New CISA Advisory: Threat Actors Exploited Adobe ColdFusion Vulnerability (CVE-2023-26360) to Target Government Servers
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a Cybersecurity Advisory (CSA), regarding exploitation of a vulnerability in Adobe ColdFusion, targeting government-related servers. The advisory aims to guide organizations in enhancing their security posture against the exploitation of this vulnerability by providing known Indicators of Compromise (IOCs) and Tactics, Techniques, and Procedures (TTPs).
About the Vulnerability in Adobe ColdFusion (CVE-2023-26360)
CISA cautions that unidentified threat actors have exploited an Adobe ColdFusion vulnerability within a Federal Civilian Executive Branch (FCEB) agency.
The vulnerability, identified as CVE-2023-26360, involves an improper access control issue impacting Adobe ColdFusion. CVE-2023-26360 allows attackers to execute arbitrary code, and holds a critical CVSS severity score of 9.8.
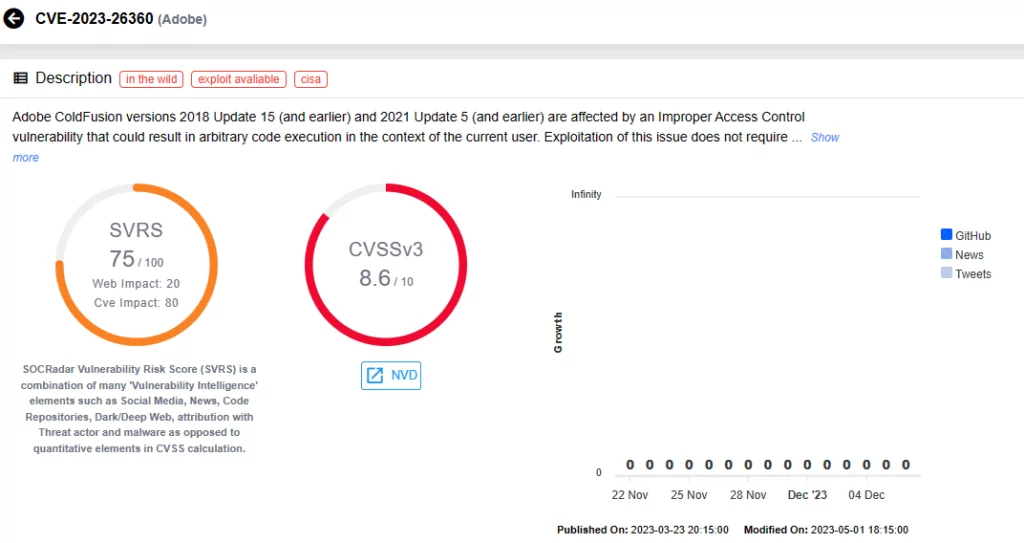
Versions affected by the vulnerability include:
- Adobe ColdFusion 2018 Update 15 (and earlier)
- Adobe ColdFusion 2021 Update 5 (and earlier)
- ColdFusion 2016 and ColdFusion 11 (These installations have reached End-of-Life, and will not receive updates)
CISA’s Report on the Adobe ColdFusion Vulnerability’s Exploitation
CISA reports that, after the affected agency’s investigation, network logs revealed the compromise of at least two public-facing servers between June and July 2023.
Threat actors exploited CVE-2023-26360, establishing an initial foothold on two agency systems, issuing commands on web servers and deploying malware. Microsoft Defender for Endpoint (MDE) identified the exploitation of outdated versions of ColdFusion in the agency’s pre-production environment.
Attackers’ primary focus was reconnaissance, mapping the network, with no evidence of successful data exfiltration or lateral movement. Attribution of the threat actors remains unknown.
The First Incident (June 26, 2023):
- The Intrusion: Exploiting CVE-2023-26360, threat actors gained entry to a public-facing web server from IP address 158.101.73[.]241, linked to a public cloud provider. They performed reconnaissance and executed other malicious activities.
The attack started with a specific URI (/cf_scripts/scripts/ajax/ckeditor/plugins/filemanager/iedit.cfc), targeting outdated software to exploit CVE-2023-26360, prompting the removal of the compromised asset within 24 hours of the MDE alert. Subsequent actions involved process enumeration, network connectivity checks, and obtaining information about the web server and its operating system, with specific checks for ColdFusion versions 2016 and 2018.
