
Pi-hole RCE Exploit, Netflix Scam Pages, Rockwell Access Sale, and Massive Password Leak
The SOCRadar Dark Web Team has identified multiple critical cyber incidents, highlighting ongoing threats to various sectors. Recent findings include an alleged RCE exploit, a DDoS attack on Copenhagen Police, and sale of Netflix scam pages. Additionally, unauthorized access to major automation systems and a massive password compilation have been detected.
Receive a Free Dark Web Report for Your Organization:
The Alleged CVE-2024-21762 RCE Exploit is Shared for Pi-hole
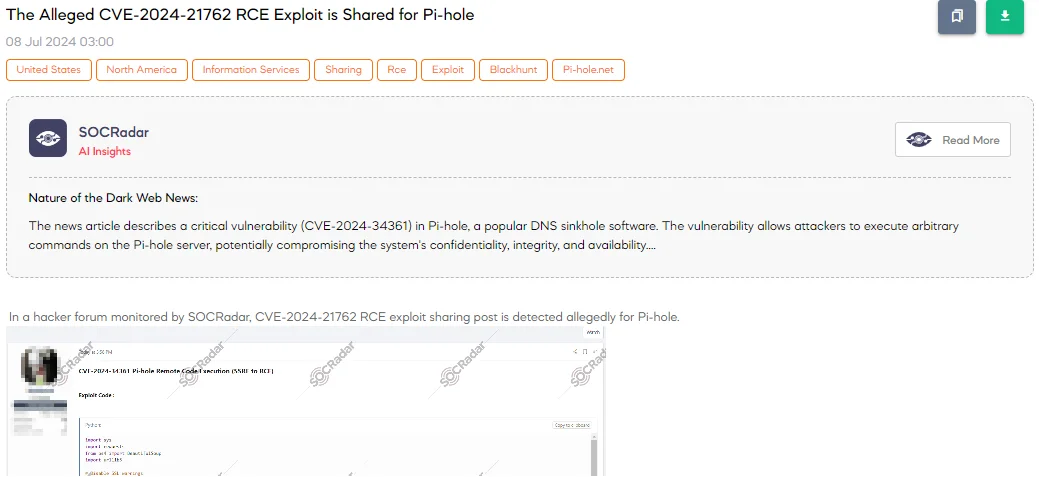
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor claims to have shared an exploit for CVE-2024-21762, allegedly targeting Pi-hole.
The threat actor describes the exploit as a critical vulnerability (CVSS 8.6) in Pi-hole, which allows Remote Code Execution (RCE) via Server-Side Request Forgery (SSRF). The exploit involves a detailed Python script that can log into a Pi-hole instance, obtain a CSRF token, send a payload, and execute arbitrary commands on the server.
According to the threat actor, the alleged exploit affects Pi-hole versions up to 5.18.2 and has been resolved in version 5.18.3. This security flaw compromises system confidentiality, integrity, and availability by enabling unauthorized command execution.
CyberArmy Conducted DDoS Attack on Copenhagen Police
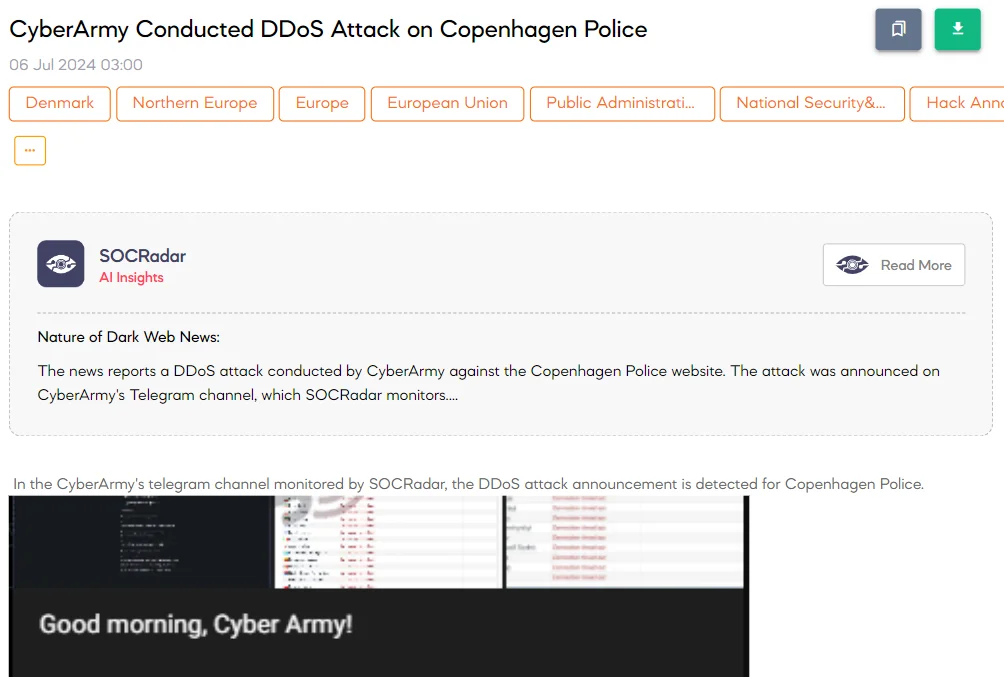
The SOCRadar Dark Web Team detected a post in a hacker forum announcing a Distributed Denial of Service (DDoS) attack on the Copenhagen Police. The attack was claimed by the People’s CyberArmy, also known as the Cyber Army of Russia, a pro-Russian hacktivist group.
