
Exploited SonicWall Zero-Day and Multiple QNAP Vulnerabilities Demand Immediate Action
Significant security vulnerabilities have been discovered, affecting SonicWall and QNAP products. These flaws, including a critical zero-day in SonicWall appliances and multiple vulnerabilities in QNAP’s Rsync implementation, could lead to Remote Code Execution (RCE) and unauthorized system compromise if left unpatched. Administrators are urged to apply the necessary patches immediately to protect their systems and data from potential exploitation.
A Closer Look at the SonicWall Zero-Day Vulnerability: CVE-2025-23006
SonicWall has issued a critical advisory regarding a pre-authentication deserialization vulnerability, tracked as CVE-2025-23006 (CVSS 9.8), affecting its SMA1000 Appliance Management Console (AMC) and Central Management Console (CMC). This vulnerability allows remote unauthenticated attackers to execute arbitrary OS commands under specific conditions.
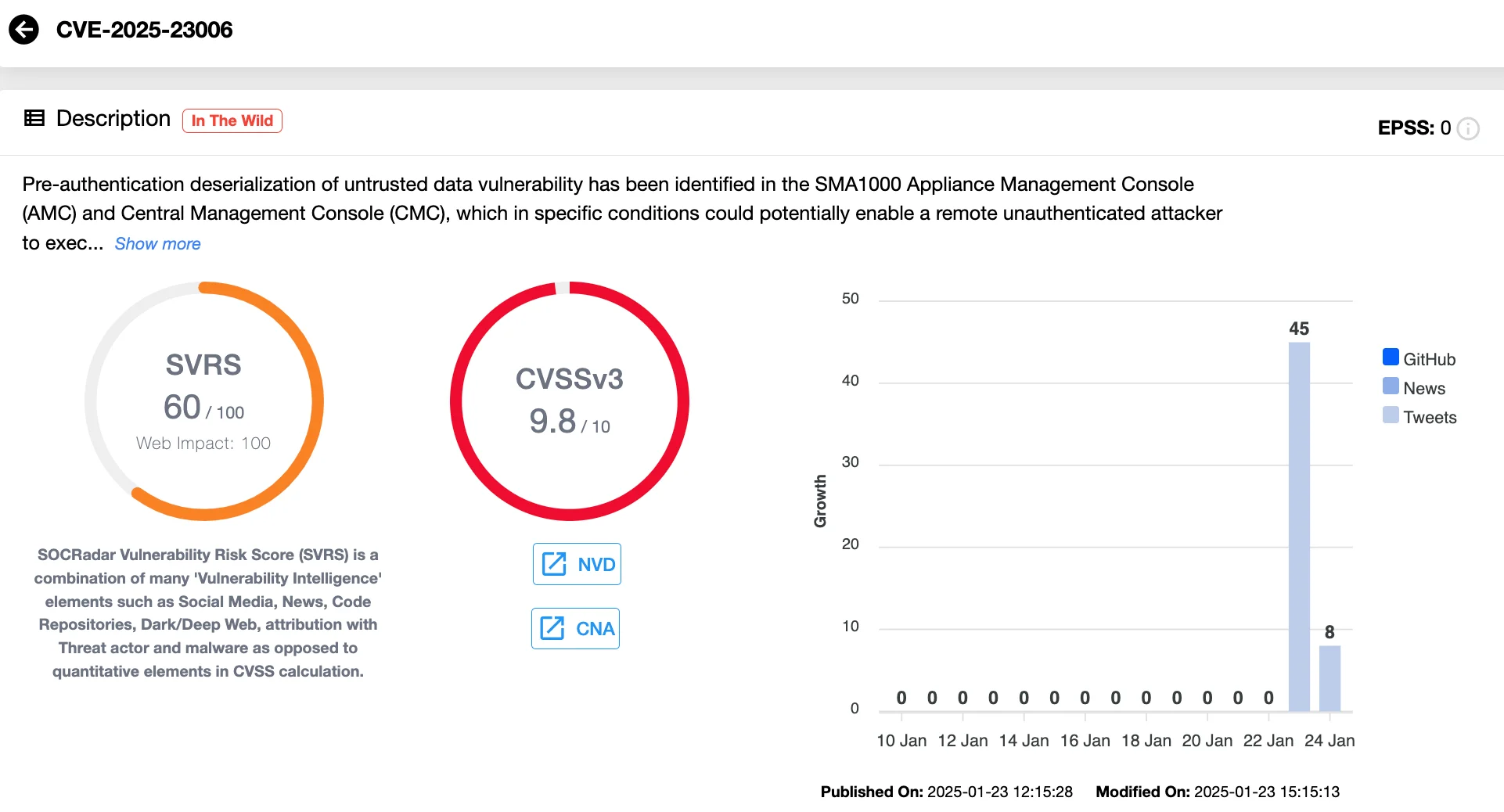
Vulnerability card of CVE-2025-23006 (SOCRadar Vulnerability Intelligence)
Active Exploitation as a Zero-Day
This zero-day vulnerability requires immediate patching to mitigate risks effectively. SonicWall’s Product Security Incident Response Team (PSIRT) has confirmed ongoing exploitation by threat actors, heightening the importance of prompt action.
