
MITRE ATT&CK® v14: A New Chapter in Cybersecurity Resilience
As we begin 2024, let’s take a moment to reflect on the transformative year for cybersecurity landscapes that was 2023. The MITRE ATT&CK® framework has guided you, bolstering your defenses with knowledge and strategic insights. The roadmap delineated early in the year has led us to the doorstep of two pivotal releases—MITRE ATT&CK® v13 and the latest MITRE ATT&CK® v14, which have expanded the framework substantially, according to the release notes published on October 31, 2023.
2023’s version of ATT&CK® has been particularly robust, comprising 760 pieces of software, 143 groups, and 24 campaigns, broken down by domain to offer tailored defensive strategies. With 201 techniques, 424 sub-techniques, and a rich tapestry of groups, software, and campaigns within the Enterprise domain, your arsenal against cyber threats has never been more comprehensive. The Mobile domain has seen its growth with 72 techniques and a significant collection of software and data sources. In comparison, the ICS domain has fortified its structure with 81 techniques and introduced 14 critical assets.
MITRE ATT&CK® framework
What’s New in MITRE ATT&CK® v14?
It is time to take stock of the new features and enhancements that MITRE ATT&CK® v14 has introduced. This latest framework iteration has expanded its repertoire to provide a more granular understanding of threat actors’ tactics, techniques and procedures. Here’s what you can expect to find in the v14 update:
