Atlassian Hacked: SiegedSec Hacker Group Leaks Company’s Data
As a late Valentine’s Day hack, a hacker group called “SiegedSec” claims to have hacked software company Atlassian. The group leaked the company’s floorplans and information about 13,000 employees. Atlassian has also acknowledged the hack, although it contradicts the alleged number of employees.
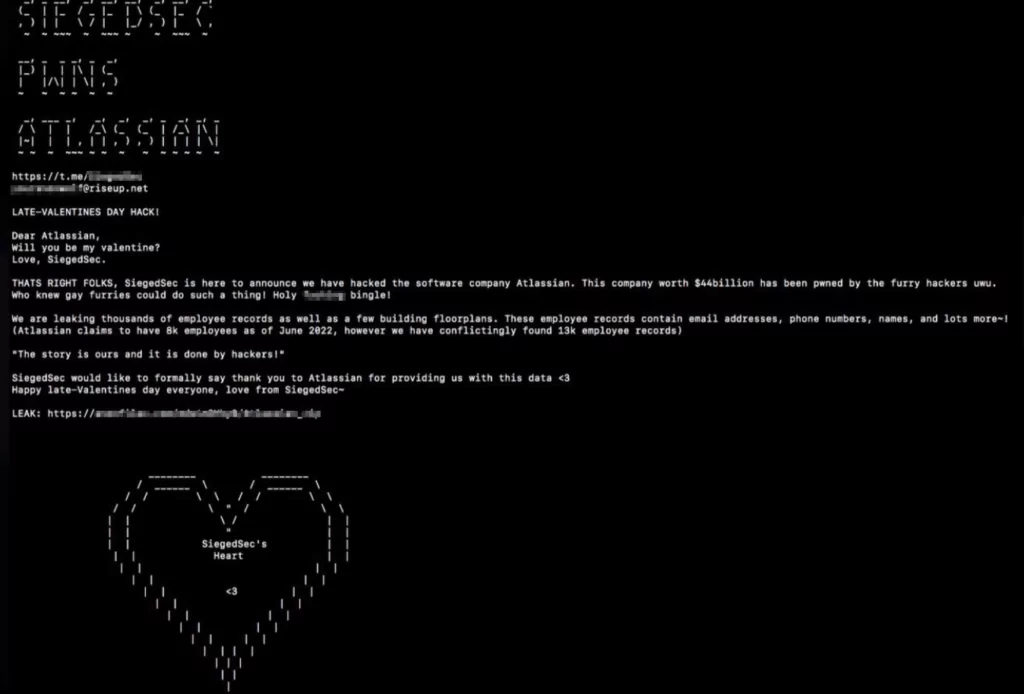
The group called out to Atlassian on its data leak post, asking, “Will you be my valentine?” before declaring the hack. They also thanked Atlassian for providing them with the data, which could put the affected employees at risk of identity theft and other malicious activities.
Which Data Were Exposed?
Threat actors distributed the leaked data’s link across various channels, including the BreachForums and the SiegedSec group’s official Telegram channel. The file includes the following lines: cc-employee, company-id, deleted, do-not-sync, email, hide-from-host-list, manually-added, manually-added-location-present, name, phone-number, profile-picture-url, cost-center, division, department, organization, title, hide-from-employee-schedule, created-at, deleted-at, updated-at, relationships, company, links, self, user, default-location, related-location, assistants, related, data, bosses, manager, employee-locations, related-locations, locations, employee-favorites
The incident serves as a reminder of the ongoing threat posed by cyberattacks and the importance of employing strong security measures to protect sensitive data. Atlassian has yet to issue a statement on the potential impact of the breach and any subsequent security measures the company may take to address the situation.
Who is SiegedSec?
A new threat group called SiegedSec emerged a few days prior to the Russian invasion of Ukraine. SiegedSec uses slogans emphasizing “sieging” the victim’s security, per its name. Cybersecurity researchers discovered that the group has 7 active members and is led by a hacktivist known as “YourAnonWolf.”
The group shows no preference for the industries or locations of its victims. They have successfully targeted companies across numerous industries all around the world, including healthcare, information technology, insurance, legal, and finance.
SiegedSec group has gained access to confidential data, leaked emails, or stolen databases from at least 30 different companies since their start in February. They have leaked stolen data on various forums but have not used ransomware or attempted to sell it. Since many of the victim companies are small businesses, hardly any have publicly announced cybersecurity incidents caused by SiegedSec.
Is SiegedSec Affiliated with Other Threat Actors?
The group appears to be affiliated with GhostSec, as members frequently share GhostSec’s announcements on SiegedSec’s channels. On BreachForums, the leading member YourAnonWolf has declared that they are a member of both GhostSec and SiegedSec. YourAnonWolf has a history of being active in campaigns with Anonymous and GhostSec, targeting oppressive governments and countries with records of human rights violations. They have also claimed affiliation with other groups, including HackersGhost25, AxoSec, and BreachSec, although these groups’ current status is unclear.
Past Activities of SiegedSec
Analysts have observed SiegedSec providing evidence of defacing or compromising at least 11 websites with crude language and graphics. In April, the group claimed to have successfully defaced over 100 domains and hinted they still have access. They have also been found to be associated with several thousand compromised LinkedIn profiles.
In May, SiegedSec announced that they successfully attacked an Indian online news distribution outlet, NewsVoir. The group leaked two archives, one containing 27GB of documents stolen from the organization’s servers and another consisting of hundreds of gigabytes of source code and API data.
Recently, the group claimed that the website provider for NewsVoir, WebGuruz, had contacted them directly. SiegedSec leaked a screenshot reportedly from their chat with a WebGuruz representative, where “Wolf” (YourAnonWolf) hinted that they might be interested in financial compensation for their actions, suggesting that their motives are not just for fun or games.
Atlassian Suspects Third-Party Vendor
Atlassian has confirmed that the data breach was caused by a breach of their third-party vendor Envoy. However, Atlassian clarified that product and customer data were not at risk since they were not accessible via the Envoy app. The company is currently investigating the incident and has enhanced physical security across its offices.
On the other hand, Envoy has denied any breach on their systems and believes that an Atlassian employee’s valid credentials were stolen, allowing the hacker to access the Atlassian employee directory and office floor plans held within Envoy’s app. Envoy also assured its customers that they have stringent measures to protect their data’s security and privacy.
Stay Ahead of Hackers with SOCRadar
Although the damage caused by their cyberattacks is unknown, the leaked data that SiegedSec shared on their Telegram channel and dark web forums could be used by other threat actors to gain access to private corporate and personal information which they have posted.
Hackers can use building floorplans to aid in their attack plans in several ways. For instance, floorplans can provide detailed information about a building’s layout, including the location of security cameras, access points, and critical IT infrastructure. Armed with this information, hackers can identify potential vulnerabilities, execute physical security breaches such as stealing physical documents or hardware and launch targeted attacks against specific areas of the building.
SOCRadar’s comprehensive threat actor tracking capabilities allow organizations to stay ahead of emerging threats and take proactive measures to protect their critical assets from potential attacks.
The SOCRadar Supply Chain Intelligence tab keeps you up-to-date on the latest cybersecurity incidents involving other businesses. You can add businesses you want to monitor to your watchlist and gain insights into hacker campaigns targeting your partners or vendors. This module is designed to avoid potential incidents caused by third-party involvement.