Microsoft Entra Account Lockouts Explained (FAQ on the MACE Credential Revocation Alerts)
Starting around April 19, system administrators began noticing a troubling pattern: legitimate user accounts were being unexpectedly locked out across various organizations. The root cause appears to be tied to a new security feature in Microsoft Entra ID – formerly known as Azure Active Directory. This feature, called MACE, is designed to detect leaked credentials. However, it seems to be flagging some accounts in error.
This sudden wave of lockouts has prompted confusion and concern, especially as affected admins report no signs of actual compromise. In response, we’ve compiled this FAQ to clarify what’s happening, what’s known so far, and how organizations can respond effectively while minimizing disruption.
1. What is causing account lockouts in Microsoft Entra ID?
The recent surge in account lockouts across Microsoft Entra ID environments appears to be linked to a new security feature known as MACE Credential Revocation.
Beginning around April 19, many organizations noticed a sudden influx of leaked credential alerts, resulting in widespread account lockouts. In numerous cases, these appear to be false positives – instances where MACE flagged secure accounts in error.
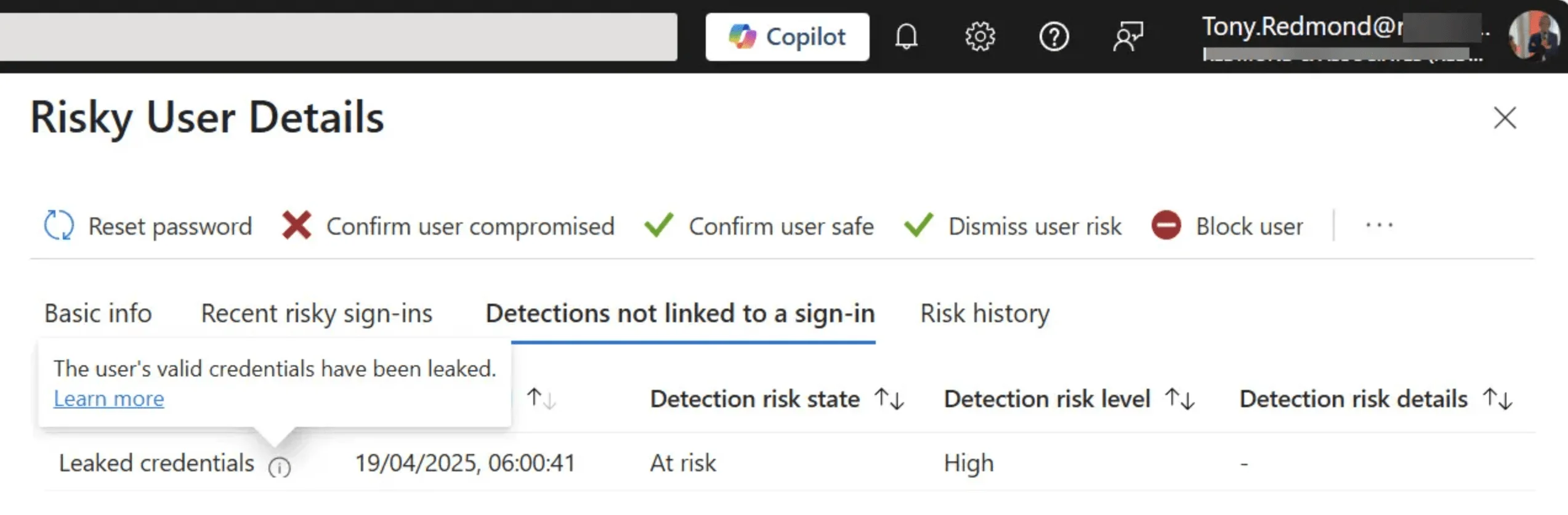
2. What is MACE Credential Revocation?
MACE Credential Revocation is a security enhancement within Microsoft Entra ID that helps detect and respond to potentially compromised user credentials. It can identify credentials that may have been exposed, whether through data breaches or listings on the Dark Web, and then proactively lock the associated accounts to prevent unauthorized access.
