
Top 10 Exploited Vulnerabilities of 2024
Organizations face a relentless battle against vulnerabilities that threaten their critical assets, and 2024 has proven to be no exception. Cybersecurity teams constantly juggle priorities, racing to patch gaps before attackers exploit them. But what happens when resources are stretched thin or when the exploitation of a vulnerability takes mere days? The consequences can be devastating, from financial losses to irreparable reputational damage.
A staggering statistic from Google highlights the urgency of this challenge: by late 2024, the average time for exploitation after a vulnerability’s disclosure had dropped to just five days. This gives organizations a razor-thin margin to act – let alone when the vulnerability is exploited as a zero-day, the worst-case scenario for any company.
Compounding this issue is the sheer volume of vulnerabilities surfacing each year. According to our observation, in 2024, the National Vulnerability Database (NVD) recorded 40,003 CVEs, marking a nearly 39% increase from 2023’s 28,817 CVEs. To put this into perspective, the growth from 2022 to 2023 was only approximately 15%.

“Top 10 Exploited Vulnerabilities of 2024” illustrated by DALL-E
With vulnerabilities emerging daily, it’s no wonder security teams often feel overwhelmed. In this blog, we’ll delve into ten of the most significant vulnerabilities exploited in 2024. Rather than ranking them by frequency, we’ll focus on those that left a profound impact. Whether the fallout was financial, reputational, or both, these vulnerabilities serve as a reminder of the high stakes in today’s cybersecurity play.
Major Contributors to the KEV Catalog: A Closer Look at Vendor Vulnerabilities
Before diving into the specifics, let’s examine which vendors have dominated the Known Exploited Vulnerabilities (KEV) Catalog compiled by the Cybersecurity and Infrastructure Security Agency (CISA). This focus on vendor contributions provides critical context for understanding how the vulnerabilities discussed in this blog reflect broader patterns of exploitation throughout 2024.
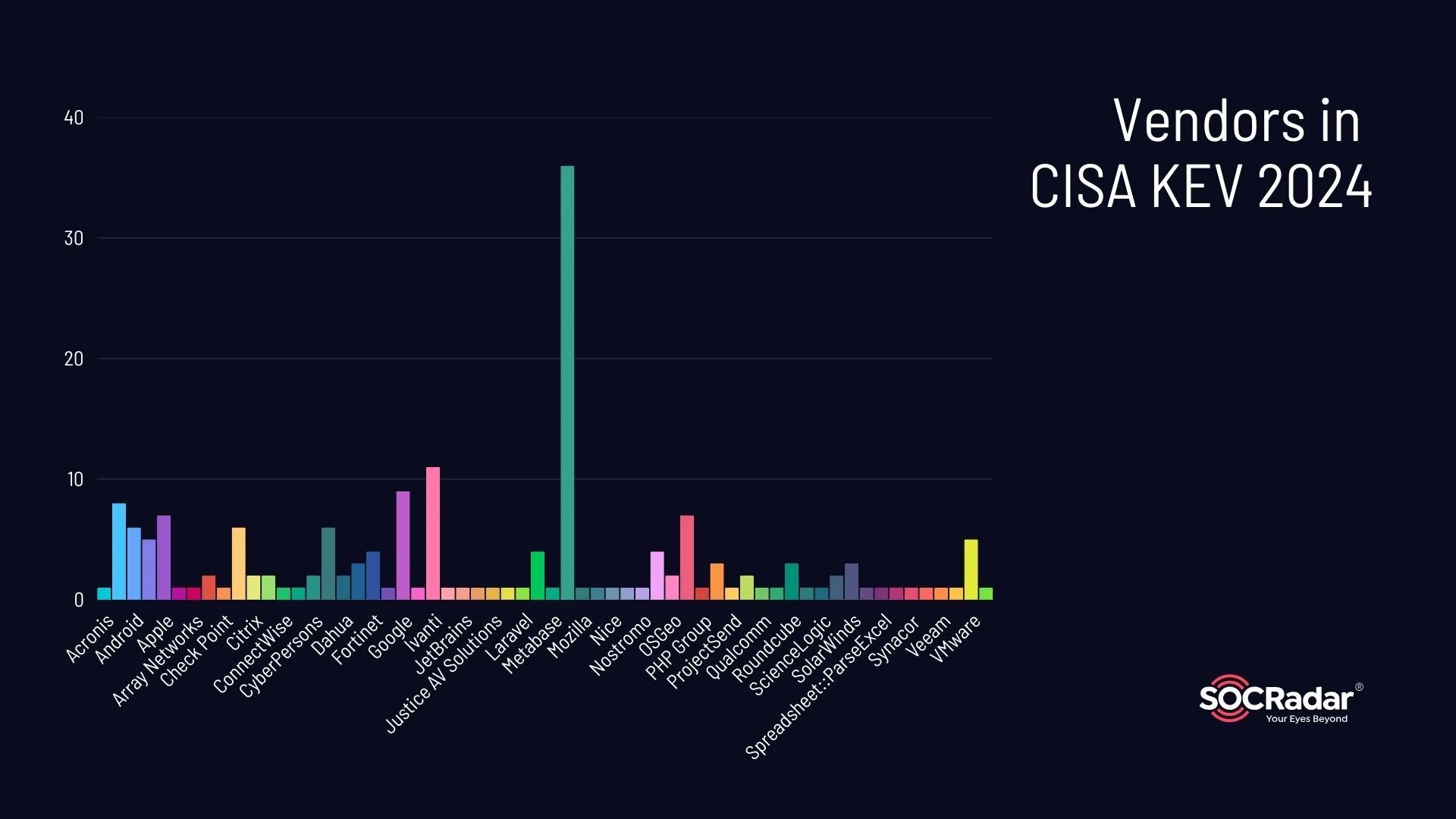
Vulnerabilities by vendors in CISA KEV 2024
The KEV Catalog highlights vulnerabilities from numerous high-profile companies, with Microsoft leading the list by a substantial difference. Other major contributors include names like Apple and VMware, reflecting their widespread adoption and the critical nature of their software in enterprise environments.
