
Severe Vulnerabilities in Moby BuildKit and OCI runc: CVE-2024-23651, CVE-2024-23652, CVE-2024-23653, CVE-2024-21626
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert regarding Moby and the Open Container Initiative (OCI) security updates that fix multiple vulnerabilities. The vulnerabilities affect Docker-related components, including Moby BuildKit and OCI runc, and encompass a range of high-severity and critical issues.
The Moby Project (GitHub)
“BuildKit,” developed by Moby, serves as a toolkit designed to efficiently transform source code into build artifacts, while OCI runc functions as a Command-Line Interface (CLI) tool dedicated to initiating and executing containers in line with the OCI specification.
CISA cautions that malicious actors could exploit the vulnerabilities affecting these components to seize control of affected systems. Organizations are strongly advised to examine associated advisories and implement essential security measures.
Details of the Vulnerabilities Affecting Moby BuildKit and OCI runc
The vulnerabilities addressed by Moby and the Open Container Initiative (OCI) are detailed below, along with fixed version information and recommended workarounds:
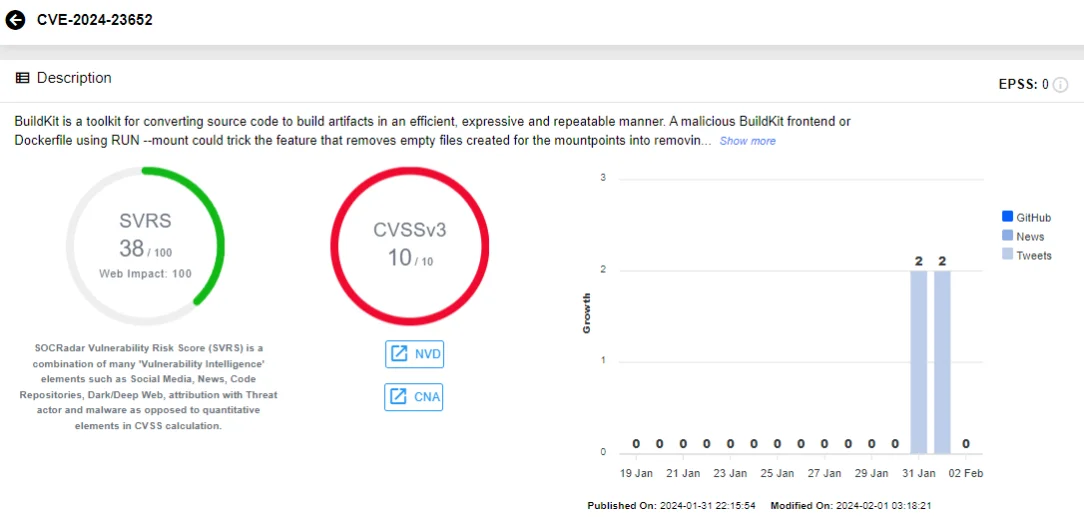
CVE-2024-23652 (CVSS: 10.0, Critical): This vulnerability, with a maximum CVSS score, pertains to a malicious BuildKit frontend or Dockerfile using RUN –mount, which could deceive the feature into removing a file outside the container, on the host system.
SOCRadar vulnerability card for CVE-2024-23652
Moby has resolved this issue in BuildKit v0.12.5. As a workaround measure, it is recommended to refrain from utilizing the BuildKit frontend from untrusted sources or constructing Dockerfiles containing the RUN –mount feature from untrusted origins.
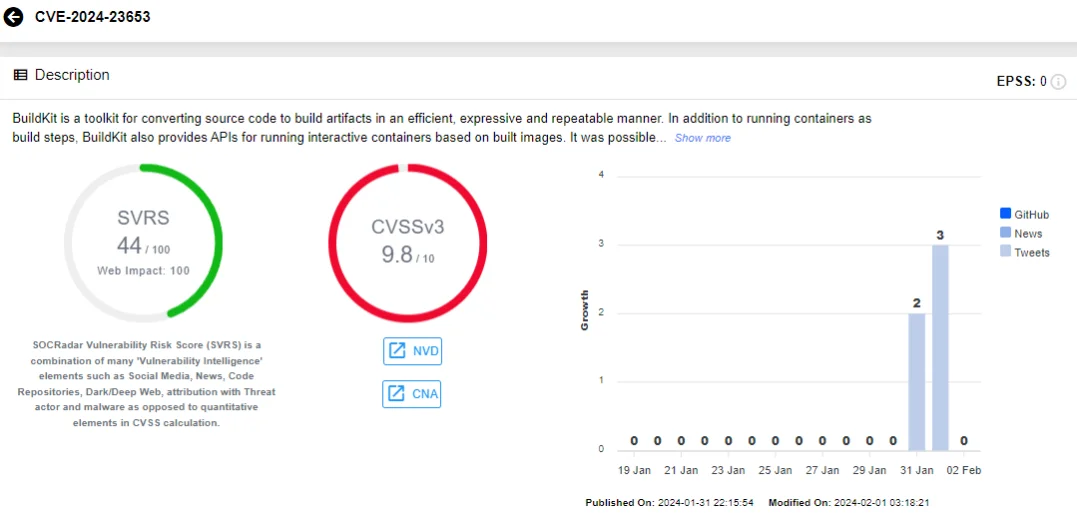
CVE-2024-23653 (CVSS: 9.8, Critical): BuildKit provides APIs for running interactive containers based on built images, which could be exploited to execute a container with elevated privileges.
