
Operational Technology (OT) and Cybersecurity: Safeguarding Critical Infrastructure
Operational Technology (OT) encompasses hardware and software capable of detecting or inducing alterations in industrial equipment, assets, processes, and events directly. It highlights the technological and functional distinctions from traditional Information Technology (IT) systems, emphasizing the industrial control systems environment.
Industrial Control Systems (ICS) represent a fundamental element of Operational Technology (OT), extensively employed across various critical industries and automation frameworks. Consequently, cybersecurity solutions have become imperative within this technological domain.
A case occurred in 2010 with Stuxnet, a significant event demonstrating the intricacy and potential risks associated with OT through an attack on industrial devices. Therefore, the importance of OT security came to light with the Stuxnet incident, which can be considered the first major attack on critical systems.
Security for Critical Industries (Image: Bing AI)
Incidents like these in critical industry security, seen in the New York Dam, Florida Water Treatment, and Colonial Pipeline attacks, have recurred and continue to do so, even during the Israel-Hamas conflict in 2023. However, before asking questions such as what are critical industries, ICS, and SCADA, we need to look at the concept of Operational Technology (OT).
What is Operational Technology (OT)?
While the interpretation of critical infrastructures may vary across nations, they typically encompass physical and digital assets, systems, and networks whose compromise in terms of accessibility, confidentiality, and integrity could result in loss of life, national security risks, public disorder, and significant economic harm.
