Surge in Attention Towards Critical Vulnerabilities in QNAP QTS and NAS Services (CVE-2023-23368, CVE-2023-23369)
QNAP recently published advisories for two critical command injection vulnerabilities, tracked as CVE-2023-23368 and CVE-2023-23369. These vulnerabilities affect the QTS operating system, QuTS hero, QuTScloud, and several other applications on QNAP NAS (Network-Attached Storage) devices.
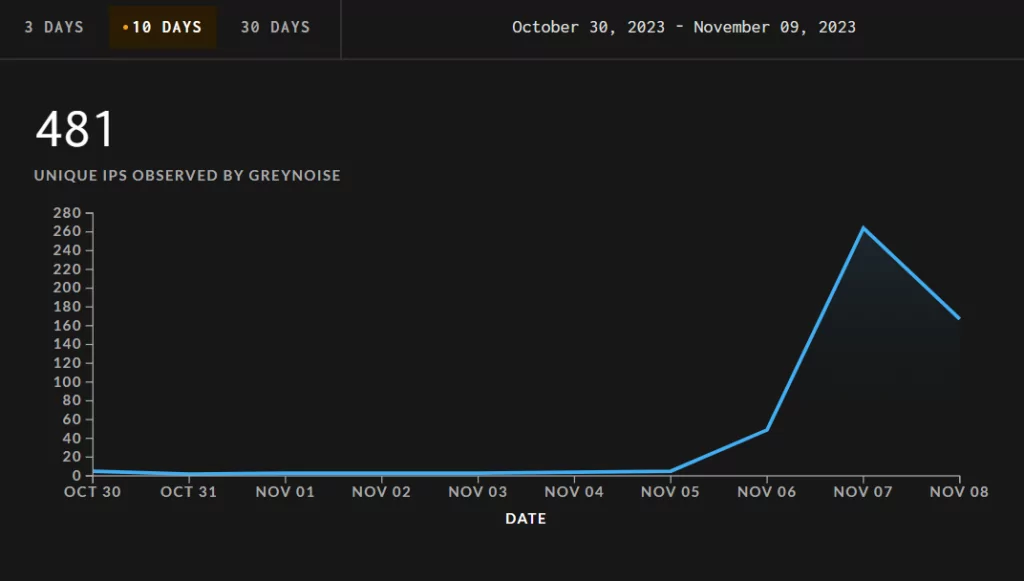
The vulnerabilities were disclosed in QNAP’s advisory on November 4, 2023, and since then, there have been observations of increased activity related to them.
“There is no surprise here: an anomalous increase in interest in QNAP due to the recently announced critical vulnerabilities (CVE-2023-23369, CVE-2023-23368),” @NTKramer on X states.
Details of the Vulnerabilities Affecting QNAP QTS, QuTS hero, QuTScloud, and Other NAS Services
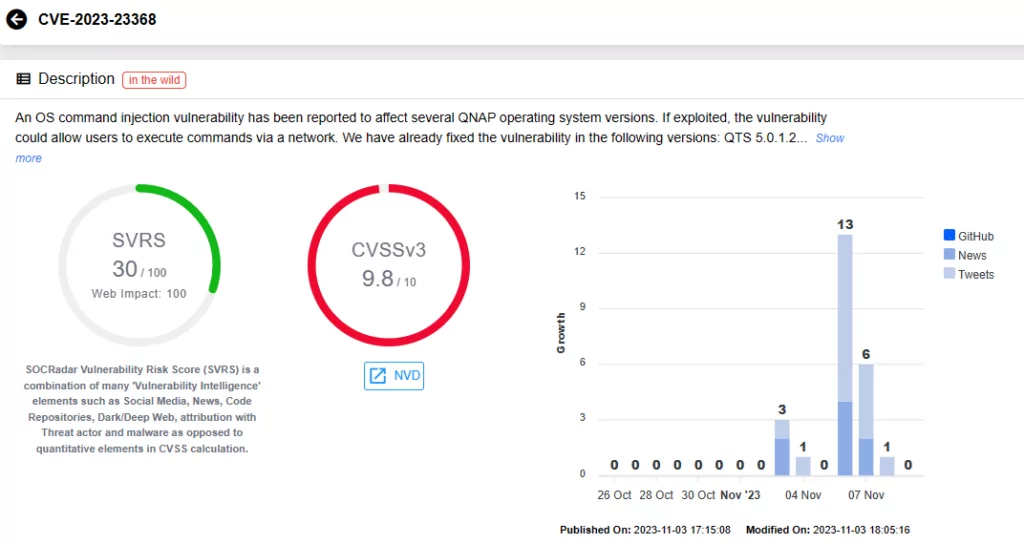
The first vulnerability that QNAP disclosed is CVE-2023-23368, with a CVSS score of 9.8. This vulnerability is described as a command injection issue that affects QTS, QuTS hero, and QuTScloud.
The second vulnerability, tracked as CVE-2023-23369, holds a CVSS score of 9.0. It also impacts the QTS operating system, and additionally affects Multimedia Console and the Media Streaming add-on.