Usually, running such containers is permitted only if the special security.insecure entitlement is enabled both in the buildkitd configuration and allowed by the user initializing the build request.
SOCRadar vulnerability card for CVE-2024-23653
Moby has addressed this vulnerability in BuildKit v0.12.5. It is advised to refrain from using BuildKit frontends from untrusted sources. Frontend images are typically specified as the #syntax line in your Dockerfile or with the –frontend flag when using the buildctl build command.
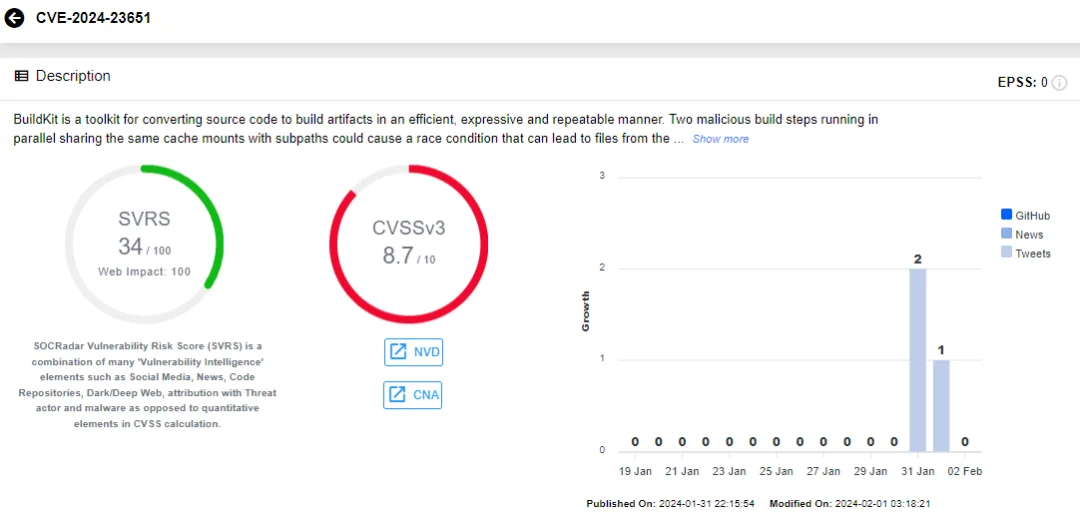
CVE-2024-23651 (CVSS: 8.7, High): Concurrent execution of two malicious build steps, sharing the same cache mounts with subpaths, could trigger a race condition, potentially granting access to files from the host system within the build container.
SOCRadar vulnerability card for CVE-2024-23651
Moby has addressed CVE-2024-23651 in BuildKit v0.12.5 as well. To mitigate this vulnerability, it is advised to avoid using BuildKit frontends from untrusted sources or building Dockerfiles with cache mounts containing –mount=type=cache,source=… options.
CVE-2024-21626 (CVSS: 8.6, High): In runc versions 1.1.11 and earlier, an internal file descriptor leak could be exploited by attackers. This vulnerability could result in a newly-spawned container process from runc exec having a working directory within the host filesystem namespace, facilitating a container escape – the exploitation of this issue varies, and this scenario is known as “attack 2”. Similarly, in “attack 1,” a malicious image could exploit this to grant a container process access to the host filesystem through runc run.
It is explained on the OCI advisory that variants of attack 1 and 2 may also allow the overwrite of semi-arbitrary host binaries, resulting in complete container escapes – these variants are known as “attack 3a” and “attack 3b”.
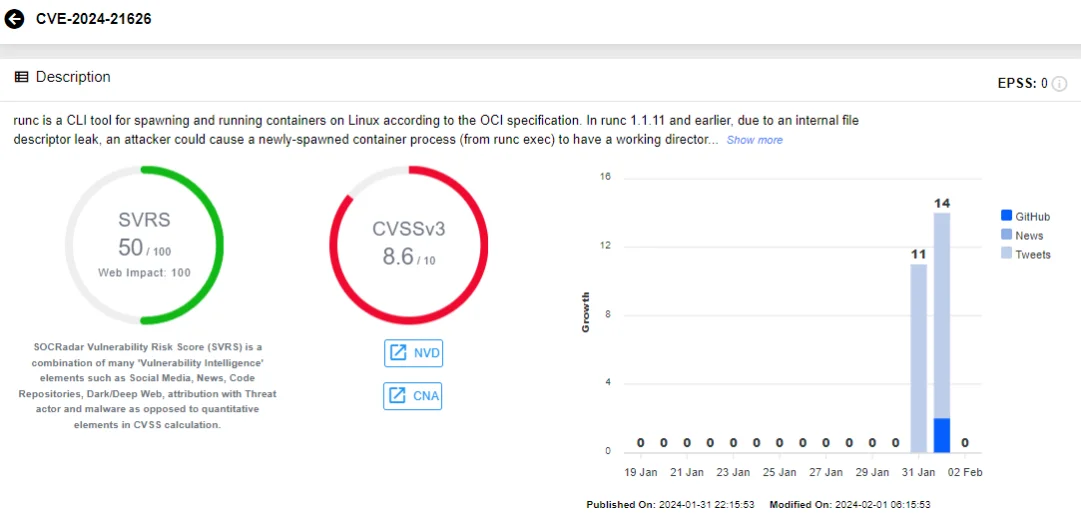
SOCRadar vulnerability card for CVE-2024-21626
OCI implemented patches against CVE-2024-21626 in runc version 1.1.12. Workarounds for this vulnerability vary based on the identified attack methods:
- OCI, against attacks 1 and 2, advises to restrict containers and runc exec to use a process.cwd of /. Since / cannot be replaced with a symlink, the path is resolved from within the container’s mount namespace, preventing changes to the root of a mount namespace or an fs root to a symlink.
