
The Week in Dark Web – 02 April 2021 – Data Sale Frenzy
Powered by DarkMirror™
This week’s edition covers the latest dark web news from the past week. SQL Injection to Hyundai Russia, Chinese mobile app data breach, LinkedIn 100M personal data sale, 300GB of personal details sale from a cryptocurrency trading platform hit the headlines.Click here to read the last week’s edition. Here are the details of the major events that took place on the deep web this week:
Chinese Victims Can Also Take Place on the Dark Web
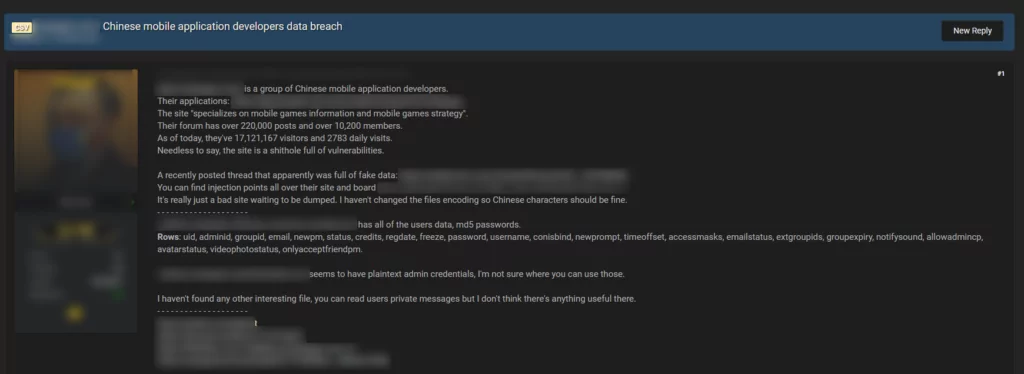
On dark web portals, confidential information of many different companies from various countries and sectors are put for sale by threat actors, however China is not one of the frequent targets. Nevertheless, sometimes hackers disclose data belonging to Chinese victims. On March 31, 2021, SOCRadar identified a post where a dark web vendor was offering for sale alleged data leaks related to a Chinese mobile application platform. According to the vendor, the victim platform specializes on mobile games and its forum has over 10.000 subscribers. Moreover, the vendor asserted to have a database including all of the users data like email, username, even passwords and mentioned that there are a lot of injection points all over the site.
LinkedIn Data of 100 Millions of People For Sale on the Dark Web
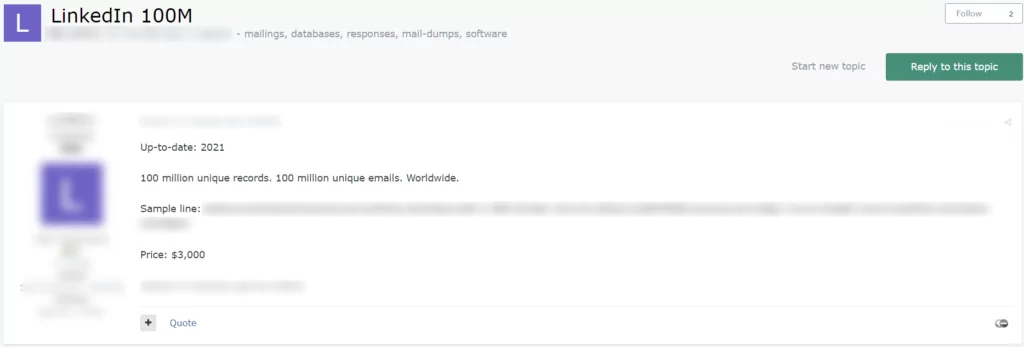
On March 31, 2021, a vendor offered to sell 100 million records for LinkedIn, on a Russian-speaking dark web forum monitored by SOCRadar. In the dump, according to the vendor, there are 100 million unique emails and some LinkedIn profile information available and the vendor was asking $3000 for the database. According to the SOCRadar Analyst Team, if threat actors would seize the surfaced details, they could combine them with the contact information such as emails in order to perform phishing attacks on the victim users.
Sensitive Data of an UAE Company’s 180K Users on the Dark Web

On March 31, 2021, a vendor posted a thread claiming to sell a user database of an e-shopping platform from UAE, on a dark web forum tracked by SOCRadar. According to the post and shared sample, the database contains credentials as emails and passwords of 180.000 users. Other information in the leaked dump includes Personally Identifiable Information (PII) like full name, date of birth and phone number. Besides, the vendor stated there are some employees from different companies and a large number of individual users among the database. SOCRadar Analyst Team highlights that this information could be abused by threat actors in credential stuffing attacks.
Sensitive KYC Data of a Cryptocurrency Trading Platform Put For Sale on the Dark Web
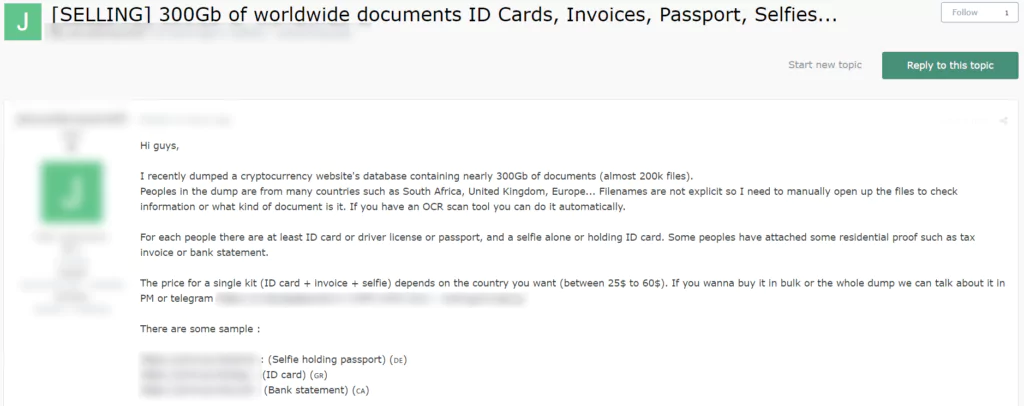
On March 31, 2021, a vendor put 300 GB of KYC (Know Your Customer) data and documents belonging to worldwide customers of a cryptocurrency platform for sale, on a dark web forum monitored by SOCRadar. This is not the first time a cryptocurrency platform has witnessed a breach but this is a major data breach, exposing the personally identifiable information (PII) of people from various countries like South Africa and the United Kingdom. The vendor behind the attack claimed to have ID cards, invoices, passports in the database, further added in the sale post that for each person there are at least ID card, driver license or passport and a selfie alone or with ID card while there is nothing clear about how many people affected. The vendor was contacting buyers on Telegram and was asking payments in dollars. The SOCRadar Analyst Team indicated that even though there are a lot of postings on the dark web claiming to have confidential information of people, the sale posts about cryptocurrency and similar financial platforms should be given a special importance.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, it is simply not feasible to monitor all sources which can be time-consuming as well as challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by targeted country or industry.



