- Lateral Movement Analytics: The expansion of ATT&CK® v14’s analytics, especially in Lateral Movement with over 75 BZAR-based analytics, equips you with the cutting-edge capability to detect stealthy movements across your network, which is a critical aspect of defending against advanced persistent threats. BZAR (Bro/Zeek ATT&CK-based Analytics and Reporting) is a set of scripts and tools for the Bro/Zeek Network Security Monitor designed to detect adversarial activities based on the MITRE ATT&CK framework.
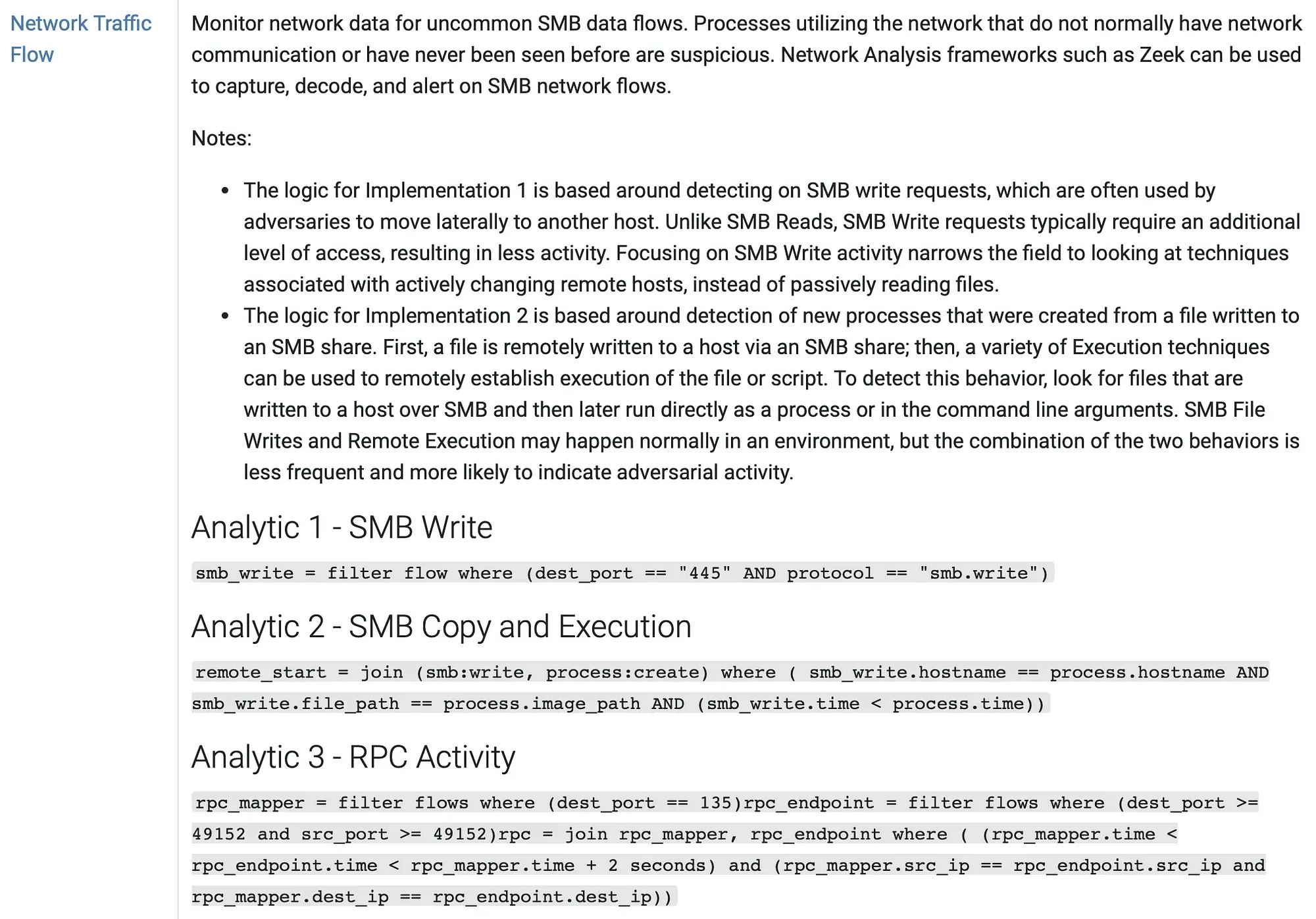
Sample Analytic Derived from BZAR (Source: MITRE ATT&CK® Medium)
- ICS Assets: In the realm of Industrial Control Systems (ICS), v14 has added over a dozen new assets that map the primary functional components of ICS environments. This addition offers a detailed lexicon to better understand and protect the operational technologies underpinning critical infrastructure.
- Mobile Threat Spectrum: The expanded mobile matrix of the framework now covers new phishing vectors, including quishing, to reflect the evolving nature of social engineering attacks in the mobile domain, enabling you to bolster defenses against various mobile threats.
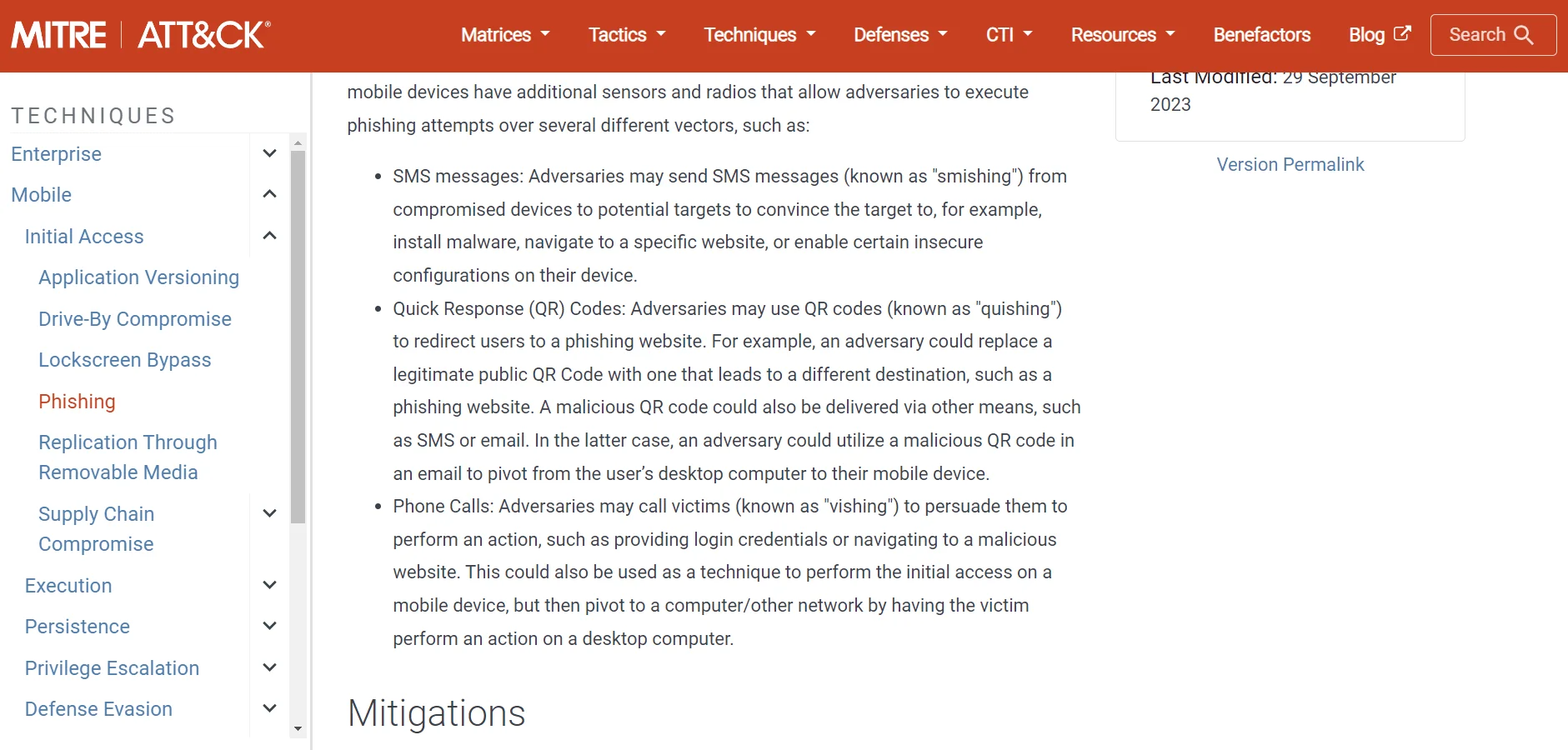
The screenshot depicts a section of the MITRE ATT&CK framework detailing phishing vectors such as smishing and quishing.
- Structured Detections for Mobile: The introduction of mobile structured detections provides a more systematic approach to identifying specific techniques and understanding the required data sources for each detection, bringing mobile defense strategies up to par with enterprise-grade security measures.
- Enhanced Detection Notes: Building upon the foundation set by v13, v14 features extensive detection notes that aid in identifying signs of adversary behavior, especially when analyzing network traffic. This enhancement streamlines the process of correlating observed activities with potential threats.
