
Ingress Nightmare: Critical Unauthenticated Remote Code Execution Vulnerabilities in Ingress NGINX
On March 24, 2025, the Kubernetes Security Response Committee released a patch for a set of high to critical RCE vulnerabilities in the ingress-nginx controller putting over 6,500 clusters at immediate risk by exposing the component to the internet, including CVE-2025-1974, which carries a CVSS score of 9.8 and could lead to complete Kubernetes cluster compromise.
4 of these vulnerabilities were discovered and responsibly disclosed by researchers from Wiz, who worked with Kubernetes maintainers to ensure timely patches.
TL;DR – Key Points
- 4 high to critical, 1 medium ingress-nginx vulnerabilities disclosed:
- CVE-2025-1974 (CVSS 9.8) – Allows cluster-wide compromise via configuration injection.
- CVE-2025-24513 & CVE-2025-24514 – Could lead to Kubernetes Secret exposure.
- CVE-2025-1097 & CVE-2025-1098 – Increase the risk of unauthorized access.
- Discovered by Wiz researchers and reported to Kubernetes maintainers.
- Affected versions: ingress-nginx v1.11.0 – v1.12.0 (and older versions).
- Fix available: Upgrade to v1.12.1 or v1.11.5 immediately.
- Mitigation options: If upgrading isn’t possible, disable the Validating Admission Controller to reduce risk. (Remember to re-enable)
- Impact: Attackers could access Kubernetes Secrets, escalate privileges, and fully compromise clusters.
Background
Ingress controllers like ingress-nginx are widely used to manage external access to services within Kubernetes clusters, routing HTTP and HTTPS traffic via NGINX. Due to its flexibility and ease of deployment, ingress-nginx is used in over 40% of Kubernetes clusters.
However, improper handling of NGINX configuration parameters can introduce severe security risks. The newly discovered vulnerabilities exploit weaknesses in how ingress-nginx processes these configurations, potentially allowing attackers to escalate privileges, access sensitive data, or gain full control of a cluster.
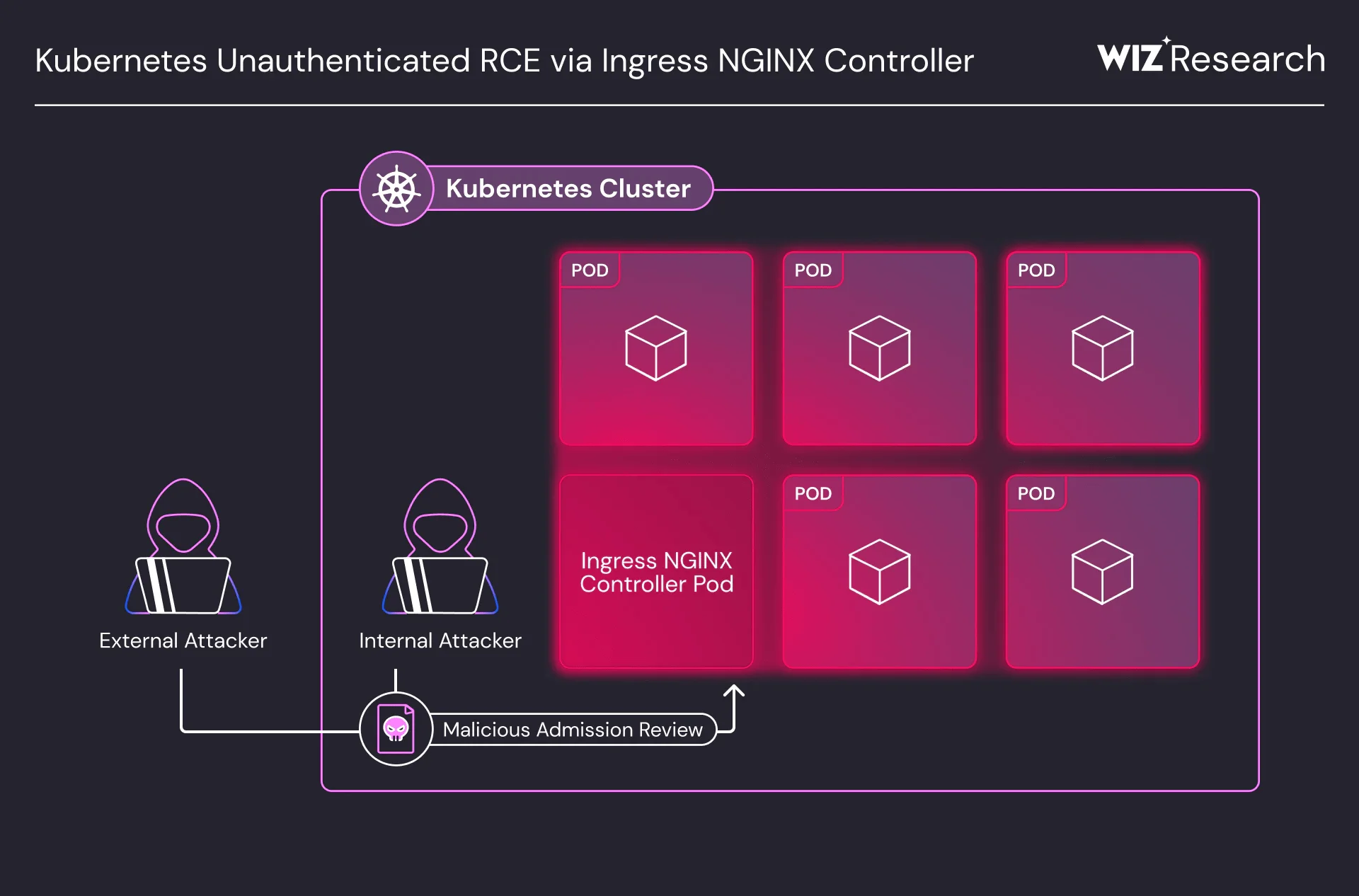
IngressNightmare attack vectors (Wiz)
Vulnerability Details
The latest security update patches five vulnerabilities, all of which could be leveraged by attackers to escalate privileges or expose sensitive information.
