Docker Hub Images Expose Secrets and Private Keys, Potentially Leading to Attacks
Researchers at RWTH Aachen University in Germany have conducted a study, revealing that numerous Docker images shared on Docker Hub expose sensitive data. This poses a significant security risk.
Docker Hub, a cloud-based repository, facilitates the widespread use and sharing of Docker images, which contain all the necessary components to run an application. However, there is a risk of users inadvertently or carelessly including private keys or API secrets within the shared images.
The researchers analyzed 337,171 images from Docker Hub and private registries; they found that 8.5% of these images contained sensitive information, including private keys and API secrets, and many of these exposed keys were actively used for malicious purposes.
The study highlights the exposure of confidential information in container images that increases the risk of attacks against software, online platforms, and users.
Near 55K Valid Keys and Secrets Exposed in Docker Images
The researchers compiled 1,647,300 layers from 337,171 Docker images to create a comprehensive dataset, aiming to source the most up-to-date versions from each repository whenever feasible.
The researchers discovered 52,107 valid private keys and 3,158 distinct API secrets exposed in 28,621 Docker images through data analysis using regular expressions to identify specific secrets. It is important to note that the researchers thoroughly verified these figures, removing test keys, example API secrets, and invalid matches.
The vast majority of exposed secrets, precisely 95% of private keys and 90% of API secrets were discovered in single-user images, implying these were most likely unintentional leaks.
Exposure Is More Common on Docker Hub, Rather Than Private Registries
Secret exposure was more common on the Docker Hub platform, with 9% of images affected, compared to 6.3% for images from private registries. This, and the fact that hosting a registry necessitates more advanced technical knowledge, suggests that users of private registries may possess a stronger understanding of container security.
Further investigation uncovered that the exposed private keys had a significant impact, as 22,082 compromised certificates relied on them. The report states that 61% of these certificates were self-signed, while the remaining 39% were signed by certification authorities (CA). Among these leaked CA-signed certificates, 7,546 were signed privately, and 1,060 were signed publicly.
The exposure of CA-signed certificates raises serious concerns because they are widely used and universally accepted. At the time of the study, only 141 of these CA-signed certificates were still valid.
More Than 275K Hosts Rely on Compromised Keys
The researchers analyzed 15 months of internet-wide measurements from the Censys database to assess the real-world impact of the exposed secrets. They found that 275,269 hosts relied on compromised keys.
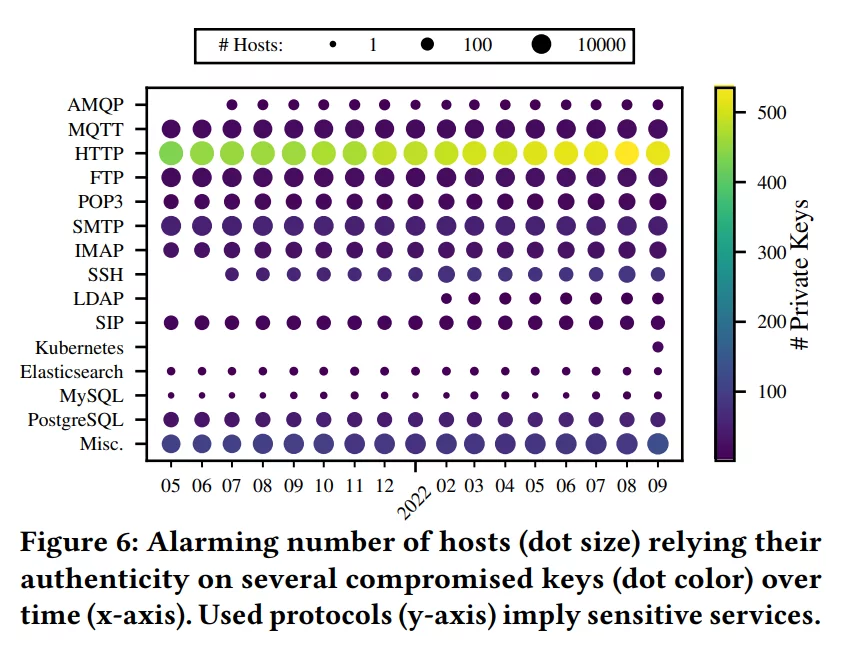
MQTT and AMQP hosts, which may transmit privacy-sensitive Internet of Things (IoT) data, as well as FTP, PostgreSQL, Elasticsearch, and MySQL instances that may contain confidential data, were among the hosts. The study mentions that due to leaked private keys, SIP hosts used for telephony and SMTP, POP3, and IMAP servers used for email services included in these hosts are vulnerable to impersonation attacks, allowing attackers to eavesdrop, relay, or alter sensitive data transmitted.
Lastly, researchers discovered SSH servers and Kubernetes instances with leaked keys, which may allow remote-shell access, botnet expansion, and unauthorized access to data.
Safeguard Repositories with SOCRadar
The extensive disclosure of confidential information highlights a significant problem in container security, emphasizing the utmost importance of being thorough when creating and sanitizing images to eliminate all secrets.
The analysis of API secrets revealed nearly 3,000 containers associated with cloud providers like Amazon AWS and financial services such as Stripe.
You can utilize SOCRadar’s platform to check for data and secret exposures, and search public buckets and code repositories.

Furthermore, you can use SOCRadar’s Cloud Security Module (CSM) to receive alerts when a bucket’s status changes from private to public, allowing you to mitigate the risk of exposing your data in a timely manner.




































