Next.js Middleware Vulnerability (CVE-2025-29927): What You Need to Know and How to Respond
A critical security flaw has recently shaken the Next.js ecosystem, bringing urgent attention to the framework’s middleware feature. Tracked as CVE-2025-29927, this vulnerability potentially affects millions of applications built using Next.js, one of the most popular frameworks for full-stack React development.
What is CVE-2025-29927?
The CVE-2025-29927 (CVSS 9.1) vulnerability lies in an authorization bypass flaw in Next.js middleware. Middleware functions are designed to intercept incoming HTTP requests, often used to implement access control, session validation, redirects, or security headers. Unfortunately, this vulnerability allows attackers to slip past these critical security checks.
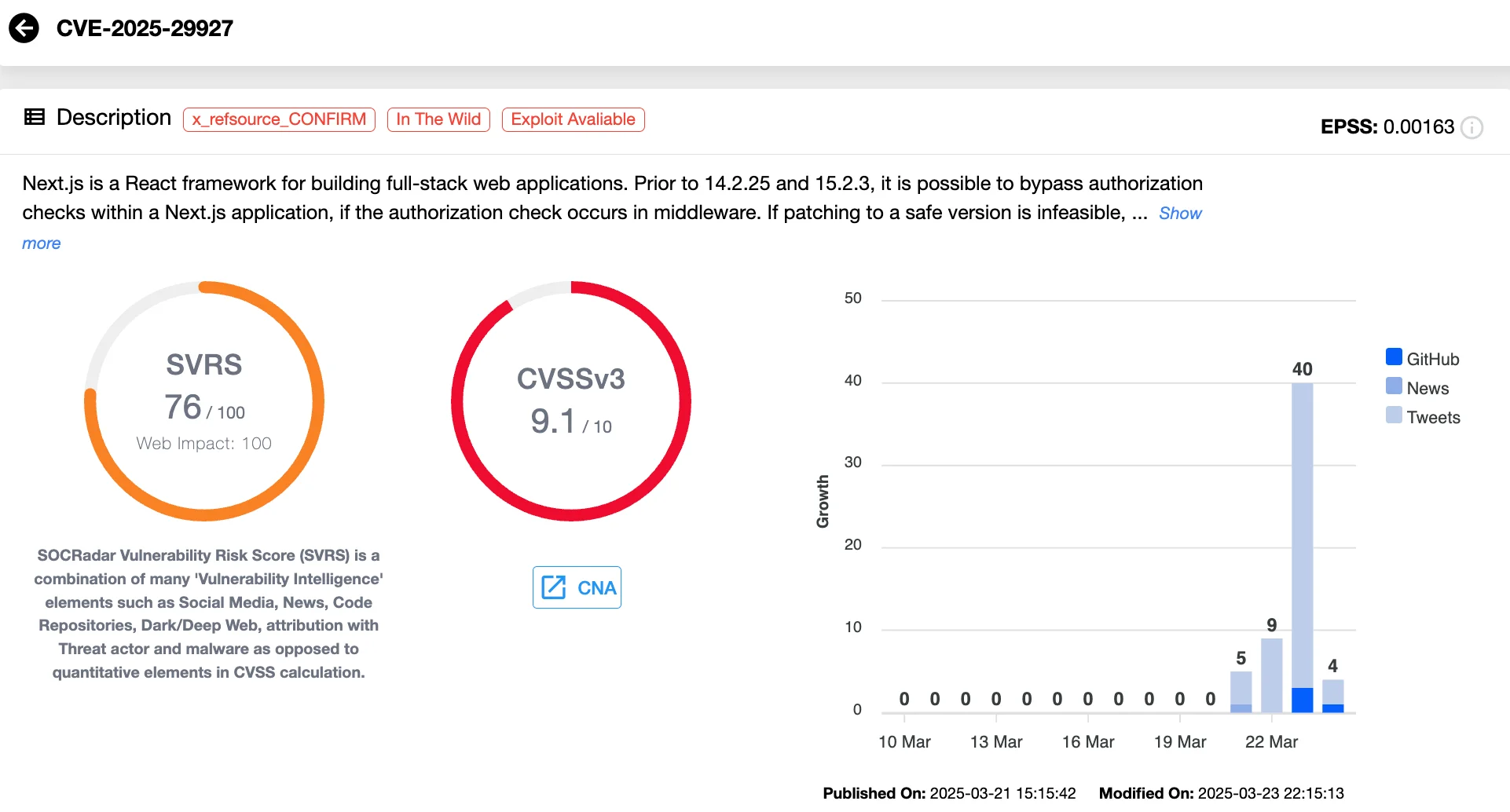
Vulnerability card of CVE-2025-29927 (SOCRadar Vulnerability Intelligence)
The exploit hinges on a crafted HTTP request containing the x-middleware-subrequest header. When used with certain values, this header tricks the application into skipping authorization logic that developers assumed was safely handled at the middleware level.
