
PoC Available for Critical RCE Vulnerability in Microsoft Word (CVE-2023-21716)
CVE-2023-21716 was discovered in Microsoft Word last year. It is a critical remote code execution (RCE) vulnerability in Microsoft Office, with a CVSS score of 9.8.
Joshua Drake, a researcher, had reported the vulnerability to Microsoft along with a technical advisory and proof-of-concept (PoC) exploit code. The issue has been addressed in the February Patch Tuesday, so now the researcher made the advisory and the PoC available, which you can access here.
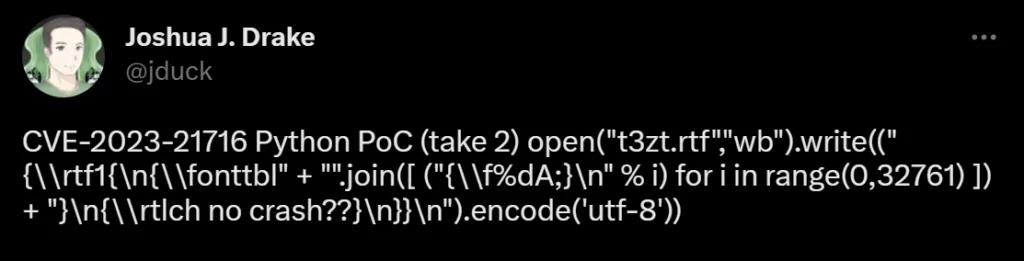
The researcher also posted the full PoC in a tweet, as it can fit without the comments.
How Does the CVE-2023-21716 Vulnerability Work?
An attacker could exploit the vulnerability to achieve remote code execution with the same privileges as the victim after the victim is compromised with a malicious RTF file.
CVE-2023-21716 requires no prior authentication, and the methods used to distribute the malicious file vary. Victims may receive emails containing malicious RTF attachments. The victim does not need to open the malicious file; simply loading it into the Preview Pane is sufficient for an attacker to be able to exploit CVE-2023-21716 and eventually achieve remote code execution (RCE).
The CVE-2023-21716 vulnerability, according to the researcher, stems from a heap corruption issue in the Microsoft Word RTF parser, which is triggered when dealing with a font table that contains an excessive number of fonts.
There is additional processing after the memory corruption occurs, and a threat actor could exploit the CVE-2023-21716 vulnerability by using a specially crafted heap layout.
Possible Risk of Exploitation
There is no evidence that the CVE-2023-21716 vulnerability is being actively exploited, and Microsoft believes that it is unlikely to be exploited.
However, advanced threat actors may try to reverse engineer the fix to exploit the vulnerability. While a proof-of-concept (PoC) for the vulnerability exists, it is unclear if it can be turned into a full-blown exploit, given that it does not provide evidence for exploitation but simply suggests it is possible. Exploiting this vulnerability in Microsoft Word could allow malware to spread through email.
Microsoft’s Workarounds Carry Risks, Security Update Recommended
Microsoft suggests two possible workarounds. While one workaround is to read emails in plain text, this may be inconvenient as it limits the content displayed.
Another option is to use the Microsoft Office File Block policy, which restricts the opening of RTF documents from untrusted sources but requires changes to the Windows Registry. This method may lead to problems if not executed correctly, like reinstalling your operating system. The possibility of users being unable to open any RTF document also exists if an exempt directory has not been specified.
Therefore, the safest way to address the vulnerability is to install the security update provided by Microsoft.
How Can SOCRadar Help?
SOCRadar is a threat intelligence platform that can help organizations stay up-to-date on vulnerabilities and potential risks. The platform collects information on known vulnerabilities and presents it in an actionable format through alarms, making it easy to prioritize actions and stay aware of potential threats.
SOCRadar’s Vulnerability Intelligence module provides detailed information on vulnerabilities, allowing users to manage related issues effectively and prioritize necessary patches.




































