NPM Packages Used In A Supply Chain Attack
Hundreds of desktop applications and websites were compromised by an NPM supply chain attack that started in December 2021, using malicious NPM packages with obfuscated Javascript code.
Researchers from ReversingLabs found that the attackers (named IconBurst) impersonated popularly used NPM packages like umbrellas and ionicons by using the typosquatting technique, which is done by choosing names that are similar to the official package names or using common typos.
It is also worth noting that similar naming has been used for some exfiltration domains, which suggests this supply chain attack campaign might have been the work of the same threat actor/s all along.
The Malicious Packages Exfiltrate Data
ReversingLabs said in their blog: “The presence of a javascript obfuscator was the indicator that initially got our team looking at a wide range of NPM packages.” As a result, more malicious packages that used the same obfuscation were discovered.
The packages’ deobfuscated content revealed a pattern. The malicious packages used jQuery ajax() functions to steal form data. Some of these packages used altered parts to exfiltrate the data to malicious domains belonging to threat actors. These functions perform target filtering checks by validating the URL content before exfiltrating the data.
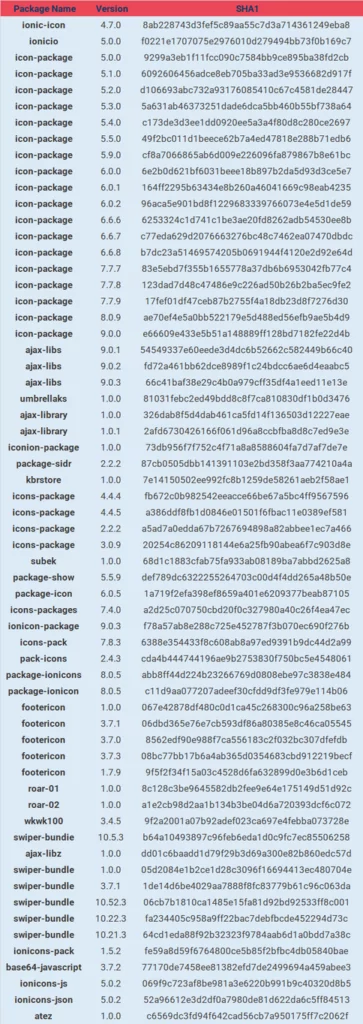
NPM accounts published the malicious packages with the names ionic-io, arpanrizki, aselole, and kbrstore.
Ten of the most downloaded packages are listed below:
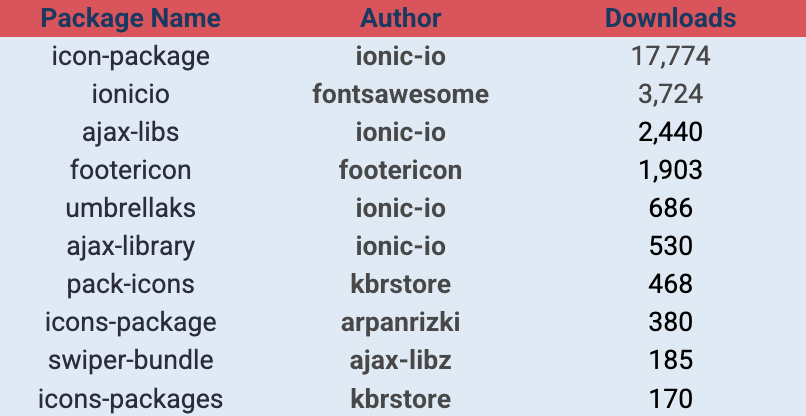
One Package Has Over 17,000 Downloads
The top downloaded package is icon-package by ionic-io; with nearly 18,000 downloads, it impersonates the popular icon set ionicons.
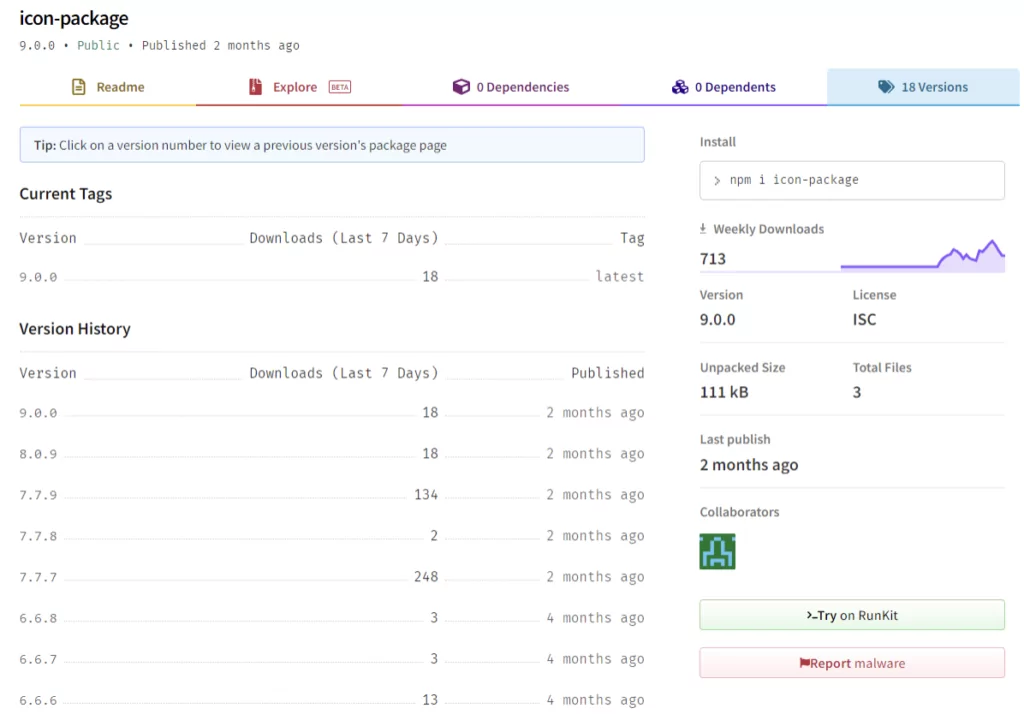
This package’s data exfiltration method uses the https://ionicio[.]com domain, a fake site that closely resembles the official ionicons website ionic.io.
When this campaign started is yet to be found, but an older malicious package from December 2021 with the same exfiltration functionality has been observed. It is by font-awesome. The domain used for data exfiltration in fontsawesome’s containers (https://graph-googleapis[.]com) is the same as in the two oldest versions of the icon package.