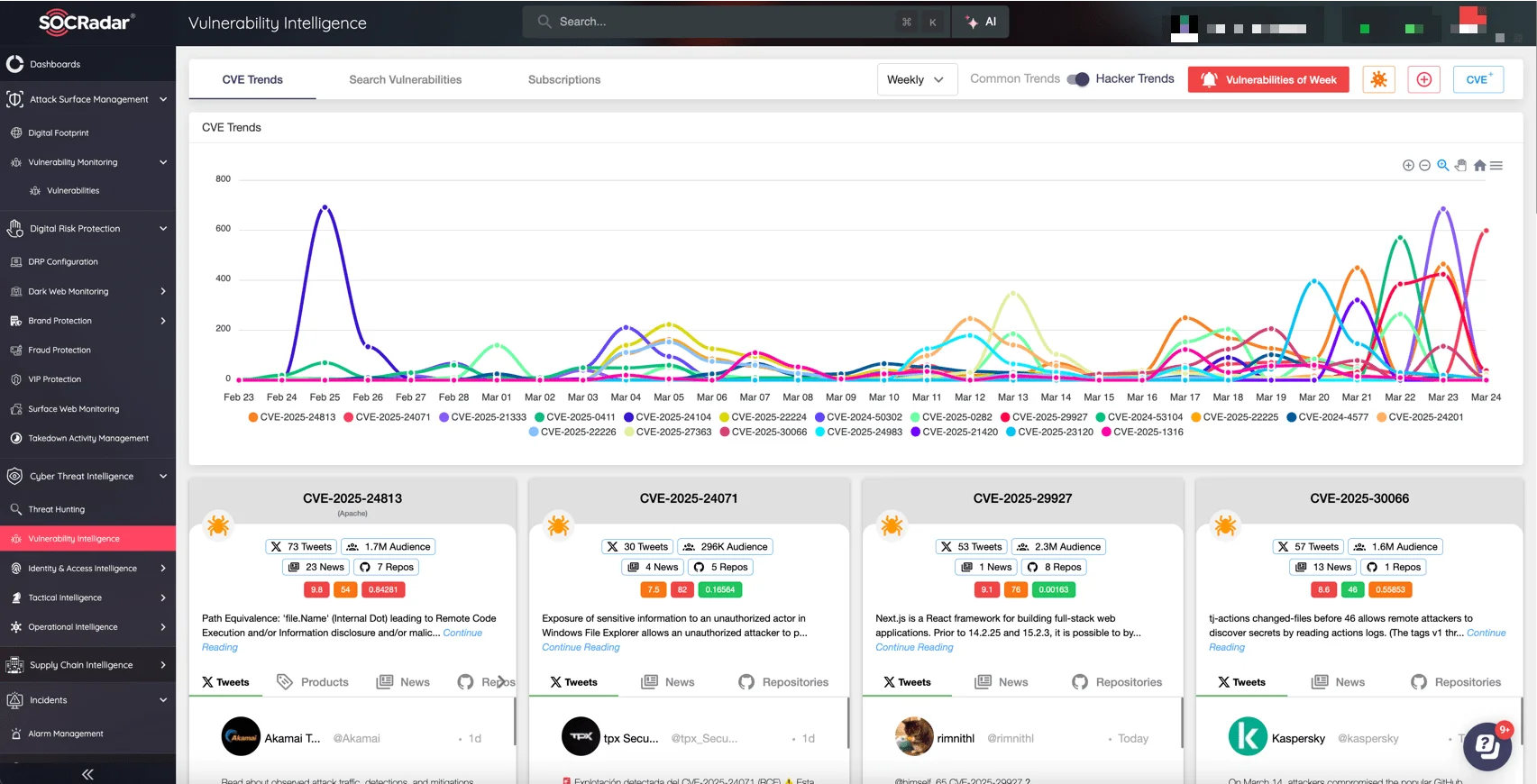
SOCRadar’s Vulnerability Intelligence
To proactively track vulnerabilities like CVE-2025-29927, leverage SOCRadar’s Vulnerability Intelligence within the Cyber Threat Intelligence module. This powerful feature delivers timely alerts about newly disclosed vulnerabilities, along with actionable context on real-world exploitation. Accurately prioritize remediation based on active threats rather than generic severity scores, enabling your security teams to effectively manage risks and mitigate vulnerabilities before attackers exploit them.
Impacted Versions and Exploit Mechanics
All Next.js versions from 11.1.4 through 13.5.6, and unpatched versions of 14.x and 15.x, are vulnerable. Specifically, any application that relies on middleware for authorization checks is at risk.
The mechanics differ slightly across versions:
- Legacy versions (pre-12.2) are vulnerable when the header is set to:
x-middleware-subrequest: pages/_middleware - Modern setups are exploited using repetitive patterns like:
