
SmoothOperator Supply Chain Attack Targeting 3CX VOIP Desktop Client
[Update] June 21, 2023: Researchers found exposed Elasticsearch and Kibana instances of a third-party vendor of 3CX. Find under the subheading: “3CX Third-Party Exposes Elasticsearch and Kibana Instances.”
[April 24, 2023] Update: Mandiant’s research delved deeper into the 3CX supply chain exploit scheme and discovered the initial intrusion vector to be a malware-infected package from another website. The package was distributed through a previous software supply chain compromise which involved an altered installer for X_TRADER, a software package available on Trading Technologies’ website. According to researchers, this is the first time a software supply chain attack has been followed by another. Researchers also discovered a multi-stage modular backdoor named VEILEDSIGNAL. Its modules were deployed as a result of a complicated loading process.
[Update] April 12, 2023: 3CX confirmed on April 11 that a North Korean hacking group carried it out. Mandiant’s investigation attributes the attack to UNC4736, which has ties to North Korea. The 3CX systems were compromised by the attackers using a malware strain called TAXHAUL (or TxRLoader), which then deployed a second malware downloader called Coldcat. Additionally, the attackers targeted macOS systems in the attack, infecting them with a backdoor malware named Simplesea.
[Update] April 7, 2023 – Update 7 Windows Electron App build number 18.12.424 has been checked by the 3CX’s advisor Mandiant who found no evidence of compromise. Due to certificate changes, the company had to update the naming convention. They re-opened the build to address this. Build 18.12.425 has been created and released. You can read the most up-to-date information here.
[Update] April 1, 2023 – 3CX CEO, Nick Galea, published a security incident update. CEO suggests uninstalling 3CX Electron Desktop Application from all Windows or MacOS computers; continuing AV scans and EDR solutions in your organization’s networks for any potential malware with the latest signatures. He reminds switching to the PWA Web Client App rather than the Desktop App.
[Update] March 31, 2023 – Google has invalidated 3CX’s software security certificate. This means the MSI DesktopApp files that the company released after March 30 afternoon can no longer be downloaded via Google Chrome (nor can the originally infected MSI files). Furthermore, several AV vendors are blocking any software signed with the old security certificate of the company.
[Update] March 30, 2023 – 3CX has appointed Mandiant to conduct a full investigation.
3CX Third-Party Exposes Elasticsearch and Kibana Instances
The researchers recently discovered open Elasticsearch and Kibana instances belonging to a third-party vendor of 3CX. The exposed data consisted of call metadata, license activation keys, and encoded database connection strings.
The discovery came to light on May 15, 2023, merely two months after the initial attacks were publicly disclosed. This incident raises concerns about how 3CX handles cyberattacks and the effectiveness of the security measures they put in place to safeguard sensitive data.
According to the researchers, attackers could have exploited the exposed data in various ways:
- The call metadata provides attackers with insights into the behavior of callers, including information about who called whom and the duration of the calls. This data can reveal call patterns and frequency, indicating the organization’s overall health.
- Exposed license keys allow attackers to use 3CX software without payment while possibly enabling them to sync data between devices during activation and grant unauthorized access to user data.
- Exposed database connection strings pose the greatest danger as they allow unauthorized individuals to access the database and manipulate stored data through actions like reading, copying, modifying, or deleting.
After notifying 3CX, it was revealed that a third-party vendor hosted and managed the exposed instances, though ownership was unclear. Subsequently, authentication was implemented on the instances, indicating the involvement of another third-party. After the involvement of multiple vendors, the issue was eventually resolved within a week.
1 – What is SmoothOperator Supply Chain Attack, When was the Trojanized Version of 3CX VOIP Desktop Client Released, What is it Used For, and Why is it so Important?
The SmoothOperator supply chain attack is a campaign that targets the 3CX VOIP software clients, including top brands like American Express, AirFrance, BMW, Toyota, Mercedes, the National Health Service, and Coca-Cola.
