
Nestle Brazil Leak, Rakuzan RAT, Access Sales for Japan & UAE Companies
Embark on an exploration of the latest Dark Web revelations brought to light by the SOCRadar Dark Web Team. Last week’s findings include a leak involving Nestle Brazil, the sale of customer contracts from an Ecuadorian telecommunications company, the introduction of a new Remote Access Trojan called Rakuzan, the unauthorized sale of RDWeb access to a Dubai-based retailer, and the sale of unauthorized network access to a major Japanese automotive corporation, each presenting significant cybersecurity risks.
Receive a Free Dark Web Report for Your Organization:
Database of Nestle Brazil is Leaked
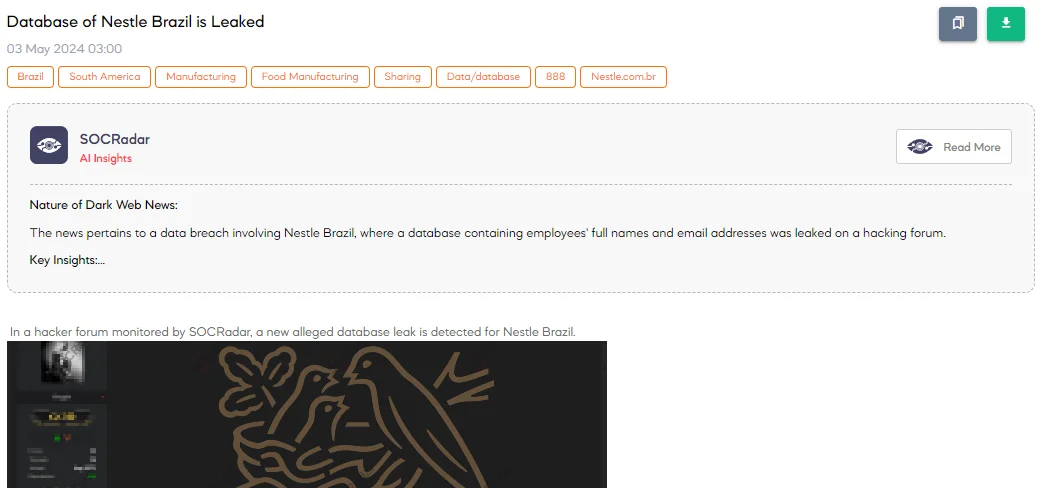
The SOCRadar Dark Web Team has detected a post on a hacker forum indicating a new alleged database leak concerning Nestle Brazil. According to the threat actor’s claim, the leak occurred in May 2024 and involves the personal information of employees. The compromised database reportedly contains full names and email addresses of Nestle Brazil employees, amounting to 4,409 lines of data.
Customer Contracts of Ecuadorian Telecommunication Company are on Sale
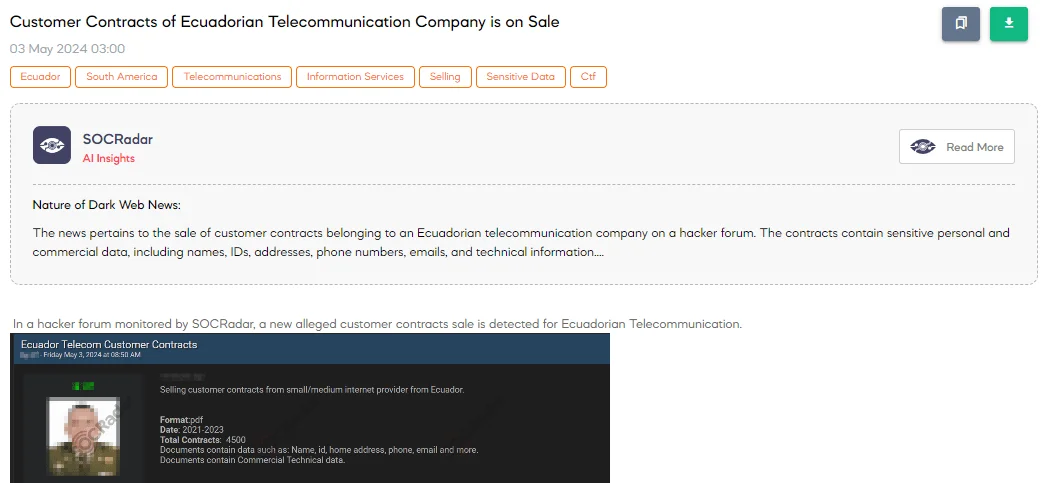
The SOCRadar Dark Web Team has identified a post on a hacker forum where a threat actor claims to be selling customer contracts from an Ecuadorian telecommunication company. According to the post, the contracts originate from a small to medium-sized internet provider in Ecuador, covering the years 2021 to 2023.
The threat actor advertises a total of 4,500 contracts in PDF format, which purportedly include personal and commercial technical data such as names, identification numbers, home addresses, phone numbers, emails, and more.
