Synology Fixes a Max Severity RCE Vulnerability in VPN Server Products
Taiwanese NAS device manufacturer Synology has released a security update to address a critical vulnerability with a CVSS score of 10. The vulnerability, tracked as CVE-2022-43931, affects Synology router products that can be set up as VPN servers to allow remote access to stored resources.
How Does the CVE-2022-43931 Vulnerability Work?
The vulnerability was discovered in the VPN Plus Server by Synology’s PSIRT (Product Security Incident Response Team); affected product names and versions are listed below:
- VPN Plus Server for SRM 1.2 versions before 1.4.3-0534
- VPN Plus Server for SRM 1.3 versions before 1.4.4-0635
In Synology’s most recent advisory from December, the vulnerability is described as an out-of-bounds write problem in the VPN Plus Server products’ remote desktop functionality. Successful exploitation of CVE-2022-43931 could allow remote attackers to execute arbitrary commands in vulnerable Synology VPN Plus Server versions.
The vendor did not provide additional information or specific attack vectors related to CVE-2022-43931.
Before the CVE-2022-43931 security advisory, Synology issued another advisory in December about several critical vulnerabilities affecting the SRM (Synology Router Manager) system. The vulnerabilities could allow attackers to read arbitrary files, as well as execute remote code, and launch denial-of-service (DoS) attacks.
NAS Devices and Routers Are Valuable Targets
NAS devices store and share data across networks, whereas routers connect networks. Both of these devices are frequently connected to the internet and have access to sensitive information, making them appealing targets for cybercriminals.
Attackers can abuse a vulnerable device’s built-in features to access networks. Attackers may then be able to steal sensitive data, carry out other malicious activity, and use these devices to launch attacks on other devices.
For instance, in 2022, ransomware gangs like Qlocker and Deadbolt targeted QNAP NAS devices. Qlocker ransomware exploited a hard-coded credentials vulnerability (CVE-2021-28799) to access QNAP’s Hybrid Backup Sync (HBS).
Is There a Mitigation Available?
Since the vendor has fixed the security vulnerability, it is advised to update to versions 1.4.3-0534 for VPN Plus Server for SRM 1.2 and 1.4.4-0635 for VPN Plus Server for SRM 1.3.
To protect against new threats, regularly check product versions and keep them updated.
Check out VPN Radar on the SOCRadar Labs, where various excellent testing tools are available. With the aid of VPN Radar, you can effectively implement preventative measures by determining whether any critical unpatched vulnerabilities are present.
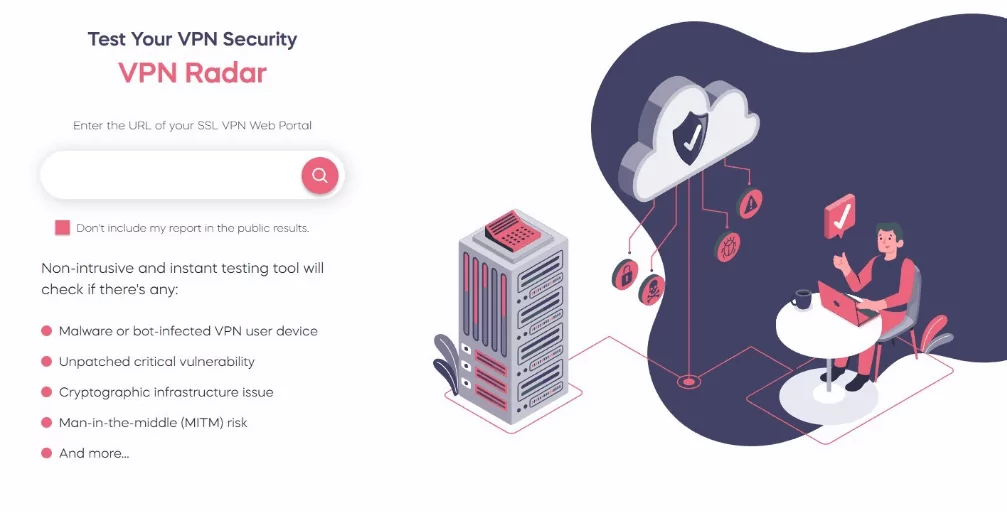
VPN Radar can also find malware and bot infections on VPN user devices and many other security issues that could compromise your VPN security.