Alleged Scam Pages of Netflix are on Sale
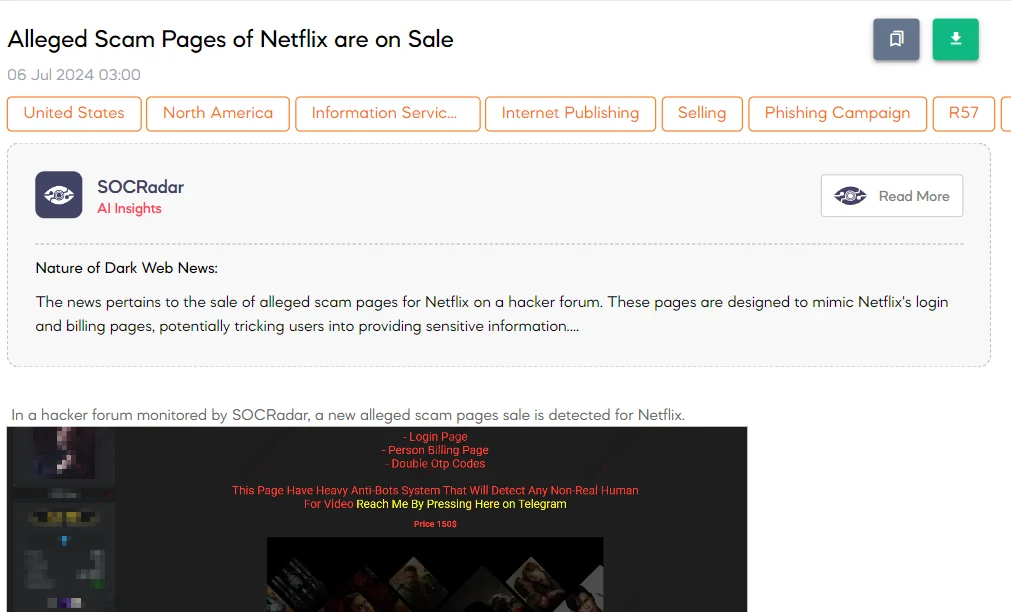
The SOCRadar Dark Web Team detected a post in a hacker forum stating that a new alleged sale of Netflix scam pages has been detected. The threat actor claims to be selling undetected Netflix scam pages, including a login page, personal billing page, and double OTP codes.
The post highlights that the scam pages have a robust anti-bot system designed to detect non-human interactions. The threat actor offers a video demonstration and sells the scam pages for $150, with contact available via Telegram.
The Alleged Unauthorized Access Sale is Detected for Rockwell Automation
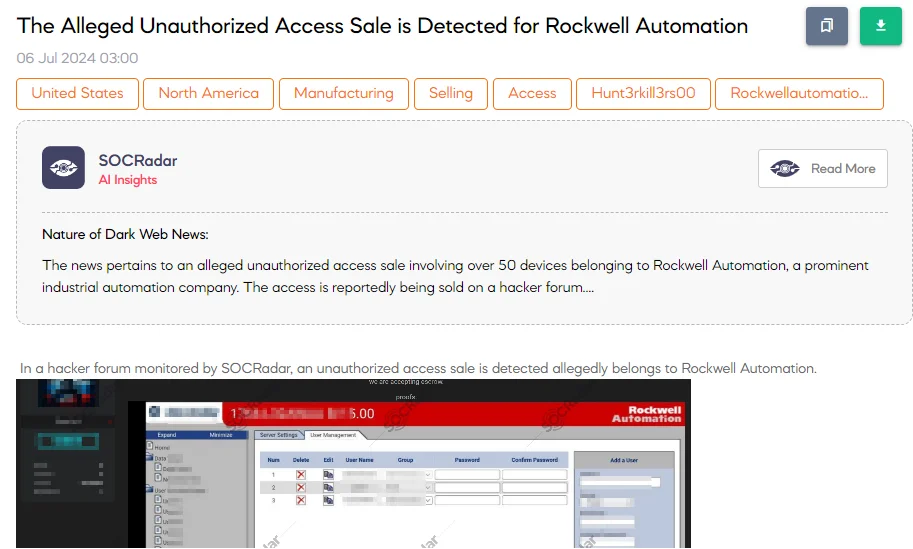
The SOCRadar Dark Web Team detected a post in a hacker forum claiming an unauthorized access sale allegedly belonging to Rockwell Automation. The threat actor claims to have access to over 50 devices from Rockwell Automation in the USA and is accepting escrow for the sale.
Rockwell Automation, an American provider of industrial automation and digital transformation technologies, faces potential security risks from this alleged breach.
A New RockYou2024 Compilation is Allegedly Leaked
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor claims to have leaked a new alleged RockYou2024 compilation. The threat actor claims the list contains over 9.9 billion passwords.
The threat actor states they updated the previous RockYou21 list with new data from leaked databases across various forums over the past years. They also mentioned cracking old passwords with advanced hardware, ensuring the list contains new real passwords from users.
With 9.9 billion passwords, brute-forcing just got a whole lot easier (and maybe even a little boring).
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