These infrastructures, including power generation and distribution, water and wastewater facilities, healthcare services, financial institutions, transportation systems, and food and agriculture sectors, play indispensable roles in contemporary society.
They are intricately interconnected, meaning an attack on any one of them can have ripple effects on others, potentially leading to societal turmoil. Thus, OT is a huge part, especially for these sectors.
OT (Operational Technology) and IT (Information Technology) appear as two pillars in the foundations of modern life. Although IT is a concept we often hear about, the same is not yet true for OT. But from a security perspective, it may be even more critical.
Operational technology (OT) systems utilize similar tools to IT environments but are tailored for different purposes, mainly interacting with other machines such as Industrial Control Systems (ICS) to ensure their proper functioning and meet stringent uptime requirements.
Traditionally, IT and OT networks operated separately, with OT systems often running legacy software and being “air-gapped” from the internet and IT networks to protect against cyber threats.
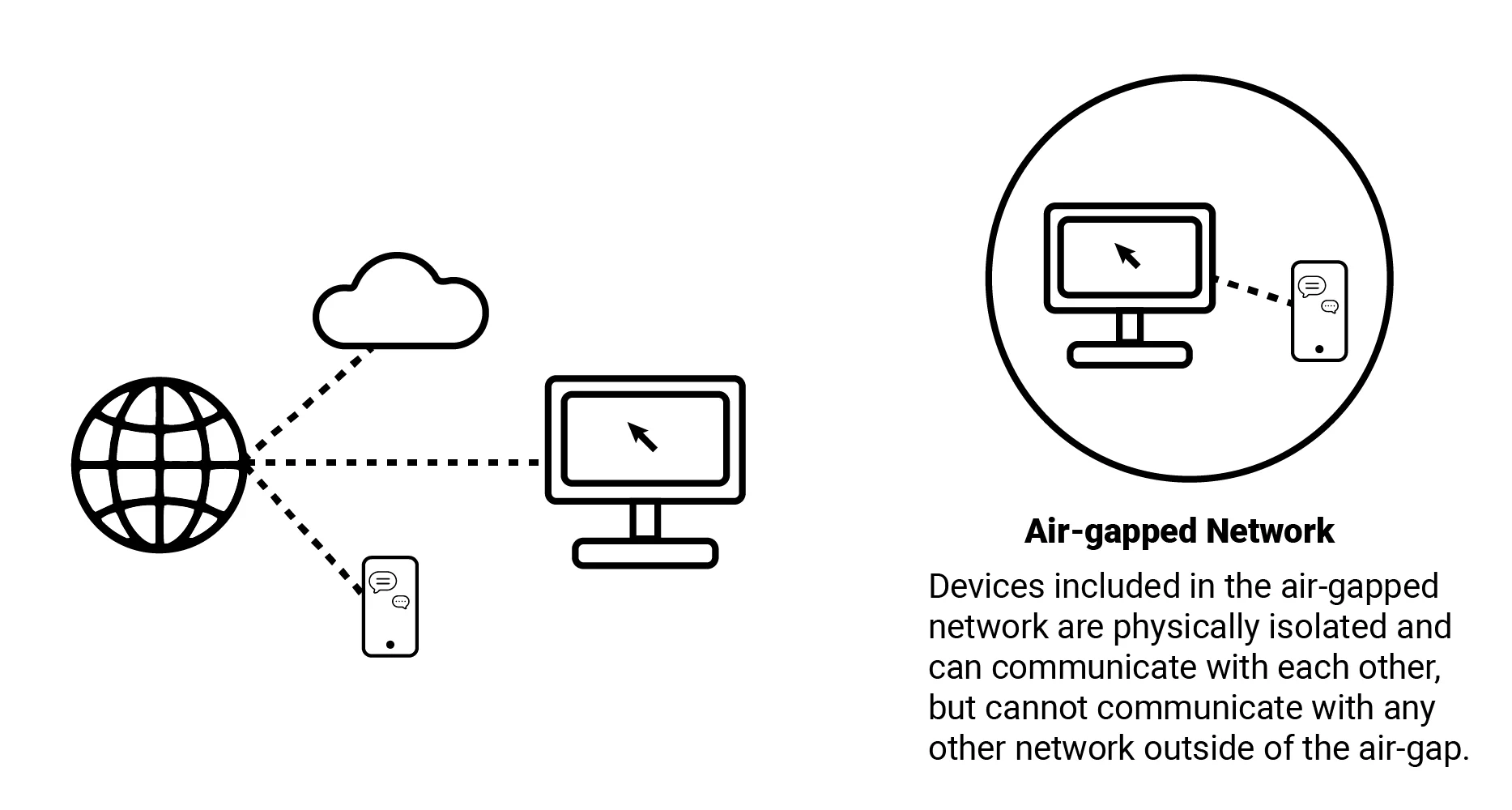
An air-gapped network is typically completely divided by outer networks in physical methods. Therefore, only via a human operator these systems communicate with other networks. (Image: Belden)
However, the advent of the Industrial Internet of Things (IIoT) has led to the dissolution of this air gap, enabling remote monitoring and management of industrial processes. Consequently, bridging this physical network disconnect has become essential, necessitating specialized Operational Technology (OT) and IoT security solutions.