Affected firmware versions include all releases up to 12.4.3-02804. SonicWall advises immediate upgrades to version 12.4.3-02854 or later to mitigate the risk.
Who’s Impacted?
While this vulnerability poses a severe risk to users of the SMA1000 series, SonicWall clarified that the issue does not affect SMA 100 series products. Administrators should also restrict access to AMC and CMC interfaces to trusted sources as an additional precaution.
How Can You Mitigate CVE-2025-23006?
System administrators should:
- Update to firmware version 12.4.3-02854 or higher.
- Follow the Best Practices for Securing the Appliance outlined in SonicWall’s administration guide.
- In the SonicWall advisory, Microsoft Threat Intelligence Center (MSTIC) is credited with discovering this vulnerability. Therefore, it is advisable to follow any updates by MSTIC for further details on exploitation activity.
In light of recent security vulnerabilities like the SonicWall zero-day, organizations must recognize emerging threats.
SOCRadar’s Vulnerability Intelligence, provided under the Cyber Threat Intelligence module, provides real-time tracking of CVEs, actionable insights, and early detection of emerging threats. With the ability to detect active exploits, monitor new CVEs, and assess the risk level of your infrastructure, SOCRadar’s platform empowers your team to address vulnerabilities before they’re exploited. Ensure your systems are protected with continuous updates and instant alerts for critical threats.
Identify, Track, and Mitigate Vulnerabilities Proactively with SOCRadar’s Vulnerability Intelligence.
Key features of Vulnerability Intelligence include:
- Real-time CVE tracking and risk analysis,
- Detection of active exploits and POCs,
- Alerts for new vulnerabilities and exploits,
- Prioritize vulnerabilities based on severity and impact.
Ensure your systems remain secure and minimize risk exposure with SOCRadar’s Vulnerability Intelligence. Proactively defend against the vulnerabilities discussed in this article and beyond.
QNAP Tackles HBS 3 Security Risks with Fixes for Rsync Vulnerabilities
QNAP has addressed six vulnerabilities, ranging from critical to medium severity, in its HBS 3 Hybrid Backup Sync, a solution for data backup and disaster recovery. The affected versions include HBS 3 Hybrid Backup Sync 25.1.x, with fixes available in version 25.1.4.952 and later.
Key Vulnerabilities in QNAP’s Rsync Implementation: CVE-2024-12084 and CVE-2024-12085
Two vulnerabilities, CVE-2024-12084 and CVE-2024-12085, are particularly noteworthy, as they bear critical and high-severity ratings:
- CVE-2024-12084 (CVSS 9.8): A heap buffer overflow vulnerability in the Rsync daemon, which could allow attackers to write out-of-bounds data, potentially leading to Remote Code Execution (RCE).