While the feature is designed to strengthen enterprise security, its recent rollout has sparked concerns due to unexpected account lockouts.
More about the feature can be found in Microsoft’s official documentation.
3. Why are accounts being flagged if passwords are secure?
Accounts with strong, unique passwords and MFA have still been flagged, suggesting false positives from the MACE tool. These alerts likely stem from detection errors during the tool’s initial rollout, not actual credential leaks or compromise.
4. How widespread is the issue?
The issue appears to be affecting a broad range of organizations. Reports from IT admins, particularly on Reddit, describe sudden and large-scale account lockouts. One managed service provider said nearly a third of their user accounts were locked within an hour, while another reported over 20,000 leaked credential alerts across multiple tenants overnight. These examples highlight the scale and sudden impact of the MACE rollout.
5. Are there reports of actual credential leaks?
So far, there’s no confirmed evidence of real credential leaks in the flagged accounts. Admins report that affected users had no signs of compromise and were protected by MFA. Checks against breach databases like Have I Been Pwned have also come up clean, pointing to false positives rather than actual exposures.
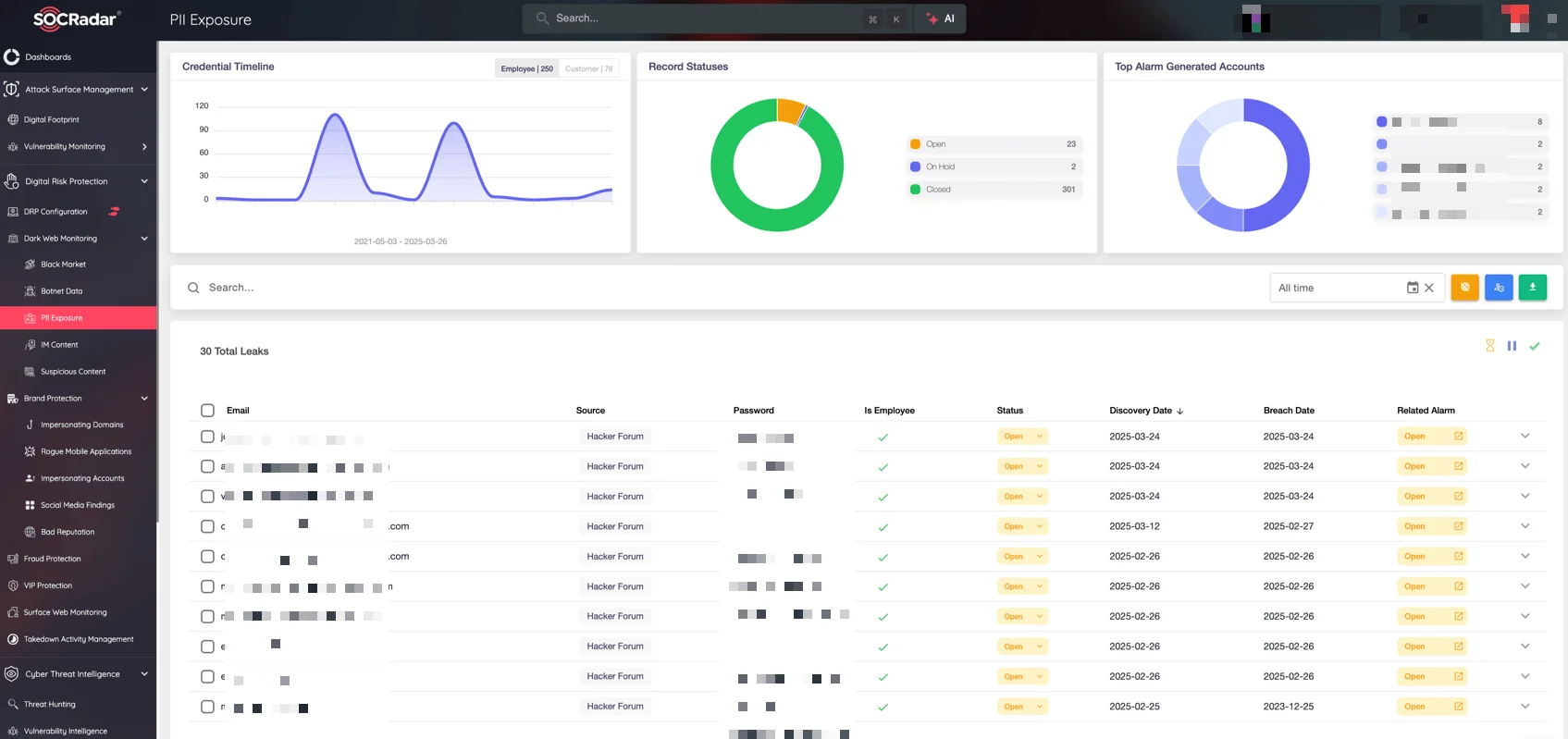