- The Attack Sequence: Threat actors traversed the filesystem, uploading artifacts to the web server, notably deleting a file named ‘tat.cfm’ before analysis. Using Certutil, they decoded conf.txt into a web shell (config.jsp), which was also deleted, possibly for evasion. Threat actors interacted solely with the config.jsp web shell from this point on.
HTTP POST requests were directed at config.cfm, a standard Adobe ColdFusion configuration file. The file contained inserted malicious code designed for ColdFusion versions 9 and earlier, with the intent to extract usernames, passwords, and data source URLs, signaling a potential avenue for future malicious activities. Additionally, the file included code for uploading additional files, and the source remained unidentified.
- Evasion Techniques: Evasion attempts involved running attrib[.]exe to hide config.jsp, yet no evidence of successful execution was found. Failures in executing files like tat.cfm and config.jsp were observed, due to syntax errors. Files created in the C:IBM directory (a staging folder for malicious activity) were considered tools employed by the attackers, but were not found on the server, as they were likely deleted by them.
CISA recommends thorough investigation of files for compromise signs before remediation. Caution is urged for two legitimate Microsoft files, observed in malicious use.
Malicious code discovered in this incident aimed to decrypt ColdFusion data source passwords, but the decryption code failed due to the server’s use of a newer version, incompatible with the default hard-coded seed value for older versions.
The Second Incident (June 2, 2023):
- The Intrusion: Threat actors gained a foothold on a web server running Adobe ColdFusion v2021.0.0.2, exploiting CVE-2023-26360 through IP address 125.227.50[.]97.
- The Attack Sequence: Utilizing nltest commands, the actors enumerated domain trusts to identify lateral movement opportunities. Further reconnaissance involved collecting information on local and domain administrative user accounts through commands like localgroup, net user, and ID. Host and network reconnaissance efforts were further conducted to discover network configuration, time logs, and query user information.
The threat actors dropped a Remote Access Trojan (RAT), d.txt (decoded as d.jsp), and eight malicious artifacts via POST command. D.jsp, identified as a modified version of a publicly available web shell code, established persistence and communicated with the actor-controlled server for actions. Regular network connectivity tests were conducted by pinging Google’s DNS, and additional reconnaissance efforts were made by searching for the uploaded .jsp files.
- Unsuccessful Attempts: Efforts to exfiltrate registry files were thwarted, and malicious files, including a LSASS dump file containing user accounts, were detected and quarantined. Threat actors also attempted to use security tools present on the victim server, including esentutl.exe for a registry dump. Attempts to download data from the threat actors’ command and control (C2) server were also observed but blocked and logged by the victim server. Attempts to access SYSVOL for policy changes were also unsuccessful. CISA warns that if these attempts had succeeded, the threat actors might have been able to alter policies across compromised servers.
During this incident, threat actors likely accessed data in the ColdFusion seed.properties file through the web shell interface. The file contains seed values for password encryption/decryption; however, no evidence suggests attempts to decode passwords.
Recommendations
It is always advised to promptly manage software updates, giving priority to patching vulnerabilities that are under active exploitation. CISA also underscores the importance of prioritizing secure configurations, such as eliminating default passwords and adopting Single Sign-On (SSO) technology through modern open standards.
Further recommendations by CISA involve the deployment of network segmentation based on role and functionality to prevent lateral movement, implementing the principle of least privilege to restrict threat actors’ access to crucial network resources, restricting file and directory permissions, and managing NTLM authentication policy settings to limit incoming NTLM traffic from client computers, member servers, or a domain controller, enhancing overall security.
You can review the CISA advisory here for additional information, guidance, as well as IOCs and MITRE ATT&CK TTPs related to the Adobe ColdFusion vulnerability (CVE-2023-26360).
How Can SOCRadar Help?
By leveraging SOCRadar’s Attack Surface Management (ASM), you can actively monitor emerging vulnerabilities across your digital assets and receive timely threat alerts, which can help streamline your organization’s patching efforts to effectively mitigate potential impacts.
Explore SOCRadar’s Vulnerability Intelligence to obtain valuable insights into hacker trends, access detailed information and updates about specific vulnerabilities, and their SVRS score (SOCRadar Vulnerability Risk Score). The SVRS score provides a comprehensive understanding of a vulnerability’s popularity and its likelihood of exploitation, offering a valuable insight.