- CVE-2025-1974 (CVSS 9.8 – Critical)
This critical vulnerability allows an unauthenticated attacker with access to the Pod network to exploit configuration issues, resulting in arbitrary code execution within the ingress-nginx controller’s context, under specific conditions. This is especially dangerous as it requires no credentials or administrative access, making it highly exploitable in certain environments.
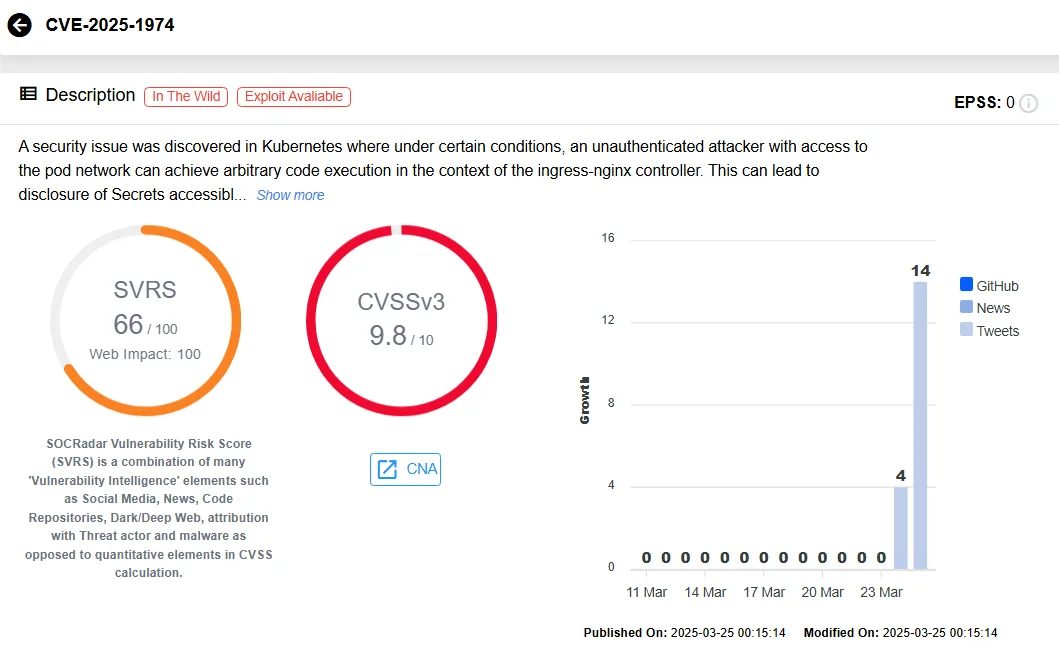
SOCRadar’s Vulnerability Intelligence, CVE-2025-1974
- CVE-2025-1097 (High Severity)
The auth-tls-match-cn Ingress annotation vulnerability enables attackers to inject configuration into NGINX, potentially executing arbitrary code in the ingress-nginx controller’s context. This can also result in the disclosure of sensitive secrets accessible to the controller.
