
Predicting Vulnerability Exploitation for Proactive Cybersecurity: What’s EPSS, and How Can SVRS Enhance It?
Predicting outcomes closely before taking action is a fundamental aspect of effective decision-making. Whether in our personal lives, business strategies, or even the realm of technology, the ability to anticipate and prepare for potential developments can greatly enhance our chances of success. In vulnerability management, this principle holds true.
In the complex landscape of cybersecurity, understanding which vulnerability is most likely to pique the interest of threat actors and become the target of exploitation is crucial. Prioritizing vulnerabilities based on their likelihood to be exploited first ensures that the most critical issues are addressed promptly. This strategic approach means that security teams can allocate their efforts and resources where they are needed most, effectively reducing the attack surface and enhancing overall security posture, allowing organizations to stay one step ahead of potential attackers.
Ultimately, the ability to predict and prepare for potential threats in vulnerability management is akin to a chess game, where staying ahead of the opponent is the key to success. By identifying and addressing vulnerabilities with the highest risk of exploitation, organizations can proactively strengthen their defenses and create a formidable barrier against potential cyber threats.
EPSS: Exploit Prediction Scoring System
The Exploit Prediction Scoring System (EPSS) was founded in 2019 as an open community-driven effort to model and manage vulnerability risk from a probabilistic perspective. It is governed by the Forum of Incident Response and Security Teams (FIRST), a team responsible for a number of vulnerability scoring protocols.

EPSS is used in cybersecurity to predict the likelihood of a particular software vulnerability being exploited by attackers. It assigns a score to vulnerabilities between 0 and 100, helping organizations prioritize their security efforts based on the severity of potential threats. Firms can typically address between 5% and 20% of known vulnerabilities per month. Furthermore, only a small subset (2%-7%) of published vulnerabilities is ever seen to be exploited in the wild. The goal is to focus resources on addressing the most critical vulnerabilities first to reduce the risk of cyberattacks.
The EPSS model works by evaluating various factors to predict the likelihood of a software vulnerability being exploited by attackers. While the specific methodology and factors used can vary, it typically assesses historical data and environmental factors, referencing the Common Vulnerabilities and Exposures (CVE) database, assigning scores based on risk, and prioritizing response efforts. It relies on continuous updates as new data becomes available, guiding organizations in patch management and security strategies.
FIRST lists EPSS’ data sources as follows:
- MITRE’s CVE List – Only CVEs in the “published” state are scored
- Text-based “Tags” derived from the CVE description and other sources talking about the vulnerability
- Count of how many days the CVE has been published
- Count of how many references are listed in the CVE
- Published Exploit code in any of: Metasploit, ExploitDB and/or Github
- Security Scanners: Jaeles, Intrigue, Nuclei, sn1per
- CVSS v3 vectors in the base score (not the score or any subscores) as published in the National Vulnerability Database (NVD)
- CPE (vendor) information as published in NVD
- Ground Truth: Daily observations of exploitation-in-the-wild activity from AlienVault and Fortinet.
Overall, the goal of EPSS is to assist organizations in making informed decisions about how to allocate their cybersecurity resources efficiently, focusing on the vulnerabilities most likely to be exploited by malicious actors, referencing its wealth of information on previous vulnerabilities.
How to Use EPSS?
At its core, EPSS streamlines the intricate process of predicting the probability of a CVE being exploited in the wild within the next 30 days. Simply input a CVE, and EPSS promptly furnishes the likelihood of imminent exploitation.
What distinguishes EPSS is its emphasis on real-world exploitation. Unlike conventional scoring systems, it transcends reliance solely on vulnerability severity or CVSS scores; it delves deep into the realm of real-world proof-of-concepts and exploitation trends, prioritizing practical implications.
A vulnerability bearing a high CVSS score doesn’t foretell in-the-wild exploitation. Utilizing statistical analysis to make this prediction, the Exploit Prediction Scoring System is an invaluable tool for efficient vulnerability prioritization on a larger scale.
