The IDOR Vulnerability in Microsoft Teams: Risks in Your Collaboration Environment
[Update] July 5, 2023: A new tool called TeamsPhisher has been released by a member of the U.S. Navy’s red team. It exploits the discussed and unresolved security issue in Microsoft Teams, allowing it to bypass file restrictions for external users. TeamsPhisher is a Python-based tool that automates the attack process, combining ideas from Jumpsec’s researchers, techniques from Andrea Santese, and authentication functions from Bastian Kanbach’s ‘TeamsEnum’ tool. The tool verifies target users and their ability to receive external messages before creating a new thread and sending them a message with a Sharepoint attachment link. TeamsPhisher requires a Microsoft Business account with valid Teams and Sharepoint licenses. It also offers features like preview mode, secure file links, delay specification, and logging.
Overall, TeamsPhisher is a new tool designed to exploit a security vulnerability in Microsoft Teams, enabling the bypassing of file restrictions for external users. By automating the attack process, it streamlines the creation of threads and sending of messages with Sharepoint attachment links.
Microsoft Teams, a popular collaboration platform, allows users with a Microsoft account to communicate with external tenants, which are businesses or organizations using Teams. However, a vulnerability discovered by Max Corbridge and Tom Ellson of JUMPSEC’s Red Team highlights a potential security risk in the default configuration of Microsoft Teams.
Understanding the Vulnerability
External Tenants in Microsoft Teams refer to organizations that have their own Microsoft tenancy and can send messages to users in other tenancies. When an external tenant sends a message, it is labeled with an “External” banner, indicating its origin.
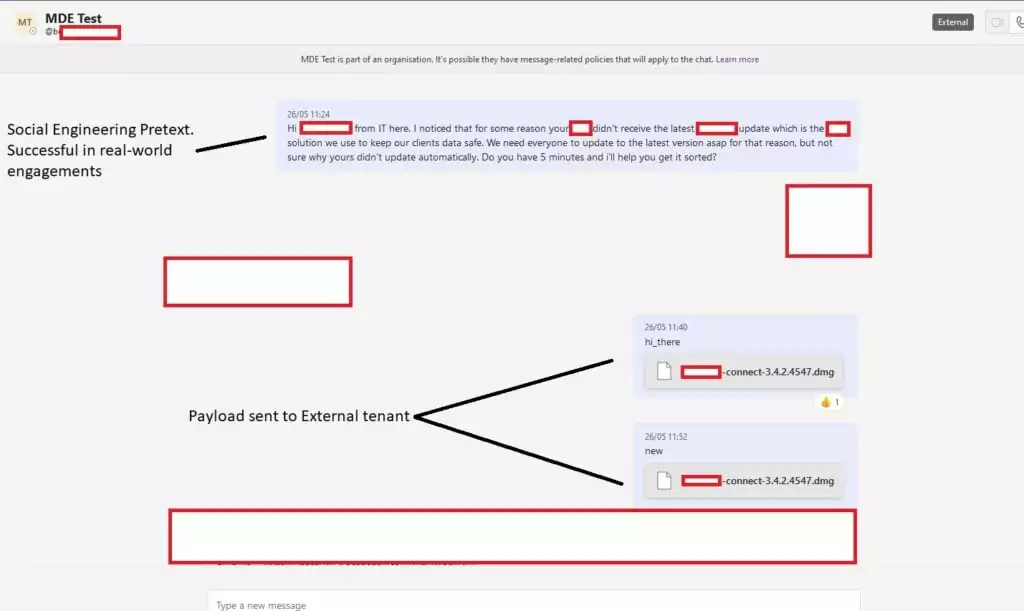
While external tenants are generally restricted from sending files to members of other organizations, Corbridge and Ellson found a way to bypass this security control. By exploiting an Insecure Direct Object Reference (IDOR) vulnerability, they were able to manipulate the recipient ID in the POST request and deliver a payload directly into a target organization’s inbox.
One of the significant concerns associated with this vulnerability is the potential for social engineering attacks. Threat actors have the ability to impersonate known members of an organization and exploit the established trust within Microsoft Teams. As stated by JUMPSEC, “when this vulnerability is combined with social engineering via Teams, it becomes very easy to start a back-and-forth conversation, jump on a call, share screens, and more.”
The Significance of the Vulnerability
This vulnerability poses a significant risk as it bypasses many modern anti-phishing security controls. Traditional phishing techniques often rely on convincing users to click on links in emails. In this case, payload delivery occurs via a trusted Sharepoint domain, resulting in a file appearing in the recipient’s Teams inbox. By avoiding the need for domains, web servers, landing pages, and URL filtering, threat actors can save time and increase their chances of success.
Threat actors can easily purchase and register domains similar to their target organizations and associate them with Microsoft 365. This eliminates the need for sophisticated phishing infrastructure, such as convincing landing pages and domain categorization, making it quicker and simpler for attackers to launch successful social engineering campaigns.
By leveraging this vulnerability, threat actors can bypass the risks associated with email-based phishing attacks. Users have been trained to exercise caution when clicking on links in emails, but this vulnerability delivers the payload through a trusted Sharepoint domain. As a result, the payload inherits the reputation of Sharepoint, reducing the likelihood of users detecting it as a phishing attack.
