
Renault India Breach, 147M Stealer Logs, Cardinal Health Leak, University ESXi & Saudi Company Access Sales
In the last week, SOCRadar’s Dark Web Team has identified multiple critical cyber threats, including the sale of 147 million stealer logs sourced from platforms like Google Ads and YouTube. Additionally, a customer database from Renault India, containing over 1.3 million records, is being advertised for sale. Other alarming discoveries include unauthorized access to a VMware ESXi server at Heinrich Heine University Düsseldorf, a leaked database from Cardinal Health, and the sale of IT system access for a Saudi Arabian EPC company specializing in Oil & Gas services.
Receive a Free Dark Web Report for Your Organization:
147 Million Lines of Stealer Logs are Allegedly on Sale
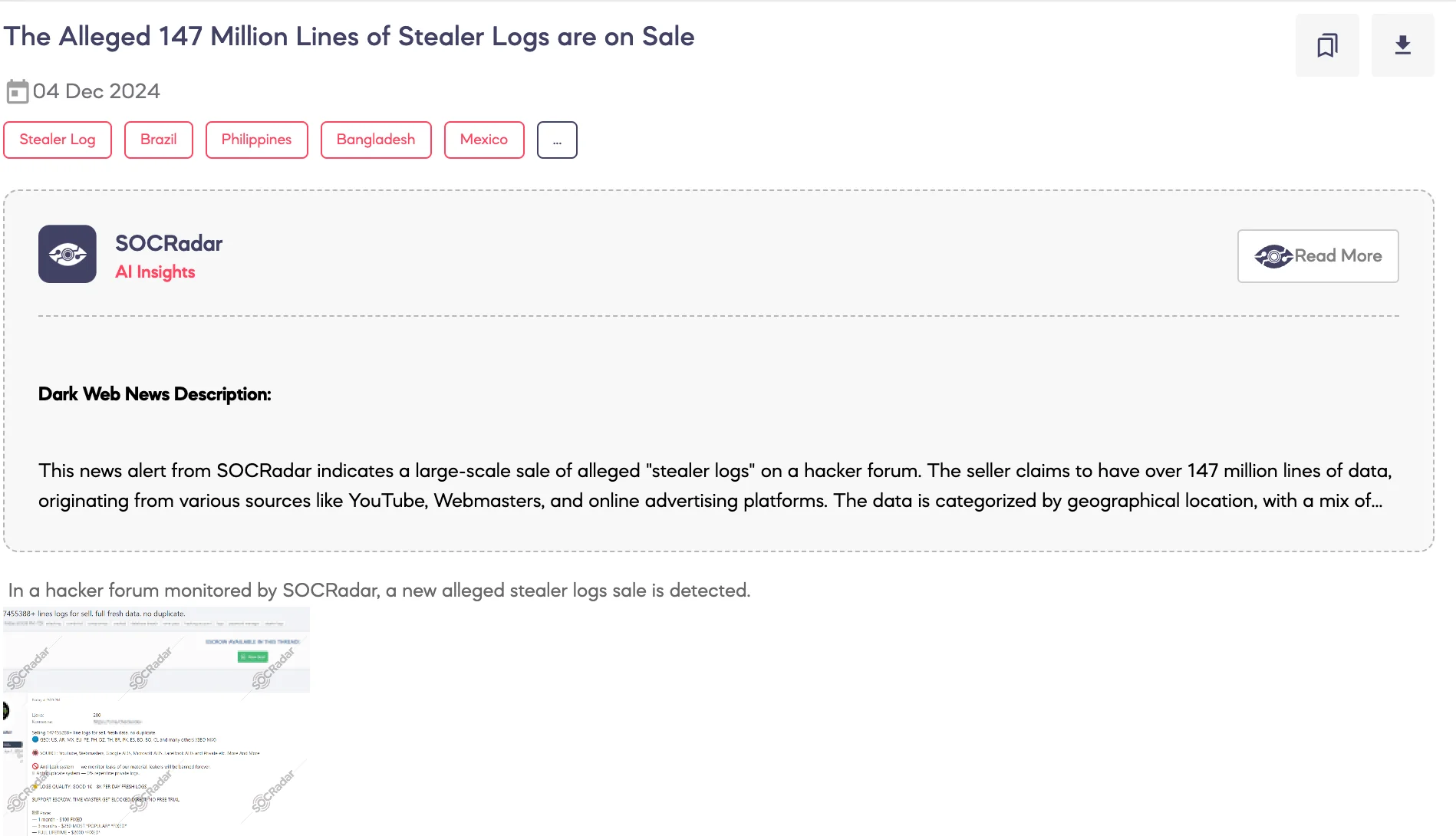
SOCRadar Dark Web Team detected a post on a hacker forum advertising the sale of an alleged database containing over 147 million stealer logs. According to the threat actor, the logs are fresh, free of duplicates, and sourced from platforms such as YouTube, Google Ads, Microsoft Ads, and Facebook Ads. The logs reportedly span various regions, including the United States, Argentina, Mexico, Europe, and more.