It first appeared under a Reddit thread“SITUATIONAL AWARENESS // CrowdStrike Tracking Active Intrusion Campaign Targeting 3CX Customers” that raised the concern: “Falcon OverWatch observed unexpected malicious activity emanating from a legitimate, signed binary, 3CXDesktopApp — a softphone application from 3CX. The malicious activity includes beaconing to actor-controlled infrastructure, deployment of second-stage payloads, and, in a small number of cases, hands-on-keyboard activity.”
Customers have noted that these security alerts are triggered after installing certain versions of the 3CXDesktopApp software, such as versions 18.12.407 and 18.12.416 for Windows and 18.11.1213, and the latest version for macOS. The attack on the supply chain commenced with downloading the MSI installer from 3CX’s original website or installing an update on an already installed desktop application.
The 3CX support identified these alerts as false positives in a forum thread where customers reported them, and the company has yet to publicly acknowledge the problems.
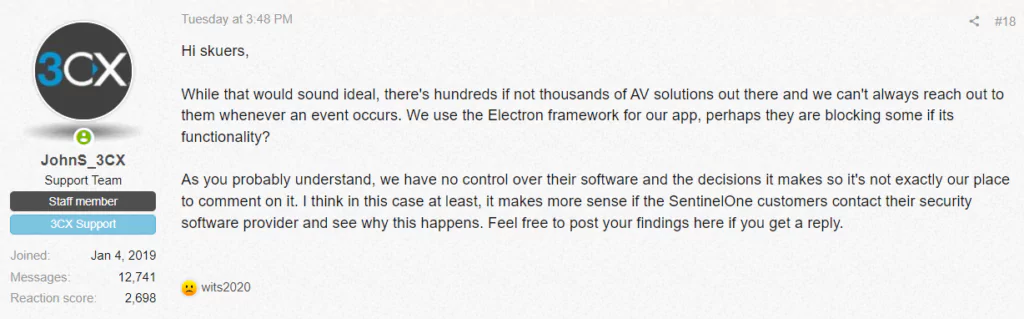
The SmoothOperator targets the 3CX VOIP software used by clients of 3CX more than the company itself. The trojanized application included in the attack attempts to access browser profiles and hands-on keyboard activities of infected systems.
As of the time of writing, Shodan, a search engine for internet-connected devices, reports that 242,519 IP addresses are using the trojanized 3CX Phone System Management Console. This indicates that a significant number of systems may be at risk of compromise from the attack.
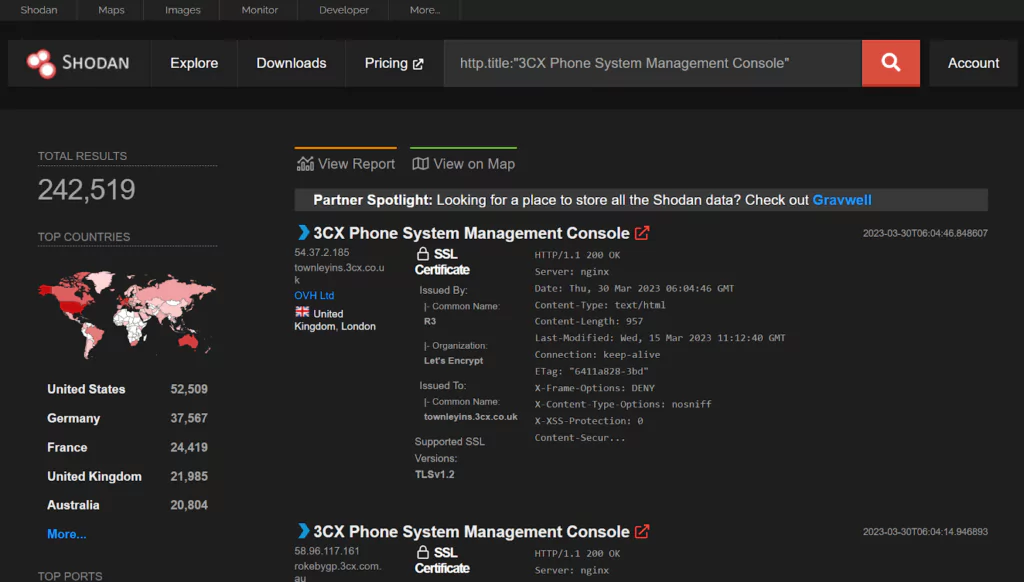
According to the attacked company, their phone systems are widely used by over 600,000 businesses globally. Many affected organizations highlight the seriousness of the attack and the need for organizations to take proactive measures to protect against supply chain attacks.