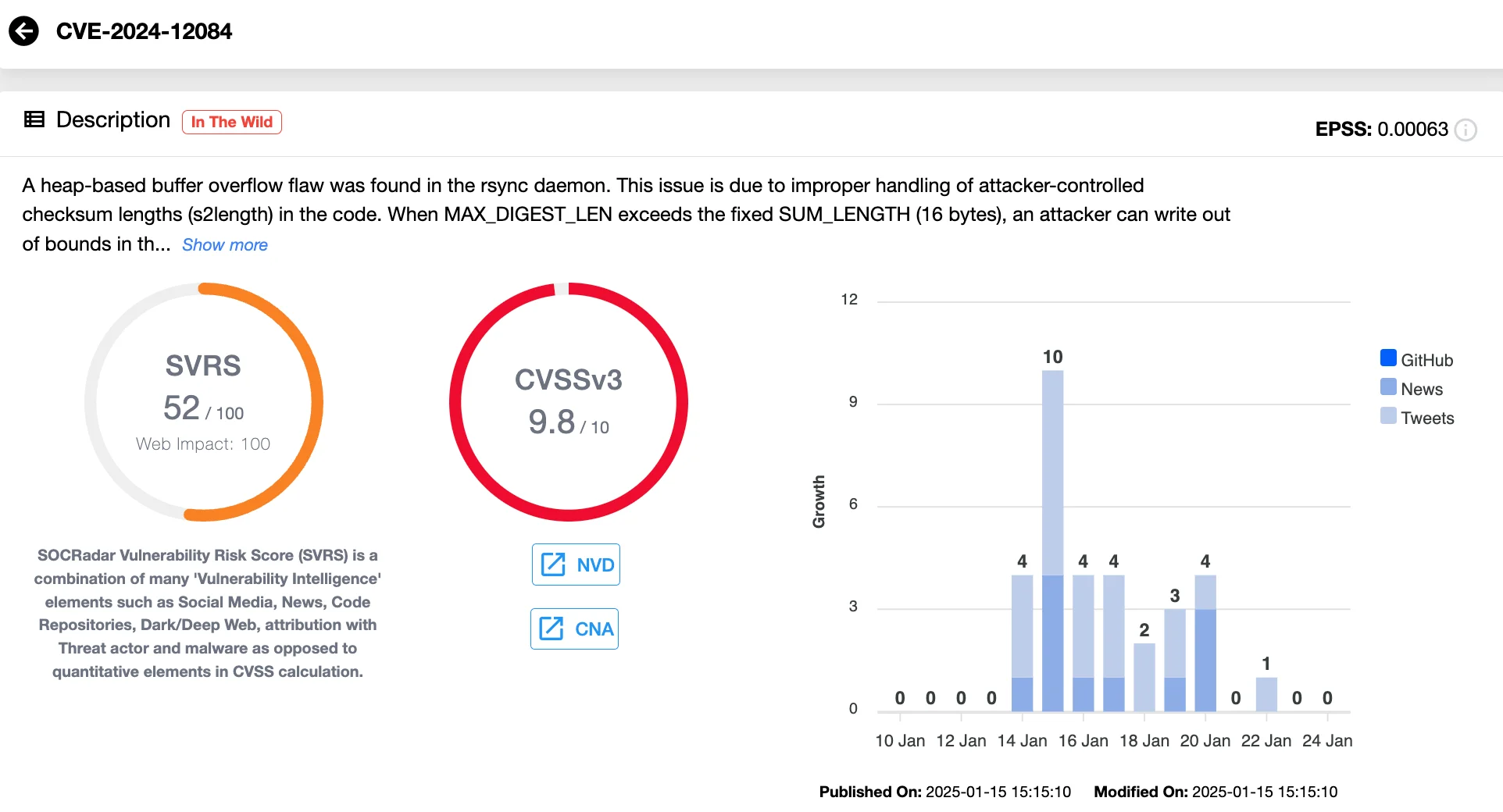
Vulnerability card of CVE-2024-12084 (SOCRadar Vulnerability Intelligence)
- CVE-2024-12085 (CVSS 7.5): An information leak vulnerability that could enable attackers to extract uninitialized stack data, exposing sensitive information.