For instance, when assessing the exploitability of the Log4j vulnerability (CVE-2021-44228) on the API endpoint, EPSS suggests a 97.4% likelihood of this CVE being exploited in the wild within the next 30 days. However, it is just an example of its usage; FIRST underscores that for well-known vulnerabilities like Log4Shell, EPSS has limited applicability due to the imperative need for immediate response. Its scoring mechanism activates upon the publication of a CVE on the official CVE List, allowing it to adapt and learn from actual exploitation incidents. Furthermore, the presence and dissemination of PoC exploit code plays a pivotal role in influencing the detection likelihood.
In conclusion, EPSS possesses both strengths and limitations; still, it is particularly valuable in the assessment of less-publicized vulnerabilities that might otherwise escape notice.
Here is a full guide on how to use the EPSS API.
For more in-depth insights into the challenges posed by vulnerabilities such as Log4J, refer to the dedicated page on FIRST.
How Many Critical Vulnerabilities Are Actually Exploited?
Before we give further examples of vulnerabilities, let’s take a look at how many critical vulnerabilities are actually exploited. According to a 2019 report, among vulnerabilities with a CVSS score of 10, approximately 17% were found to be exploited.
In the report, it is revealed that vulnerabilities with a CVSS score of 9 or 10 have a higher likelihood of being exploited compared to the baseline rate of 5.5%. Furthermore, nearly half of all exploited vulnerabilities have a CVSS score of 9 or higher.
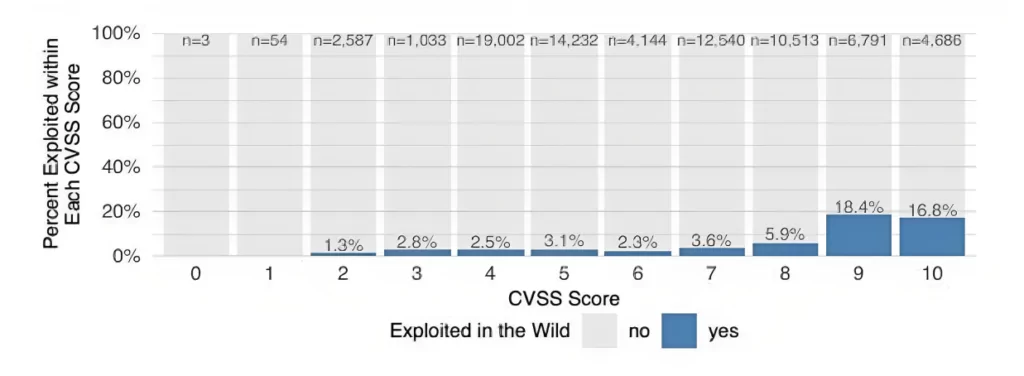
The EPSS model’s performance depends on multiple sources, not limited to the criticality of a vulnerability. For instance, a performance analysis on FIRST’s site demonstrates that prioritizing and remediating all vulnerabilities with CVSS scores above 7 is simply not feasible.
FIRST visualized this model’s performance with a diagram, showing published and exploited vulnerabilities along with True Positives (TP), False Positives (FP), False Negatives (FN), and True Negatives (TN).
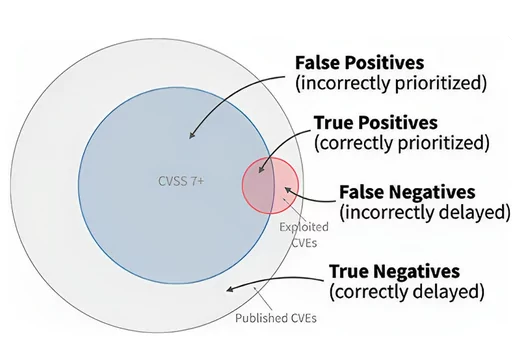
The quality of this approach is assessed by tracking vulnerabilities exploited in the wild and categorizing each vulnerability into one of four groups based on two attributes: whether it should be remediated and whether it has been observed as exploited. True Positives (TP) represent prioritized vulnerabilities that were indeed exploited (the overlap of remediated and exploited vulnerabilities). False Positives (FP) are vulnerabilities prioritized but not exploited (in the blue circle without overlap with the red circle). False Negatives (FN) are vulnerabilities not prioritized but observed as exploited (in the red circle without overlap with the blue circle). True Negatives (TN) are vulnerabilities not prioritized and not exploited, represented by the outer gray circle.
In vulnerability management, when prioritizing vulnerabilities, the primary goal is to identify true positives, hence why remediating all vulnerabilities with CVSS scores over 7 will not be feasible.