New Remote Access Trojan Rakuzan Offered on Hacker Forums
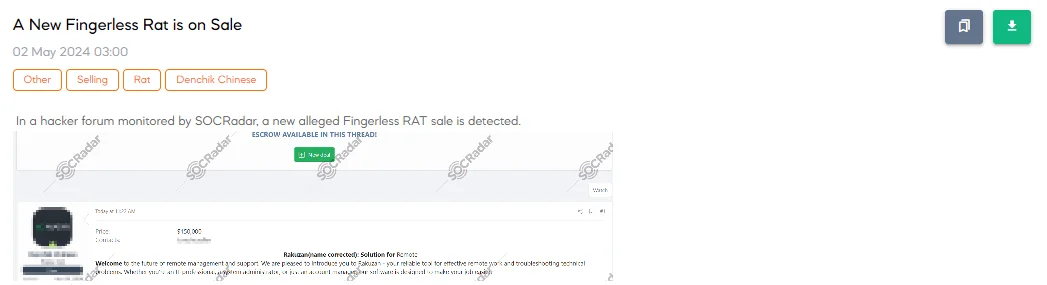
The SOCRadar Dark Web Team has uncovered a forum post advertising a new Remote Access Trojan (RAT) named “Rakuzan” for $150,000. Touted as a sophisticated tool for remote management, Rakuzan promises high-level encryption, platform versatility (Windows, macOS, Linux), and stealth operation without user detection. Key advertised features include interactive control for remote operations and a claim of complete invisibility on client systems. The sale and use of such tools pose serious ethical and legal concerns due to their potential for unauthorized surveillance and data theft.
Unauthorized RDWeb Access Sale is Detected for a United Arab Emirates Retail Company
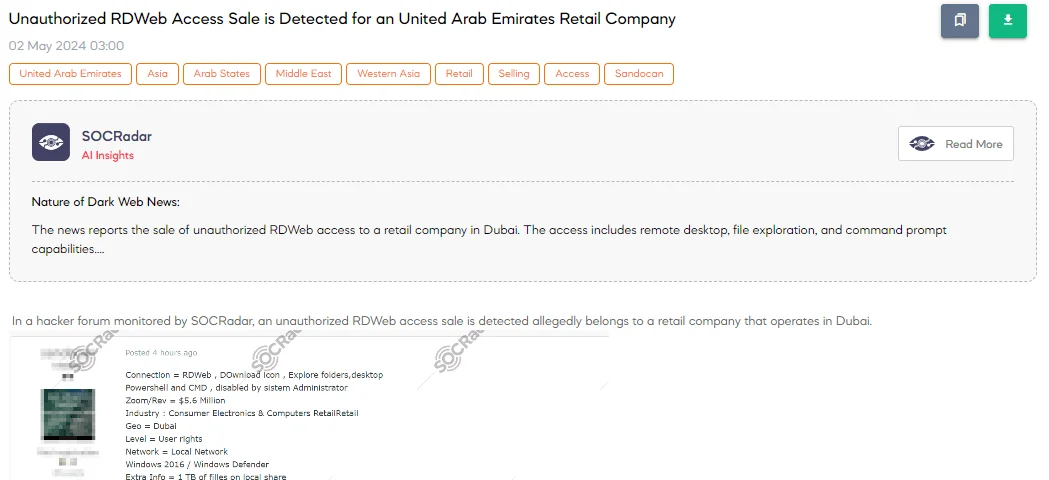
The SOCRadar Dark Web Team has identified a concerning post on a hacker forum where a threat actor alleges unauthorized RDWeb access for sale, which reportedly belongs to a consumer electronics and computers retail company based in Dubai.
The hacker details the RDWeb connection capabilities, noting that while PowerShell and CMD are disabled by the system administrator, users can still access download icons, explore folders, and use the desktop. The unauthorized access is claimed to include user rights on a local network running Windows 2016 with Windows Defender and contains an extra 1 TB of files on the local share.
Unauthorized Network Access Sale is Detected for a Japanese Automotive Company
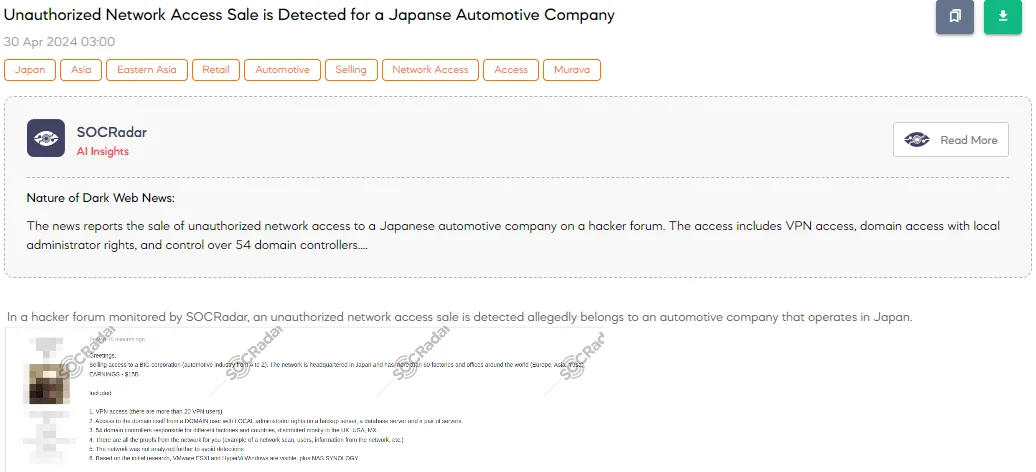
The SOCRadar Dark Web Team has detected a concerning post on a hacker forum where a threat actor claims to be selling unauthorized network access to a major Japanese automotive company. The company, described as a “BIG corporation” in the automotive industry, reportedly operates a network headquartered in Japan, with over 60 factories and offices globally, including in Europe, Asia, and the US.
The post outlines extensive unauthorized access to the company’s network, which includes VPN access with more than 20 users, local administrator rights on several critical servers, and control over 54 domain controllers across various global locations, including the UK, US, and Mexico. The threat actor also mentions having untouched parts of the network to avoid detection, alongside visible VMware ESXi and Hyper-V Windows systems, emphasizing that the sale is due to an inability to manage the large volume of data, rather than seeking cooperation.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