2 – How Critical is the Compromise Detected in 3CX VOIP Desktop Client?
The compromise detected in the 3CX VOIP Desktop Client is very critical because it allows attackers to change downloadable files on the company’s website / distribute a software update that includes a backdoor to steal information or compromise systems. This situation can cause serious harm to the affected organizations and put their data and privacy at risk.
3 – How Does the Attack Work?
The attack is initiated by installing the MSI installer from 3CX’s website or updating an existing application. Upon installation, the trojanized software connects to an infrastructure controlled by a threat actor to launch the attack.
The software proceeds to extract two DLL files: ffmpeg.dll and d3dcompiler_47.dll. The first file, ffmpeg.dll, is sideloaded and runs the encrypted payload from the second DLL, d3dcompiler_47.dll.
Next, the malware retrieves icon files (*.ICO) from GitHub, which contain Base64 encoded strings at the end of the images that serve as instructions. Using these instructions, the malware downloads the final payload.
The final payload is downloaded as a DLL and is a new information-stealer malware designed to target stored credentials and other information in user profiles of Chrome, Edge, Brave, and Firefox browsers.
In some instances, the attackers directly interact with the system and use an interactive command shell after successfully exploiting it.
4 -Which Products and Systems that You Use May be Affected by This Compromise? Which 3CX VOIP Desktop Client Versions are Affected?
The Windows version was initially thought to be the only OS affected, but macOS installers are also affected.
The version numbers announced by 3CX are:
- Electron Windows App shipped in Update 7, version numbers 18.12.407 & 18.12.416
- Electron Mac App version numbers 18.11.1213, 18.12.402, 18.12.407 & 18.12.416
5-How to Protect From This Attack? Are There Any Additional Solutions Other Than Patching?
At the moment, the affected company has not provided an official update to fix the issue. In the statement by 3CX, company said that the new Windows Application is in progress and recommended using the PWA App. Since the PWA App is web-based, there is no danger of installing a trojanized installer, and it can do much the same job as the Electron app.
As a precaution, they recommended removing any trojanized applications from your system and further scanning your system with an up to date antivirus software. However, some good news: the GitHub repository used by the malicious executable has been removed, and traffic between the malicious file and the repository has been disconnected, making subsequent malicious file downloads unlikely. This is a positive step towards preventing further damage from the attack.
6-How did the 3CX VOIP Desktop Client get Trojanized?
The 3CX VOIP Desktop Client became trojanized application after signed by the company’s certificate obtained by hackers; then, it was delivered by threat actors through the company’s website and update channels. The attackers compromised a legitimate 3CX update server and distributed a malicious version of the software that included a backdoor.
It is still not clear how the attackers were able to obtain the code signing certificates of the company or how they were able to deliver the malicious MSI file through the company website and update channel. The attack highlights the importance of protecting against supply chain attacks, which can be difficult to detect and can have severe consequences for affected organizations.
7-How Can You Determine Whether Your Systems are Affected by Looking at the Logs?