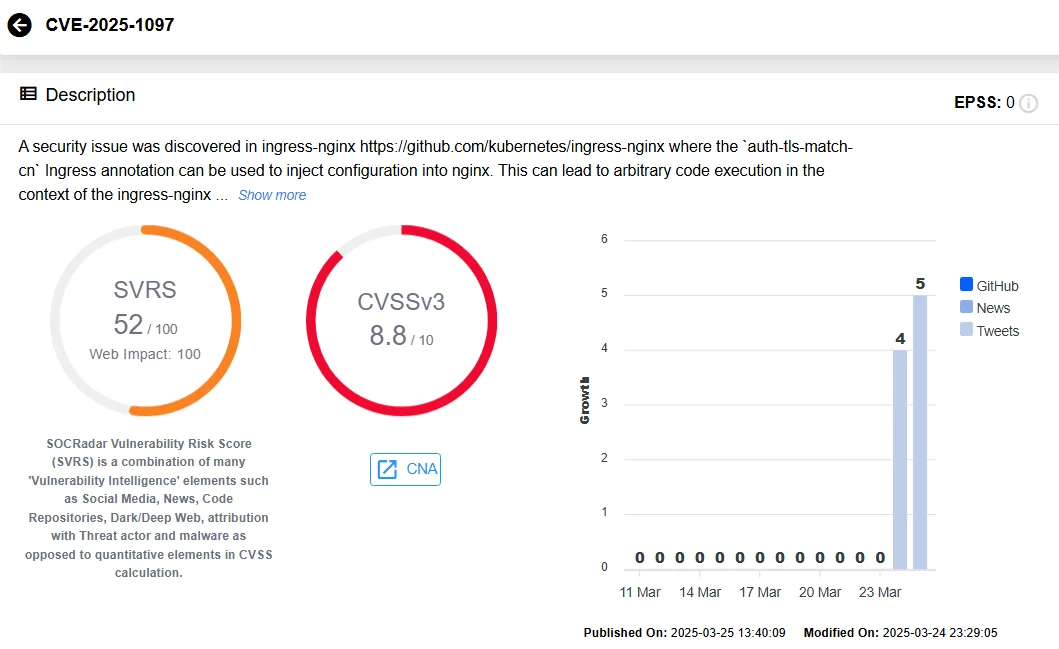
SOCRadar’s Vulnerability Intelligence, CVE-2025-1097
- CVE-2025-1098 (High Severity)
By exploiting the mirror-target and mirror-host Ingress annotations, attackers can inject arbitrary configurations into NGINX. This leads to arbitrary code execution in the ingress-nginx controller and the potential exposure of secrets accessible by the controller.
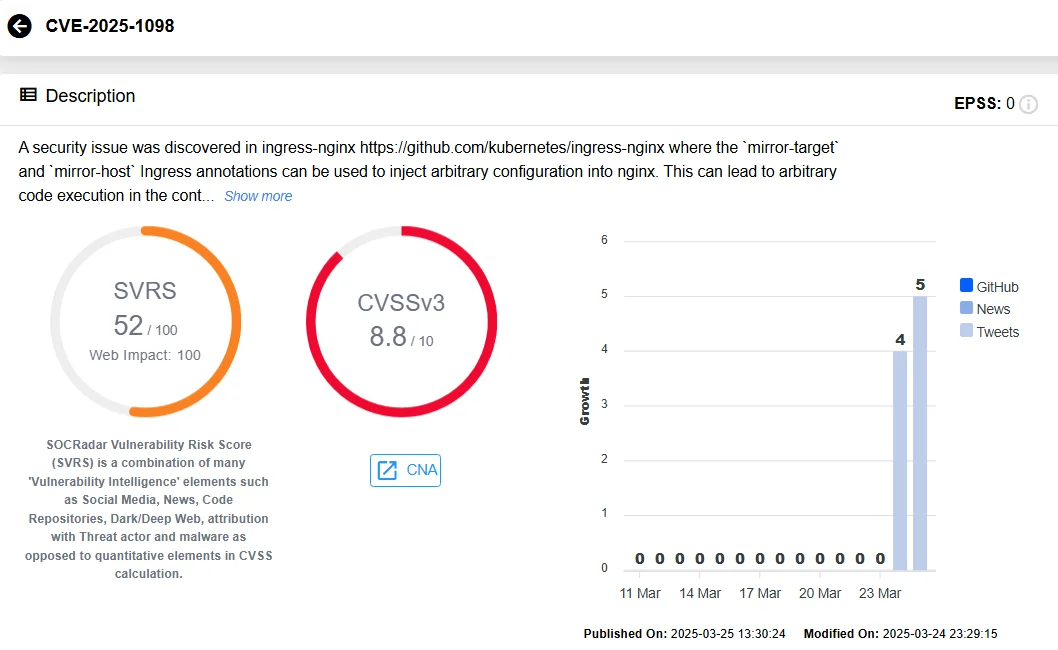
SOCRadar’s Vulnerability Intelligence, CVE-2025-1098
- CVE-2025-24513 (Medium Severity)
This vulnerability arises from improper input validation, potentially leading to directory traversal within the container. When combined with other vulnerabilities, it can result in Denial-of-Service (DoS) or limited exposure of secret objects within the Kubernetes cluster. - CVE-2025-24514 (High Severity)
This vulnerability allows attackers to exploit the auth-url Ingress annotation to inject malicious configurations into NGINX. This could lead to arbitrary code execution within the context of the ingress-nginx controller and provide attackers access to secrets stored in the cluster.