The vulnerabilities discussed in the continuation of this blog post are all included in the CISA KEV Catalog, primarily within 2024 and some in early 2025. Nevertheless, their prominence stems from being actively exploited in 2024, leading to significant repercussions for affected organizations and raising serious concerns about cybersecurity preparedness.
1. Cleo File Transfer Vulnerabilities: CVE-2024-50623 (CVSS 8.8) and CVE-2024-55956 (CVSS 9.8)
Cleo’s Managed File Transfer (MFT) software, including Harmony, VLTrader, and LexiCom, became a prime target for cybercriminals in 2024, setting a precedent for how vulnerabilities in widely used enterprise tools could be leveraged in increasingly sophisticated attacks. This case reflects a broader pattern seen throughout the year, where critical software used for secure data exchange became a key focus for threat actors, highlighting the escalating stakes in cybersecurity.
The critical flaws in Cleo allowed attackers to exploit unrestricted file uploads and downloads, leading to Remote Code Execution (RCE).
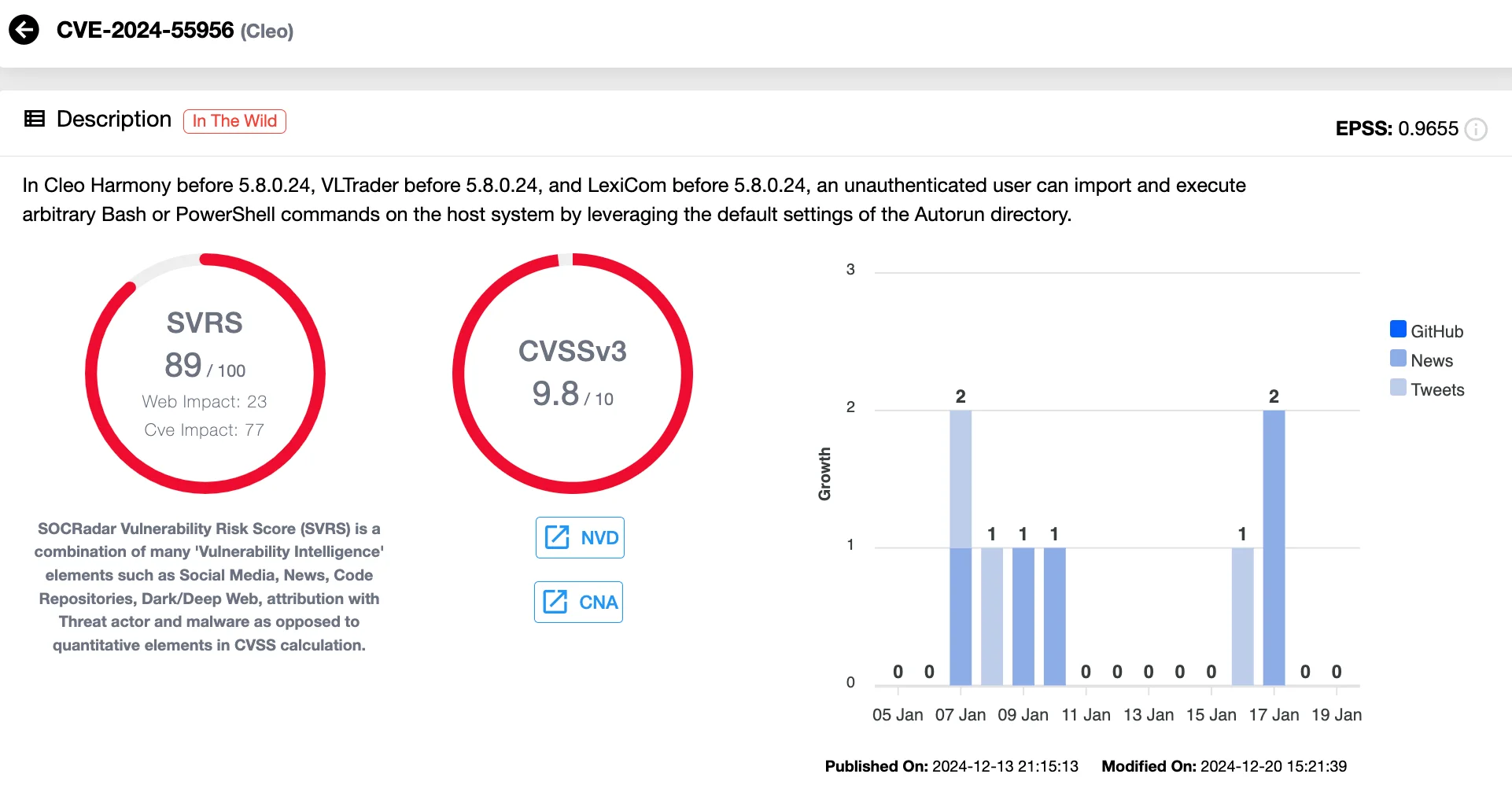
Vulnerability card of CVE-2024-55956 (SOCRadar Vulnerability Intelligence)
While Cleo attempted to patch these vulnerabilities in October 2024, incomplete fixes left systems exposed. Threat actors, including Cl0P ransomware, capitalized on this weakness, leveraging the flaws to implant backdoors, exfiltrate sensitive data, and move laterally within networks. These attacks began on December 3, with Cl0P later claiming responsibility on their data leak site, confirming their use of these vulnerabilities for targeted extortion campaigns.