Besides the icons hosted on GitHub, the researchers have identified a list of domains that could indicate compromise (IOCs). The attacker controls these domains, and the trojanized version of 3CX’s desktop client will connect to one of these domains:
- akamaicontainer[.]com
- akamaitechcloudservices[.]com
- azuredeploystore[.]com
- azureonlinecloud[.]com
- azureonlinestorage[.]com
- dunamistrd[.]com
- glcloudservice[.]com
- qwepoi123098[.]com
- sbmsa[.]wiki
- sourceslabs[.]com
- visualstudiofactory[.]com
- msedgepackageinfo[.]com
- msstorageazure[.]com
- msstorageboxes[.]com
- msboxonline[.]com
- officeaddons[.]com
- officestoragebox[.]com
- pbxcloudeservices[.]com
- pbxphonenetwork[.]com
- zacharryblogs[.]com
- pbxsources[.]com
- journalide[.]org
Several customers have reported that the desktop client attempted to connect to domains such as azureonlinestorage[.]com, msstorageboxes[.]com, and msstorageazure[.]com.
For security reasons using the above domain addresses, organizations should look at their DNS and proxy records and add rules to detect and block systems that try or may contact these addresses.
As for IoC, the trojanized applications’ hash values are as follows:
3CXDesktopApp.exe SHA256 hashes
a60a61bf844bc181d4540c9fac53203250a982e7c3ad6153869f01e19cc36203 (18.12.416)
5d99efa36f34aa6b43cd81e77544961c5c8d692c96059fef92c2df2624550734 (18.12.416)
54004dfaa48ca5fa91e3304fb99559a2395301c570026450882d6aad89132a02 (18.12.407)
d45674f941be3cca2fbc1af42778043cc18cd86d95a2ecb9e6f0e212ed4c74ae (18.12.407)
3CXDesktopApp MSI Installer SHA256 hashes
aa124a4b4df12b34e74ee7f6c683b2ebec4ce9a8edcf9be345823b4fdcf5d868
59e1edf4d82fae4978e97512b0331b7eb21dd4b838b850ba46794d9c7a2c0983
3CXDesktopApp macOS SHA256 hashes
92005051ae314d61074ed94a52e76b1c3e21e7f0e8c1d1fdd497a006ce45fa61
b86c695822013483fa4e2dfdf712c5ee777d7b99cbad8c2fa2274b133481eadb
3CXDesktopApp macOS DMG Installer hashes
5407cda7d3a75e7b1e030b1f33337a56f293578ffa8b3ae19c671051ed314290
E6bbc33815b9f20b0cf832d7401dd893fbc467c800728b5891336706da0dbcec
It’s important to exercise caution until the vendor of the affected software announces that everything is under their control and they have taken all necessary precautions to clean artifacts of the attack. As the attackers were able to sign the malicious executable and distribute it through the company’s website and update channel, it’s possible that the hashes of the trojanized application could have been changed. This could make it more difficult to detect and protect against the attack, highlighting the importance of remaining vigilant and taking proactive measures to protect against potential threats.
8-Are There Any Rules to Detect and Prevent Trojanized Software for Systems Such as IPS, SIEM?
Researchers have created a YARA Rule that organizations can customize according to their needs. Yara Rules are malware detection patterns that can be used against such targeted attacks or threats.
