
Patch Released for RCE Vulnerability in pfSense Firewall
A critical vulnerability has been discovered in a plugin of Netgate’s pfSense firewall. The flaw is tracked as CVE-2022-31814 and can expose the affected instances to unauthenticated remote code execution attacks.
pfSense is an open-source firewall and router software distribution based on FreeBSD. The firewall does not include the plugin named pfBlockerNG by default. pfBlockerNG enables allow-listing in the pfSense firewall, allowing the users to block specific IPs and entire countries.
To become exposed, the issue requires access to the web server on the firewall, which should never be open on WAN and is often restricted when configured per best practices.
The vulnerability affects pfBlockerNG versions 2.1.4_26 and earlier, and software updates are available to address the problem.

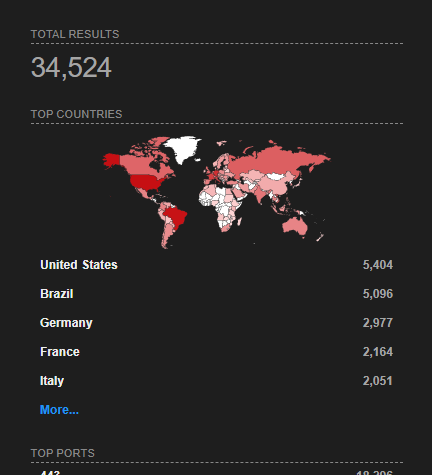
Over 30K pfSense Machines Exposed
The CVSS score of the vulnerability is 9.8, as noted in IHTeam’s advisory since the web server is run by root and exploitable by unauthenticated attackers.
According to Netgate, the overall practical impact was deemed lower even though the issue received a high score. A Shodan search shows over 30,000 pfSense machines are exposed on the internet. And as Netgate also implies, this does not indicate the specific count of instances impacted by the plugin’s vulnerability.
The pfSense firewall’s distributor, Netgate, stated that the issue uncovered by the researchers was in the pfBlockerNG package but had previously been addressed in the pfBlockerNG-devel package, the version the package maintainer recommends everyone use.
Developers continue shipping and enabling users to install between the 2.x and the 3.x branch. The researchers said, if the affected 2.x branch was removed entirely from the list of accessible plugins, the misunderstanding could be resolved quickly.
Proof-of-concept is Available
Software updates are available from pfSense, and the plugin’s developer, pfBlockerNG-devel, is a secure version recommended.
According to an IHTeam researcher, other software developers could learn from the flaw’s characteristics.
The researcher explained: “To avoid these types of vulnerabilities, developers should take extra care while handling user input (not only via direct GET and POST requests but also via input that might be passed in request headers such as Cookies, Host, or User-Agent). All user input should be carefully analyzed and sanitized before being passed to the application. This is also valid for other attacks such as cross-site scripting (XSS) or SQL injection, not only for command execution.”
The exploit code can be found here.
Check IHTeam’s blog post for a technical description and proof-of-concept of the problem.




































