SAP November 2023 Security Patch Day: Critical Business One Vulnerability Has Been Fixed (CVE-2023-31403)
SAP, a prominent enterprise software company, has unveiled three new vulnerabilities in its November 2023 Security Patch Day update. The company has also updated security notes for three previously disclosed security vulnerabilities. The most critical issue among the newly revealed vulnerabilities is CVE-2023-31403, an Improper Access Control vulnerability affecting SAP Business One.
SAP Business One, an Enterprise Resource Planning (ERP) application, plays a crucial role in assisting enterprises with the management of various business aspects, spanning financials, purchasing, inventory, sales, customer relationships, analytics, and more.
Details of the Critical SAP Business One Vulnerability (CVE-2023-31403)
The CVE-2023-31403 vulnerability is classified as an Improper Access Control vulnerability, with a critical CVSS rating of 9.6. It affects the SAP Business One, version 10.0. SAP has labeled this vulnerability as ‘Hot News’ in the advisory.
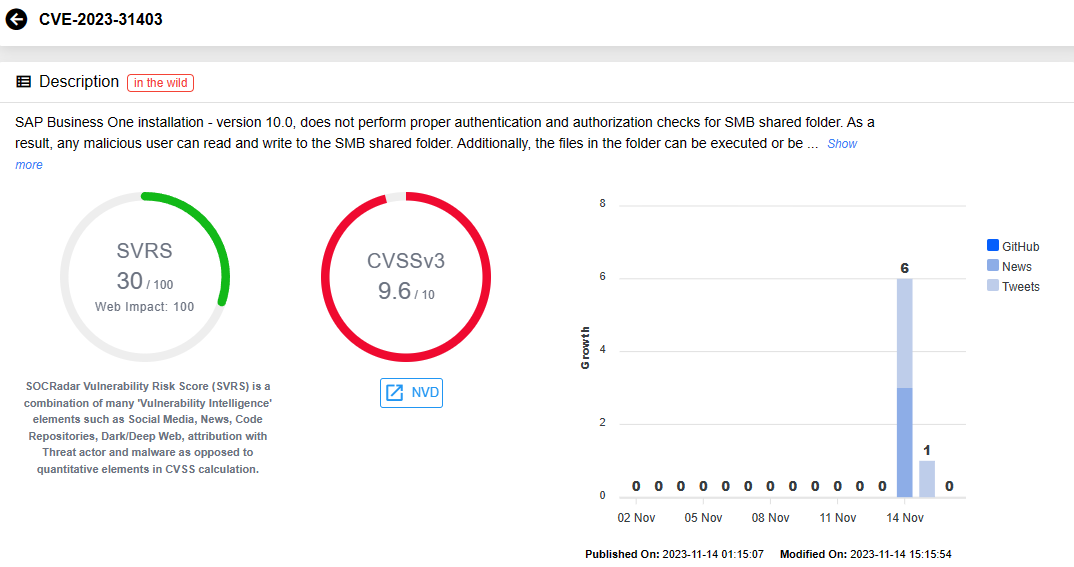
As outlined in the SAP advisory, the specific installation fails to conduct proper authentication and authorization checks for the SMB shared folder, leading to the vulnerability. This oversight allows anonymous users to gain read and write access to the SMB shared folder.
The affected components include the Crystal Report (CR) shared folder, Traditional Mobile app (attachment path), RSP (log folder logic), Job Service, and BAS (file upload folder).
Moreover, the files within the folder can be executed or utilized by the installation process, resulting in a significant impact on confidentiality, integrity, and availability.
Apply the Patches for CVE-2023-31403 in SAP Business One
Security note 3340576 provides a hotfix for SAP Business One version 10.0 SP 2308, while installations on lower support package (SP) levels are also vulnerable to CVE-2023-31403. There are no workarounds available, and SAP advises updating to SAP Business One 10.0 SP 2308 and applying the provided hotfix.
SAP Updates Previously Disclosed Critical Vulnerability: CVE-2023-40309
CVE-2023-40309, also labeled Hot News, carries a critical CVSS score of 9.8 and was initially disclosed and patched with SAP’s September 2023 Patch Day. The vulnerability stems from a missing authorization check, affecting SAP CommonCryptoLib and many other SAP products – find the extensive list of affected products in the advisory, or see here.