Another graphic on FIRST’s site visualizes and compares the coverage and efficiency of EPSS v1, v2, and CVSS v3.
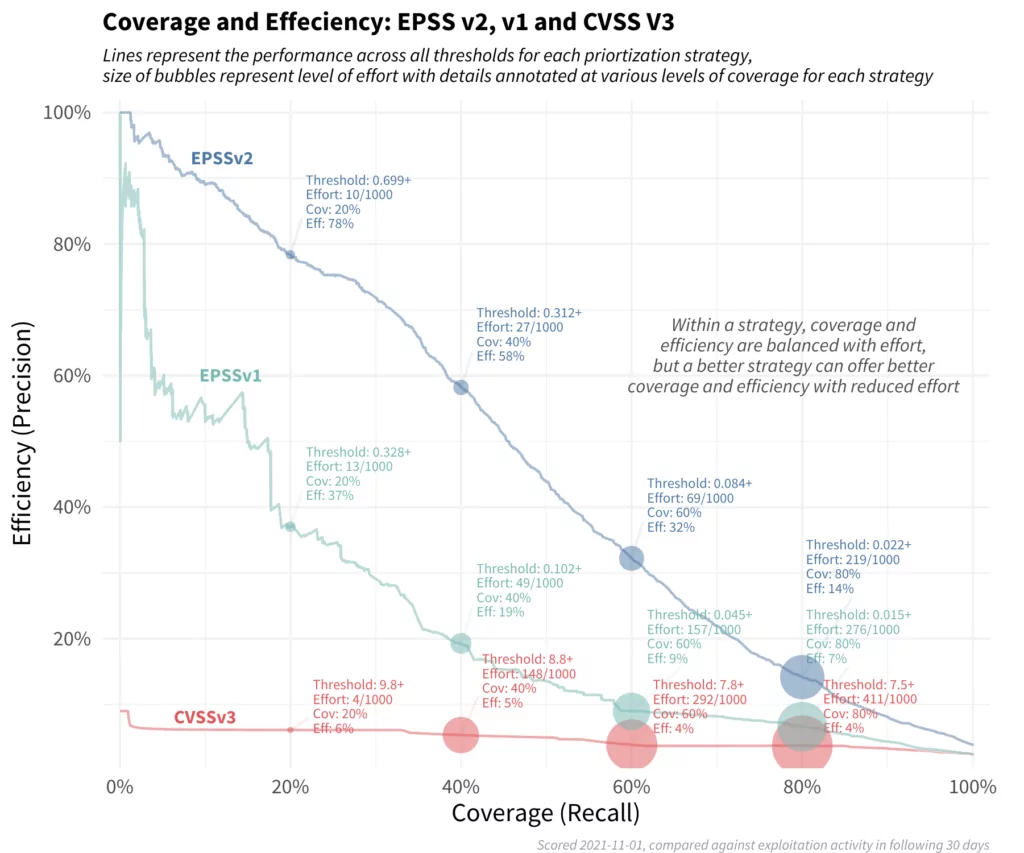
The red line at the bottom depicts a remediation strategy based on CVSS v3.1 base scores. It maintains a consistent level of efficiency, but to enhance coverage, more vulnerabilities need remediation. The green middle line showcases EPSS v1, which offers higher efficiency and coverage than CVSS alone, although performance has declined since its inception. The upper blue line represents the latest EPSS model, allowing smaller organizations to achieve notable efficiency with limited resources.
Organizations with more resources can attain both improved efficiency and coverage. While there’s typically a tradeoff between coverage and efficiency, shifting to the latest EPSS scores in prioritization can yield a significant improvement over existing methods.
Enhancing EPSS with SOCRadar SVRS
While EPSS is a valuable tool for predicting vulnerability exploitation, it is important to note that the threat landscape is constantly evolving. To further enhance the accuracy of vulnerability prioritization, organizations can incorporate SOCRadar Vulnerability Intelligence, which employs a special score called the SOCRadar Vulnerability Risk Score (SVRS). This score rates vulnerabilities based on how likely they are to be exploited and draws information from various sources, including social media, news, and most importantly, the dark web and Telegram channels. By combining EPSS and SOCRadar SVRS, organizations can gain a more comprehensive and real-time understanding of the threat landscape. This dynamic approach allows security teams to stay ahead of emerging threats, making it more difficult for attackers to find and exploit vulnerabilities within the organization’s infrastructure.
