
The Week in Dark Web – February 20, 2023 – Access Sales and Data Leaks
Powered by DarkMirror™
Organizations’ worst nightmares are “data breaches” and “data leaks.” Atlassian is one of the companies that has had a large share of such cyber incidents in recent years. Last week we saw it experience yet another one. The attackers shared information about the company’s 13K employees.
Another company that experienced a data breach was GoDaddy. Threat actors stole the company’s source code and installed malware on its servers.
Here is other notable news from the dark web.
Find out if your data has been exposed.
GoDaddy Discloses Multi-Year Breach Involving Source Code Theft and Malware Installation
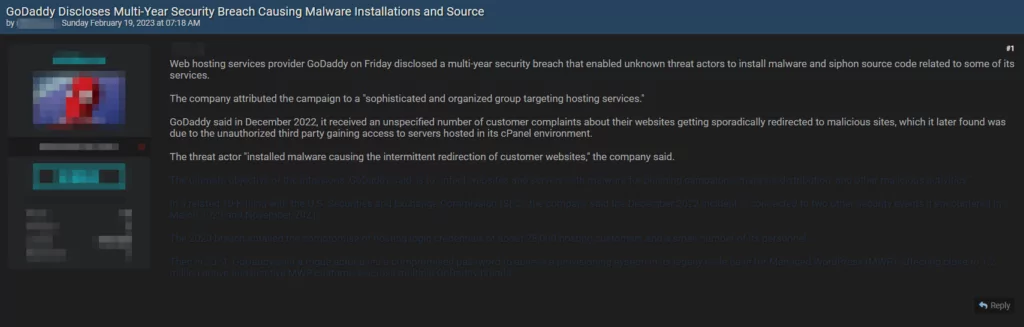
SOCRadar researchers detected GoDaddy-related posts by threat actors on dark web forums. GoDaddy, a major web hosting provider, has disclosed a breach in which its cPanel shared hosting environment was compromised by unknown attackers. The breach resulted in stealingsource code and installing malware on the company’s servers. Although the company discovered the breach in early December 2022 following reports from customers that their sites were redirecting to random domains, the attackers had been infiltrating GoDaddy’s network for several years. The company has stated that earlier breaches disclosed in March 2020 and November 2021 are also related to this prolonged attack.
Sensitive Documents of Atlassian Are Leaked
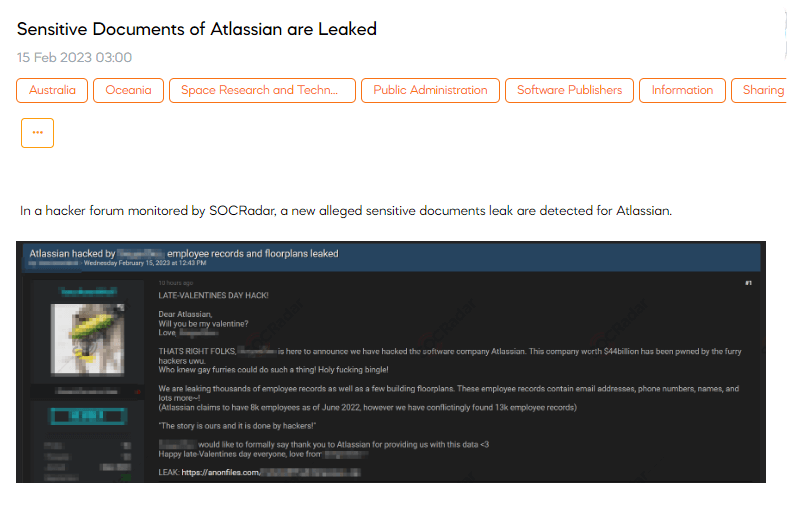
On February 15, a SOCRadar dark web researcher detected a post sharing sensitive documents belonging to Atlassian. Software company Atlassian was targeted by a hacker group named “SiegedSec,” who claimed to have carried out a hack on Valentine’s Day. As part of the breach, the group leaked the personal information of 13,000 employees and the company’s floor plans. The leaked data’s link was shared by threat actors on different platforms, such as hacker forums and the official Telegram channel of the SiegedSec group.