The ransomware group emphasized their intent to focus solely on newly compromised victims, threatening exposure of affected organizations if demands weren’t met. Among the victims was Blue Yonder, a high-profile supply chain management firm that faced data exfiltration via its public-facing Cleo servers.
Multiple companies were affected, with Termite ransomware also previously claiming an attack. The exposure of Cleo’s software, primarily in North America, mirrors similar incidents involving MOVEit Transfer breaches, highlighting a growing trend in exploiting file transfer solutions.
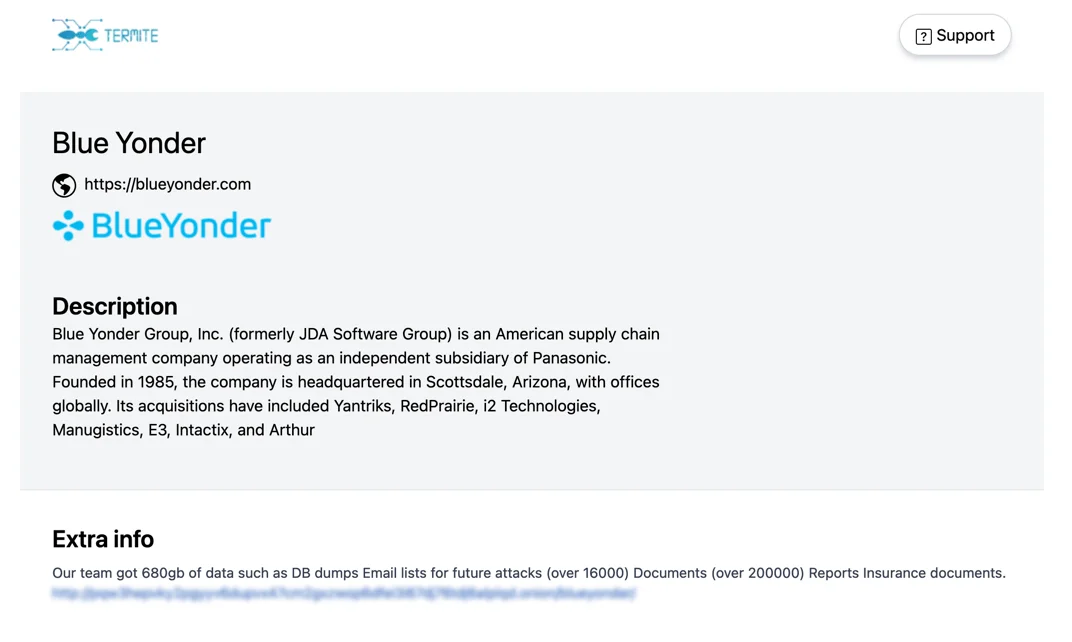
Although Termite ransomware initially made a data breach claim on Blue Yonder, the broader attacks related to Cleo software were claimed by Cl0P ransomware.
To this date, Cl0P continues to make claims regarding Cleo data theft attacks. Their most recent announcement warned of another partial exposure of victim names, scheduled for January 21, as part of their ongoing extortion campaign.
2. Ivanti VPN Vulnerabilities: CVE-2023-46805 (CVSS 8.2), CVE-2024-21887 (CVSS 9.1), and CVE-2024-21893 (CVSS 8.2)
Ivanti Connect Secure (ICS) VPN products were also at the center of multiple high-profile exploitation campaigns in 2024. This case vividly illustrates the broader trend discussed earlier: attackers are increasingly exploiting overlooked gaps in widely-used enterprise infrastructure, often with devastating outcomes.