Vulnerability Scoring with EPSS
MOVEit Transfer – CVE-2023-34362 (CVSS Score: 9.8):
Let’s use the MOVEit vulnerability (CVE-2023-34362) as an example. The Clop Ransomware group exploited this vulnerability, causing a massive data breach. This was a zero-day vulnerability, with threat actors initiating exploits in late May. However, its CVE identifier was assigned later and published on the National Vulnerability Database (NVD) on June 2, 2023.
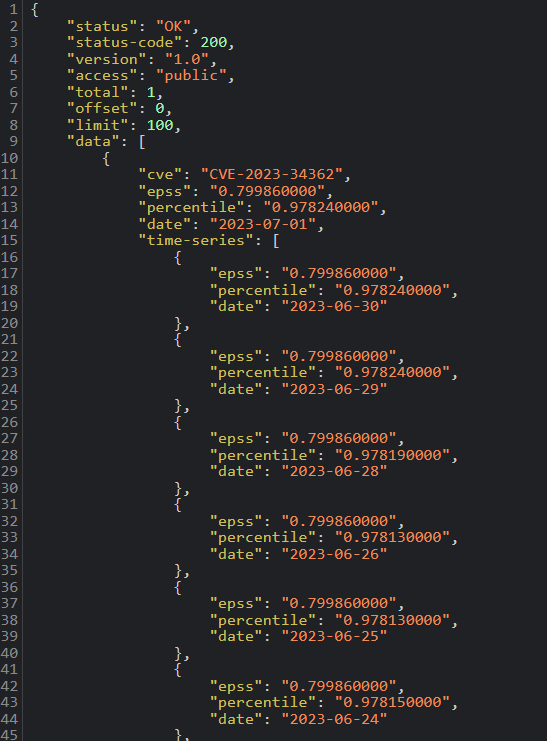
Examining the vulnerability’s page on SOCRadar, the lifecycle data indicates numerous new repository creations related to CVE-2023-34362 following its publication. Exploitation activity saw a substantial increase. On the day after its publication, June 3, 2023, the CVE exhibited an exploitability rate of 1.8%.
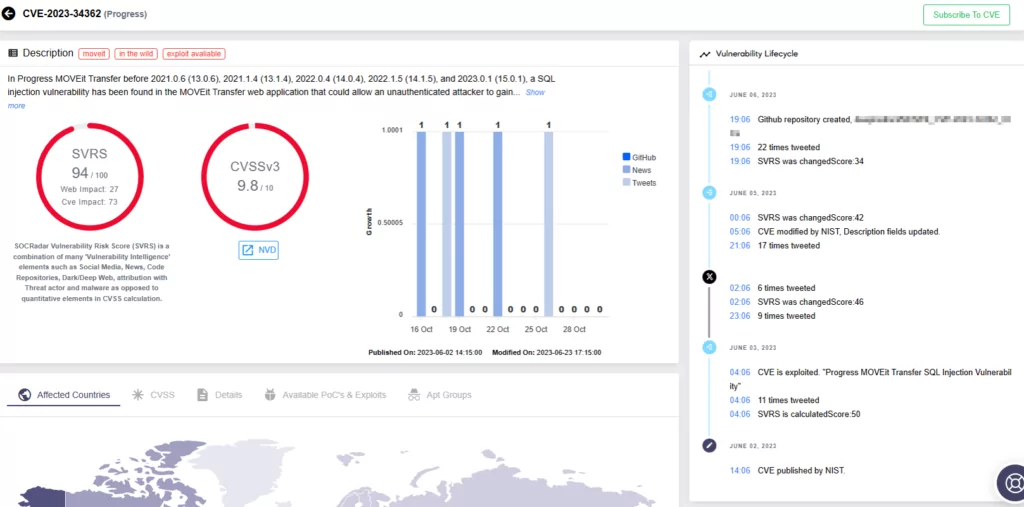
The score undergoes significant fluctuations with alterations in the time frame. If we select July 1 as our reference date and search for EPSS scores for each of the previous 30 days leading up to that date, the exploitability score for June 3 increases substantially to 86%. Each day introduces a fresh probability, leading to varying outcomes.
