
Microsoft Reevaluates SPNEGO NEGOEX Vulnerability CVE-2022-37958 as Critical
Microsoft reassessed the severity score of a vulnerability fixed in September 2022 Patch Tuesday. The vulnerability, tracked as CVE-2022-37958, was previously identified as an information disclosure vulnerability and had a CVSS score of 7.5.
A researcher from IBM recently discovered CVE-2022-37958 could lead to remote code execution. Microsoft reevaluated the vulnerability afterward, earning a CVSS score of 8.1 and a “critical” classification.
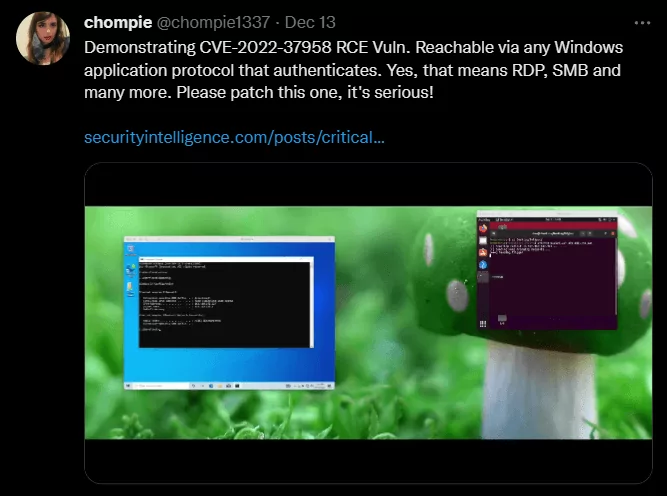
Potential Impact of CVE-2022-37958
The security vulnerability affects SPNEGO Extended Negotiation (NEGOEX) Security Mechanism. A client and a remote server can agree on which authentication protocol should be used (for instance, Kerberos or NTLM) by using SPNEGO (Simple and Protected GSSAPI Negotiation Mechanism).
CVE-2022-37958 is a “pre-authentication remote code execution vulnerability” with the potential to be wormable, according to IBM.
The firm compares CVE-2022-37958 to the CVE-2017-0144 vulnerability that WannaCry exploited in their attacks. It is detailed that the vulnerability in SPNEGO NEGOEX may affect a broader range of Windows systems because CVE-2017-0144 only affected SMB protocols, whereas CVE-2022-37958 affects SMB, HTTP, and RDP.
How Does CVE-2022-37958 Work?
An attacker must put in significant effort in preparation for an attack to succeed. To accomplish this, an attacker could:
- Try to gather information about the target environment.
- Prepare the target environment to improve exploit reliability.
- Conduct a man-in-the-middle (MITM) attack in the logical network path, allowing them to interfere with network communications.
Is There a Mitigation Available?
Researchers have yet to provide additional explanations or technical details about the vulnerability to allow time for the updates to be applied.
Microsoft rolled out a patch for CVE-2022-37958 in the September 2022 Patch Tuesday. It is recommended to apply the patch as soon as possible.
If you cannot apply the patch immediately, you should limit Windows authentication to Kerberos or Net-NTLM and remove “Negotiate” from the default option.
The best practice is to continuously monitor your attack surface for these types of threats and to safeguard any services accessible via the internet.
SOCRadar’s External Attack Surface Management assists you in discovering and actively protecting your digital assets with the attacker’s point of view against potential threats.
Visit Microsoft’s Update Guide for more information.




































