TL;DR: MITRE CVE Program Funding Expiration – What CISOs Must Know
MITRE’s funding to manage the CVE program was reported to be expiring, triggering immediate alarm across the cybersecurity landscape. Below are the key points every cybersecurity decision-maker needs to grasp about the situation:
- MITRE’s funding to manage the CVE program was reported to be expiring on April 16, 2025, raising alarm across the industry.
- The CVE program is essential for tracking and standardizing cybersecurity vulnerabilities across the world.
- Immediate effects could include disruption in assigning new CVE IDs, impacting scanners, patching, and incident response.
- Mid-term concerns involve fragmented vulnerability tracking, deteriorated national databases, and slower vendor coordination.
- There are no official alternatives, though CNAs like VulnCheck are providing temporary stopgaps.
- A new non-profit, the CVE Foundation, was announced shortly before the April 16 funding deadline to support the program’s future as a community-driven initiative; though questions remain about its timing, readiness, and long-term role.
- CISOs should act now: monitor developments, prepare internal tracking plans, and advocate for government action.
In this article, we’ll break down the most critical and commonly asked questions surrounding this issue, to help CISOs and security leaders navigate what has changed and what may come next.
1. What happened to MITRE’s CVE program funding?
As of April 16, 2025, MITRE’s federal contract to operate and maintain the Common Vulnerabilities and Exposures (CVE) program, as well as the Common Weakness Enumeration (CWE) program, were reported to be expiring, prompting warnings about potential disruption.
The CVE program has especially been a cornerstone in cybersecurity, providing standardized identifiers for publicly disclosed vulnerabilities.
While the immediate crisis was ultimately averted through a last-minute funding extension, the episode raised serious concerns about the continuity and long-term stability of this critical cybersecurity resource.
2. Why did the funding expire?
The funding lapse is attributed to budgetary decisions by the U.S. government, specifically the Department of Homeland Security (DHS) and the Cybersecurity and Infrastructure Security Agency (CISA), which have not renewed MITRE’s contract.
While the specific reasons for the initial non-renewal have not been publicly detailed, CISA ultimately secured an 11-month contract extension to prevent disruption to the programs.
3. When did this occur?
- April 15, 2025: MITRE leadership notified the CVE Board and broader cybersecurity community that its funding to operate the CVE and CWE programs was expiring the following day.
- April 16, 2025: On the day the programs were set to lapse, CISA confirmed it had secured incremental funding to prevent a break in service. As a result, both the CVE and CWE programs remained operational.
MITRE warned about the potential disruption had the lapse occurred, citing wide-ranging impacts from vulnerability database degradation to breakdowns in critical infrastructure protection. The quick extension avoided those outcomes, but also intensified calls for long-term sustainability planning.
4. What are the immediate implications for the cybersecurity community?
Although the immediate disruption was avoided, the scare underscored how dependent the cybersecurity ecosystem is on continuous CVE program operations. Key concerns raised included:
- Disruption in Vulnerability Tracking: Without a central authority, assigning and cataloging new CVEs may be delayed or inconsistent.
- Impact on Security Tools and Operations: Many cybersecurity tools and incident response protocols rely on CVE identifiers for threat assessment and mitigation.
- Challenges for Critical Infrastructure: Organizations may face difficulties in identifying and addressing vulnerabilities promptly, potentially affecting national and global cybersecurity postures.
5. What are the mid-term effects on the cybersecurity community?
While funding has been temporarily extended, the episode revealed longer-term risks that could arise from future disruptions or permanent changes:
- Fragmentation of Vulnerability Databases: In the absence of a universally trusted source, various organizations might build their own tracking systems, leading to data inconsistency and compatibility issues.
- Delayed Vulnerability Disclosures: Without a trusted coordination body, researchers and vendors may struggle with responsible disclosure, increasing the risk of unpatched exploits.
- Increased Risk Exposure: Organizations might find it harder to assess, prioritize, and act on vulnerabilities without a standardized reference framework, raising the potential for exploitation.
6. Are there alternatives to the CVE program?
While the CVE program is the most recognized standard for vulnerability identification, other entities may step in to fill a potential gap:
- CVE Numbering Authorities (CNAs): Organizations like VulnCheck have proactively reserved CVE identifiers to continue vulnerability tracking.
