
Critical RCE Vulnerability in Fortra FileCatalyst Workflow Threatens File Transfer Security (CVE-2024-25153)
Fortra FileCatalyst Workflow, a trusted enterprise file transfer solution, is under severe threat due to the disclosure of a critical Remote Code Execution (RCE) vulnerability.
The vulnerability, CVE-2024-25153 (CVSS: 9.8), poses significant risks to organizations using FileCatalyst Workflow, compounded by the availability of a Proof-of-Concept (PoC) exploit that could be leveraged by potential attackers.
What Is the Fortra FileCatalyst Workflow Vulnerability, CVE-2024-25153?
The Fortra FileCatalyst MFT (Managed File Transfer) solution, comprising FileCatalyst Direct, Workflow, and Central components; FileCatalyst Workflow features a web portal allowing users to manage files within their organization.
However, the recently discovered CVE-2024-25153 vulnerability lies within this web portal, representing a directory traversal issue exploitable by attackers.
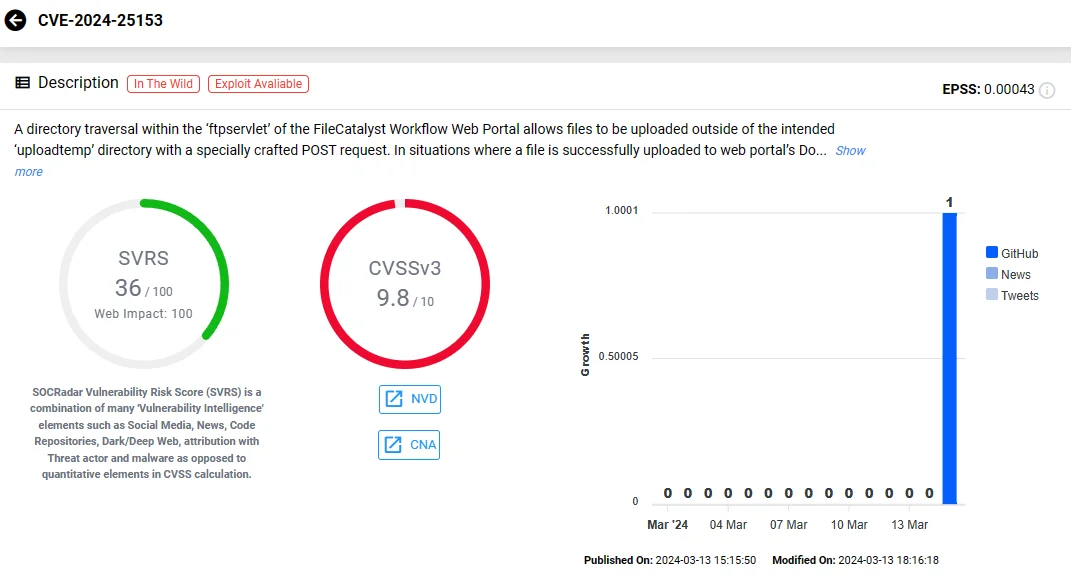
Vulnerability card of CVE-2024-25153 (SOCRadar Vulnerability Intelligence)
Due to CVE-2024-25153, by manipulating POST requests, attackers can bypass security measures and upload malicious files outside designated safe zones. This opens the door for planting dangerous files, such as web shells, directly into the server’s web root, granting remote attackers the ability to execute arbitrary code on the system.
Fortra FileCatalyst Workflow versions before 5.1.6 Build 114 are vulnerable to CVE-2024-25153.
Proof-of-Concept for CVE-2024-25153 Heightens Risk
Security researcher Tom Wedgbury has published a detailed technical analysis of the vulnerability, as well as a Proof-of-Concept (PoC) exploit code on GitHub. While these provide researchers with valuable insights, malicious actors may weaponize the PoC to target vulnerable systems.
The PoC demonstrates how attackers can automatically detect vulnerable systems with anonymous login enabled, obtain session tokens, upload command shells, and execute OS commands, streamlining the exploitation process and heightening the risk of successful attacks.
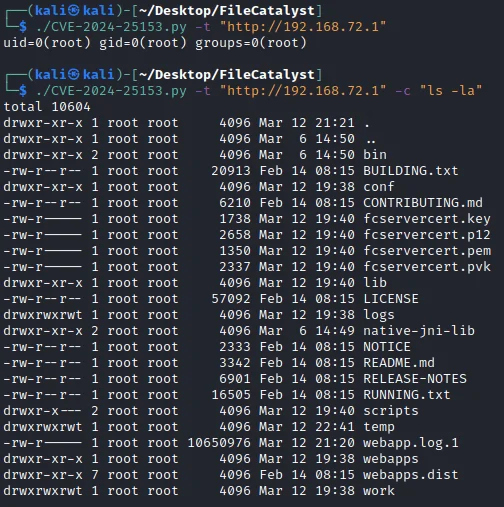
Exploit demonstration (Source)
Could the Fortra FileCatalyst Workflow Vulnerability (CVE-2024-25153) Lead to Ransomware Attacks?
