testing infrastructure that enabled the exploit.
The backdoor code was strategically embedded only in the full XZ source package download, not the standard Git repository. Furthermore, there were signs of attempts to avoid detection by sabotaging the ‘oss-fuzz’ code testing project.
The article also discusses the sudden push for the inclusion of the vulnerable version in Debian, accompanied by suspicious activities from anonymous accounts. It notes the subsequent suspension of Jia Tan’s GitHub account and the actions taken by Lasse Collin to revert changes introduced by Jia.
Furthermore, the article delves into OSINT findings, including insights from IRC channels and LinkedIn profiles, shedding light on potential identities associated with Jia Tan. Finally, it discusses discoveries in Git logs, revealing variations in Jia Tan’s username and speculating on the origins of the name “Jia Cheong Tan.”
5. Which versions of XZ Utils are affected by CVE-2024-3094?
The vulnerability affects XZ library versions 5.6.0 and 5.6.1, in which meticulously obfuscated malicious code is only present in the downloadable package.
Of particular note, the M4 macro required for compiling the malicious code is missing from the Git distribution. However, the second-stage artifacts required for its injection at build time are present, assuming the malicious M4 macro has been added. This results in the creation of a compromised build that is specifically designed to target sshd authentication through systems.
6. Which Linux distributions are affected?
The malicious version of XZ is present in Fedora 41 and Rawhide, Debian unstable (Sid), Alpine Edge, and Arch Linux.
Red Hat, Kali Linux, SUSE, and Debian have all responded to this security concern, providing guidance and updates to mitigate the risk posed by this vulnerability.
Red Hat has identified that Fedora 41 and Rawhide encompass the vulnerable packages, advising users of these distributions to promptly discontinue their usage. It is worth noting that other Linux distributions like Amazon Linux, Ubuntu, and Red Hat Enterprise Linux (RHEL) remain unaffected.
Kali Linux stated that the vulnerability only impacts installations updated between March 26 and March 29. Users who updated their Kali Linux systems during this period are strongly urged to apply the latest updates promptly to mitigate the risk.
Debian confirmed that no stable versions of its distribution are compromised. However, affected packages did infiltrate Debian testing, unstable, and experimental distributions. Users of these versions are advised to promptly update their xz-utils packages.
An Online Scanner Is Available for Detecting CVE-2024-3094
Binarly introduced an online scanner aimed at identifying Linux executables affected by the CVE-2024-3094 vulnerability found in XZ Utils.
Available online at xz.fail, the scanner offers unlimited free checks, complemented by an API for bulk scans.
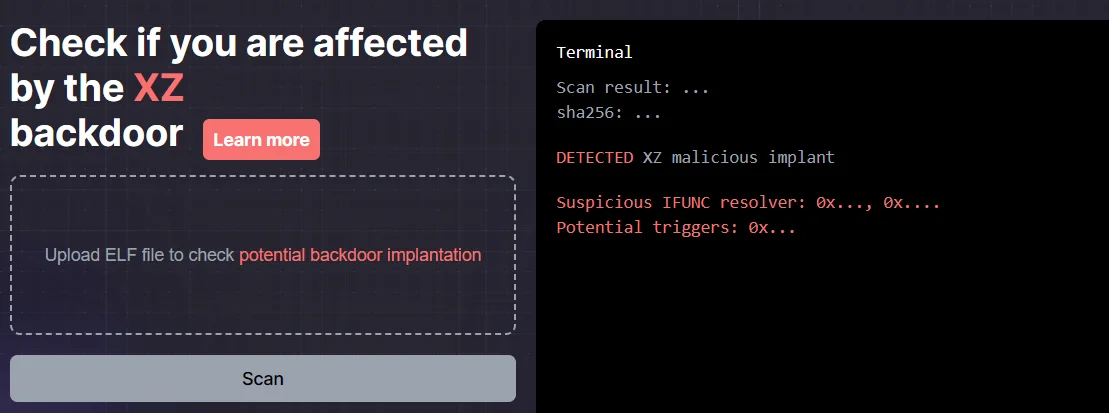
Online scanner for the XZ backdoor, xz.fail
To overcome the issue of false positives arising from simple mitigation methods, Binarly’s solution employs static analysis to identify alterations in transitions within GNU Indirect Function (IFUNC). The XZ backdoor is known to exploit GNU IFUNC by manipulating calls to intercept execution and insert malicious code.
Binarly’s scanner extends detection beyond the XZ Utils project, enhancing confidence in results. CEO Alex Matrosov underscores the scanner’s effectiveness in spotting variations and stresses its ability to adapt to code changes or recompilation.
7. How can CVE-2024-3094 be mitigated?
To mitigate CVE-2024-3094, users and developers are advised to immediately downgrade to known, unaffected versions of xz Utils, such as 5.4.6.
CISA Alerts Users and Administrators to Take Action and Address the XZ Utils Vulnerability
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert regarding the matter, recommending that both developers and users downgrade to an uncompromised release of XZ Utils (such as the stable version 5.4.6).
It is also advised to remain vigilant for any signs of malicious activity, reporting any findings directly to the CISA.