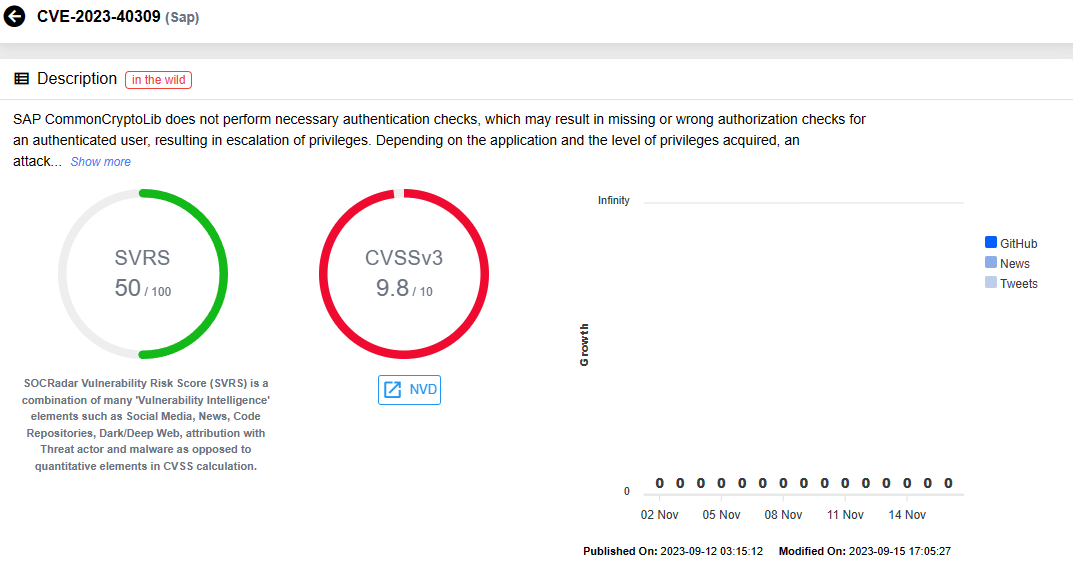
In detail, SAP CommonCryptoLib fails to perform necessary authentication checks, potentially resulting in missing or incorrect authorization checks for an authenticated user, leading to privilege escalation.
It is essential to note that, depending on the application and the level of privileges acquired, an attacker could exploit functionality restricted to a particular user group and read, modify, or delete restricted data, potentially leading to the complete compromise of the affected application.
What Other Vulnerabilities Are Included?
The remaining two new security notes include CVE-2023-41366 and CVE-2023-42480, which are both medium-severity vulnerabilities (with CVSS scores of 5.3). These are Information Disclosure vulnerabilities, residing in NetWeaver Application Server ABAP and ABAP Platform, and NetWeaver AS Java Logon.
The updates further include medium-severity vulnerabilities, CVE-2023-42477, and another one that does not have a CVE identifier (with CVSS scores of 6.5 and 6.3). CVE-2023-42477 is a Server-Side Request Forgery (SSRF) vulnerability residing in NetWeaver AS Java, while the other flaw allows Cross-Site Request Forgery (CSRF) in Sybase products.
Are There Reports of Exploitation? How to Patch These Vulnerabilities?
While there are no reports of exploitation in the wild regarding any of these vulnerabilities, customers are advised to apply the patches as soon as possible.
You can access the full list of vulnerabilities and their respective security notes in the official advisory for SAP Security Patch Day.
How Can SOCRadar Help?
SOCRadar empowers organizations to effectively address vulnerabilities through its Attack Surface Management solution, delivering advanced threat intelligence and monitoring capabilities with real-time alerts.
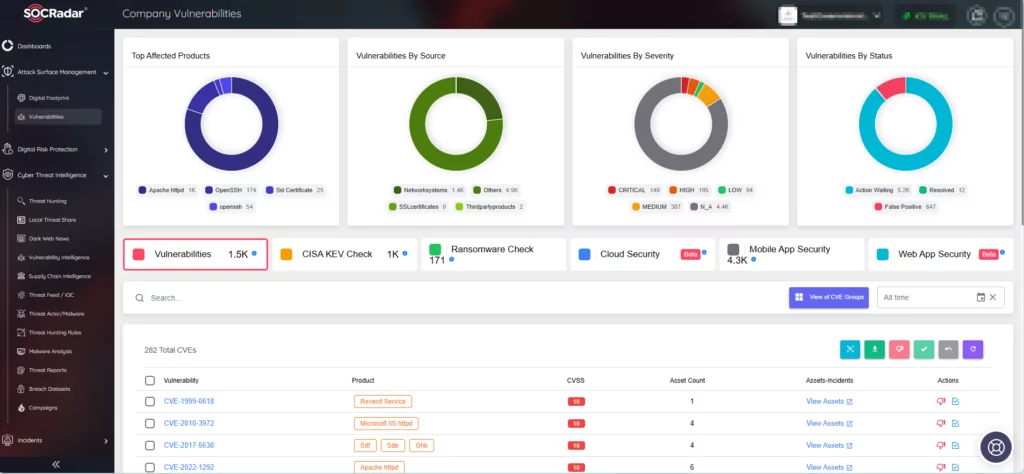
Additionally, SOCRadar’s Vulnerability Intelligence offers an extensive database of known vulnerabilities, providing detailed insights into threat severity, affected systems, and exploitation activity.