Yara rule created for SmoothOperator:
rule Malware_dprk_3cx
{
meta:
author = "HuntressLabs"
created = "2023/03/30"
strings:
$ffmpeg = {41 f7 da 44 01 d2 ff c2 4c 63 ca 46 8a 94 0c 50 03 00 00 45 00 d0 45 0f b6 d8 42 8a ac 1c 50 03 00 00 46 88 94 1c 50 03 00 00 42 88 ac 0c 50 03 00 00 42 02 ac 1c 50 03 00 00 44 0f b6 cd 46 8a 8c 0c 50 03 00 00}
$s1 = "D3dcompiler_47.dll" ascii
$s2 = "3jB(2bsG#@c7" ascii
$ror = {41 c1 cb 0d 0f be 03 48 ff c3 44 03 d8 80 7b ff 00}
$header = {31 32 30 30 20 32 34 30 30 20 22 4d 6f 7a 69 6c 6c 61 2f 35 2e 30 20 28 57 69 6e 64 6f 77 73 20 4e 54 20 31 30 2e 30 3b 20 57 69 6e 36 34 3b 20 78 36 34 29 20 41 70 70 6c 65 57 65 62 4b 69 74 2f 35 33 37 2e 33 36 20 28 4b 48 54 4d 4c 2c 20 6c 69 6b 65 20 47 65 63 6b 6f 29 20 33 43 58 44 65 73 6b 74 6f 70 41 70 70 2f 31 38 2e 31 31 2e 31 31 39 37 20 43 68 72 6f 6d 65 2f 31 30 32 2e 30 2e 35 30 30 35 2e 31 36 37 20 45 6c 65 63 74 72 6f 6e}
$downloader1 = {33 c1 41 69 d0 7d 50 bf 12 45 8b d1 83 c3 10 4c 0f af d7 49 c1 e9 20 81 c2 87 d6 12 00 4d 03 d1 44 69 ca 7d 50 bf 12}
$github = "https://raw.githubusercontent.com/IconStorages/" wide nocase
condition:
$ffmpeg or ($s1 and $s2) or ($ror and $header) or $downloader1 or $github
}To find TAXHAUL (TxRLoader), you can apply the following YARA rule:
rule TAXHAUL
{
meta:
author = "Mandiant"
created = "04/03/2023"
modified = "04/03/2023"
version = "1.0"
strings:
$p00_0 = {410f45fe4c8d3d[4]eb??4533f64c8d3d[4]eb??4533f64c8d3d[4]eb}
$p00_1 = {4d3926488b01400f94c6ff90[4]41b9[4]eb??8bde4885c074}
condition:
uint16(0) == 0x5A4D and any of them
}
YARA rules created for VEILEDSIGNAL:
rule M_Hunting_VEILEDSIGNAL_1
{
meta:
author = "Mandiant"
disclaimer = "This rule is meant for hunting and is not tested to run in a production environment"
md5 = "404b09def6054a281b41d309d809a428, c6441c961dcad0fe127514a918eaabd4"
strings:
$rh1 = { 68 5D 7A D2 2C 3C 14 81 2C 3C 14 81 2C 3C 14 81 77 54 10 80 26 3C 14 81 77 54 17 80 29 3C 14 81 77 54 11 80 AB 3C 14 81 D4 4C 11 80 33 3C 14 81 D4 4C 10 80 22 3C 14 81 D4 4C 17 80 25 3C 14 81 77 54 15 80 27 3C 14 81 2C 3C 15 81 4B 3C 14 81 94 4D 1D 80 28 3C 14 81 94 4D 14 80 2D 3C 14 81 94 4D 16 80 2D 3C 14 81 }
$rh2 = { 00 E5 A0 2B 44 84 CE 78 44 84 CE 78 44 84 CE 78 1F EC CA 79 49 84 CE 78 1F EC CD 79 41 84 CE 78 1F EC CB 79 C8 84 CE 78 BC F4 CA 79 4A 84 CE 78 BC F4 CD 79 4D 84 CE 78 BC F4 CB 79 65 84 CE 78 1F EC CF 79 43 84 CE 78 44 84 CF 78 22 84 CE 78 FC F5 C7 79 42 84 CE 78 FC F5 CE 79 45 84 CE 78 FC F5 CC 79 45 84 CE 78}
$rh3 = { DA D2 21 22 9E B3 4F 71 9E B3 4F 71 9E B3 4F 71 C5 DB 4C 70 94 B3 4F 71 C5 DB 4A 70 15 B3 4F 71 C5 DB 4B 70 8C B3 4F 71 66 C3 4B 70 8C B3 4F 71 66 C3 4C 70 8F B3 4F 71 C5 DB 49 70 9F B3 4F 71 66 C3 4A 70 B0 B3 4F 71 C5 DB 4E 70 97 B3 4F 71 9E B3 4E 71 F9 B3 4F 71 26 C2 46 70 9F B3 4F 71 26 C2 B0 71 9F B3 4F 71 9E B3 D8 71 9F B3 4F 71 26 C2 4D 70 9F B3 4F 71 }
