
SOCRadar Technical Whitepaper: ‘Snapshot of 70 Million Stealer Logs’
SOCRadar’s first technical white paper is out!
Here are some highlights:
- Threat actors created fake data to increase the number of records.
- Stealer software commonly runs in the Downloads folder and AppData/temp directories.
- Corporate credentials compromised by attackers can target these organizations in future attacks.
Cyber-attack threats loom more significant as the world becomes increasingly digitized. One of the most insidious forms of cyber-attack is using stealer software to obtain sensitive data, including corporate credentials.
In this article, we will explore the dangers of fake data and how stealer software can be used to obtain it. You can get detailed information by downloading our first technical white paper on Stealer Logs.

Fake data is a growing problem in today’s digital landscape. With so much online information, it can be difficult to distinguish between real and fake data. This is particularly true regarding corporate credentials, often targeted by cybercriminals seeking access to sensitive information.
One way that cybercriminals obtain corporate credentials is through the use of stealer software. Stealer software is a type of malware that is designed to steal sensitive information from a victim’s computer. This can include everything from login credentials to credit card numbers.
Stealer Malware On The Rise
The prevalence of stealer software is alarming. According to a report by SOCRadar Threat Research Team, over 70 million stealer log records were analyzed in March 2023 alone. This highlights just how widespread this type of malware has become.
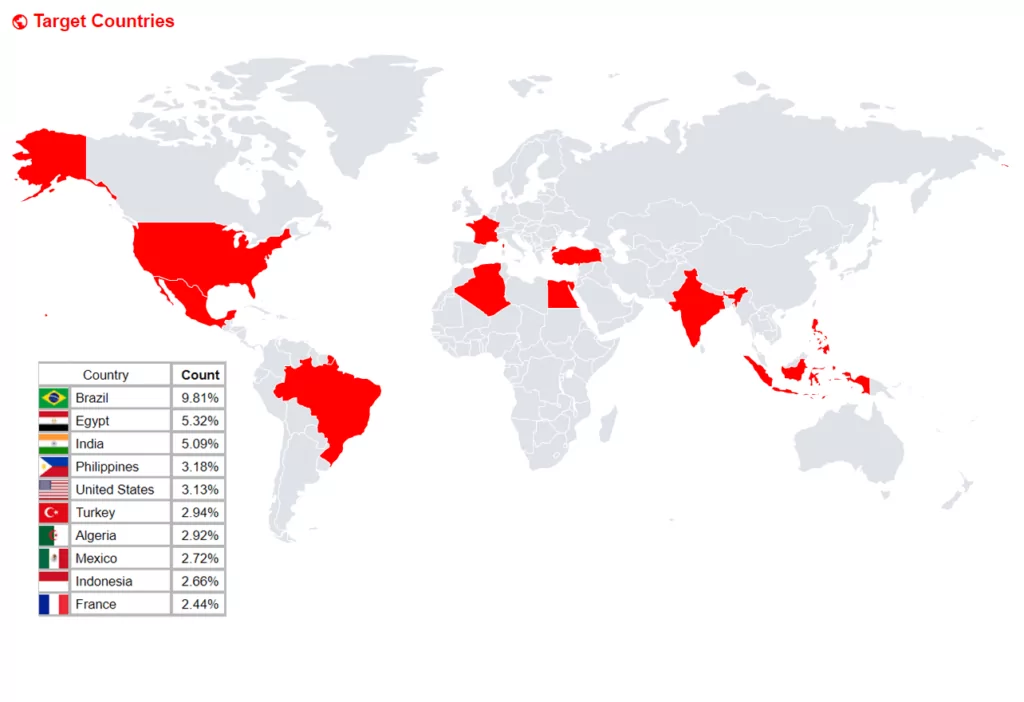
One reason for the popularity of stealer software is its ease of use. Cybercriminals do not need any special skills or knowledge to use this type of malware. They simply need to download and run it on their victim’s computer.
Once installed, stealer software can collect a wide range of information from a victim’s computer. This includes login credentials for various websites and applications and personal information such as credit card numbers and social security numbers.
The implications of this are significant for both individuals and corporations alike. For individuals, having their personal information stolen can lead to identity theft and financial loss. For corporations, having their credentials stolen can lead to data breaches and other security incidents that can have far-reaching consequences.
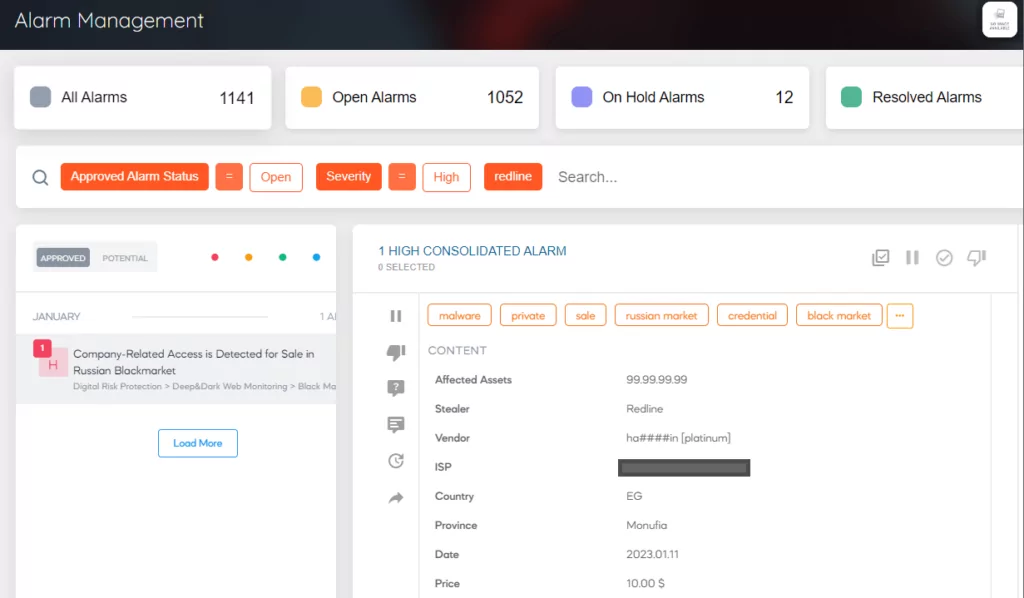
To protect against these types of attacks, it is important for individuals and corporations to take proactive measures. This includes using strong passwords, enabling two-factor authentication, and keeping software up-to-date with the latest security patches.
In addition to these measures, knowing the signs of a potential stealer attack is important. These can include unusual activity on your computer, such as programs running in the background or files being deleted without your knowledge.
If you suspect your computer has been infected with stealer software, it is important to act immediately. This may include running a malware scan on your computer or contacting a cybersecurity professional for assistance.
the threat of fake data and stealer software is a serious one that cannot be ignored. As more and more information is stored online, it is essential that individuals and corporations take steps to protect themselves from these types of attacks.
This includes being vigilant about your computer’s security and using strong passwords and two-factor authentication whenever possible. It also means staying up-to-date with the latest security patches and knowing the signs of a potential stealer attack.
By taking these steps, we can help to protect ourselves and our organizations from the growing threat of cyber-attacks. While there is no foolproof way to prevent all attacks, we can minimize our risk and keep our data safe by being proactive and staying informed.
SOCRadar regularly analyzes the threats mentioned in the report to inform its customers and help them provide a more secure business environment. As a result of this research conducted by the SOCRadar Threat Research Team, the research areas in the expanded stealer logs contribute to the enrichment of SOCRadar’s automated scans.



