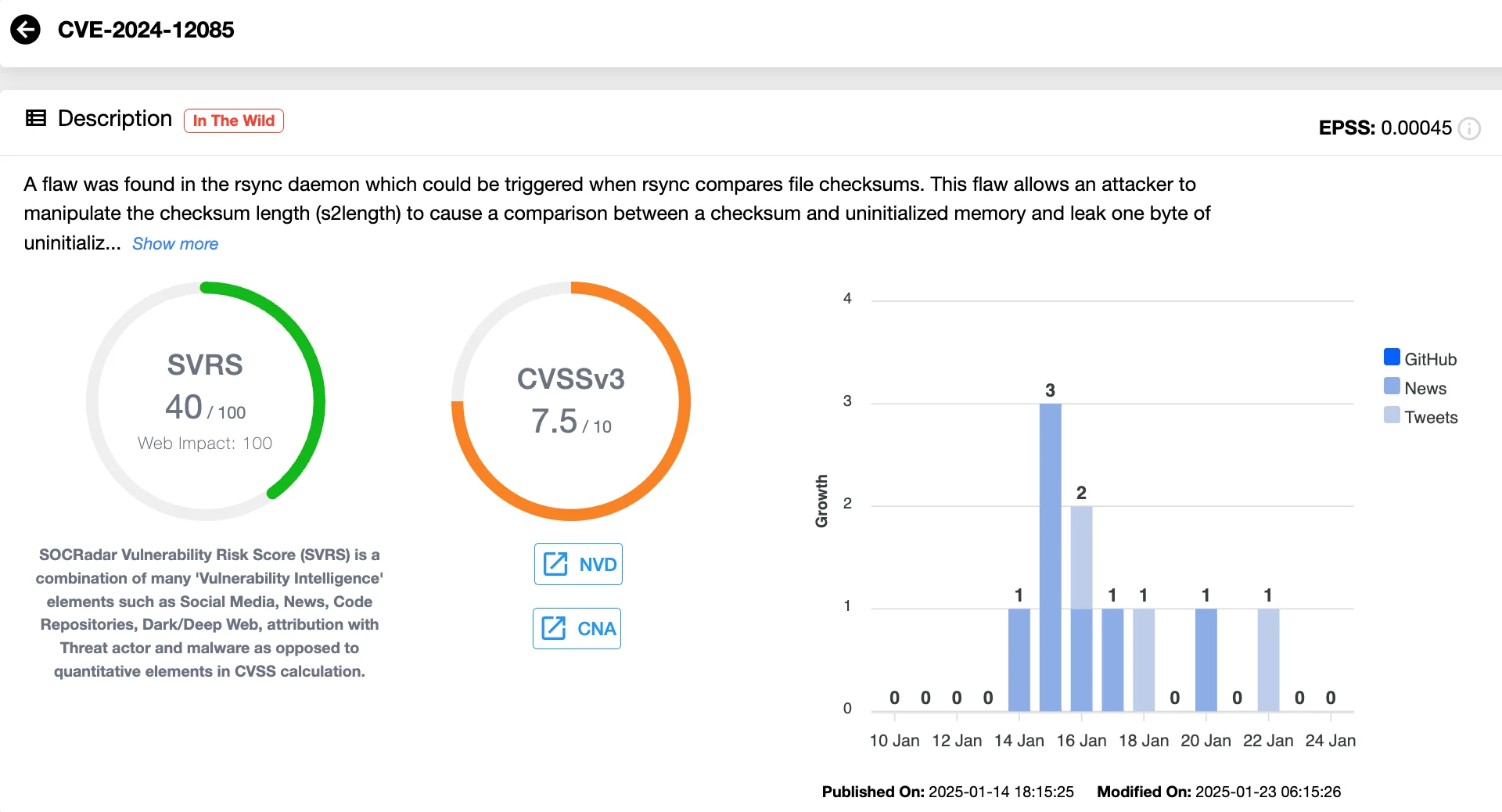
Vulnerability card of CVE-2024-12085 (SOCRadar Vulnerability Intelligence)
When combined, CERT/CC notes that these vulnerabilities allow attackers with anonymous read-access to:
- Execute arbitrary code on the NAS device.
- Overwrite files like ~/.bashrc or ~/.popt, enabling malicious code execution.
- Access sensitive data, including SSH keys.
Exploitation Potential
The latest QNAP vulnerabilities can be exploited with minimal access, as attackers target anonymous or inadequately secured Rsync servers. Administrators managing QNAP’s HBS 3 Hybrid Backup Sync should promptly update their systems to version 25.1.4.952 or later to mitigate the risk.
To apply the update, simply log in as an administrator, navigate to the App Center, and follow the installation prompts. Additionally, ensure that Rsync servers are properly secured against unauthorized access and follow recommended best practices for data synchronization tools. For further guidance, refer to the QNAP advisory.
Strengthen Your Perimeter with SOCRadar’s Attack Surface Management
In addition to tracking vulnerabilities, protecting your organization from attacks also requires visibility into your external-facing assets. SOCRadar’s Attack Surface Management (ASM) continuously monitors your digital footprint, identifying exposed assets and potential risks that can be targeted by cybercriminals.
Monitor your assets and company vulnerabilities with SOCRadar’s ASM. Secure your systems before they become targets.
By providing real-time alerts, detailed asset analysis, and comprehensive risk assessments, SOCRadar’s ASM allows you to mitigate risks before attackers can exploit them.



