$rh4 = { CB 8A 35 66 8F EB 5B 35 8F EB 5B 35 8F EB 5B 35 D4 83 5F 34 85 EB 5B 35 D4 83 58 34 8A EB 5B 35 D4 83 5E 34 09 EB 5B 35 77 9B 5E 34 92 EB 5B 35 77 9B 5F 34 81 EB 5B 35 77 9B 58 34 86 EB 5B 35 D4 83 5A 34 8C EB 5B 35 8F EB 5A 35 D3 EB 5B 35 37 9A 52 34 8C EB 5B 35 37 9A 58 34 8E EB 5B 35 37 9A 5B 34 8E EB 5B 35 37 9A 59 34 8E EB 5B 35 }
condition:
uint16(0) == 0x5A4D and uint32(uint32(0x3C)) == 0x00004550 and 1 of ($rh*)
}
rule M_Hunting_VEILEDSIGNAL_2
{
meta:
author = "Mandiant"
disclaimer = "This rule is meant for hunting and is not tested to run in a production environment"
md5 = "404b09def6054a281b41d309d809a428"
strings:
$sb1 = { C1 E0 05 4D 8? [2] 33 D0 45 69 C0 7D 50 BF 12 8B C2 41 FF C2 C1 E8 07 33 D0 8B C2 C1 E0 16 41 81 C0 87 D6 12 00 }
$si1 = "CryptBinaryToStringA" fullword
$si2 = "BCryptGenerateSymmetricKey" fullword
$si3 = "CreateThread" fullword
$ss1 = "ChainingModeGCM" wide
$ss2 = "__tutma" fullword
condition:
(uint16(0) == 0x5A4D) and (uint32(uint32(0x3C)) == 0x00004550) and (uint16(uint32(0x3C)+0x18) == 0x020B) and all of them
}
rule M_Hunting_VEILEDSIGNAL_3
{
meta:
author = "Mandiant"
disclaimer = "This rule is meant for hunting and is not tested to run in a production environment"
md5 = "c6441c961dcad0fe127514a918eaabd4"
strings:
$ss1 = { 61 70 70 6C 69 63 61 74 69 6F 6E 2F 6A 73 6F 6E 2C 20 74 65 78 74 2F 6A 61 76 61 73 63 72 69 70 74 2C 20 2A 2F 2A 3B 20 71 3D 30 2E 30 31 00 00 61 63 63 65 70 74 00 00 65 6E 2D 55 53 2C 65 6E 3B 71 3D 30 2E 39 00 00 61 63 63 65 70 74 2D 6C 61 6E 67 75 61 67 65 00 63 6F 6F 6B 69 65 00 00 }
$si1 = "HttpSendRequestW" fullword
$si2 = "CreateNamedPipeW" fullword
$si3 = "CreateThread" fullword
$se1 = "DllGetClassObject" fullword
condition:
(uint16(0) == 0x5A4D) and (uint32(uint32(0x3C)) == 0x00004550) and (uint16(uint32(0x3C)+0x18) == 0x020B) and all of them
}
rule M_Hunting_VEILEDSIGNAL_4
{
meta:
author = "Mandiant"
disclaimer = "This rule is meant for hunting and is not tested to run in a production environment"
md5 = "404b09def6054a281b41d309d809a428, c6441c961dcad0fe127514a918eaabd4"
strings:
$sb1 = { FF 15 FC 76 01 00 8B F0 85 C0 74 ?? 8D 50 01 [6-16] FF 15 [4] 48 8B D8 48 85 C0 74 ?? 89 ?? 24 28 44 8B CD 4C 8B C? 48 89 44 24 20 }
$sb2 = { 33 D2 33 C9 FF 15 [4] 4C 8B CB 4C 89 74 24 28 4C 8D 05 [2] FF FF 44 89 74 24 20 33 D2 33 C9 FF 15 }
$si1 = "CreateThread" fullword
$si2 = "MultiByteToWideChar" fullword
$si3 = "LocalAlloc" fullword
$se1 = "DllGetClassObject" fullword
condition:
(uint16(0) == 0x5A4D) and (uint32(uint32(0x3C)) == 0x00004550) and (uint16(uint32(0x3C)+0x18) == 0x020B) and all of them
}
rule M_Hunting_VEILEDSIGNAL_5
{
meta:
author = "Mandiant"