The threat actor highlights the use of anti-leak and anti-duplicate systems to maintain exclusivity. Access to the logs is offered at fixed prices, with payment accepted in Bitcoin, USD, and other methods. The post stresses high log quality, regular updates, and strict rules against free trials or non-serious inquiries.
Alleged Customer Database of Renault India is on Sale
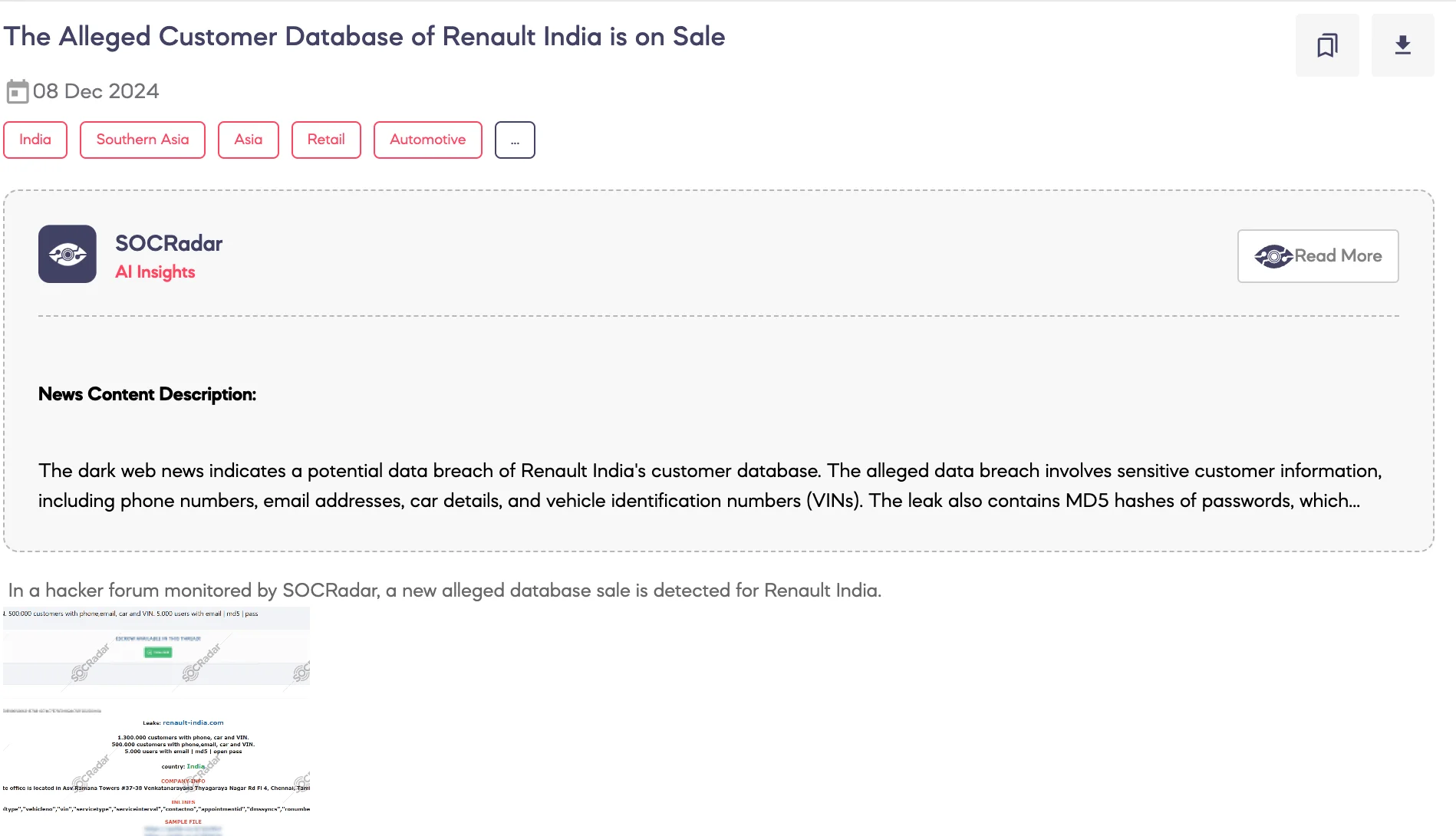
SOCRadar Dark Web Team detected a post on a hacker forum advertising the sale of an alleged customer database from Renault India.
According to the threat actor, the database includes sensitive customer and company information. The data allegedly contains 1.3 million customer records with phone numbers, car details, and