LockBit Attack Fails, 3AM Ransomware Steps In as Plan B
Researchers have recently identified a new strain of ransomware called 3AM. Their investigation revealed that the first known usage of this ransomware occurred when threat actors substituted it for LockBit ransomware in a failed attack.
Typically, ransomware affiliates carry a variety of tools in their arsenal for use in attacks; likewise, this new approach demonstrates that they can also carry multiple ransomware strains to pursue their targets until the very end and ensure the success of their attacks.
In the specific incident, the affiliates attempted to use LockBit but were blocked, prompting them to use 3AM instead.
While Symantec’s report on 3AM indicates that this is not the first time attackers attempting to use two different ransomware strains, it remains a relatively novel approach. Moreover, the fact that a LockBit affiliate resorted to 3AM as a fallback, could pique the interest of other malicious actors. This, in turn, implies the potential for encountering 3AM in future attacks.
This phenomenon also highlights the increasing independence of ransomware affiliates from operators, and could pave the way for a new trend in ransomware attacks.
Later on the day we published this post, the 3AM (ThreeAM) Ransomware group displayed their leak sites and added six organizations, five US and one Malaysian, to their victim list. It is unclear whether this event was a publicity opportunity or a coincidence for this group, which emerged just as the researchers identified the strain.
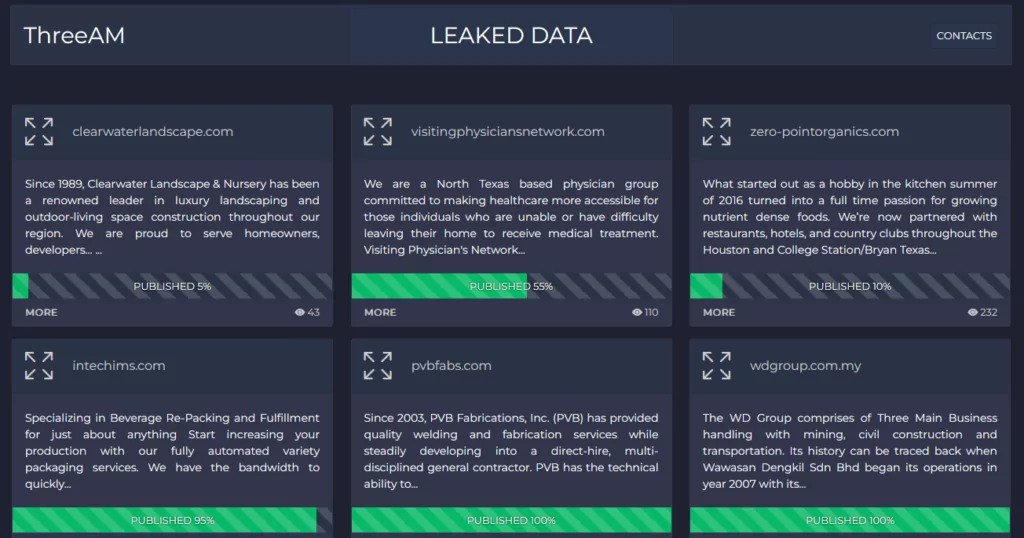
Outline of a 3AM Ransomware Attack
3AM is a newly developed ransomware written in Rust, and operates as a 64-bit executable with the capability to execute multiple commands. These commands can halt applications, obstruct backup processes, and disable security software.
Researchers note that the 3AM ransomware strain exclusively encrypts files that meet predefined criteria, and adds the extension “.threeamtime” to the filenames of the compromised files. It also tries erasing Volume Shadow (VSS) copies.
Following encryption, the ransomware generates a TXT file named “RECOVER-FILES” in each scanned folder, containing the ransom note:
Hello. "3 am" The time of mysticism, isn't it?
All your files are mysteriously encrypted, and the systems "show no signs of life", the backups disappeared. But we can correct this very quickly and return all your files and operation of the systems to original state.
All your attempts to restore data by himself will definitely lead to their damage and the impossibility of recovery. We are not recommended to you to do it on our own!!! (or do at your own peril and risk).