- Private Sector Databases: Companies such as Tenable maintain their own vulnerability databases and may offer alternative tracking mechanisms.
However, if widely adopted alternatives are not coordinated in the absence of a centralized system like MITRE’s CVE program, the result could be inconsistency and reduced efficiency across the industry.
7. What should CISOs and security leaders do?
In light of the uncertainty around the CVE program’s funding, security leaders must take proactive steps to safeguard their vulnerability management practices. The following actions can help organizations stay resilient regardless of future developments:
- Engage with CNAs: Collaborate with organizations that have reserved CVE identifiers to ensure continued access to vulnerability information.
- Diversify Vulnerability Sources: Incorporate multiple vulnerability databases and advisories into your security operations to mitigate reliance on a single source.
- Advocate for Funding Restoration: Engage with industry groups and government contacts to emphasize the importance of the CVE program and advocate for renewed funding.
- Monitor Developments: Stay informed about alternative solutions and community efforts to establish new standardized vulnerability tracking mechanisms.
8. Is there a chance for funding restoration?
MITRE has expressed its commitment to the CVE program and is working with government agencies to secure continued support. However, while an 11-month contract extension has temporarily averted service disruption, long-term funding and oversight remain uncertain.
In response to these uncertainties, several CVE Board members have launched the “CVE Foundation”, a non-profit initiative aiming to make the CVE program more independent and community-driven. The foundation stated that this transition effort has been underway for a year, but some observers have raised questions about the timing and readiness of the initiative – especially since its domain registration and website launch closely coincided with the reported expiration date.
Whether this new foundation will complement or eventually replace MITRE’s role remains to be seen, but its formation underscores growing concerns about relying solely on a government-contracted model for such a globally critical resource. However, as of now, no official plans have been announced to restore funding.
9. What does this mean for global coordination and the future of vulnerability management?
The CVE program has long served as a shared language for cybersecurity professionals around the world. Any disruption to its continuity could have threatened international collaboration, timely threat intelligence sharing, and coordinated incident response. While the recent contract extension averted immediate disruption, it also exposed deeper structural fragilities in how vulnerability tracking is managed.
To strengthen resilience going forward, the cybersecurity community may need to adapt by:
- Developing New Standards: Creating alternative frameworks for vulnerability identification and tracking.
- Enhancing Collaboration: Strengthening partnerships between public and private sectors to maintain effective vulnerability management.
- Investing in Automation: Leveraging AI and machine learning to identify and prioritize vulnerabilities in the absence of a centralized system.
10. What happens to the existing CVE database?
MITRE has confirmed that the CVE database remains publicly accessible and fully functional for now. With the government contract extended, new entries continue to be added. However, the recent uncertainty has highlighted the importance of transparency and long-term planning to ensure continuity regardless of funding models.
How SOCRadar Helps You Navigate the CVE Uncertainty
SOCRadar helps organizations maintain comprehensive visibility and situational awareness, even when uncertainty surrounds centralized vulnerability tracking systems.
1. Continuous Vulnerability Discovery
- SOCRadar doesn’t rely solely on CVE IDs.