- Refined Relationships: The interplay between detections, data sources, and mitigations has been meticulously refined. These relationships are crucial for developing comprehensive defensive strategies, and the latest updates allow for a more cohesive and practical application of security measures.
- Navigation Bar Improvements: The ATT&CK® website’s navigation experience has improved with a streamlined structure, making it easier to find and utilize the resources you need.
These features represent a concerted effort to keep the cybersecurity community ahead of adversaries. As you continue to bolster your defenses and refine your security strategies, these updates will provide the intelligence and tools necessary to anticipate and counter emerging threats.
To explore these new features in detail and understand how to integrate them into your cybersecurity practices, refer to the official MITRE ATT&CK® release notes and changelogs as indispensable resources.
MITRE ATT&CK 2023 Roadmap and Progress from v13 to v14
In the 2023 roadmap, MITRE ATT&CK® laid out a strategic plan to broaden the framework’s coverage and deepen its insights into cyber threats. The focus was on enhancing the usability and functionality of the ATT&CK website, incorporating feedback from the cybersecurity community, and expanding the knowledge base to include more diverse and advanced threat actor behaviors.
The roadmap anticipated the growth of the ATT&CK matrices, with particular emphasis on developing more granular and actionable content. It also outlined the intention to improve collaboration tools, enabling you to contribute more effectively to the evolving database of cyber adversary intelligence.