There is another important point: we stole a fairly large amount of sensitive data from your local network: financial documents; personal information of your employees, customers, partners; work documentation, postal correspondence and much more.
We prefer to keep it secret, we have no goal to destroy your business. Therefore can be no leakage on our part.
We propose to reach an agreement and conclude a deal.
Otherwise, your data will be sold to DarkNet/DarkWeb. One can only guess how they will be used.
Please contact us as soon as possible, using Tor-browser:
http://threeam7[REDACTED].onion/recovery
Access key:
[32 CHARS SPECIFIED BY -k COMMAND LINE PARAMETER]
Symantec researchers have reported that in the failed LockBit attack, threat actors deployed the 3AM ransomware on three computers within the target organization’s network. However, their attempts were again thwarted on two of these machines.
The attackers were observed employing the post-exploitation tool Cobalt Strike and subsequently initiated reconnaissance commands such as “whoami,” “netstat,” “quser,” and “net share” to facilitate lateral movement. To maintain persistence, the attackers added a new user. They then utilized the Wput tool to exfiltrate files to their FTP server.
After a successful attack, the attackers await contact from the victims. There is a TOR support portal for 3AM, which is used to negotiate on ransom payments with victims.
Researchers state that the precise entry point used in the attack remains unclear.
Indicators of Compromise (IoCs) Related to 3AM Ransomware
File hash (SHA256):
- 079b99f6601f0f6258f4220438de4e175eb4853649c2d34ada72cce6b1702e22 (LockBit)
- 307a1217aac33c4b7a9cd923162439c19483e952c2ceb15aa82a98b46ff8942e (3AM)
- 680677e14e50f526cced739890ed02fc01da275f9db59482d96b96fbc092d2f4 (Cobalt Strike)
- 991ee9548b55e5c815cc877af970542312cff79b3ba01a04a469b645c5d880af (Cobalt Strike)
- ecbdb9cb442a2c712c6fb8aee0ae68758bc79fa064251bab53b62f9e7156febc (Cobalt Strike)
Network indicators:
- 185.202.0[.]111
- 212.18.104[.]6
- 85.159.229[.]62
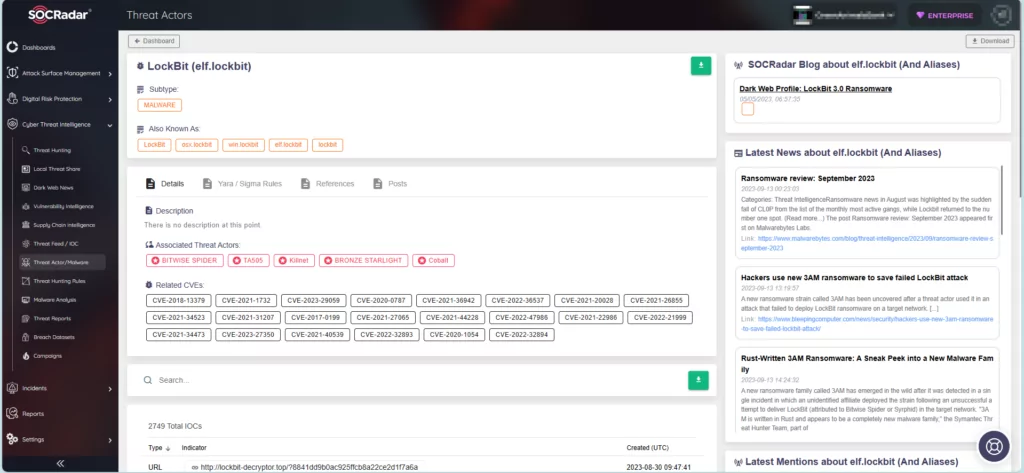
Threat Intelligence Made Easy with SOCRadar
SOCRadar actively monitors threat actors and malware, furnishing up-to-date intelligence to fortify your organization against potential threats in advance. On the platform, you can search for specific threat actors and access comprehensive details such as their targeted vulnerabilities, affiliations with other actors, and indicators of compromise. Furthermore, you can continually track and monitor their activities to stay well-prepared.