What are the Information Technology (IT) & Operational Technology (OT) Differences?
Operational Technology (OT) security addresses the unique requirements of OT environments, prioritizing system availability and understanding OT-specific protocols while mitigating targeted attacks and malware infections.
OT systems have prolonged life cycles compared to IT systems, often spanning decades, presenting challenges in maintaining security measures for outdated infrastructure. Additionally, some OT systems are heavily regulated, further complicating security management.
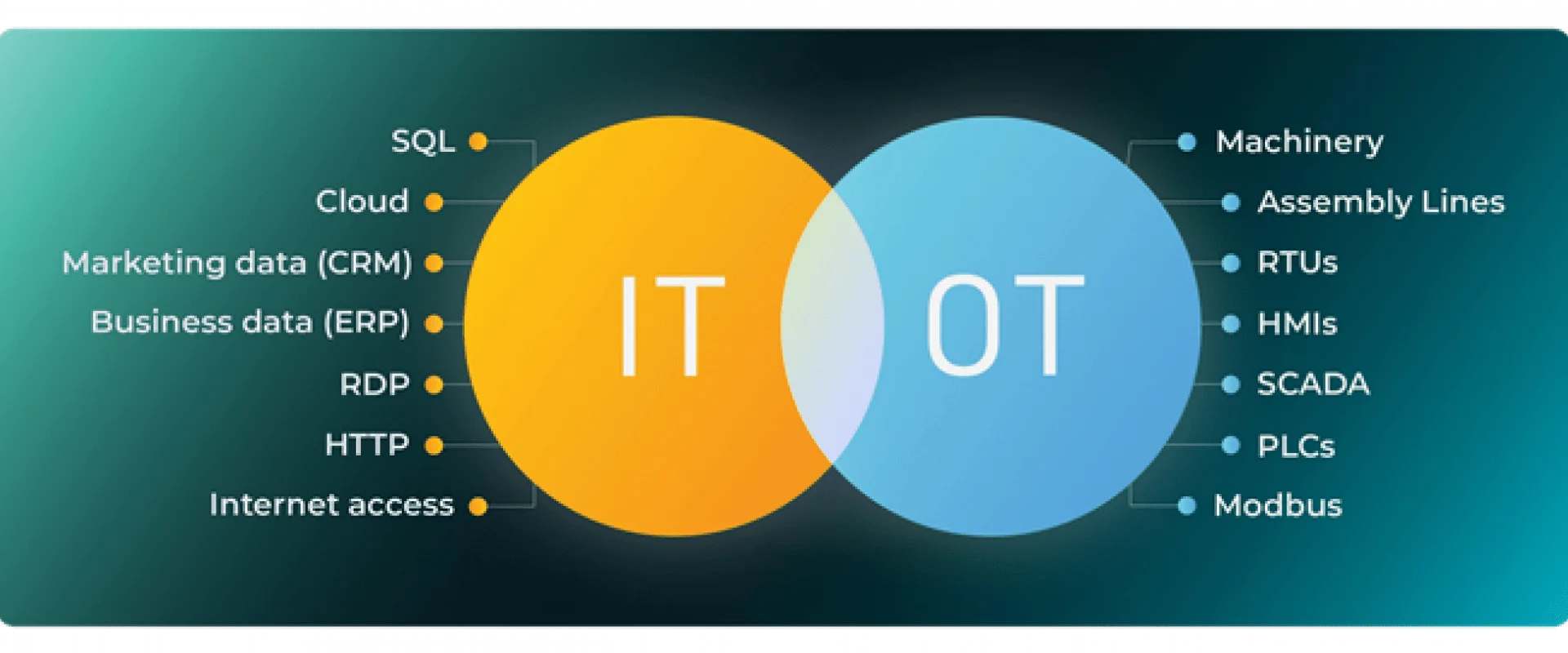
IT/OT Components (Image:ZippyOps)
As OT assets increasingly connect to the internet, they become susceptible to web-borne threats, posing significant risks to Industrial Control Systems (ICS) and potentially leading to severe consequences for organizations.
What are the Operational Technology (OT) Components?
Operational Technology devices are utilized in industrial environments and critical infrastructure sectors. The components of OT and industrial networks form a powerful ecosystem for industrial control and monitoring.
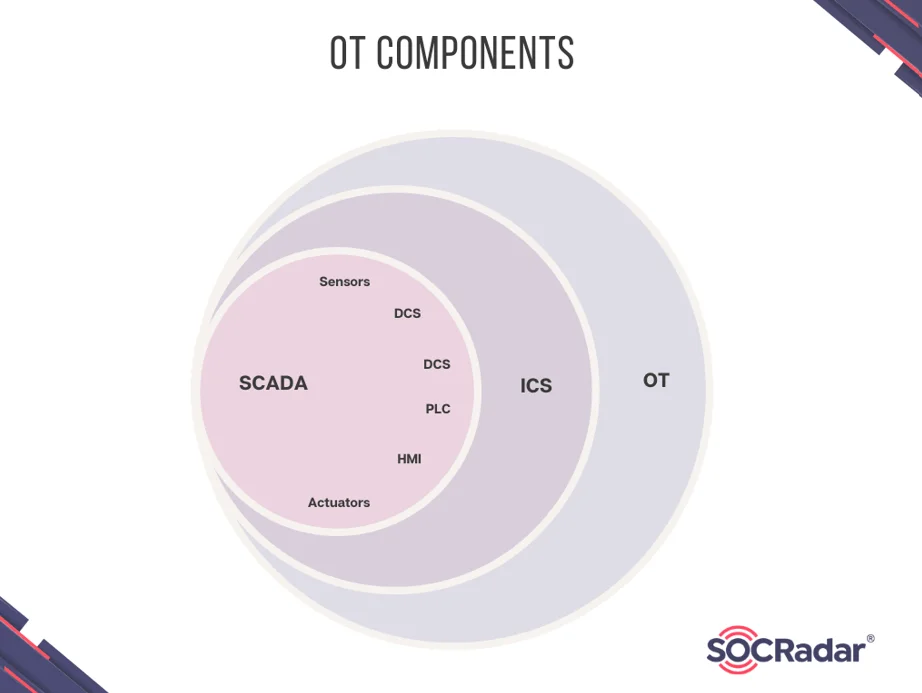
Simplified Operational Technology (OT) Components
Industrial Control System (ICS):
Industrial Control System (ICS) serves as an overarching term covering both SCADA (Supervisory Control and Data Acquisition) and DCS (Distributed Control System). ICS networks are capable of monitoring various infrastructure and raw material systems. The reliability and immediate availability of ICS networks are paramount, setting them apart from IT systems.
