
MSI Breach, Operation Cookie Monster & Data Sales
Powered by DarkMirror™
Ransomware attacks continue to be a nightmare for organizations. The Money Message group made a name for itself for a while and performed a shocking attack last week. The threat actor targeting Taiwanese computer parts manufacturer MSI has captured sensitive data, including the company’s source code.
Another significant incident of the last week was the seizure of Genesis Market. How the site, which the FBI’s Operation Cookie Monster destroyed, will affect the cybercrime ecosystem is a matter of curiosity.
Find out if your data has been exposed.
The New Ransomware Victim of Money Message: MSI
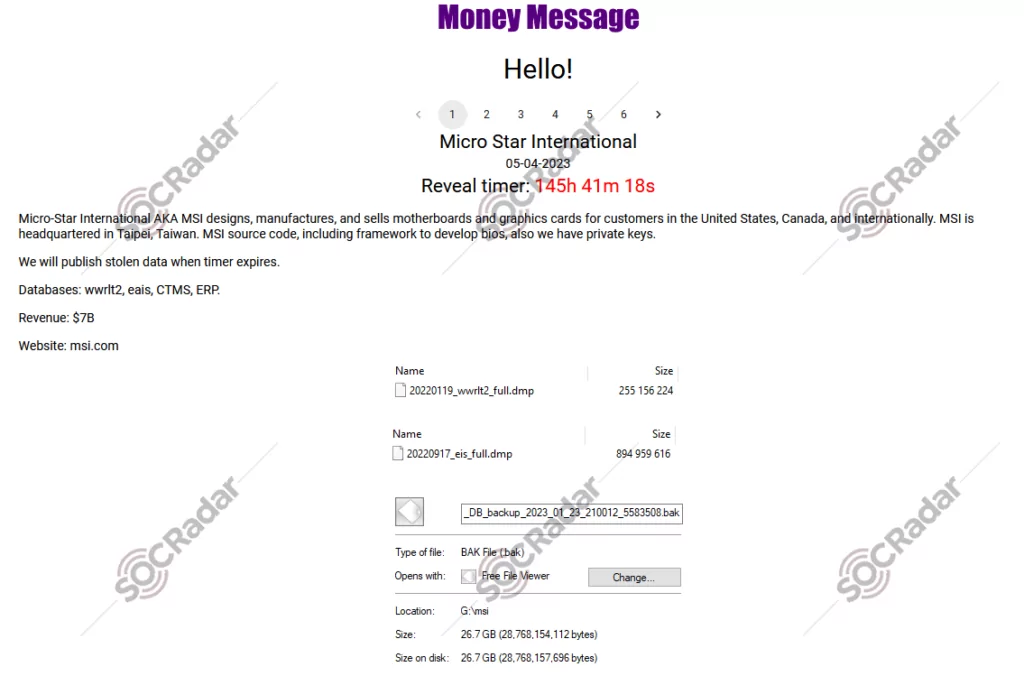
On April 5, SOCRadar dark web researchers found a post that the Money Message ransomware gang had added Taiwanese computer parts manufacturer MSI (Micro-Star International) to its list of victims. The threat actor claims to have compromised sensitive data such as source codes, CTMS and ERP databases, private keys, and BIOS firmware. MSI has acknowledged the cyberattack and confirmed that its network was breached.
FBI Seizes Genesis Market in ‘Operation Cookie Monster’
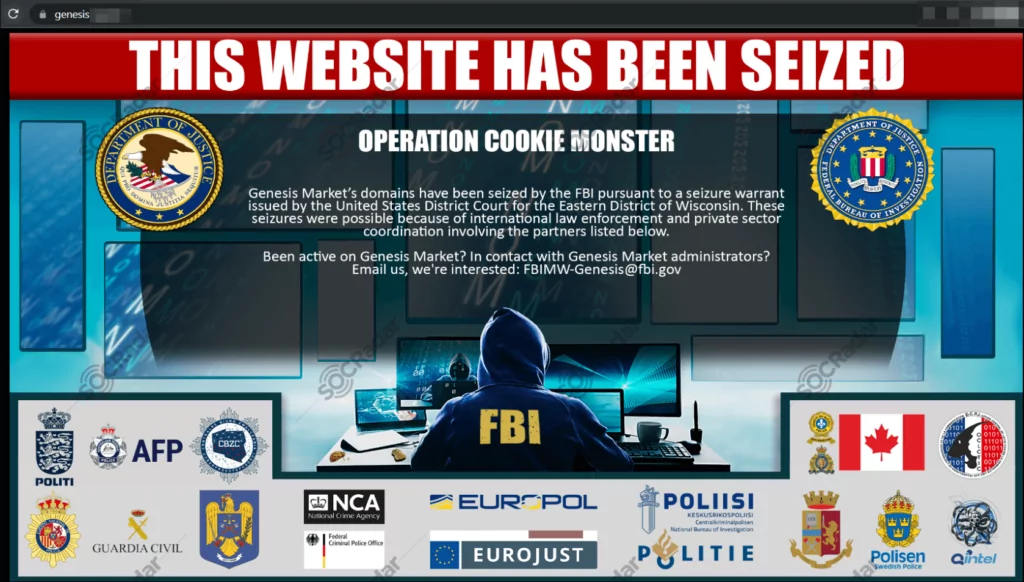
On April 4, Under a court order from the US District Court for the Eastern District of Wisconsin, the FBI seized Genesis Market’s web domains on Tuesday. The operation, dubbed “Operation Cookie Monster,” was so named due to the sale of web browser information, or “cookies,” on the underground market. The United States Department of Justice, along with the FBI, Europol, and other international partners, collaborated to successfully seize the domain of Genesis Market. The marketplace was renowned for its vast collection of thousands of digital identities.
