PyPI Packages Found Distributing Payloads in WhiteSnake Malware Campaign
Security researchers recently uncovered a new malware payload in the PyPI repository for Python packages. The payload, written in C#, raised concerns about the possibility of cross-language malware attacks.
Security researchers at JFrog discovered 22 malicious packages containing the same payload that targeted both Windows and Linux systems. They identified the Windows-specific payload as a variant of the WhiteSnake malware. The malware includes an Anti-VM mechanism, communicates with its command and control server via the Tor protocol, and is capable of data theft and command execution.
The Linux-specific payload is a simple Python script focused on data theft that leaks stolen data to a Telegram chat via the chatbot API.
Malicious Packages on PyPI
The following packages were identified as part of the WhiteSnake malware distribution campaign and began being distributed in April 2023:
By author “WS”:
- aeodatav04 (0.4)
- aeodata (0.4)
- testwhitesnake (0.1)
- testwhitesnake123a (0.1)
- testwhitesnakemodule (0.1)
- test23414234234 (0.6)
- test-23234231 (0.1)
- tiktokthon (0.1)
- androidspyeye (2.5)
- support-dev (7.8)
- support-hub (0.8)
By author “develepor_pyton_telethon”:
- social-checker (7.2)
- scrappers (3.5)
- scrappers-dev (4.1)
- detection-telegram (5.6)
- parser-scrapper (7.2)
By author “Brazil”:
- pandirequests (0.1)
- panderequests (0.1)
- libidrequest (0.4)
By author “YOURNAME”:
- test24234 (0.1)
By author “santic12”:
- aeivasta (0.3)
By author “Portugal”:
- pandarequest (0.1)
Payloads for Windows and Linux
The malicious packages run the Python package’s setup[.]py file during installation to determine the operating system and execute the correct payload. WhiteSnake malware is designed for Windows systems, while a malicious Python script will be executed on Linux systems.
WhiteSnake malware, the payload for Windows, was built using a builder available on the dark web. The WhiteSnake malware sends beacons and messages via a Telegram bot token and account chat ID, and allows for selecting encryption methods for logs and data leaks.
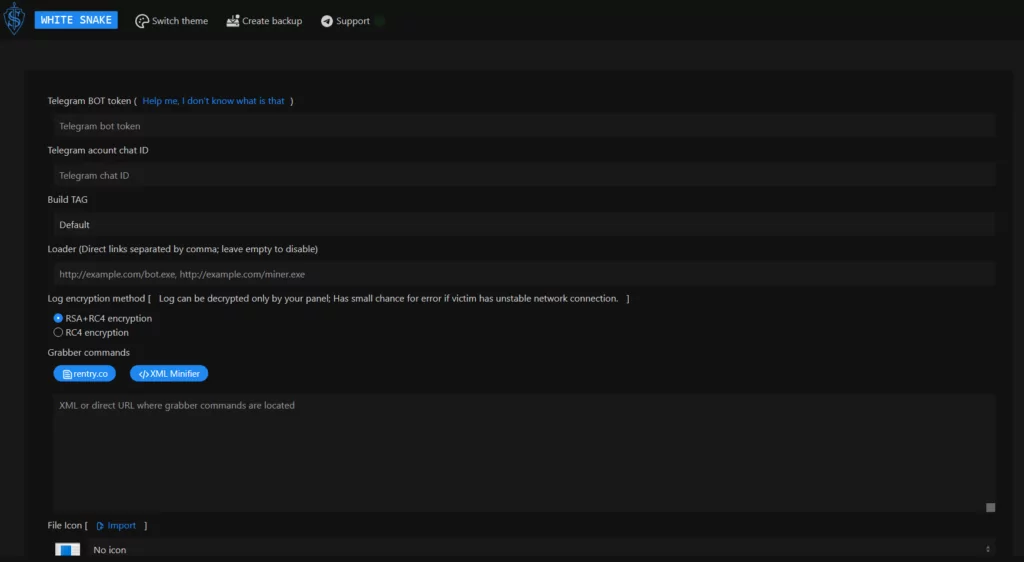
WhiteSnake Malware
The Windows payload identified as WhiteSnake malware is a Remote Access Tool (RAT) written in C#. According to the researchers, the sample included obfuscation methods like string encoding and code entity name scrambling.