The Impact and Remediation Options
This vulnerability affects organizations using Microsoft Teams in the default configuration, making it potentially widespread in its impact. To mitigate the risks associated with this vulnerability, organizations have several remediation options:
A. Addressing the vulnerability through tightened security controls
Organizations should review the necessity of external tenants’ permission to message their staff. If there is no legitimate business requirement, tightening security controls and removing the option for external communication can be done through the Microsoft Teams Admin Center.
B. Educating staff about productivity apps and alternative avenues for social engineering
It is crucial to raise awareness among staff about the possibility of social engineering attacks via productivity apps like Teams, Slack, and Sharepoint. By expanding security awareness beyond email-based threats, organizations can enhance their resilience against social engineering attempts.
C. Monitoring external message requests and implementing web proxy logs for detection
While Microsoft currently offers limited support for this vulnerability, organizations can leverage web proxy logs to gain visibility into staff members accepting external message requests. Monitoring the URI associated with accepting external message requests can provide insights into the frequency of such transactions within the organization and inform the implementation of mitigation measures.
Conclusion
The discovery of this vulnerability in Microsoft Teams highlights the potential risks of malware delivery and phishing attempts within organizations. By taking proactive steps to address the vulnerability, tighten security controls, educate staff, and monitor external message requests, organizations can mitigate the risks associated with this security gap. Staying vigilant and adapting security measures to evolving social engineering attacks is essential to safeguarding digital assets and maintaining a secure collaboration environment.
How SOCRadar can help?
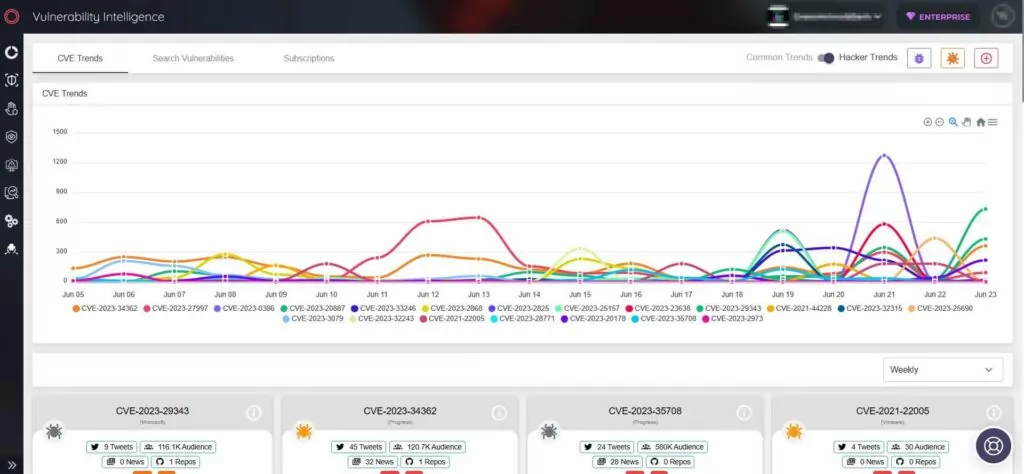
SOCRadar’s External Attack Surface Management (EASM) feature identifies your assets and maintains continuous monitoring, ensuring rapid detection of emerging security issues. By promptly issuing alerts, SOCRadar empowers organizations to proactively address potential risks and better prioritize patches.
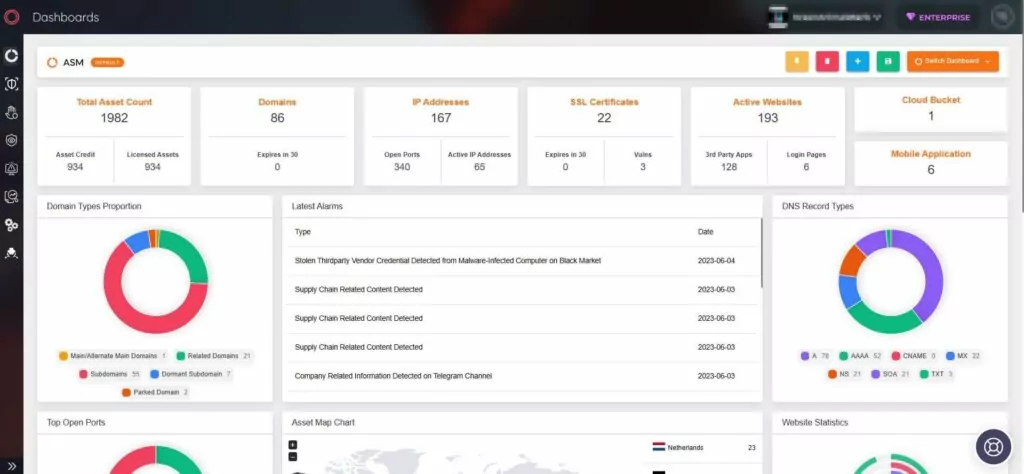
Moreover, SOCRadar significantly enhances security measures by providing actionable intelligence through its Vulnerability Intelligence, enabling organizations to track the latest vulnerability trends and details.