For organizations looking to monitor exposed credentials proactively, SOCRadar offers tools to track leaked account data across the surface, deep, and Dark Web. If your organization is affected by these alerts, you can use SOCRadar’s Advanced Dark Web Monitoring module to verify whether the flagged credentials have actually appeared in any known breaches, helping distinguish real risks from false positives. This allows for quicker decision-making and more precise incident response.
6. How can I identify locked accounts?
Go to the Microsoft Entra admin center and review the sign-in logs under Monitoring & Health. Look for error codes like AADSTS50053, which indicate account lockouts.
7. What should I do if I’m affected by the Microsoft Entra ID lockouts?
Start by checking sign-in logs for affected users. Reset passwords for any locked accounts, ensure Multi-Factor Authentication (MFA) is enabled, and consider opening a support case with Microsoft for further guidance.
8. How do I unlock affected accounts?
Reset the user’s password either through the Entra admin center or using the Microsoft Graph PowerShell module. This will restore access to locked accounts.
9. Can I disable MACE to prevent this?
Currently, there’s no direct way to disable MACE, as it’s built into Entra’s broader security infrastructure.
10. Has Microsoft addressed the issue?
As of now, Microsoft has not issued a public statement, and no official fix timeline exists. Some administrators report receiving confirmation that the issue stems from the initial rollout of the MACE tool.
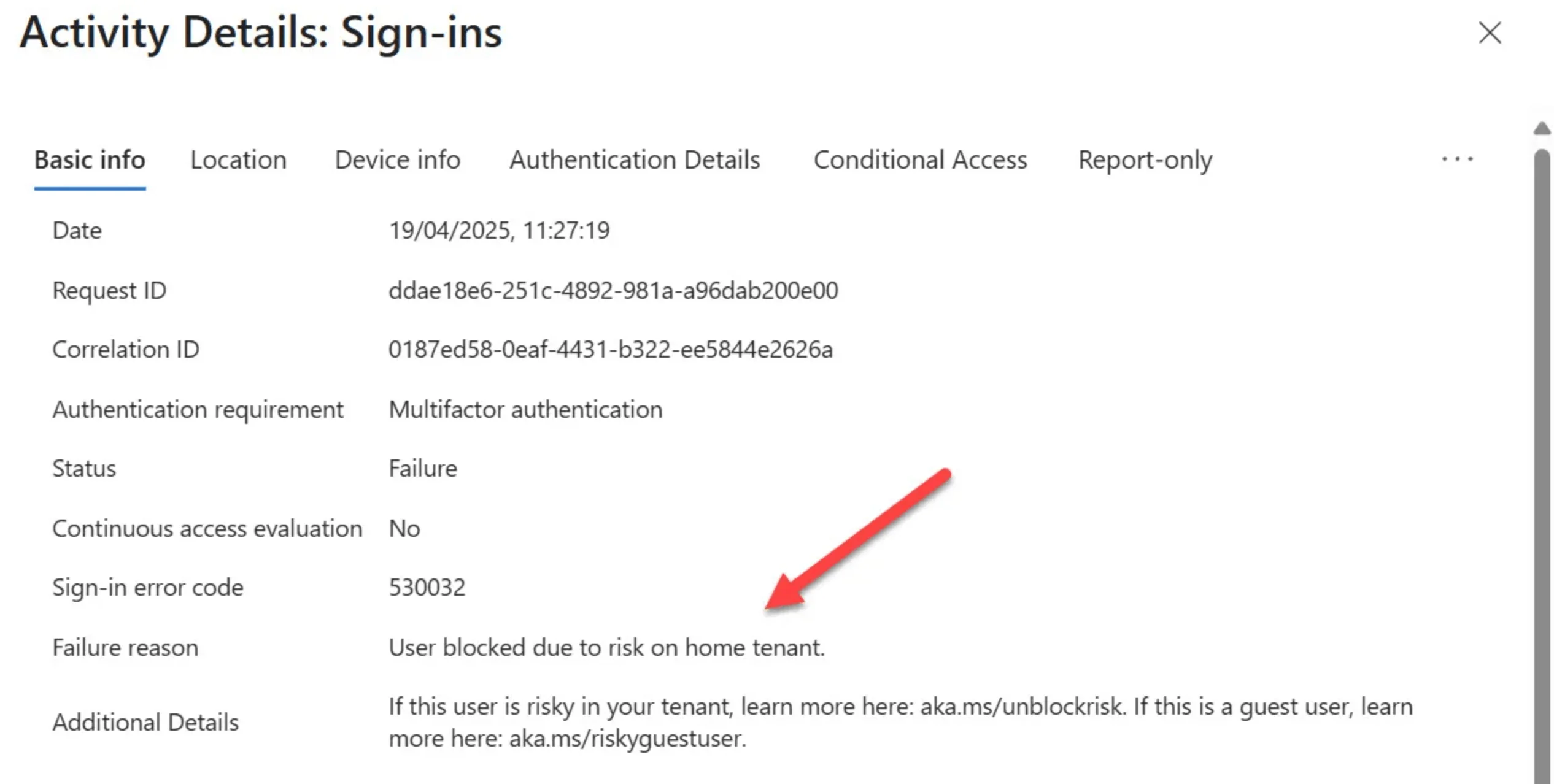
Notably, administrators observed Error Code 53003 and the recent deployment of the MACE app in their Entra tenants just before the lockouts began.
Until further clarification is provided, organizations are advised to treat all alerts seriously but consider the possibility of false positives when large numbers of accounts are suddenly affected.
11. What additional details have emerged about the Microsoft Entra lockouts?
Microsoft MVP Tony Redmond has documented several technical observations related to the recent MACE-related lockouts, many of which align with wider admin reports. These findings provide helpful context for understanding what may have occurred across affected tenants:
- Token refresh invalidation: There was an observed change to the StsRefreshTokensValidFrom property, forcing reauthentication. This update was captured in audit logs.
- MACE app provisioning pattern: The MACE Credential Revocation app appeared as a newly added enterprise application, reportedly provisioned by Microsoft’s internal JIT process.
- Unexpected alert generation: Microsoft support attributed the alerts to an internal fix involving refresh tokens, which accidentally triggered leaked credential detections.
- Timeline confusion: Alerts were reportedly sent on April 20, but many users experienced disruptions a day earlier.
- Visibility in Microsoft 365 Defender: Affected accounts were often flagged as risky within Defender, offering another place to verify detections.
- Password reset as a workaround: A simple password reset was effective in clearing the alerts and unlocking accounts.
- Graph API usage for insights: Admins can use Graph API queries to monitor MFA and conditional access metrics for unusual spikes in activity.
These observations offer a clearer technical picture of the lockouts. For a detailed walkthrough of one such case, refer to this article.