Vehicle Identification Numbers (VINs). Additionally, 500,000 records include phone numbers, email addresses, car details, and VINs. Another 5,000 user entries are said to include email addresses with MD5 hashes and open passwords.
Alleged Unauthorized ESXi Access Leak is Detected for the Universität Düsseldorf
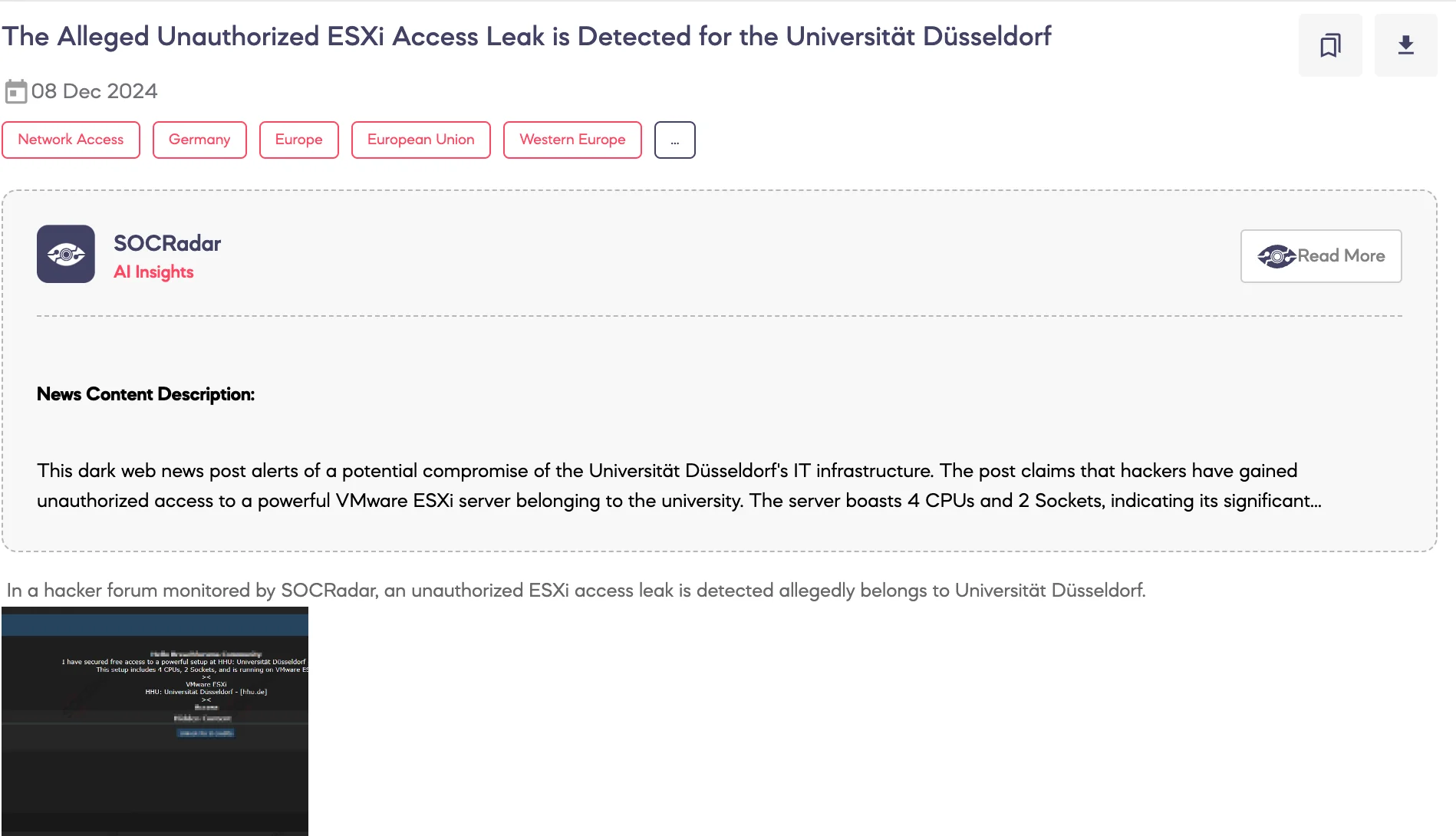
SOCRadar Dark Web Team identified a post on a hacker forum claiming unauthorized access to a VMware ESXi server allegedly belonging to Heinrich Heine University Düsseldorf in Germany. The threat actor claims to have obtained access to a powerful setup that includes 4 CPUs and 2 sockets, hosted on VMware ESXi.
Alleged Unauthorized Access Sale is Detected for a Saudi Arabian EPC Company
SOCRadar Dark Web Team detected a post advertising the alleged unauthorized access sale of IT systems belonging to a major company in Saudi Arabia specializing in engineering, procurement, and construction services, particularly in the Oil & Gas sector.
The threat actor claims to offer full access to the company’s servers for $15,000, with payment to be made through an escrow service for transaction security. They emphasize dealing only with serious buyers, requiring initial contact via TOX messaging. The process includes verification of the buyer, negotiation of terms, and final delivery of access details after payment. This unauthorized access sale poses a significant threat to the targeted company’s operations and data security.