Previous instances of vulnerabilities in similar file transfer applications have led to devastating ransomware infections and data theft, crippling organizations worldwide and across various industries. This emphasizes the potential for the newly disclosed Fortra FileCatalyst Workflow vulnerability to be exploited in the same way.
For instance, CVE-2023-34362, an SQL injection vulnerability in MOVEit Transfer, has become an attack vector of the Cl0p ransomware group.
Similarly, CVE-2024-0204, an authentication bypass issue affecting Fortra GoAnywhere MFT, was widely leveraged by threat actors including Cl0p, LockBit, and ALPHV (BlackCat).
Currently, a search on ZoomEye for FileCatalyst Workflow reveals 97 results, with the majority originating from the United States.
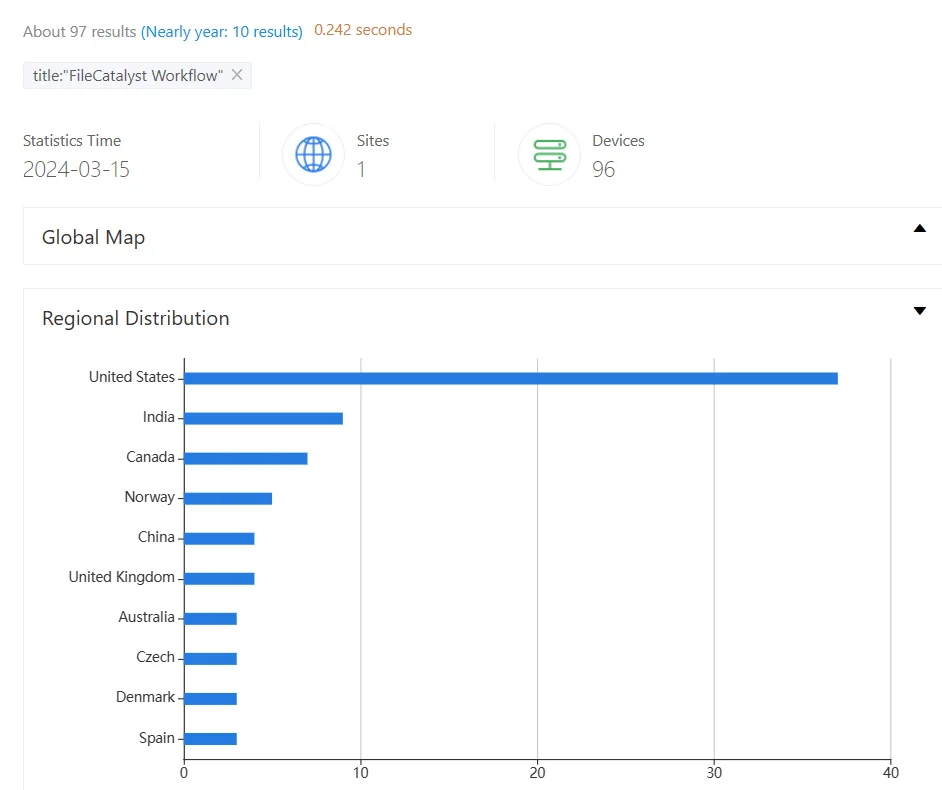
ZoomEye results for ‘FileCatalyst Workflow’
Urgent Action Required: Patch the Fortra FileCatalyst Workflow Vulnerability, CVE-2024-25153
In light of this critical vulnerability, Fortra has quickly issued a patch. Organizations must prioritize the application of this patch, especially given the history of ransomware attacks against similar products.
For more information, and guidance for remediation, visit Fortra’s advisory.
Organizations can use SOCRadar’s security solutions to significantly enhance their defense against emerging threats. SOCRadar, with the Attack Surface Management module, provides advanced monitoring capabilities that continuously scan digital assets for potential vulnerabilities and security incidents.
Enhance security posture by monitoring digital assets with SOCRadar’s ASM module
Additionally, its sophisticated Vulnerability Intelligence equips organizations to proactively track and prioritize vulnerabilities, enabling swift and targeted mitigation strategies.
Monitor CVE and exploitation trends in real-time via SOCRadar’s Vulnerability Intelligence



