CISA Breach: Disruption of Critical Infrastructure
In early 2024, attackers exploited CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893 to compromise CISA. The breach targeted two key systems: the Infrastructure Protection Gateway and the Chemical Security Assessment Tool, vital for monitoring U.S. infrastructure. Webshells were deployed, logs were wiped, and credentials were stolen to facilitate lateral movement. Initial suspicions pointed to Magnet Goblin, but later reports implicated UNC5325, a Chinese espionage group, in leveraging these flaws for sophisticated malware deployment, including KrustyLoader.
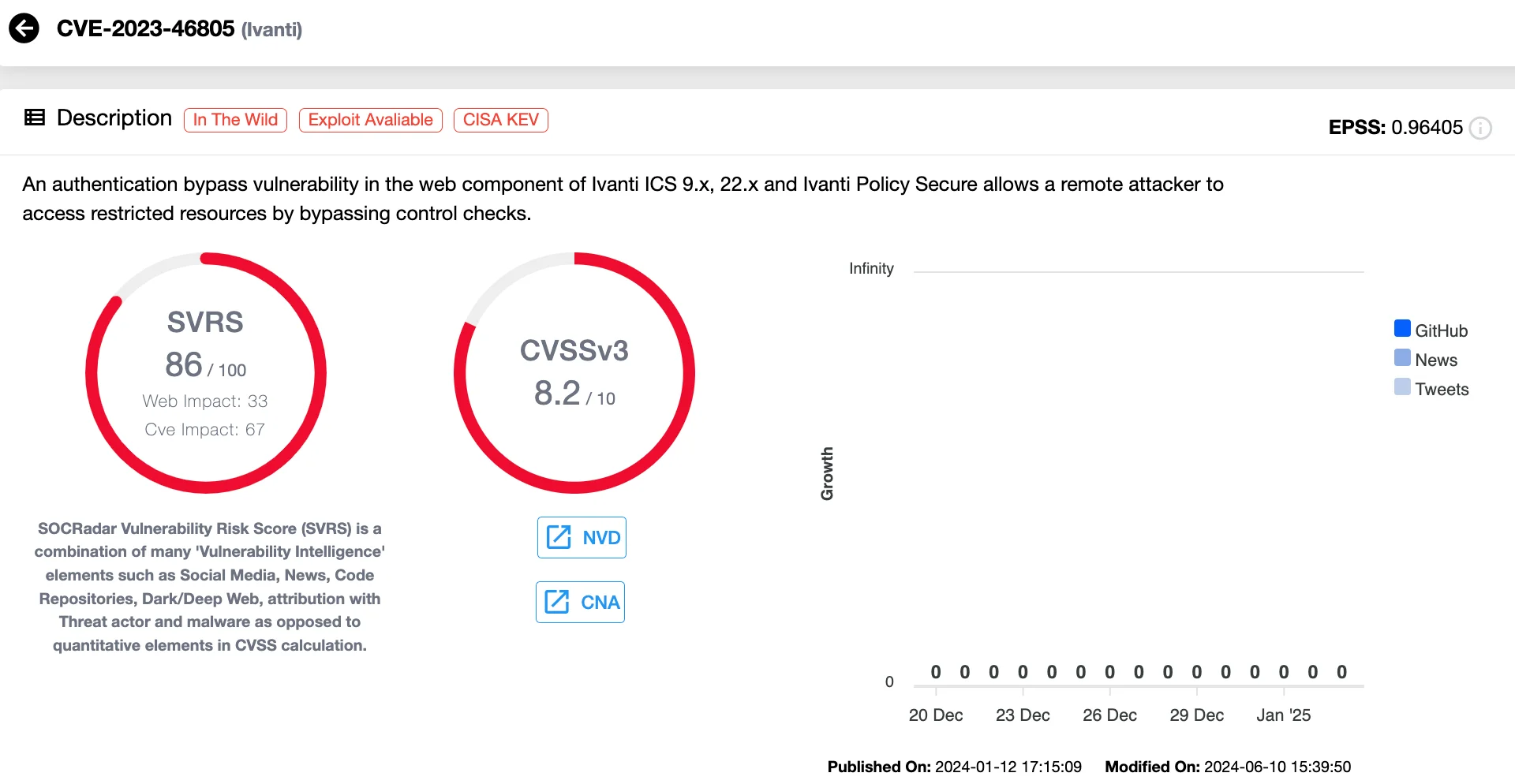
Vulnerability card of CVE-2023-46805 (SOCRadar Vulnerability Intelligence)
Magnet Goblin: Financially Motivated Exploits
Starting in January 2024, Magnet Goblin, a financially driven threat group, exploited CVE-2023-46805 and CVE-2024-21887 along with other 1-day vulnerabilities to breach edge devices. They delivered malware such as Nerbian RAT and MiniNerbian, targeting public-facing services. This campaign demonstrated the group’s rapid adoption of PoC exploits to expand their botnet and execute large-scale attacks.