Supervisory Control and Data Acquisition (SCADA) Systems:
SCADA systems bridge the gap between physical processes and digital control, providing real-time monitoring and control capabilities. SCADA systems offer a holistic view of industrial processes by integrating sensors, data acquisition devices, PLCs or Remote Terminal Units (RTUs), supervisory computers, and communication networks. They collect data on parameters such as temperature, pressure, flow rate, and more, enabling operators to make informed decisions.

A SCADA System (Image:TBMEndustri)
SCADA systems find applications in various industries, including energy distribution, manufacturing, and transportation. For instance, they monitor and control power grids, optimize production lines in manufacturing facilities, and manage traffic flow in intelligent transportation systems.
Distributed Control Systems (DCS):
DCS provides comprehensive control and monitoring capabilities across complex, continuous process industries. DCS enables real-time management of multiple variables by utilizing dedicated controllers dispersed throughout a plant or control area.
With advanced control algorithms, data logging, and alarm management features, DCS is essential in critical infrastructures. Petrochemical plants rely on DCS to efficiently control chemical processes, oil and gas industries utilize DCS for remote monitoring of drilling operations, nuclear power plants employ DCS for safe and reliable power generation, and water management systems use DCS to distribute and treat water resources efficiently.
Programmable Logic Controllers (PLCs):
PLCs are the workhorses of industrial automation and control systems. Designed to withstand challenging environmental conditions, including extreme temperatures and exposure to contaminants, PLCs offer exceptional reliability. They comprise a Central Processing Unit (CPU), input/output (I/O) modules, memory, and communication ports.
Programmable Logic Controller (Image:MROElectric)
PLCs are highly flexible and customizable, making them suitable for various industrial applications. For instance, PLCs automate assembly lines in manufacturing plants, precisely control robotic machines, and optimize wastewater treatment processes for enhanced environmental sustainability.
Human-Machine Interface (HMI):
Human-Machine Interface (HMI) is an interactive platform for operators to monitor and control industrial processes. It visually represents the system, displaying real-time data, control panels, and alarms. Operators can easily monitor process status, adjust control parameters, and receive notifications for efficient troubleshooting. HMIs also offer data analysis and reporting tools, empowering operators to optimize process performance.

Kinco HMIs (Image:AnaheimAutomation)
Even if the examples above do not include all of the components, the main frame is formed in this way, so how do we protect these systems?
What are the Challenges in Operational Technology (OT) Security?
The Operational Technology (OT) systems encounter various security vulnerabilities, including malware infiltration, human error, lack of visibility, outdated software, and insecure remote access. Malware can infiltrate systems through phishing emails, infected removable media, or unpatched software vulnerabilities, while human error, such as clicking on malicious links or opening infected attachments, can also grant attackers access to OT systems. Lack of visibility, outdated software, and insecure remote access are other significant contributors to OT security vulnerabilities.
As we mentioned before, availability is prioritized in these systems, which sometimes leads to many security vulnerabilities. Even Firewall and EDR devices typically cannot be installed on these control devices; Products that are not updated also contribute to this problem.
A report in the UK from last year showcases the challenges in a broad sense. As stated by the report, In 2020, there was a staggering 2,000% increase in incidents targeting Operational Technology (OT) and Industrial Control Systems (ICS). According to the 2022 IBM Security X-Force Threat Intelligence Index, manufacturing emerged as the most targeted industry globally, surpassing finance and insurance for the first time in five years. Equally troubling, research conducted by Make UK, a manufacturers’ organization, and BlackBerry unveiled that 65% of the UK’s manufacturers surveyed encountered production stoppages following successful cyberattacks.
Top challenges were as follows:
- Maintaining legacy IT (44.6%)
- Limited cybersecurity skills within the business (37.5%)
- Providing access to third parties for remote monitoring and maintenance (33%)
- Understanding IT security versus OT security (26.8%)
- No single tool or sensor can provide visibility into all threats (25%)
Even though they have very broad categories above, the problems kinda continue on the same issues in 2023 and 2024.