- Against attacks 1 and 3a, only allow users to run trusted images.
- Against attack 3b, avoid using runc exec entirely, as any binary executed with runc exec could potentially be a malicious binary target; the advisory states that there is no other workaround available for attack 3b.
For more details on this vulnerability, refer to the GitHub advisory issued by Open Container Initiative (OCI).
You can easily access vulnerability information and updates through the SOCRadar XTI platform – it offers comprehensive Vulnerability Intelligence, providing the latest insights on identified vulnerabilities, ensuring you stay informed about available exploits and hacker trends to be able to enhance your cybersecurity defenses.
SOCRadar Vulnerability Intelligence
Are There Any Reports of Exploitation About the Moby BuildKit or OCI runc Vulnerabilities?
Researchers have not yet discovered any proof of exploitation regarding these new vulnerabilities. Still, it is advisable for organizations to maintain vigilance over their environments and inspect containers until they can apply the patches.
In its alert, CISA advised to review advisories for Moby BuildKit and OCI runc, as well as a research blog for more technical information. You can view the CISA alert here.
SOCRadar’s Attack Surface Management module offers easy access to the tools you need to quickly identify, assess, and mitigate new vulnerabilities. The ASM module provides visibility into asset inventory and components, as well as timely notifications of security issues. These platform alerts provide quick insights, making it easier to manage the response process.
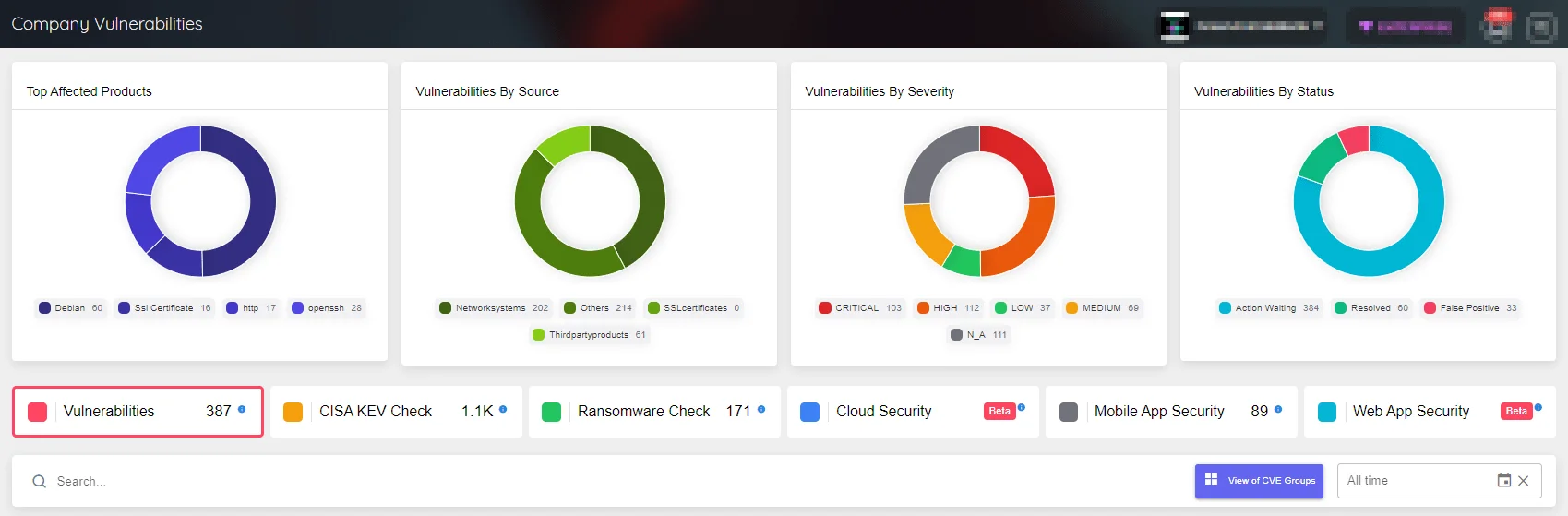
Company Vulnerabilities page under SOCRadar’s ASM




