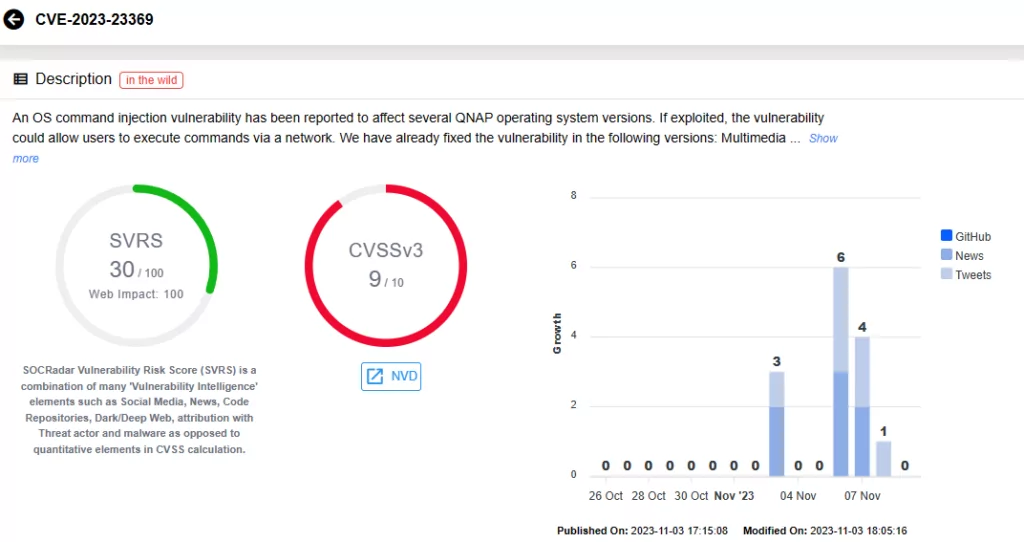
QNAP warns that if these two vulnerabilities are exploited, remote attackers could execute commands via a network.
Due to their use in data storage, QNAP NAS devices often attract the attention of ransomware threat actors. QNAP devices have been targeted in the past in various ransomware attacks. In September 2022, QNAP experienced DeadBolt Ransomware attacks after the exploitation of a zero-day vulnerability in Photo Station. In July, the Checkmate Ransomware targeted QNAP NAS devices, demanding $15,000 from its victims.
You can follow exploitation trends through SOCRadar’s Vulnerability Intelligence. The feature delivers real-time data, including updates, mentions, and hacker trends about vulnerabilities, thereby enabling organizations to proactively address emerging threats and prevent becoming a target.
Which Products and Versions Are Affected?
The tables below show products and their vulnerable versions, along with the fixed versions.
CVE-2023-23368:
|
Affected Product |
Fixed Version |
|
QTS 5.0.x |
QTS 5.0.1.2376 build 20230421 and later |
|
QTS 4.5.x |
QTS 4.5.4.2374 build 20230416 and later |
|
QuTS hero h5.0.x |
QuTS hero h5.0.1.2376 build 20230421 and later |
|
QuTS hero h4.5.x |
QuTS hero h4.5.4.2374 build 20230417 and later |
|
QuTScloud c5.0.x |
QuTScloud c5.0.1.2374 and later |
CVE-2023-23369:
|
Affected Product |
Fixed Version |
|
QTS 5.1.x |
QTS 5.1.0.2399 build 20230515 and later |
|
QTS 4.3.6 |
QTS 4.3.6.2441 build 20230621 and later |
|
QTS 4.3.4 |
QTS 4.3.4.2451 build 20230621 and later |
|
QTS 4.3.3 |
QTS 4.3.3.2420 build 20230621 and later |
|
QTS 4.2.x |
QTS 4.2.6 build 20230621 and later |
|
Multimedia Console 2.1.x |
Multimedia Console 2.1.2 (2023/05/04) and later |
|
Multimedia Console 1.4.x |
Multimedia Console 1.4.8 (2023/05/05) and later |
|
Media Streaming add-on 500.1.x |
Media Streaming add-on 500.1.1.2 (2023/06/12) and later |
|
Media Streaming add-on 500.0.x |
Media Streaming add-on 500.0.0.11 (2023/06/16) and later |
Apply the Updates for QNAP QTS QuTS hero, QuTScloud, Multimedia Console, and Media Streaming
Administrators can update QTS, QuTS hero, or QuTScloud by navigating to Control Panel > System > Firmware Update. From there, they can check for updates under “Live Update.”
To update the Multimedia Console or the Media Streaming add-on, users can locate the installation in the App Center and click the “Update” button.
For manual updating, visit QNAP’s Download Center.
Stay Ahead of Vulnerability Exploitation with SOCRadar XTI
Harness SOCRadar’s Attack Surface Management (ASM) module to enhance your vulnerability management strategy. ASM enables ongoing monitoring of your digital assets and delivers timely alerts for emerging vulnerabilities, ensuring you can prioritize and address critical security issues efficiently.