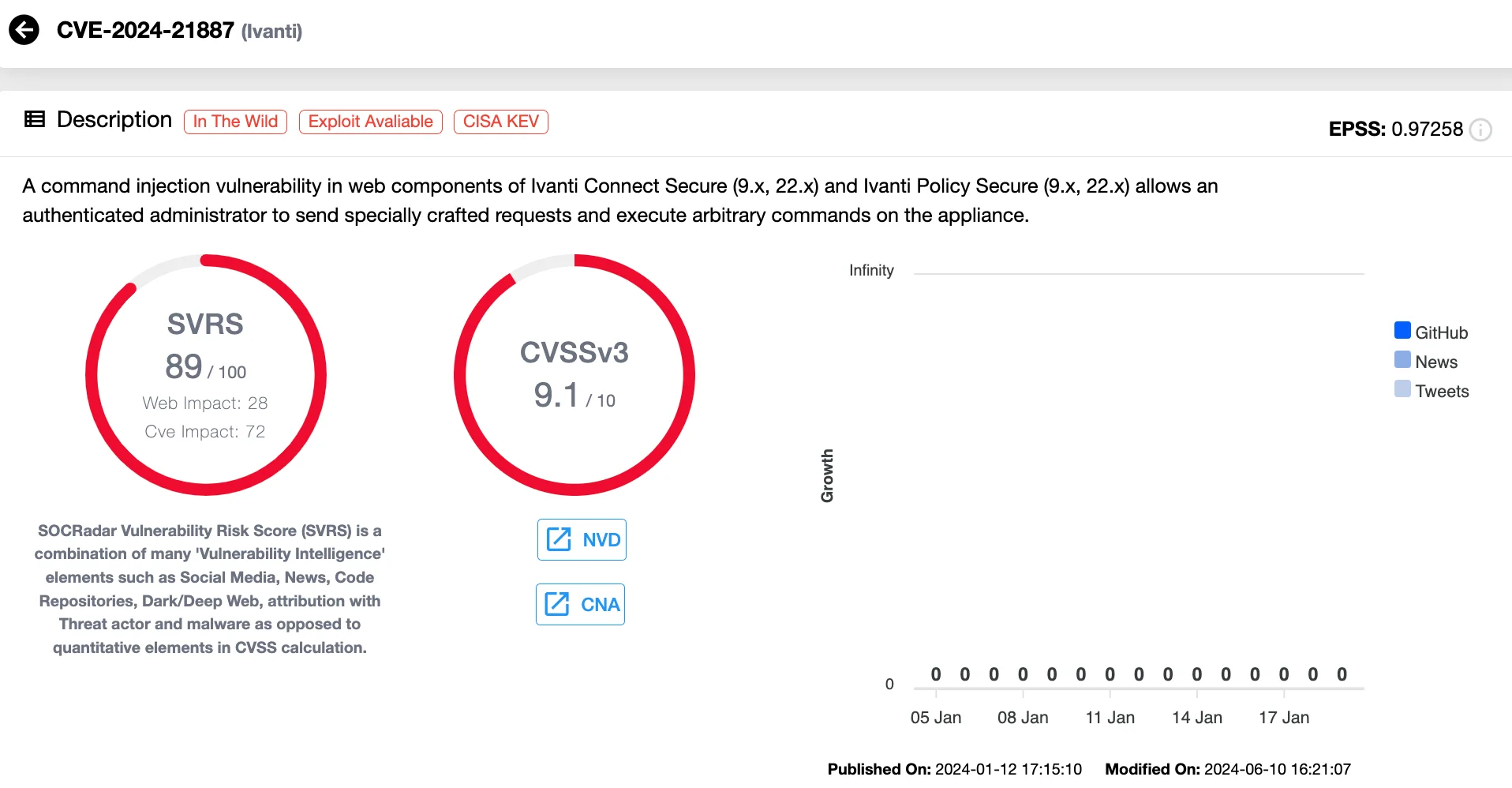
Vulnerability card of CVE-2024-21887 (SOCRadar Vulnerability Intelligence)
UNC5325 and UNC3886: Espionage and Advanced Malware
UNC5325, a Chinese-linked espionage group, exploited CVE-2024-21893 starting in January 2024 to infiltrate Ivanti appliances and deploy malware like BushWalk and LittleLamb.WoolTea. Evidence of collaboration with UNC3886, another Chinese group, surfaced, with shared techniques across sectors like defense and technology. This campaign highlighted the use of legitimate Ivanti components to maintain persistence and evade detection.
Mirai Botnet Propagation
Attackers leveraged CVE-2023-46805 and CVE-2024-21887 to integrate vulnerable systems into the Mirai botnet. Using crafted requests, they co-opted devices to launch Distributed Denial-of-Service (DDoS) attacks. This campaign demonstrated how unpatched systems could quickly be weaponized for secondary malicious purposes.
DSLog Backdoor Deployment
Researchers also discovered attackers exploiting CVE-2024-21893 to deploy the DSLog Backdoor on nearly 700 servers. This backdoor enabled persistent access through webshell insertion and tampering with legitimate components, allowing attackers to conduct reconnaissance and maintain root-level control.