Example Case: Attack on US Critical Infrastructure
In recent months, the hack on Unitronics Programmable Logic Controller (PLC) represents an Iranian nation-state (IRGC) supply chain attack targeting multiple critical infrastructures in the US. This IRGC operation focused on exploiting Unitronics PLCs through their customers, with the intent of harming both Unitronics and Israel.
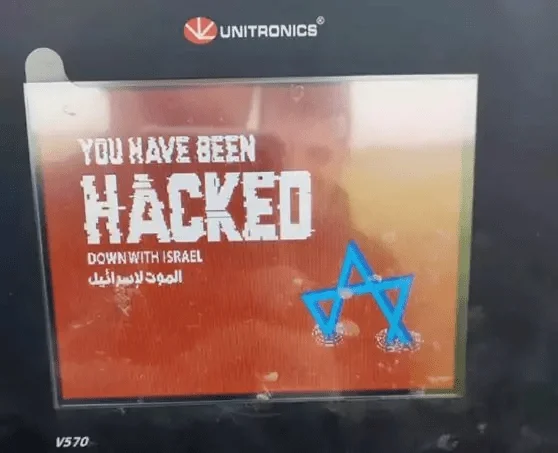
A defaced Unitronics product
The defacement of PLCs, while historically indicative of symbolic gestures by the IRGC, could potentially mask more malicious activities, such as the insertion of new code or the compromise of existing code for future attacks.
Default password vulnerabilities pose significant challenges in control system security, as PLCs are often shipped with default passwords that users neglect to change. This practice, prevalent across both IT and OT industries, exposes security risks, as demonstrated by CVE-2023-6448, highlighting the alleged insecurity of Unitronics Vision Series PLCs and HMIs due to default administrative passwords.
Although Unitronics recommended changing default passwords, authorities initially treated the issue as solely a Unitronics problem, even disclosing the default password to the public. However, the root of the problem lies in user oversight rather than a flaw in the product itself. The persistent exploitation of default passwords underscores the urgency for vendors and end-users to address this security weakness across all PLCs.
In summary, these products may harbor vulnerabilities, and numerous user-related incidents occur, making device protection challenging. Understanding how threat actors target this attack surface can inform effective defense strategies.
How Threat Actors Target ICS
The MITRE ATT&CK® framework has a different matrix for ICS, and become well-established in industrial automation networks, aiding in the comprehension of more intricate attack campaigns.
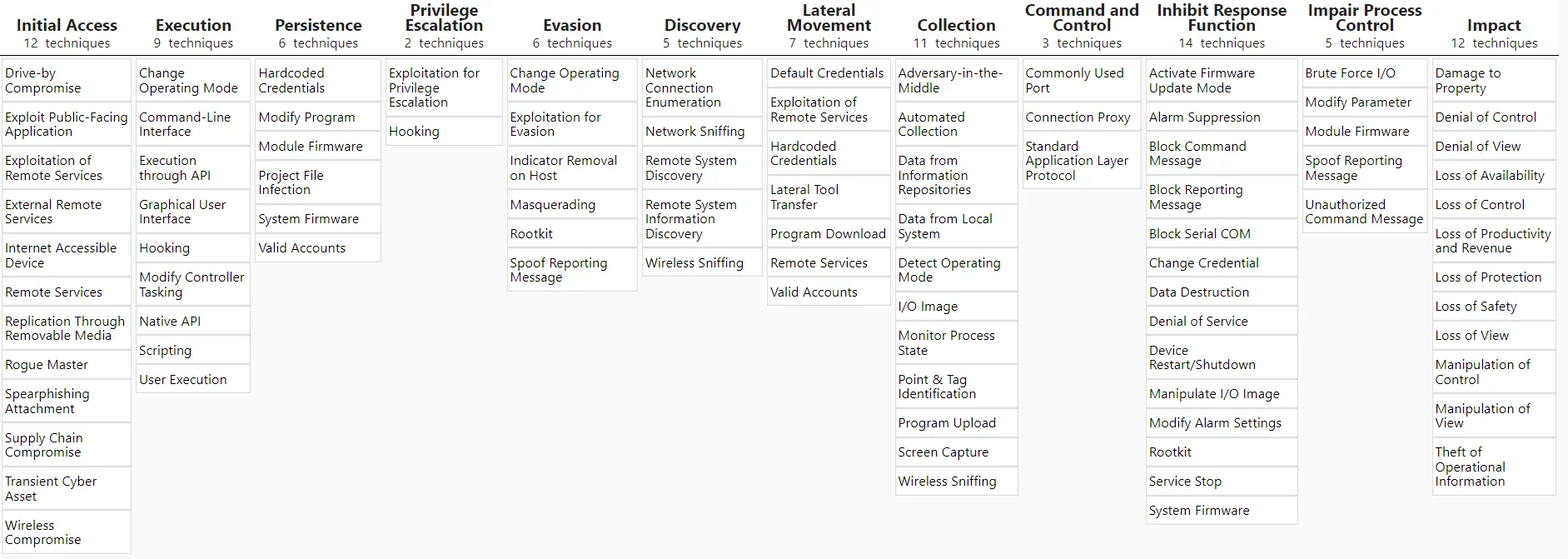
MITRE ATT&CK® Matrix for ICS (MITRE)
Traditional approaches to securing OT/ICS often fall short in addressing evolving threats. Yet, organizations equipped with insights into cyber actors’ Tactics, Techniques, and Procedures (TTPs) can prioritize their defenses effectively.