There are four main features of the WhiteSnake malware: obfuscation, persistency, data theft, and command and control (C2) communication via Tor.
Obfuscation to Avoid Debugging and Analysis
WhiteSnake malware uses anti-debugging techniques to ensure its safety. It uses the ProtectionUtils.antiVM() function that checks the system manufacturer against a blacklist. The function queries the system’s manufacturer and model properties in the ROOT/CIMV2 WMI namespace and compares them to a blacklist of manufacturers to avoid detection.
Antianalysis.antiVM() is called right away, and a few instructions later, a nearly identical debugging routine named Program.detectVM() is called. The first anti-debugging routine is assumed to have been injected by a malware builder and used to obfuscate the resulting WhiteSnake binary.
In its process, the malware looks for the presence of a debugger or a DLL linked to a research tool. If any debug mechanism is found, the malware terminates.
Persistency in Victim’s System
After being copied to the %localappdata%NET.Framework folder, the malware creates a scheduled task to run its executable every minute. However, if the affected user did not run the malware with administrator privileges, then the scheduled task will only have LIMITED runlevel permissions by default.
Data Collection and Transmission to Attackers via Telegram
Once the malware finishes its setup, it will transmit information about the infected machine to the attackers through a private Telegram chat.
This information includes a screenshot of the user’s screen, the active username, machine name, OS version, external IP address, screen resolution, hardware information, system time, and running processes.
The malware will also search for files containing financial authentication data and send them to the server. The targets include browsers such as MozillaFirefox, GoogleChrome, and MicrosoftEdge, applications like Filezilla, Steam, Discord, and Telegram, and crypto-wallets like Binance, Bitcoin, Ronin, and BinanceChain.
The collected information is compressed, encrypted, and sent to a specific Telegram chat using communication tokens embedded in the malware. The data can only be accessed by the attacker with the private key.
Using Tor for Command and Control Communication
The malware also sends a “Beacon” parameter, which is the server’s address in the Tor network.
The malware uses onion routing to receive commands from the C2 server, which provides a high level of anonymity and can bypass some firewall configurations.
The malware downloads the latest binary from the Tor project site and uses a custom configuration to start using onion routing.
Using Tor for communication is quite rare because it is more complicated to set up than other methods. However, it provides significant advantages to attackers by allowing them to stay anonymous and avoid being detected while carrying out their activities.
The control over the infected machine is implemented using a special protocol that allows the attacker to execute various commands, such as taking screenshots, downloading/uploading files, and running arbitrary commands. This combination of evasion techniques and control features makes the malware highly dangerous and allows attackers to fully control the infected machine.
Linux Payload in Python
The Linux payload is a simpler Python script that collects basic information about the infected machine, including the username, computer name, operating system, and IP address.
This information is stored in a file called system.json. The payload then proceeds to collect sensitive information from the infected machine according to an XML configuration. For browser folders, the collected files are typically cookies, keys, and login information.
The collected data is then sent to the attackers via an encrypted package using an API to a Telegram channel.
Unlike the Windows version, the Linux version does not contain anti-VM or anti-debugging mechanisms.
WhiteSnake Indicators of Compromise (IOCs)
- hxxps[://]api[.]telegram[.]org/bot6209822134:AAEHrtHFcGSwPxreBCCquU4vzJrpFtyg2kA/sendDocument?chat_id=-1001529292045&caption=Linux
- hxxps[://]api[.]telegram[.]org/bot6003786791:AAGBP7Kr5UNFj3_RBmspykT4E01xYv3Lk3Y/sendDocument?chat_id=615133582&caption=Default
Stay Ahead of Threats with SOCRadar
SOCRadar is always looking for possible dangers to provide actionable intelligence that will protect your company.
To stay informed about the latest threats, mentions, and indicators of compromise, check out the platform’s Threat Actor/Malware section.
You may also use the Threat Feed/IOC service to remain current on new patterns via personalized collections that are simple to tailor to your needs.