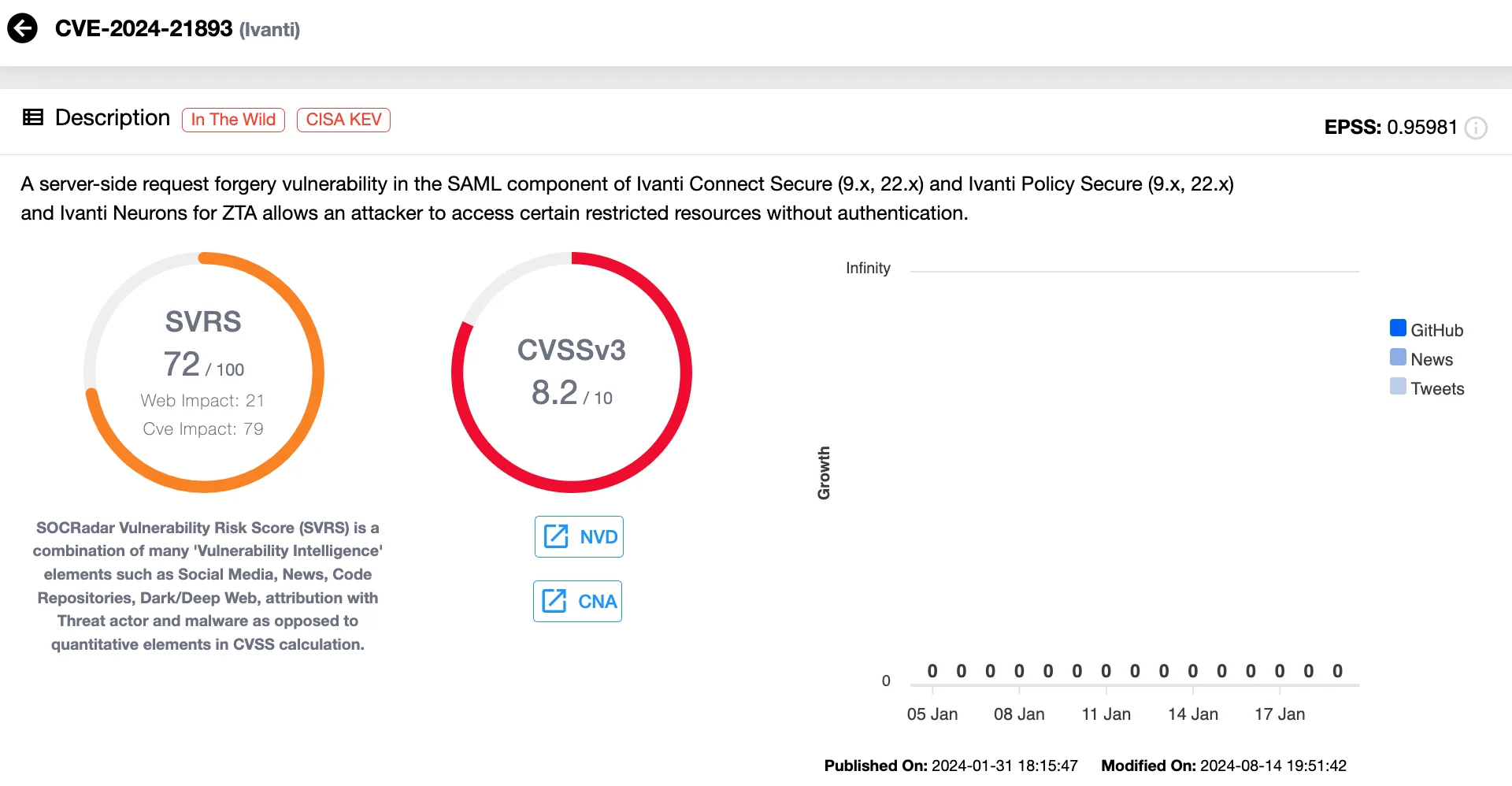
Vulnerability card of CVE-2024-21893 (SOCRadar Vulnerability Intelligence)
These reveal how threat actors exploit unpatched systems to wreak havoc. The consequences? Backdoors, data theft, and even devastating ransomware campaigns. SOCRadar’s Vulnerability Intelligence empowers your team to identify, assess, and prioritize vulnerabilities that matter most.
SOCRadar’s Vulnerability Intelligence
Here’s how Vulnerability Intelligence protects you:
- Gain real-time insights into vulnerabilities actively exploited by threat actors.
- Prioritize patches with detailed context, helping you address the most critical threats.
- Reduce the time from detection to remediation with actionable intelligence.
3. BeyondTrust Vulnerabilities: CVE-2024-12356 (CVSS 9.8) and CVE-2024-12686 (CVSS 7.5)
BeyondTrust’s Privileged Remote Access (PRA) and Remote Support (RS) solutions faced significant exploitation in late 2024 due to the two vulnerabilities. These flaws allowed unauthenticated command injection and post-exploitation privilege escalation, enabling attackers to execute arbitrary commands and compromise enterprise systems.
The most severe vulnerability, CVE-2024-12356, stemmed from improper input sanitization and required no user interaction, making it particularly dangerous. Exploitation of this flaw was linked to the Silk Typhoon threat group, a Chinese state-sponsored actor, which reportedly targeted systems including the U.S. Treasury Department. Attackers used a stolen Remote Support SaaS API key to reset application passwords and access customer networks.
