
Threat Actors Exploit CVE-2022-44877 RCE Vulnerability in CentOS Web Panel (CWP)
Update (16.01.2023):
According to data gathered by researchers, the CVE-2022-46169 vulnerability in Cacti saw an increase in exploitation attempts, and the overall number is now less than two dozen.
6,427 Cacti hosts were found to be exposed online, according to a report. But for all of them, it is impossible to determine how many run a vulnerable version or have updated it.
However, it is believed that 1,637 Cacti hosts accessible via the internet were vulnerable to CVE-2022-46169, with 465 using version 1.1.38.
The recently patched critical vulnerability in Control Web Panel (CWP), a server management tool known as CentOS Web Panel, is being actively exploited by threat actors.
The security vulnerability, CVE-2022-44877, with a CVSS score of 9.8, enables remote code execution without authentication.
PoC Exploit Available
A proof-of-concept (PoC) exploit was released by researcher Numan Türle, who had first reported the problem.
Analysis of the shared exploit code revealed that the vulnerability was in the functionality that caused incorrect entries to be logged on the panel.
The code snippet that writes content to the “wrong entry.log” file is shown below:
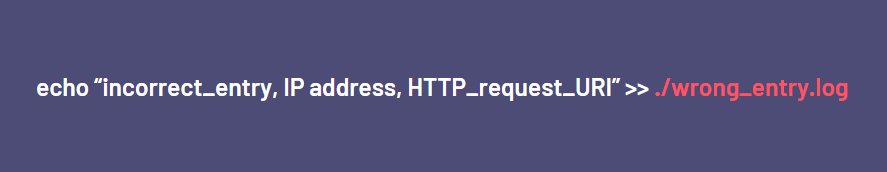
The command’s double quotes, a bash feature that enables command execution, were the reason for this misconfiguration.
An attacker-controlled HTTP_request_URI allows a threat actor to insert a command that the server will execute. A connection back to the listener shell is established when a hacker runs the command.
According to analyses, attackers are locating vulnerable hosts and using CVE-2022-44877 to spawn a terminal for communication with the machine.
Threat actors sometimes use the exploit to launch a reverse shell in an attack. The attacker’s machine is called by converting the encoded payloads into Python commands, and the Python pty module is used to spawn a terminal on the vulnerable host.
Considerable Number of CWP Servers Are at Risk
Over 400,000 CWP instances are accessible through the internet, according to a Shodan search.
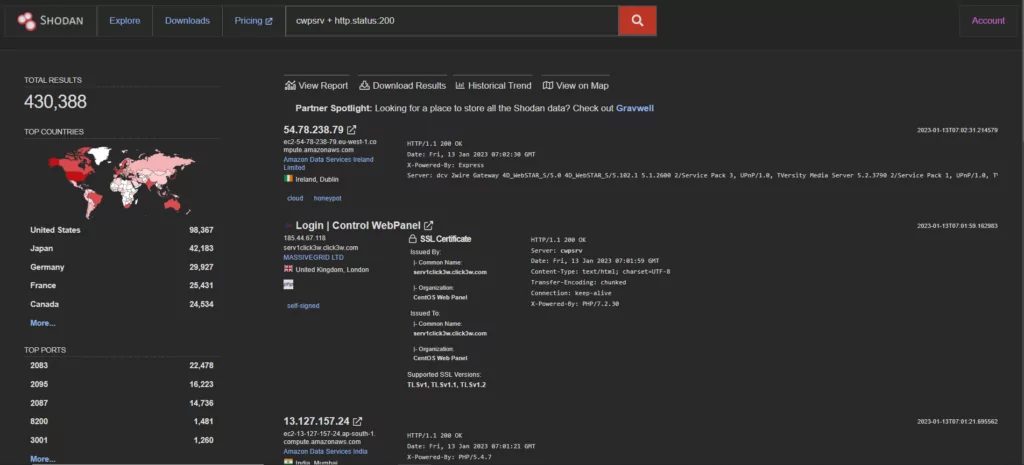
Security researchers noted that several attacks on unpatched CWP hosts come from IP addresses in the Netherlands, the United States, and Thailand.
Finding vulnerable targets is all that hackers need to do to take advantage of CVE-2022-44877, as the exploit code is already available.
Administrators are advised to update CWP to the latest version, which is currently 0.9.8.1148.




