Cyber actors meticulously plan and execute intrusions into critical infrastructure control systems. As CISA states, their playbook typically unfolds in several stages:
Establishing Intended Effect and Selecting Targets: Malicious actors, ranging from cyber criminals to state-sponsored entities, have diverse motives, from financial gain to political or military objectives. Target selection depends on the desired effect, such as disrupting operations or causing psychological impact.
Collecting Intelligence about Target Systems: Actors gather intelligence from various sources, including open-source research, insider threats, and enterprise networks. Information about both OT-specific and IT technologies in control systems is leveraged to identify vulnerabilities and potential entry points.

Iranian President at the time, Mahmoud Ahmadinejad visits the Natanz enrichment facility in 2008 (TimesOfIsrael)
- In 2008, over 40 photos of Ahmadinejad’s visit to the Natanz facility were released on the official Iranian presidential website. It has been suggested that through intelligence activities conducted via these photographs, the systems were identified, paving the way for Stuxnet. This underscores the profound intelligence potential even some images can offer, highlighting the criticality and vulnerability of such systems.
Developing Techniques and Tools: Armed with intelligence, actors procure or develop tools tailored to manipulate control systems effectively. From exploiting default passwords to crafting custom malware like TRITON, attackers adapt their arsenal to the target environment.
Gaining Initial Access: Leveraging poor security practices in remote access points, actors clandestinely infiltrate control systems. Vendor access and remote connections serve as gateways for exploitation, highlighting the need for robust cybersecurity measures.
Executing Techniques to Achieve Effects: Once inside, actors disrupt, manipulate, or disable control systems to achieve their objectives. This includes impairing data reporting, denying operator control, and enabling remote reconnaissance.
The consequences of successful intrusions can be dire, ranging from operational disruptions to physical damage or destruction of equipment. Actors exploit vulnerabilities in control systems to orchestrate sophisticated attacks with potentially far-reaching impacts.
How to Protect Critical Systems?
Balancing network security with performance, features, ease-of-use, and availability poses significant challenges for owners/operators, particularly when considering the use of system tools, scripts, and remote access. While these tools enhance functionality and facilitate maintenance, they also widen the attack surface, leaving Industrial Control Systems (ICS) vulnerable to malicious actors.
As the targeting of OT/ICS by malicious actors escalates, owners/operators must weigh the risks associated with these decisions more carefully. Understanding that system targeting is not a matter of “if” but “when” is crucial in guiding ICS security decisions. By assuming an adversarial perspective and anticipating potential attack vectors, owners/operators can proactively prioritize and implement mitigation strategies.
The abundance of available security solutions can be overwhelming, leading to decision paralysis. Amidst this complexity, owners/operators may overlook simple yet effective security measures. However, adopting straightforward ICS security best practices can significantly mitigate common threats.
Limit Exposure of System Information:
- Safeguard operational and system data, including hardware, firmware, and software details, from public disclosure.
- Incorporate information protection education into personnel training.
- Document data flow, communication pathways, and security standards rigorously.
- Restrict data sharing to essential legal and contractual requirements, preventing unauthorized access and use.
- Enforce strict administrative policies and audit procedures to ensure compliance and secure data transmission.
Identify and Secure Remote Access Points:
- Maintain comprehensive knowledge of installed systems and remote access points within the control system network.
