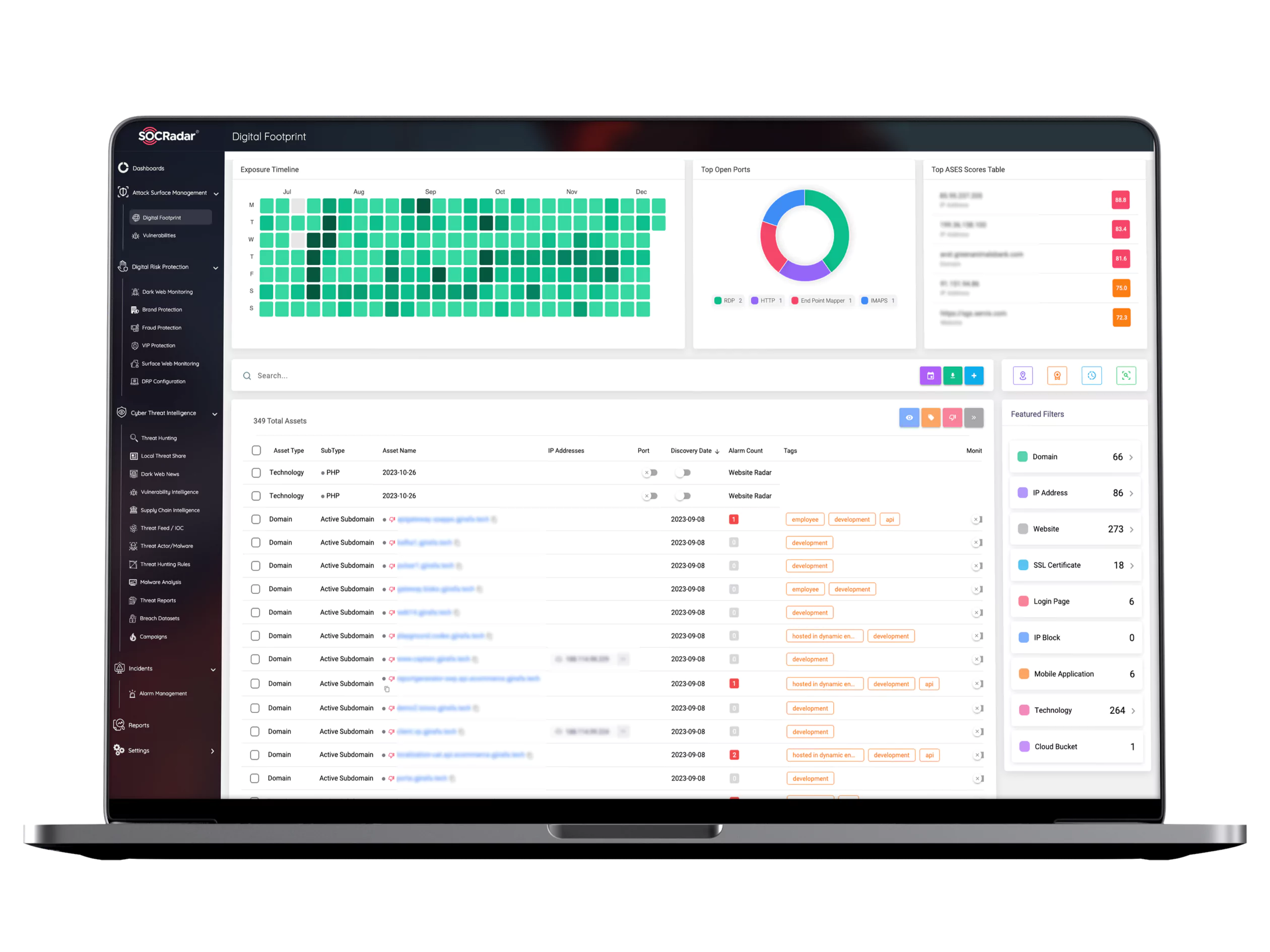
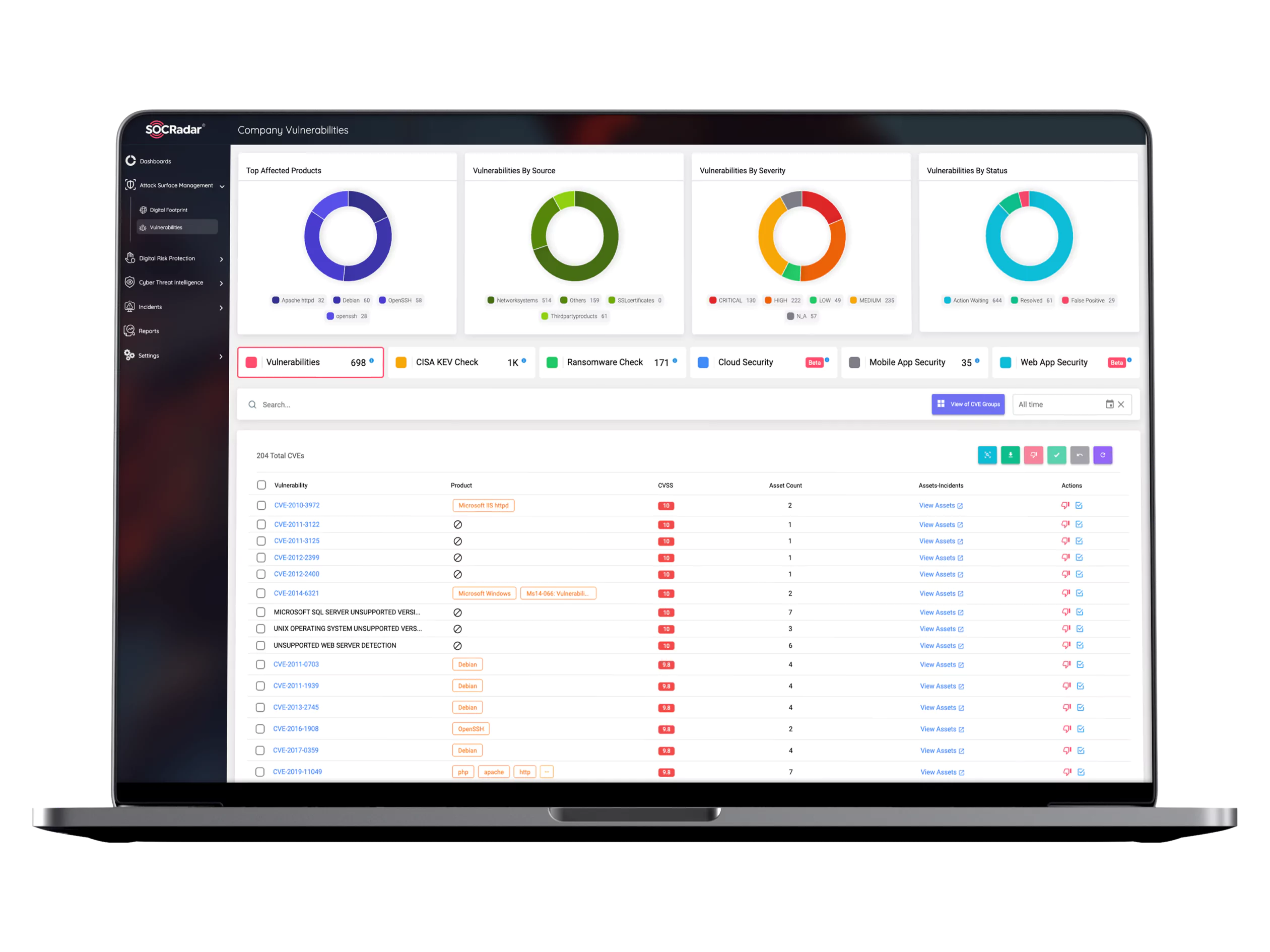
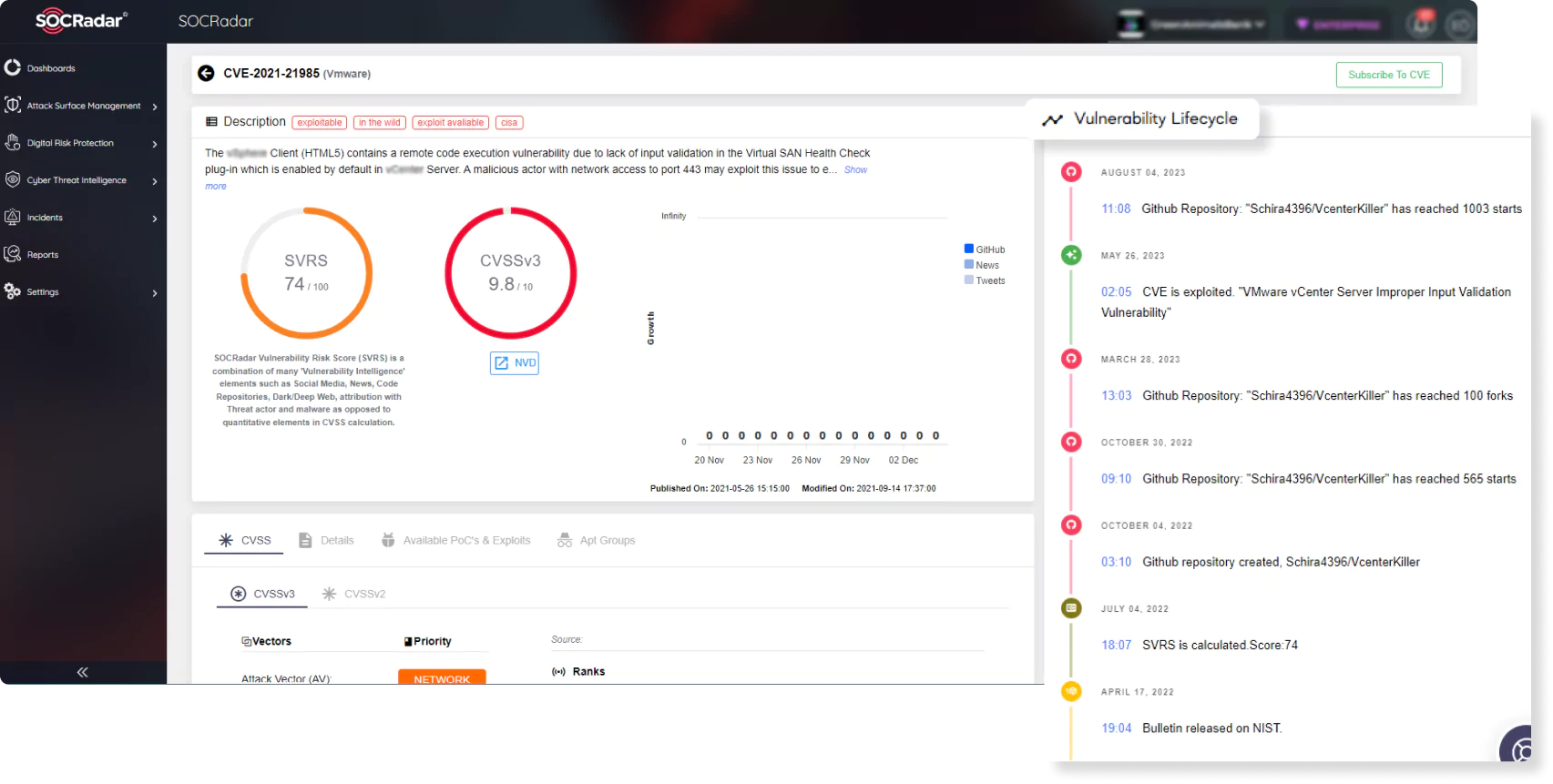
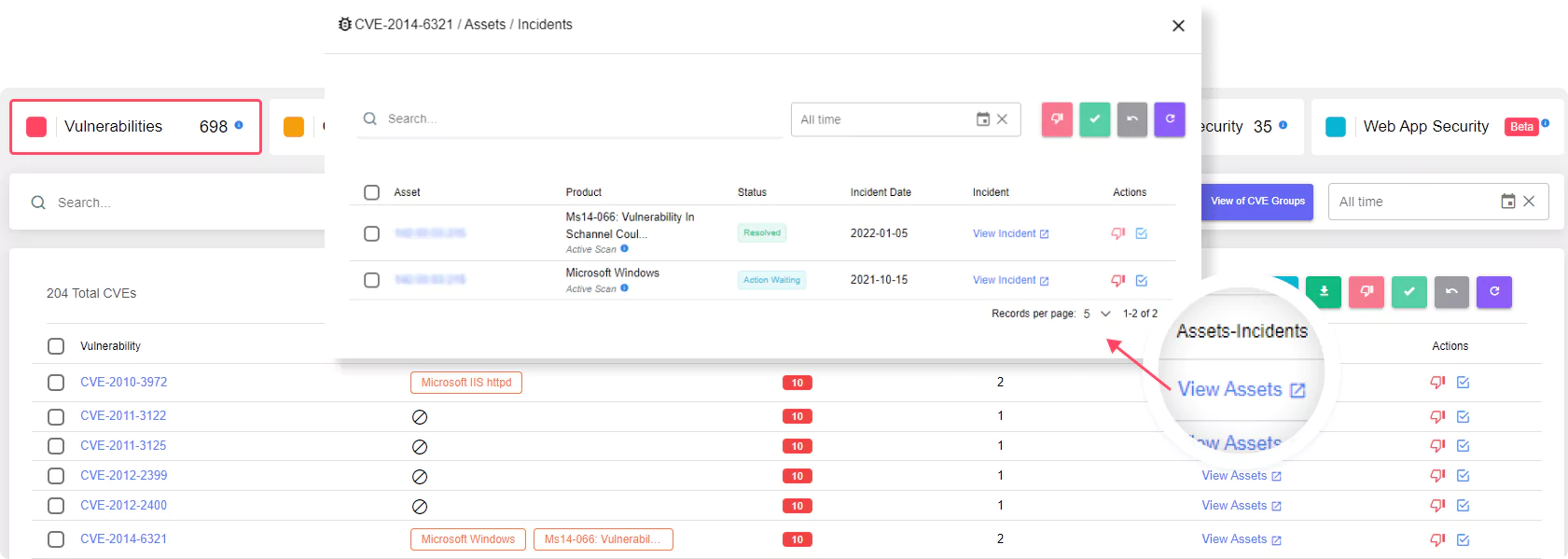
Good attack surface management products monitor all systems around the clock for newly discovered new security vulnerabilities. Real-time visibility is critical to detecting the impact of an attack on the attack surface of a range of networks, software, protocols, and services that run online in an enterprise. Given the number and complexity of network and software protocols and services in an online business, it can be difficult to identify which parts of your attacks are the source of breaches and intrusions. Identifying injury risks, which is dynamic and highly complex, is characterized by several complex areas to be explored, such as network infrastructure, network security, data security, and network management.