8. What should be done if a system is impacted by CVE-2024-3094?
If a system is impacted by CVE-2024-3094, an incident response should be conducted to determine if the system has been compromised, and comprehensive monitoring and anomaly detection should be implemented to identify any potential attacker activity.
9. What is the current status of the analysis and response to CVE-2024-3094?
The exact scope of CVE-2024-3094 is not yet 100% clear, and a thorough review is still ongoing to determine the full impact and appropriate mitigation strategies.
10. More Resources
How Can SOCRadar Help Combat Vulnerabilities?
Considering SSH’s crucial role in securing remote access to Linux systems, the CVE-2024-3094 vulnerability poses significant risks. If exploited, attackers could gain unrestricted access to vulnerable machines, leading to data breaches and even supply chain disruptions.
SOCRadar’s Vulnerability Intelligence delivers the most recent information on known vulnerabilities, including exploits, repositories, and new hacker trends. With such insights, organizations can proactively protect against potential threats and improve their vulnerability management strategy.
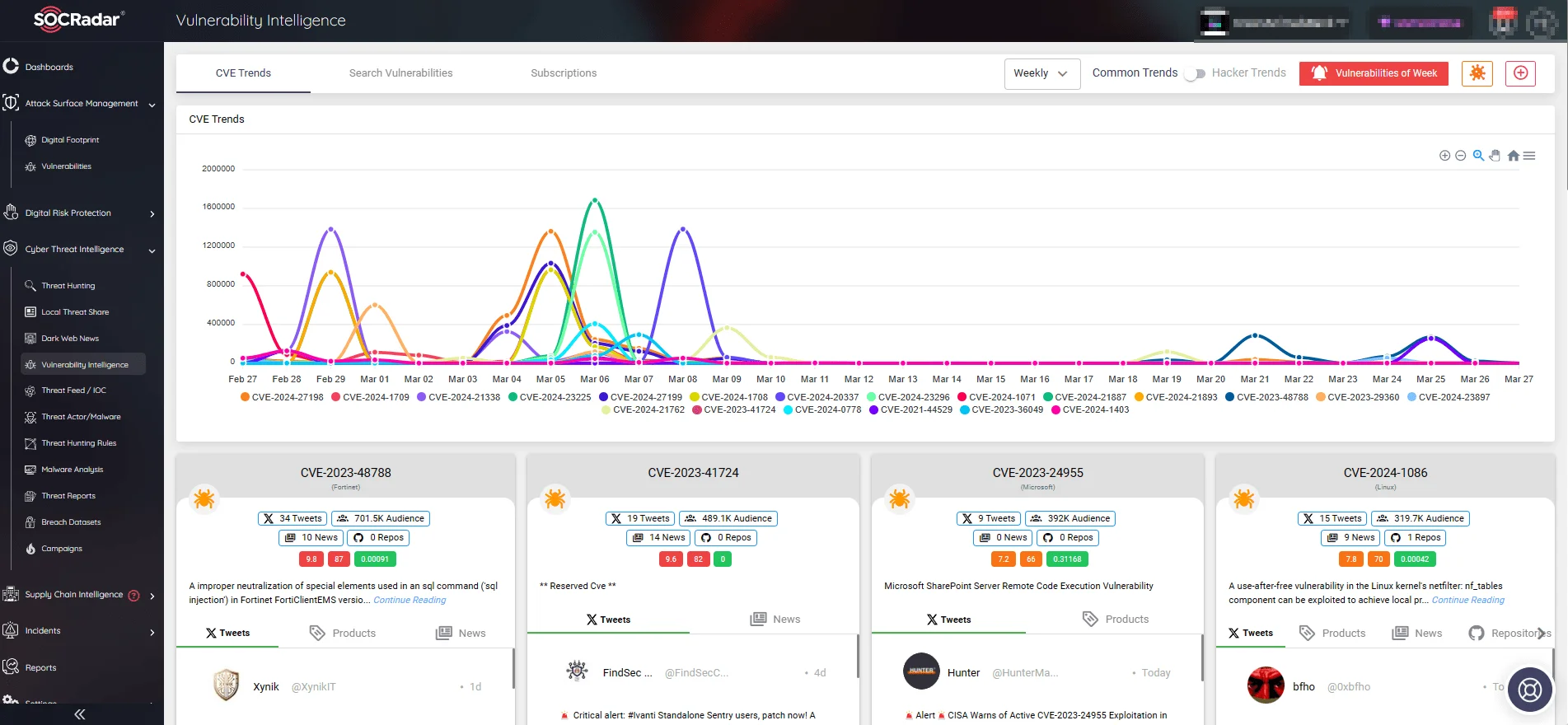
SOCRadar’s Vulnerability Intelligence, CVE Trends
SOCRadar, with its suite of XTI solutions, can help organizations significantly improve their defense against emerging threats. SOCRadar’s Attack Surface Management module offers advanced monitoring capabilities, continuously scanning digital assets for potential vulnerabilities and security incidents.
SOCRadar’s Attack Surface Management, Company Vulnerabilities




