- Establish firewalls and Demilitarized Zones (DMZ) to segregate vendor access points and devices.
- Implement Virtual Private Networks (VPNs) for secure data exchange.
- Utilize jump boxes and enforce strict access control policies.
- Regularly review configurations and conduct penetration testing to identify and address vulnerabilities.
- Change default passwords, patch known vulnerabilities promptly, and monitor access logs for suspicious activities.
Restrict Tools and Scripts:
- Limit access to network and control system tools and scripts to authorized users performing legitimate tasks.
- Remove non-critical tools and prevent unauthorized reinstallation.
- Securely store essential tools externally and conduct routine audits to ensure compliance.
Conduct Regular Security Audits:
- Perform independent security audits to identify and address system vulnerabilities.
- Validate all connections, review patching procedures, and monitor system logs continuously.
- Implement CISA ICS mitigations and best practices, and incorporate them into audit procedures.
Implement a Dynamic Network Environment:
- Periodically make manageable network changes to disrupt persistent access by malicious actors.
- Deploy additional firewalls, modify IP address pools, upgrade hardware and operating systems, and install commercially available security packages.
- Plan changes thoughtfully to minimize disruption to network operations.
By adopting these mitigation strategies, owners/operators can strengthen the resilience of their ICS against evolving cyber threats and reduce the likelihood of successful intrusions. Constant vigilance, proactive measures, and adherence to best practices are essential in safeguarding critical infrastructure from malicious actors.
How can SOCRadar Help?
Organizations tasked with safeguarding critical infrastructure must adopt a proactive approach in acknowledging, evaluating, and addressing potential risks and vulnerabilities. The process of inventorying and monitoring critical infrastructure assets, coupled with the identification of vulnerabilities against all cyber threats prevalent in the industry, expedites remediation efforts and patch management. This proactive stance aids companies in fortifying their defenses against potential cyber assaults.
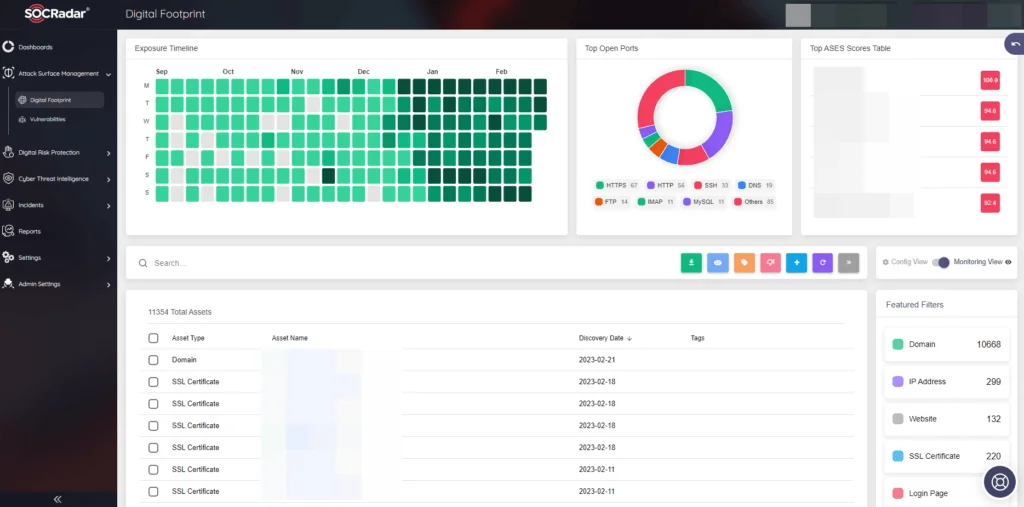
SOCRadar Attack Surface Management Module
The SOCRadar Extended Threat Intelligence offers an Attack Surface Management (ASM) solution tailored for continuous discovery, inventorying, classification, and prioritization, complemented by real-time monitoring. This comprehensive suite facilitates security professionals in attaining a thorough understanding of their external-facing digital assets. Utilizing the SOCRadar XTI ASM solution, security experts can diligently track network vulnerabilities. Recognizing and addressing vulnerabilities within critical infrastructure organizations play a pivotal role in mitigating the potential threat actors may leverage to exploit the attack surface.


