Central Institute for Nuclear Research Data is on Sale
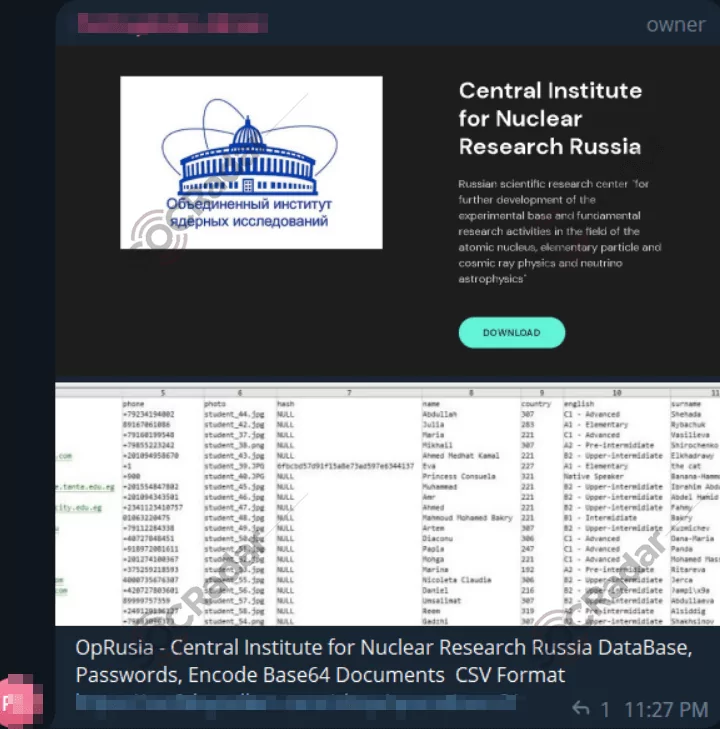
A SOCRadar researcher has detected an alleged sale of data belonging to the Central Institute for Nuclear Research in Russia on a Telegram channel. Cybercriminals claim the dataset includes a database, passwords, and encoded Base64 documents in CSV format.
The New Ransomware Victim of Lockbit 3.0: TVH
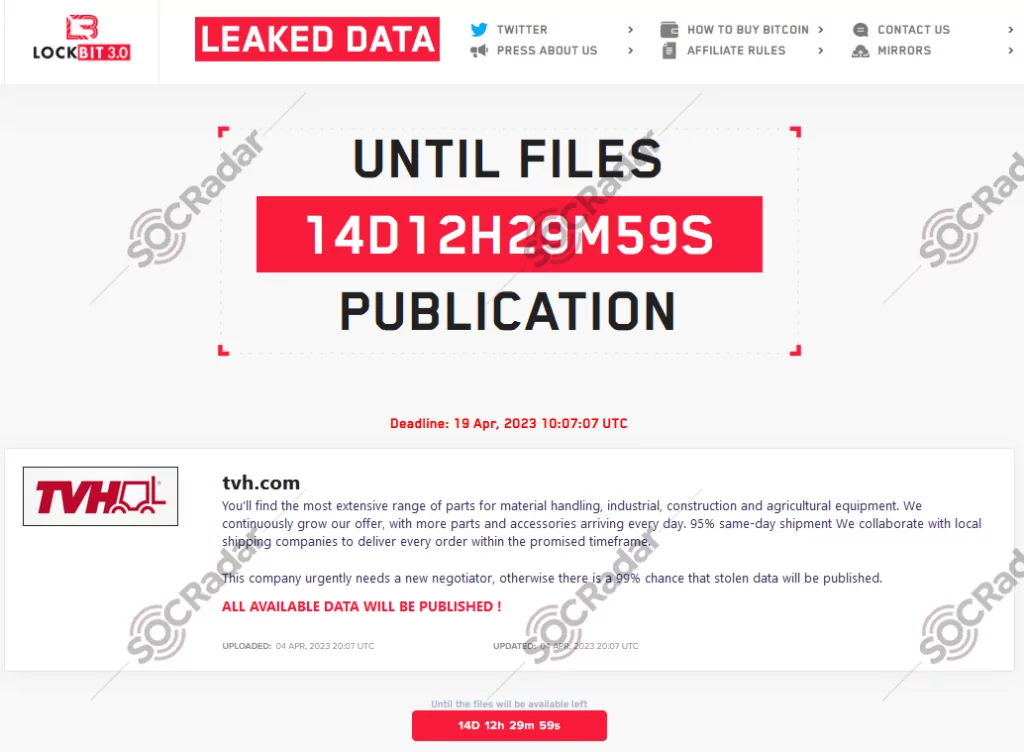
On April 4, a SOCRadar dark web researcher found a post that The LockBit ransomware group claimed responsibility for the cyber attack. Despite the absence of sample data from the company in the cybercriminals’ post, one of their statements indicated that TVH Parts Holding NV urgently requires a new negotiator; otherwise, there is a 99% chance that the stolen data will be released.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