Alleged Database of Cardinal Health is on Sale
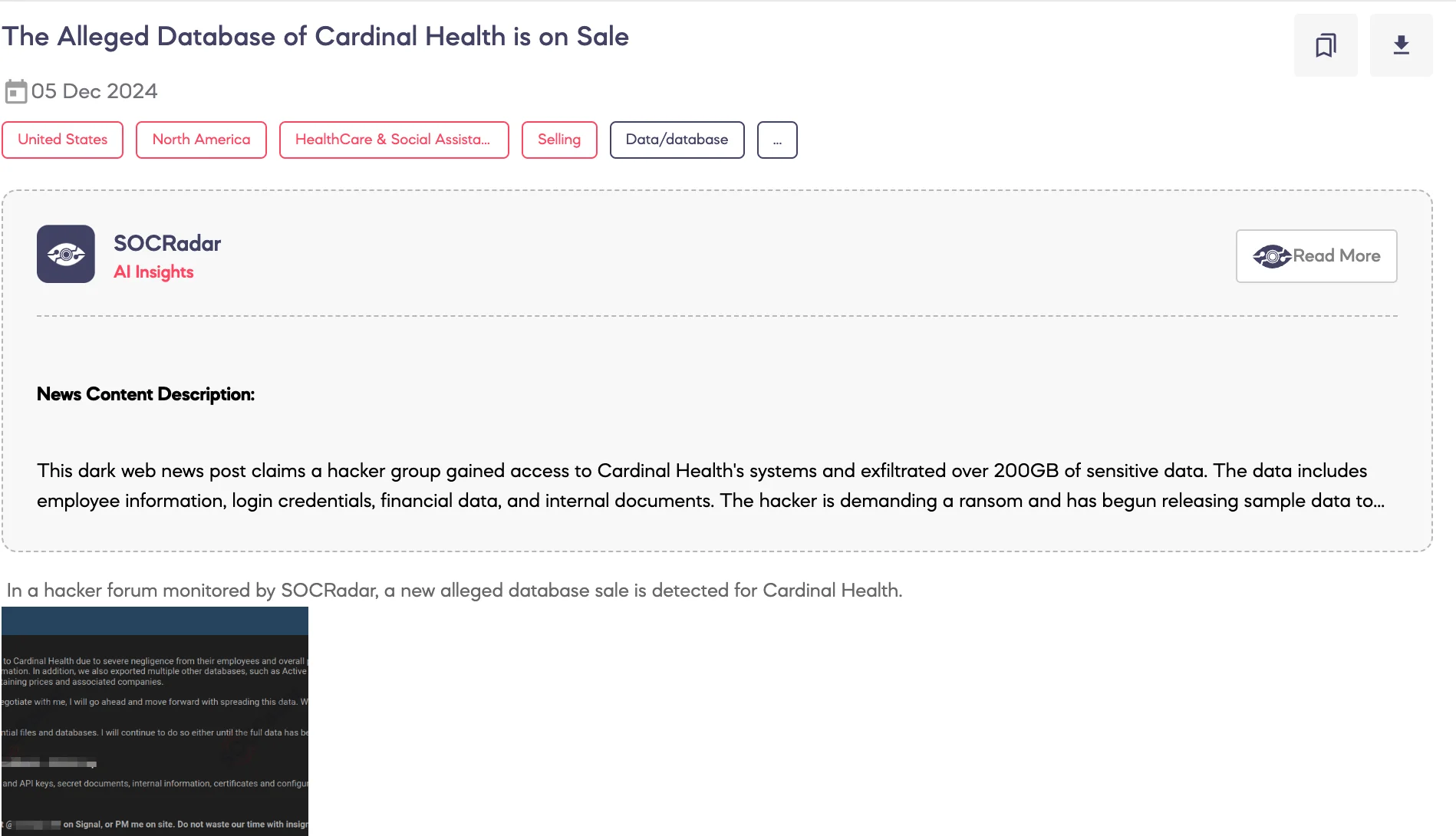
SOCRadar Dark Web team identified a post on a hacker forum advertising the sale of an alleged database associated with Cardinal Health.
According to the threat actor, over 200 gigabytes of sensitive data were exfiltrated from Cardinal Health, citing employee negligence and insufficient security measures. The claimed data includes:
- Active Directory (Microsoft Entra ID) exports containing employee information and details of logged-in devices.
- Delivery-related exports with pricing details and information on associated companies.
- Credentials, API keys, internal documents, certificates, configuration files, scripts, and source code.
- A newsletter database allegedly containing 1.8 million entries.
The threat actor alleges that no effort has been made to address the breach and has stated that further data will be published or sold until an agreement is reached or the full dataset is sold. Prospective buyers are directed to contact the actor through specified channels.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