Crypto Database of the USA is on Sale
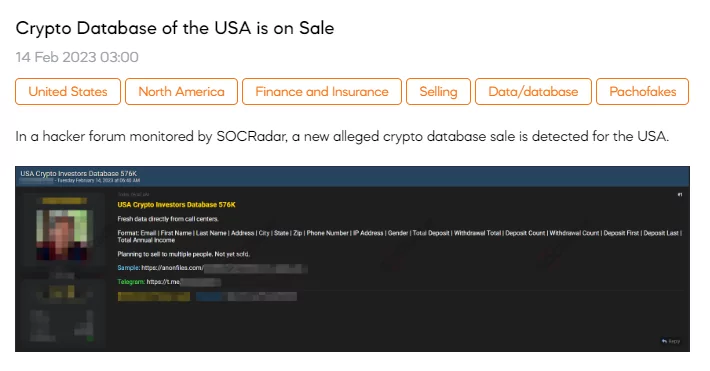
On February 14, SOCRadar researchers detected a post selling 576K crypto data originating in the U.S. The database, which is also highlighted as “fresh,” contains users’ personally identifiable information (PII) along with deposit information. The threat actor plans to sell to multiple people. The price for the database is unknown; the threat actor directs people to Telegram.
Unauthorized Network Access Sale is Detected for Mexican Government Portal
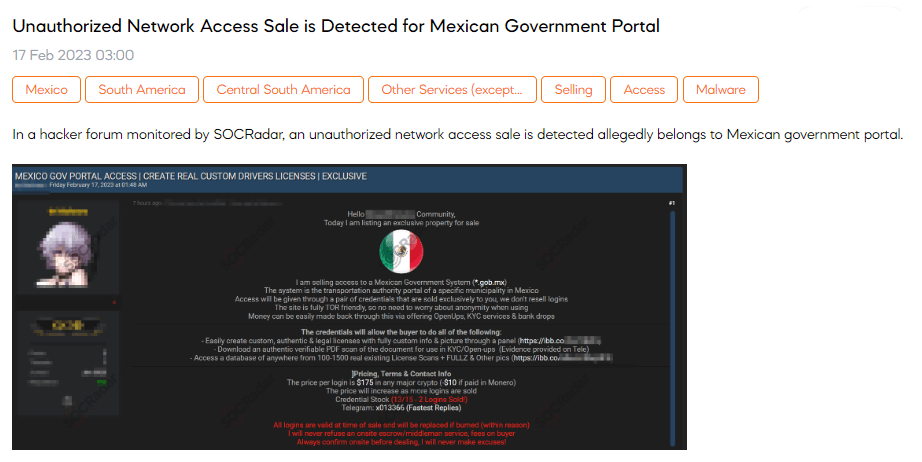
SOCRadar dark web team found a post that sells unauthorized network access to a Mexican government portal. The threat actor claims that the portal belongs to the transportation authority of a particular municipality in Mexico. The post states that the price for each login is $175, which can be paid using any major cryptocurrency.
Credit Cards Belonging to Many Countries are on Sale
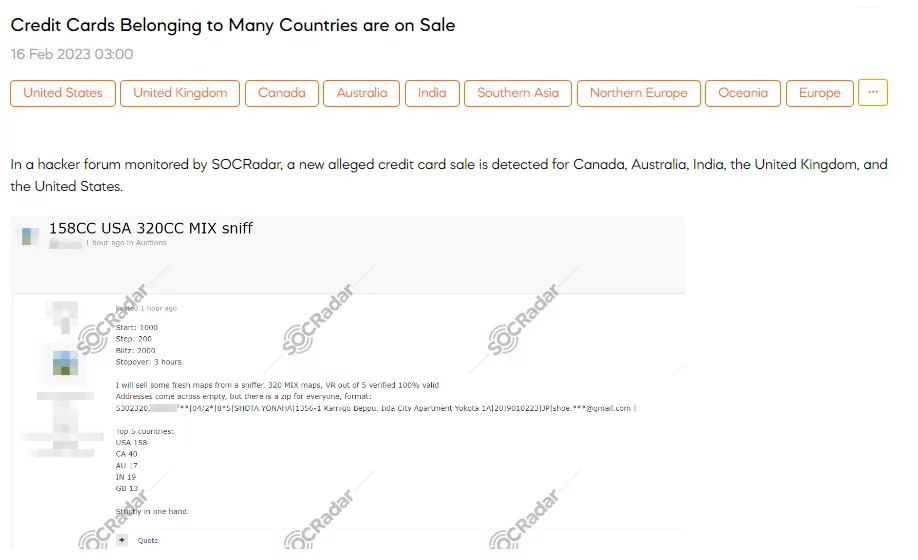
SOCRadar detected a post that sells credit card credentials for Canada, Australia, India, the United Kingdom, and the United States. The post claimed that credit cards are available for purchase at $1000. Additionally, the post mentions the availability of 320 MIX maps, including five verified maps with 100% validity, which the threat actor obtained from a sniffer. The top 5 countries are the USA with 158, Canada with 40, Australia with 17, India with 19, and the United Kingdom with 13.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