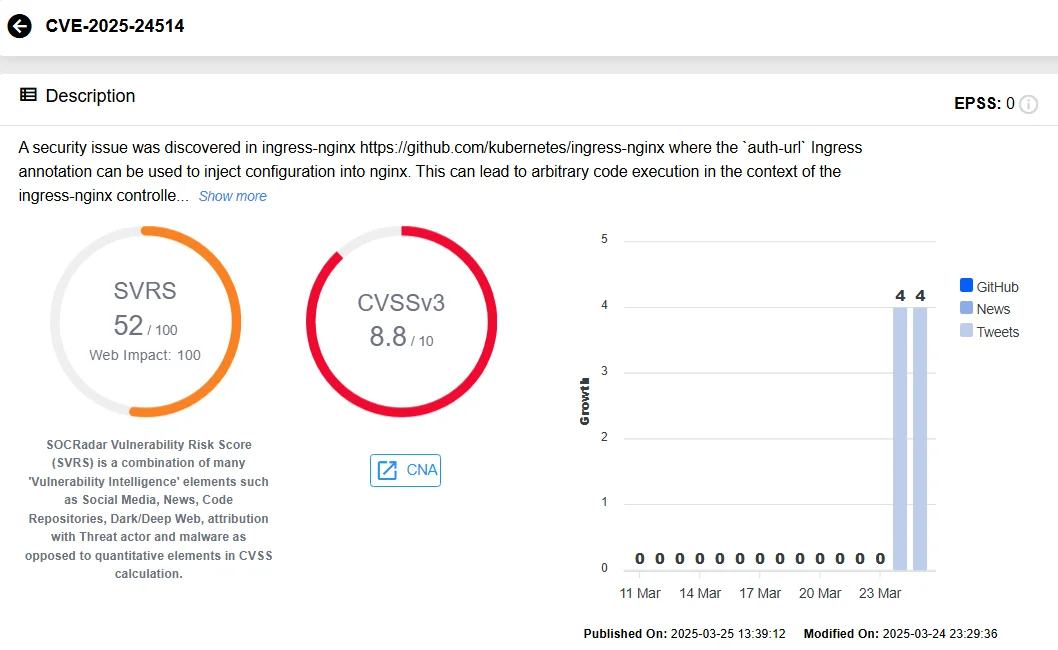
SOCRadar’s Vulnerability Intelligence, CVE-2025-24514
Affected Versions
The vulnerabilities impact ingress-nginx versions:
- All versions prior to v1.11.0
- v1.11.0 to v1.11.4
- v1.12.0
Mitigation Steps
1. Identify Affected Deployments
As suggested by Wiz, to check if ingress-nginx is running in your cluster, execute:
- kubectl get pods –all-namespaces –selector app.kubernetes.io/name=ingress-nginx
2. Upgrade Immediately
Admins should update ingress-nginx to the patched versions as soon as possible:
- v1.12.1
- v1.11.5
3. Temporary Mitigation (If Upgrading is Not Possible)
If an upgrade is not immediately feasible, disable the Validating Admission Controller to mitigate CVE-2025-1974:
- For Helm installations, reinstall with controller.admissionWebhooks.enabled=false.
- For manual installations, delete the ValidatingWebhookConfiguration named ingress-nginx-admission and remove the –validating-webhook argument from the ingress-nginx-controller container’s Deployment or DaemonSet.
Remember to re-enable the Validating Admission Controller after upgrading, as it helps prevent misconfigurations in ingress rules.
For detailed analysis of CVEs, we recommend you to take a look at the researchers’ blog.
Conclusion
The disclosure of these CVEs highlights the ongoing risks associated with misconfigured ingress controllers. Organizations using ingress-nginx should act immediately to patch these vulnerabilities or apply mitigations to secure their Kubernetes clusters from potential exploitation.
For organizations relying on Kubernetes, tools like SOCRadar’s Vulnerability Intelligence and Attack Surface Management (ASM) can help identify and monitor affected assets across your infrastructure.
Proactively identify exposed Kubernetes assets and quickly prioritize remediation efforts to secure your organization against vulnerabilities like CVE-2025-1974, ensuring attackers cannot exploit them before action is taken. (SOCRadar’s ASM)
SOCRadar’s Attack Surface Management (ASM) module provides continuous visibility into your externally exposed assets, including Kubernetes clusters using vulnerable versions of ingress-nginx. It helps security teams detect outdated software, misconfigurations, and exposed services that could be exploited by attackers, enabling proactive risk mitigation.


