disclaimer = "This rule is meant for hunting and is not tested to run in a production environment"
md5 = "6727284586ecf528240be21bb6e97f88"
strings:
$sb1 = { 48 8D 15 [4] 48 8D 4C 24 4C E8 [4] 85 C0 74 ?? 48 8D 15 [4] 48 8D 4C 24 4C E8 [4] 85 C0 74 ?? 48 8D 15 [4] 48 8D 4C 24 4C E8 [4] 85 C0 74 ?? 48 8D [3] 48 8B CB FF 15 [4] EB }
$ss1 = "chrome.exe" wide fullword
$ss2 = "firefox.exe" wide fullword
$ss3 = "msedge.exe" wide fullword
$ss4 = "\.pipe*" ascii fullword
$ss5 = "FindFirstFileA" ascii fullword
$ss6 = "Process32FirstW" ascii fullword
$ss7 = "RtlAdjustPrivilege" ascii fullword
$ss8 = "GetCurrentProcess" ascii fullword
$ss9 = "NtWaitForSingleObject" ascii fullword
condition:
(uint16(0) == 0x5A4D) and (uint32(uint32(0x3C)) == 0x00004550) and (uint16(uint32(0x3C)+0x18) == 0x020B) and all of them
}
rule M_Hunting_VEILEDSIGNAL_6
{
meta:
author = "Mandiant"
disclaimer = "This rule is meant for hunting and is not tested to run in a production environment"
md5 = "00a43d64f9b5187a1e1f922b99b09b77"
strings:
$ss1 = "C:Programdata" wide
$ss2 = "devobj.dll" wide fullword
$ss3 = "msvcr100.dll" wide fullword
$ss4 = "TpmVscMgrSvr.exe" wide fullword
$ss5 = "MicrosoftWindowsTPM" wide fullword
$ss6 = "CreateFileW" ascii fullword
condition:
(uint16(0) == 0x5A4D) and (uint32(uint32(0x3C)) == 0x00004550) and (uint16(uint32(0x3C)+0x18) == 0x010B) and all of them
}
MITRE ATT&CK® Techniques
|
Tactic |
Technique ID |
Technique Name |
|
Initial Access |
Supply Chain Compromise |
|
|
Execution |
User Execution: Malicious File |
|
|
Defense Evasion |
Deobfuscate/Decode Files or Information Obfuscated Files or Information Hijack Execution Flow: DLL Side-Loading Virtualization/Sandbox Evasion: Time-Based Evasion |
|
|
Credential Access |
Credentials from Password Stores Steal Web Session Cookie |
|
|
Command and Control |
Application Layer Protocol |
9- Are There Any Ransomware Gangs, APT Groups, or Botnet Actively Using Trojanized 3CX VOIP Desktop Clients?
While security researchers have not yet established an absolute relationship, CrowdStrike researchers claim that the attack is linked to APT, codenamed Labyrinth Chollima, which is affiliated with the notorious North Korean Lazarus Group.
10 – What is next?
In a highly interconnected world, it’s not always possible to prevent the domino effect of attacks, as seen in this case. It’s not enough to simply secure oneself; the entire ecosystem in which we live must also be secure. While this may be an ideal scenario, taking proactive measures is essential to minimize the risk of potential attacks.
One critical step in achieving this is to remain vigilant and proactive against possible threats around us. SOCRadar’s Supply Chain Intelligence offers a valuable tool for organizations to stay informed about events and be alerted to potential threats.