Citrix NetScaler – CVE-2023-4966 (CVSS Score: 9.4 on Citrix, 7.5 on NVD):
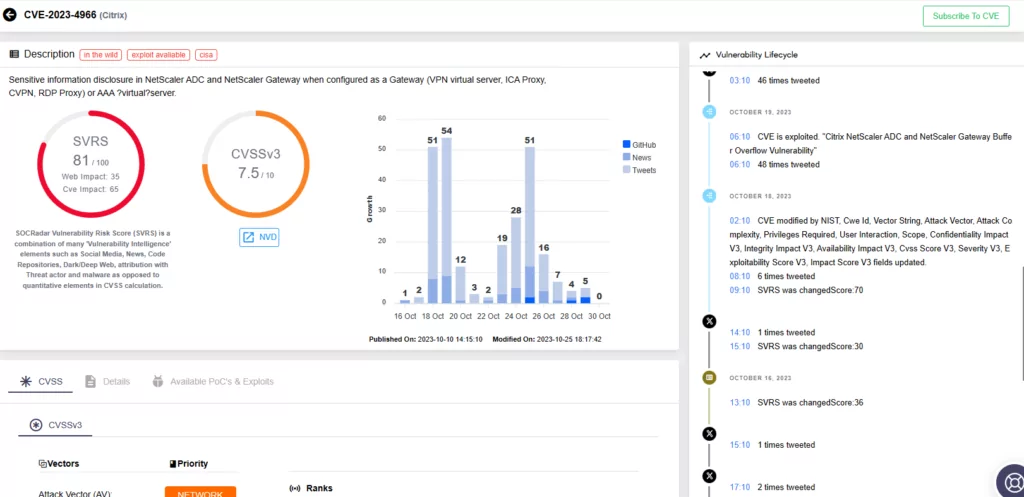
Let’s examine one of the more recent vulnerabilities that we know has been actively exploited. Discovered in October, the vulnerability in Citrix NetScaler quickly became a target for exploitation. Citrix promptly issued a call for immediate remediation in response to the vulnerability’s ongoing exploitation.
According to SOCRadar’s Vulnerability Intelligence lifecycle data, the CVE identifier CVE-2023-4966 was initially reserved on September 19, 2023. Subsequently, on October 10, the CVE was updated with additional information on NVD, followed by another update on October 18. The lifecycle data further indicates that on October 19, the vulnerability was successfully exploited.
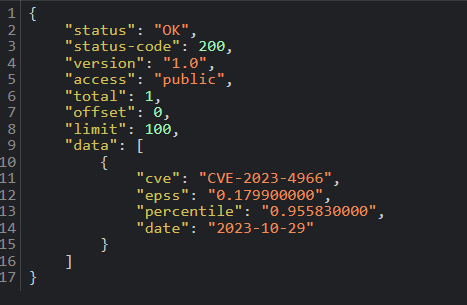
For October 19, the vulnerability exhibited an exploitability rate of less than 1%.
Throughout the month, the exploitability rate has remained relatively stable. However, by October 29, we observed a notable increase in the score, which rose to 17.9%.
Looking at these results, it is important to recognize how SOCRadar’s Vulnerability Intelligence enhances vulnerability management operations. By integrating the module, along with SOCRadar Vulnerability Risk Score (SVRS), organizations gain access to an even more current and comprehensive perspective of the threat landscape. SVRS draws information from diverse sources, providing insights into a vulnerability’s popularity from a hacker’s perspective. By combining EPSS with SOCRadar Vulnerability Intelligence, organizations are better equipped to stay ahead of emerging threats, making it more challenging for attackers to identify and exploit vulnerabilities within the organization’s infrastructure.
Which Top Vendors/Providers Use EPSS?
Numerous cybersecurity vendors and providers have recognized the value of EPSS and support EPSS in their products to assist organizations in prioritizing vulnerability management. Some of the prominent vendors/providers who use EPSS are:
Snyk
Snyk has integrated the Exploit Prediction Scoring System to enhance security intelligence for Snyk Open Source and Snyk Container vulnerabilities. This addition empowers users to identify potential vulnerabilities in their applications, prioritize them effectively, and take necessary actions while benefiting from a broader context of security information.