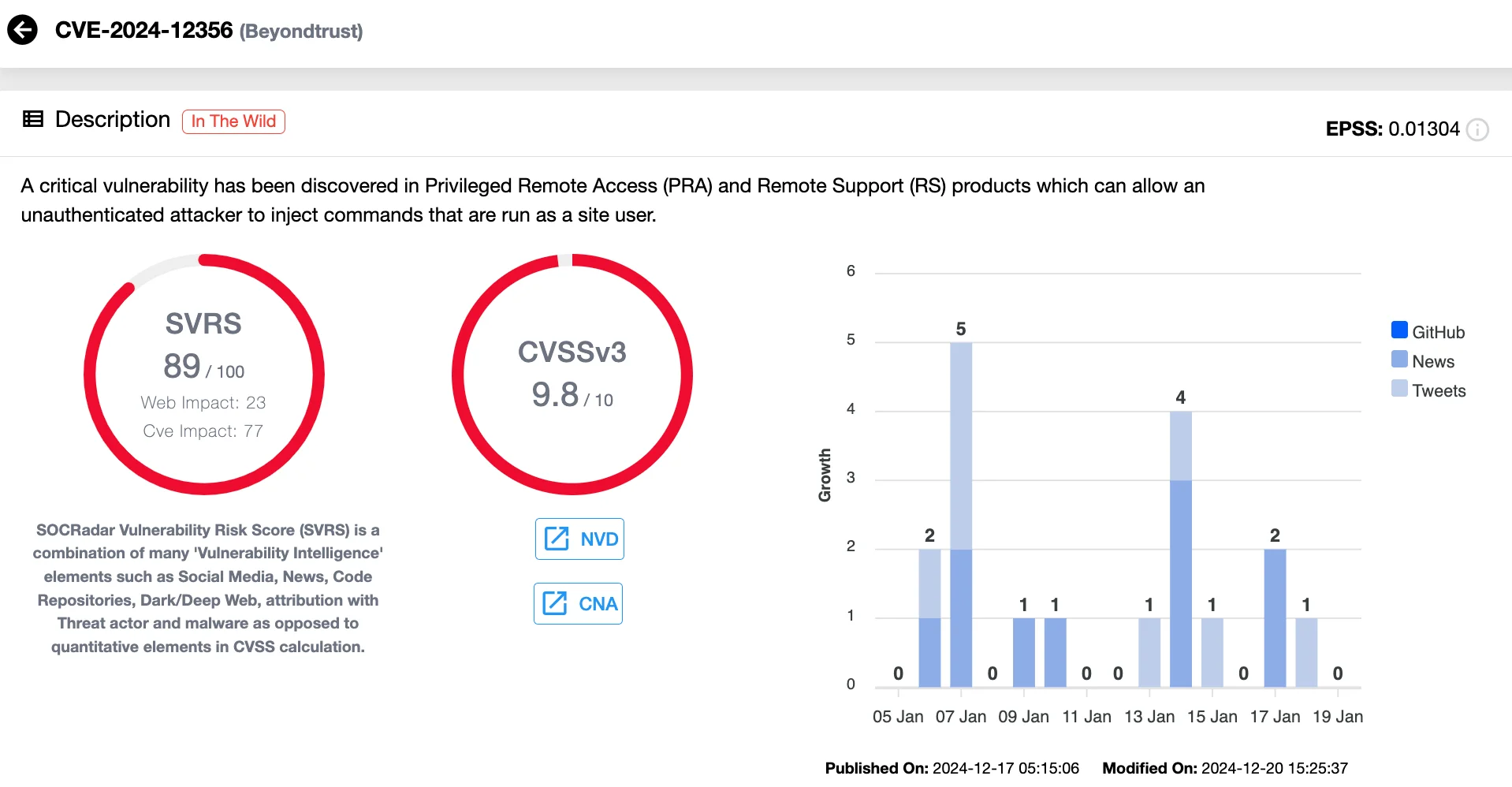
Vulnerability card of CVE-2024-12356 (SOCRadar Vulnerability Intelligence)
BeyondTrust rapidly responded by releasing patches between December 16 and 18, 2024. The vulnerabilities were added to CISA’s Known Exploited Vulnerabilities (KEV) Catalog, mandating patch deadlines for federal agencies – December 27, 2024, for CVE-2024-12356 and February 3, 2025, for CVE-2024-12686.
4. Atlassian Confluence Vulnerability: CVE-2023-22527 (CVSS 9.8)
Atlassian’s Confluence Data Center and Server products were affected by CVE-2023-22527, a critical template injection vulnerability allowing Remote Code Execution (RCE).
Exploitation attempts were first observed on January 19, 2024, with over 600 IP addresses launching attacks globally, predominantly from Russia. Threat actors initially used the vulnerability to test compromised systems via callback commands like whoami. Subsequently, cryptojacking attacks were identified, where malicious scripts deployed tools like XMRig miners to repurpose compromised systems into cryptocurrency mining networks.