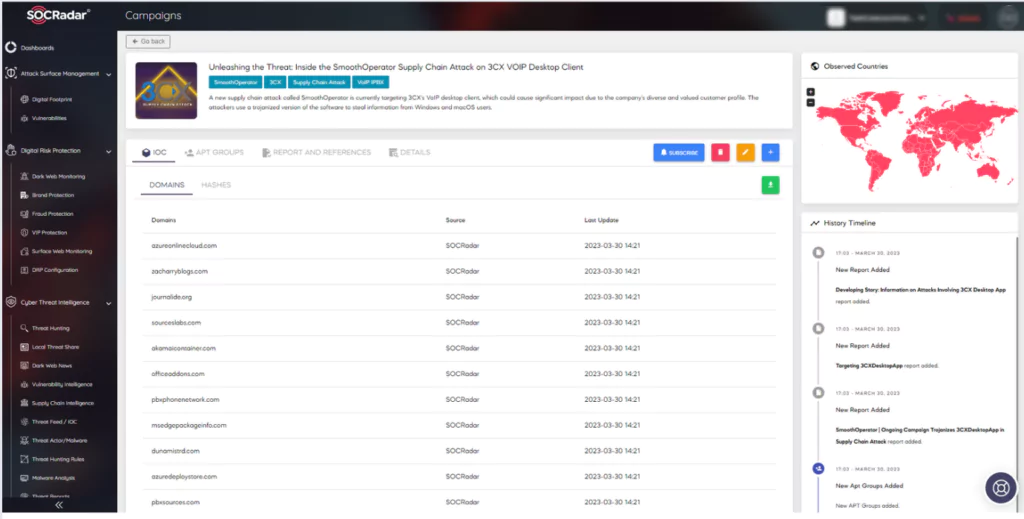
By staying current on the latest threats and taking proactive steps to protect against them, organizations can help minimize the risk of attacks and protect themselves and their customers from potentially serious harm.
The Supply Chain Intelligence feature in SOCRadar provides real-time updates on cybersecurity incidents related to other businesses.
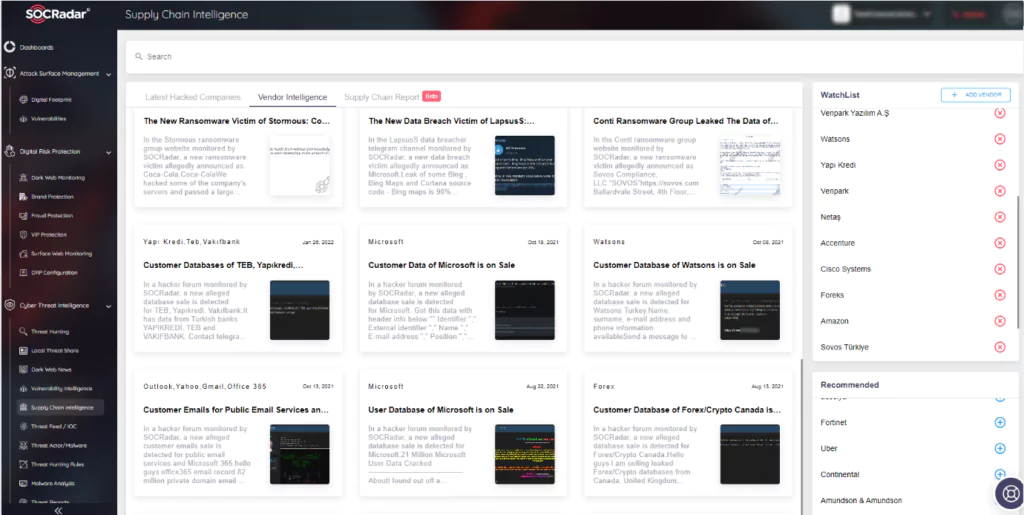
Users can also add specific businesses to a WatchList to monitor potential hacker campaigns targeting partners or vendors. This feature helps prevent incidents that may arise due to third-party involvement.



