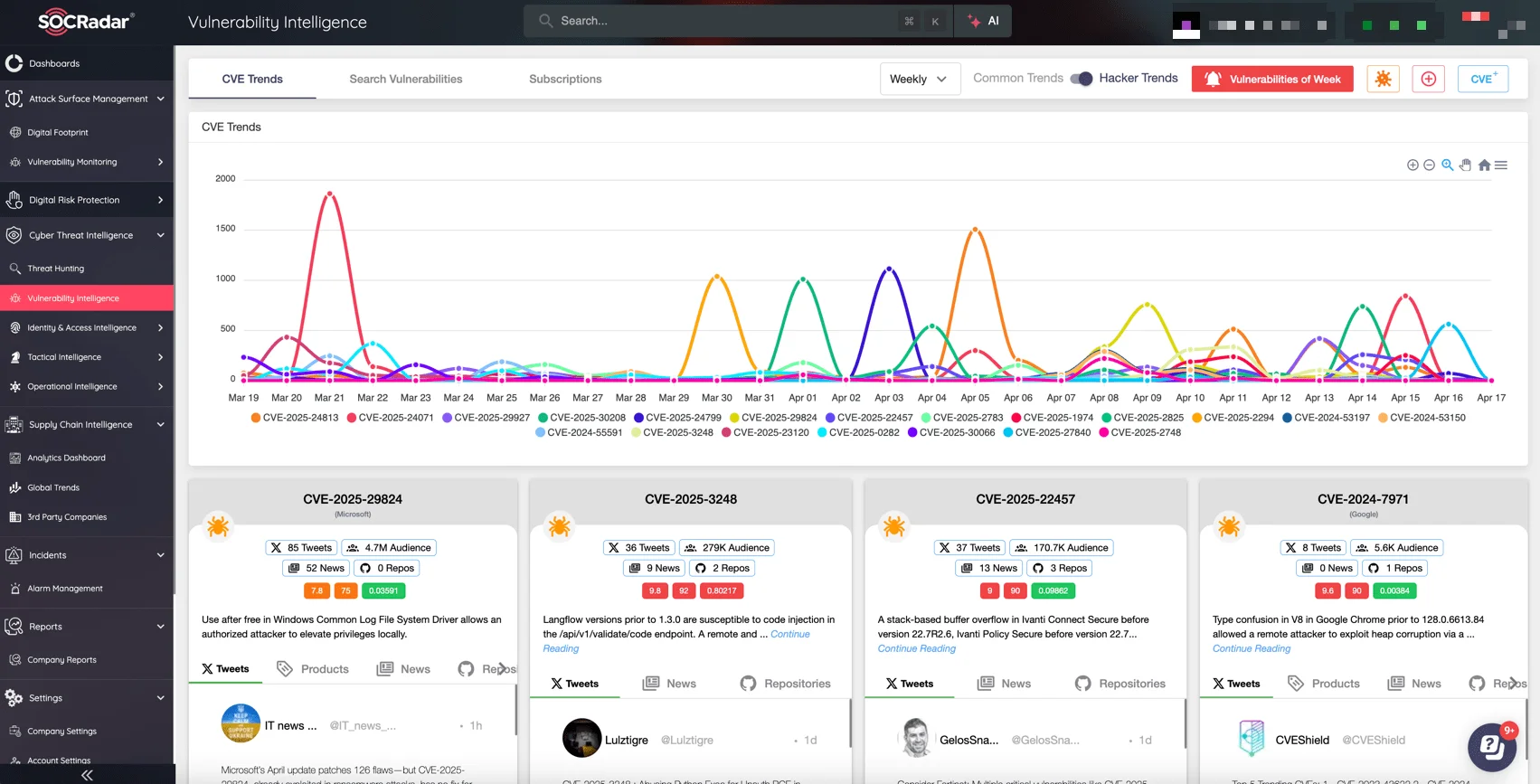
- Our Vulnerability Intelligence module tracks threat actor chatter, exploit availability, vendor advisories, and Dark Web mentions — even when a CVE isn’t issued yet.
For instance, when a zero-day is discovered but lacks a CVE, SOCRadar XTI can flag it based on vendor advisory, GitHub exploit release, and mentions on Telegram.
Explore real-time Vulnerability Intelligence with SOCRadar, powered by deep threat context and exploit insights.
2. Real-Time Alerts Based on Exploitability, Not Just CVE IDs
- SOCRadar prioritizes based on threat actor activity, critical infrastructure targeting, and exploit readiness.
- Even if a vulnerability lacks a CVE, you’ll still get an alert if it’s actively being exploited.
Example: A vulnerability in a popular VPN appliance is being used by ransomware groups. SOCRadar alerts your SOC team with proof of exploitation — even if no CVE is available.
Get free access to actionable threat intelligence tailored for professionals with SOCRadar Freemium.
3. Custom Threat Intelligence Reports
- CISOs can generate custom reports using keywords like software names, exploit types, or attack surfaces.
- You’re no longer dependent on CVE tags – your report still surfaces real threats based on context and severity.
Example: Your board asks for a report on all known vulnerabilities in your Citrix environment. SOCRadar provides one using threat actor TTPs, exploit info, and Dark Web signals.