x-middleware-subrequest: middleware:middleware:middleware…
(or src/middleware:… if using a source directory structure)
This simple yet powerful technique gives threat actors the ability to access protected routes and perform unauthorized actions.
Why CVE-2025-29927 Is Dangerous
Next.js is downloaded nearly 10 million times weekly and powers applications across various sectors and even Web3. Middleware is frequently treated as a trusted gatekeeper in edge security models, making this flaw especially dangerous. Here’s why CVE-2025-29927 is dangerous:
- No authentication required for the exploit.
- Silent bypass of logic developers trust for access control.
- Severe consequences, from data breaches to disruption.
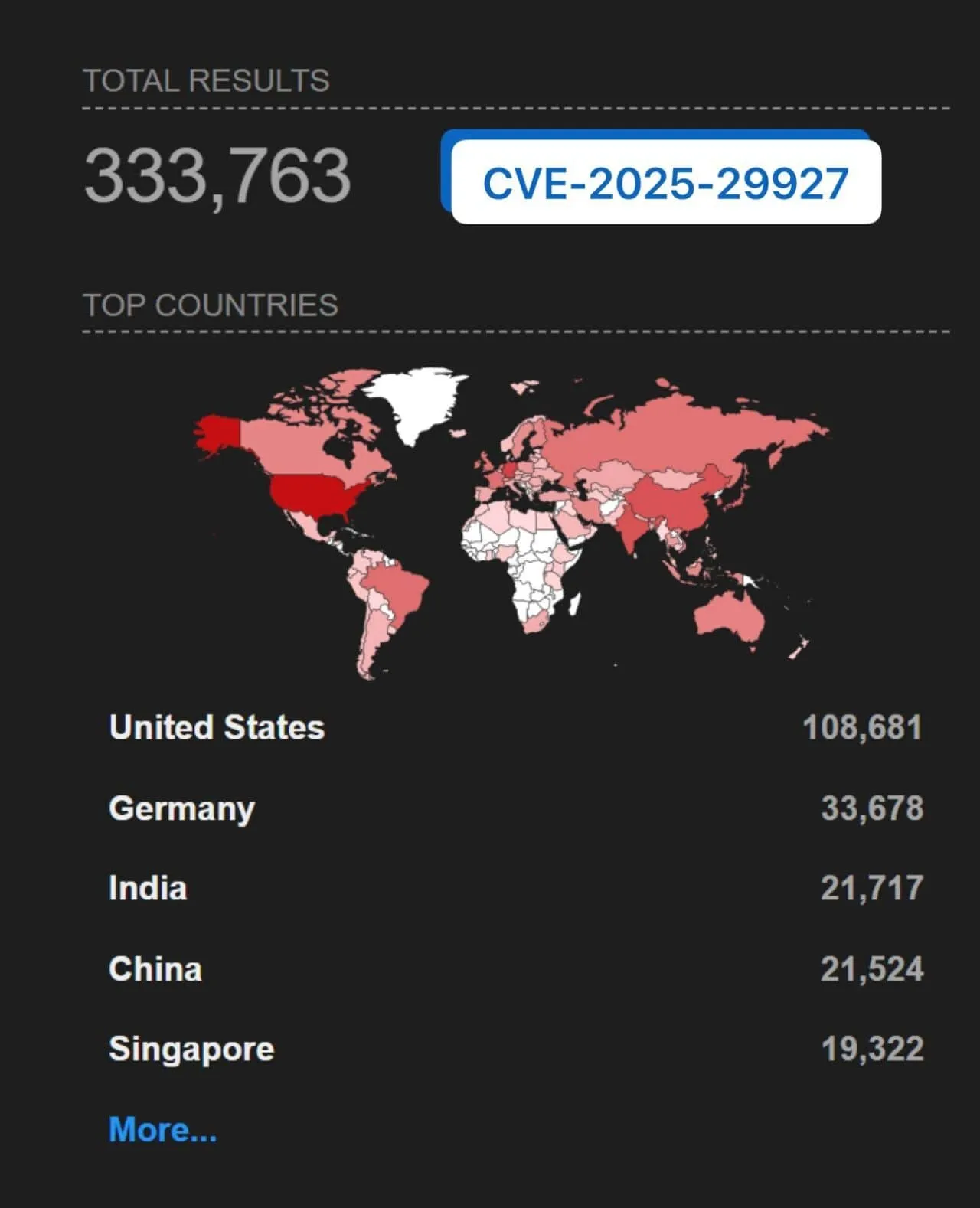
Shodan results reveal over 330,000 internet-facing instances potentially exposed, with the highest concentration in the United States.
How to Mitigate the Threat
Immediate action is essential. The Next.js team has released patches addressing the issue in the following versions:
- 15.x → Update to 15.2.3 or later
- 14.x → Update to 14.2.25 or later
Versions 11.1.4 through 13.5.6 remain unpatched.
If upgrading isn’t currently feasible, a temporary workaround is to block external requests containing the x-middleware-subrequest header, but this should be done at the edge or proxy level, not within the application middleware itself. Blocking this header helps reduce exposure but may interfere with legitimate internal operations.
Here is a summarized list of recommendations:
- Audit your current version of Next.js and upgrade if necessary.
- Review middleware usage, particularly where access control is enforced.
- Monitor logs for suspicious requests containing the x-middleware-subrequest header.
- Update threat models to reflect the limitations of middleware-based security.
- See the official advisory here.
For organizations managing broad digital footprints, tools like SOCRadar’s Vulnerability Intelligence and Attack Surface Management can help identify and monitor affected assets across your infrastructure.