As you progressed through the year, MITRE ATT&CK® v13 brought these plans to fruition by introducing a structured changelog and enhancing detection notes. This version provided a more straightforward path for tracking changes and understanding the nuances of threat actor TTPs.
Transitioning to MITRE ATT&CK® v14, you witnessed the roadmap’s ambitious goals come to life. The framework’s capabilities were significantly expanded, particularly in detection analytics and the inclusion of ICS assets. The mobile threat matrix also saw an extension to cover emerging social engineering vectors, reflecting the changing nature of cyber threats.
The enhancements in v14 over v13 included:
- The introduction of a substantial number of BZAR-based analytics for Lateral Movement.
- The enrichment of the ICS matrix with detailed asset descriptions and technique mappings.
- Adding structured detections in the mobile matrix aligns it with enterprise-level defenses.
These advancements, outlined in the 2023 roadmap, have been meticulously implemented in v14, showcasing MITRE’s commitment to continuous improvement and adaptation to the cybersecurity landscape’s evolving challenges. As you utilize these developments, you are equipped with a more robust framework to anticipate and counteract cyber threats, staying aligned with the strategic vision that MITRE ATT&CK® has set for the year.
Forging Ahead with SOCRadar and MITRE ATT&CK® v14
The MITRE ATT&CK framework is a valuable asset for Cyber Threat Intelligence (CTI), offering a structured and comprehensive catalog of known adversary Tactics, Techniques, and Procedures (TTPs). Here’s how you can use it to enhance CTI:
- Common Language for Threat Analysis: ATT&CK offers a common language and model for discussing and analyzing cyber threats. Organizations can use it to standardize how they describe adversaries’ behavior, making it easier to communicate threat intelligence internally and externally.
- Actionable Threat Intelligence: Organizations can anticipate likely attack methods and tailor their defenses accordingly by identifying and understanding the TTPs used by threat actors, particularly those targeting specific sectors like finance. The ATT&CK framework helps organizations move beyond reactive measures to more proactive and predictive security postures.
- Enhancing Security Measures: Organizations can use ATT&CK to evaluate their current security measures against the known TTPs of threat actors. This evaluation helps them determine their defenses’ effectiveness and identify any gaps needing attention.
- Using MITRE ATT&CK Navigator: The MITRE ATT&CK Navigator allows organizations to visualize and explore the tactics and techniques of different threat actors. For example, a financial institution can use it to compare the TTPs of various APT groups targeting the finance sector, understand their attack patterns, and prepare specific defenses against those techniques.
- SOCRadar and ATT&CK Integration: SOCRadar can integrate ATT&CK to offer enhanced threat actor tracking and intelligence. By utilizing the ATT&CK database, SOCRadar can provide more detailed insights into the TTPs of various threat actors, enabling organizations to dynamically track and defend against emerging threats.
- Prioritizing Detections and Improving Defense: The framework aids in documenting and communicating threat behaviors, which helps security teams prioritize detections and focus on the most critical and likely threats. Organizations can continuously improve their defense mechanisms by understanding the nature of the threat actors and their evolving tactics.
- Linking to Vulnerabilities and Mitigation Strategies: ATT&CK can link adversary techniques to known vulnerabilities to develop effective mitigation strategies. This approach is useful for understanding how attackers might exploit specific vulnerabilities and preparing appropriate defenses accordingly.
- Research and Development: The framework is widely used in CTI research to classify and understand adversary behaviors. However, there is an opportunity to further investigate how CTI insights can enhance the ATT&CK framework itself, contributing to its growth and relevance.
MITRE ATT&CK is a critical tool for organizations aiming to understand and defend against cyber threats. It provides a detailed, attacker-centric view of the threat landscape, enabling organizations to develop informed, effective, and proactive defense strategies. SOCRadar’s integration of ATT&CK exemplifies how CTI can be enriched and operationalized for real-time threat tracking and defense enhancement. As cyber threats evolve, utilizing frameworks like ATT&CK for CTI will remain essential to any robust cybersecurity strategy.




