Nucleus Security
Nucleus Security effectively utilizes EPSS – watch the company’s video about the scoring model here. The company prefers it over CVSS due to its alignment with the bell curve. This characteristic offers valuable use cases, such as fallback prioritization when vulnerabilities have not been scored yet.

Amazon Web Services (AWS)
Amazon, a leading cloud services provider, also harnesses the power of EPSS for enhanced vulnerability management. AWS offers an EPSS guide on its site, providing information about using the API in one of the language-specific AWS SDKs.

Coalition, Inc
Coalition has its own scoring system, named Exploit Scoring System (ESS). ESS combines internal data with AI and language modeling to predict the exploitability of vulnerabilities. It generates scores for Exploit Availability Probability and Exploit Usage Probability, aiding security risk managers. The company is also listed as one of the EPSS-vendors on FIRST.

Qualys
Qualys introduced VMDR 2.0 with TruRisk, an advanced vulnerability management product. TruRisk assists organizations in understanding and handling cyber risk by evaluating multiple factors, including vulnerability exploitation evidence and asset criticality.

Wiz!
Wiz, a provider of cloud security solutions, focuses on risk-based prioritization in vulnerability management, emphasizing addressing critical vulnerabilities first. The vendor also leverages EPSS to enhance its vulnerability management capabilities.

See the full list of vendors who use EPSS on FIRST’s website.
Statistical Accuracy and Accountability of EPSS
EPSS’ unique approach relies on statistical modeling. This approach means that the system is accountable for the forecasts it publishes, and this accountability is its strength. Unlike traditional CVSS scores, which provide ordinal measurements, EPSS offers scientifically measurable predictions.
EPSS continually improves because it adapts to changing data and emerging trends in vulnerability exploitation. This means that an EPSS score can change daily as new information becomes available. Its accountability allows for constant refinement and enhancement.
While occasional mispredictions may occur, the overall performance of the system is the key to assessing its value. EPSS, no doubt, is a very practical aid for vulnerability management, especially if you’re dealing with a substantial volume of vulnerabilities. Scores like CVSS and EPSS do not replace human analysis; instead, they assist in prioritizing vulnerabilities for subsequent human evaluation. Whether you are handling automated tool outputs, bug bounty triage, or large-scale governance, EPSS can significantly simplify the process of deciding which vulnerabilities require in-depth human scrutiny.
Limitations and the Road Ahead
While EPSS excels in evaluating published CVEs, it currently focuses solely on these standardized vulnerabilities. Vulnerabilities not issued a CVE are beyond its scope for now. The challenge of assessing vulnerabilities and exploits that have not been observed in the wild is acknowledged by EPSS, and this area is one that requires continued improvement.
As with any predictive model, EPSS has its limitations and complexities, especially when dealing with unconventional vulnerabilities (such as Log4j). The road ahead includes addressing these complexities and expanding its scope to further enhance its utility.
Conclusion
In conclusion, EPSS offers an accountable approach to predicting vulnerability exploitation in the ever-changing landscape of cybersecurity. Its statistical methodology and commitment to refinement make it a valuable tool for organizations looking to proactively secure their digital assets. By predicting the likelihood of a vulnerability’s exploitation, EPSS empowers organizations to allocate their security resources efficiently, focusing on vulnerabilities most likely to be targeted by malicious actors.
While scoring systems like EPSS are not a replacement for human analysis, they serve as a crucial first step in prioritizing vulnerabilities and staying ahead of potential threats in the cybersecurity arena.
EPSS has brought remarkable progress to vulnerability management, but it acknowledges the challenges of assessing unobserved vulnerabilities and unconventional exploit methods. Nevertheless, by leveraging the power of EPSS, organizations can bolster their cybersecurity defenses.
Furthermore, the integration of SOCRadar Vulnerability Intelligence and the SOCRadar Vulnerability Risk Score (SVRS) enhances vulnerability management operations. By combining EPSS with SVRS, organizations gain a more current, comprehensive understanding of the threat landscape from a hacker’s perspective, proactively defending against potential cyber threats and staying ahead in the ever-competitive game of cybersecurity.



