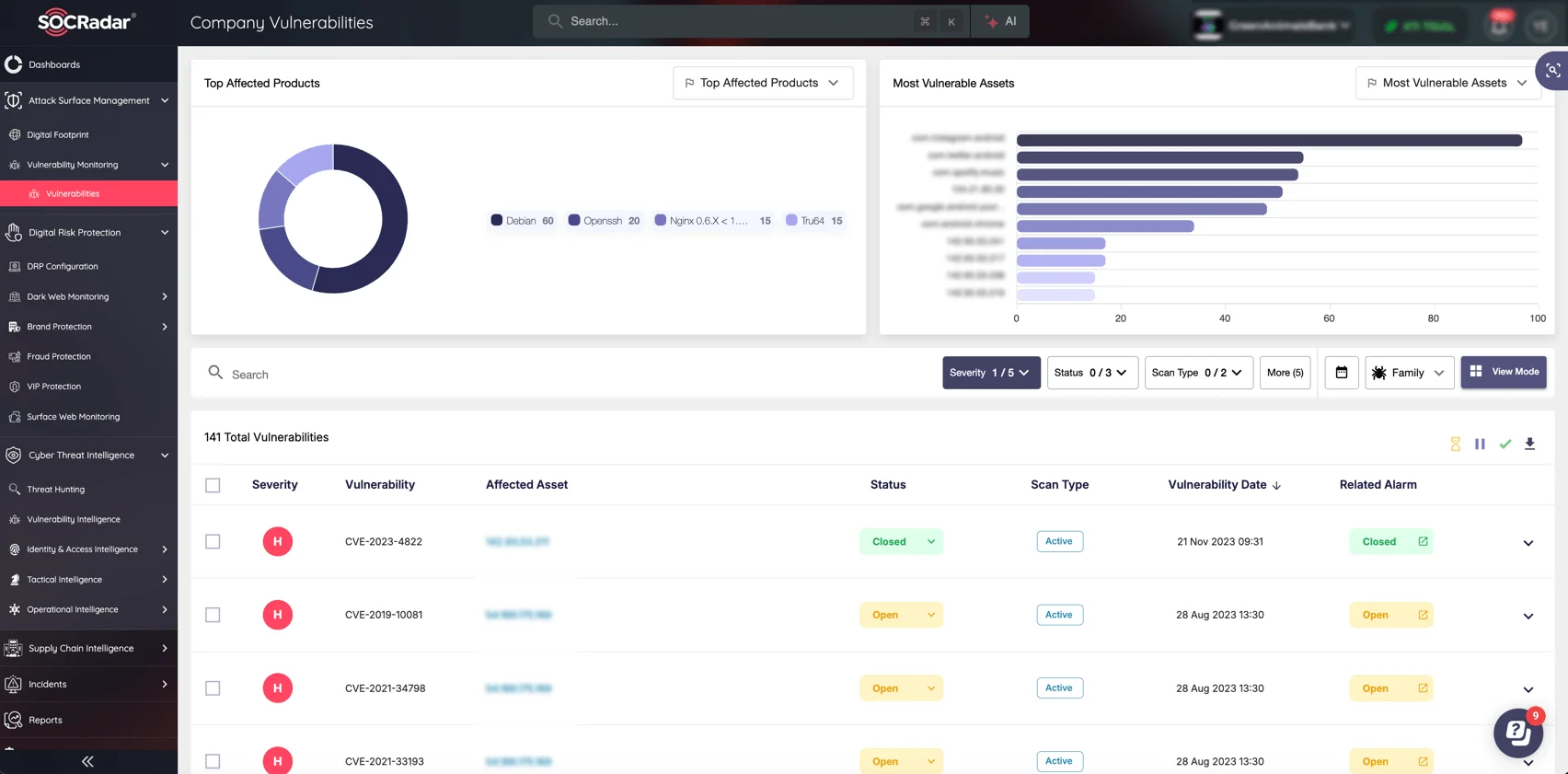
Proactively identify exposed Next.js applications and swiftly prioritize remediation efforts, securing your organization against vulnerabilities like CVE-2025-29927 before attackers can act. (SOCRadar’s ASM)
SOCRadar’s Attack Surface Management (ASM) module helps you quickly pinpoint your organization’s externally exposed assets, including web applications running vulnerable versions of Next.js. It provides continuous visibility into your digital footprint, automatically discovering outdated software, open ports, misconfigurations, and potential entry points attackers can exploit.