The cryptojacking process included disabling security services, establishing persistence through cron jobs, and spreading across networks via compromised SSH credentials. Threat actors further obfuscated their activity by clearing logs and bash histories.
CISA added CVE-2023-22527 to its Known Exploited Vulnerabilities (KEV) Catalog on January 25, 2024. Atlassian has urged customers to apply security updates immediately, as no workarounds existed for this flaw.
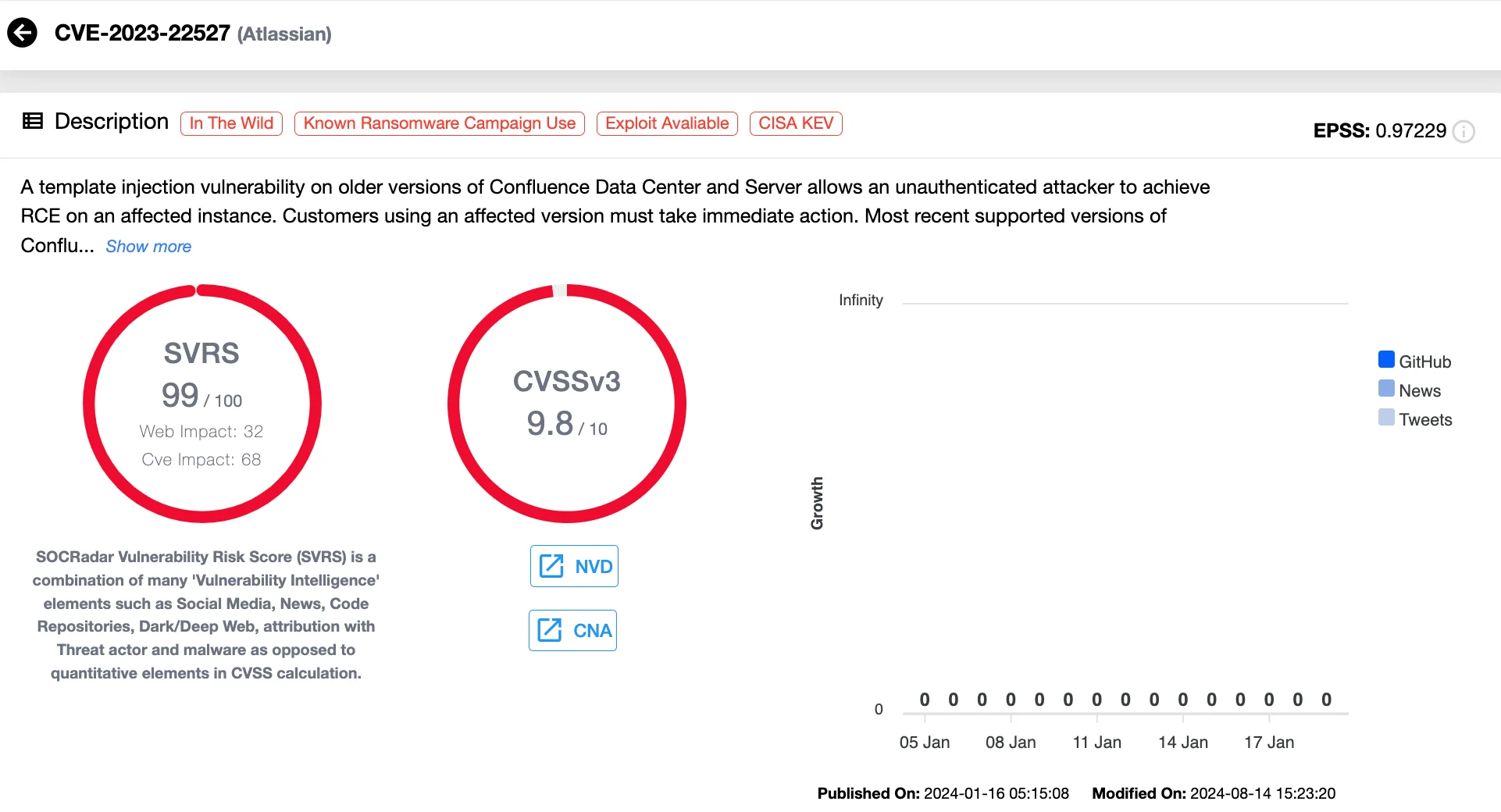
Vulnerability card of CVE-2023-22527 (SOCRadar Vulnerability Intelligence)
5. A Decade-Old Flaw in Cisco Adaptive Security Appliance (ASA): CVE-2014-2120 (CVSS 4.3)
Despite being a decade old, the CVE-2014-2120 vulnerability in Cisco’s Adaptive Security Appliance (ASA) reemerged as a critical threat, becoming a target of exploitation in 2024 and highlighting the enduring risks posed by unaddressed weaknesses in legacy systems. This flaw, stemming from insufficient input validation on the WebVPN login page, enables Cross-site Scripting (XSS) attacks and arbitrary web script injection. Exploitation of this medium-severity vulnerability requires tricking users into accessing malicious links.
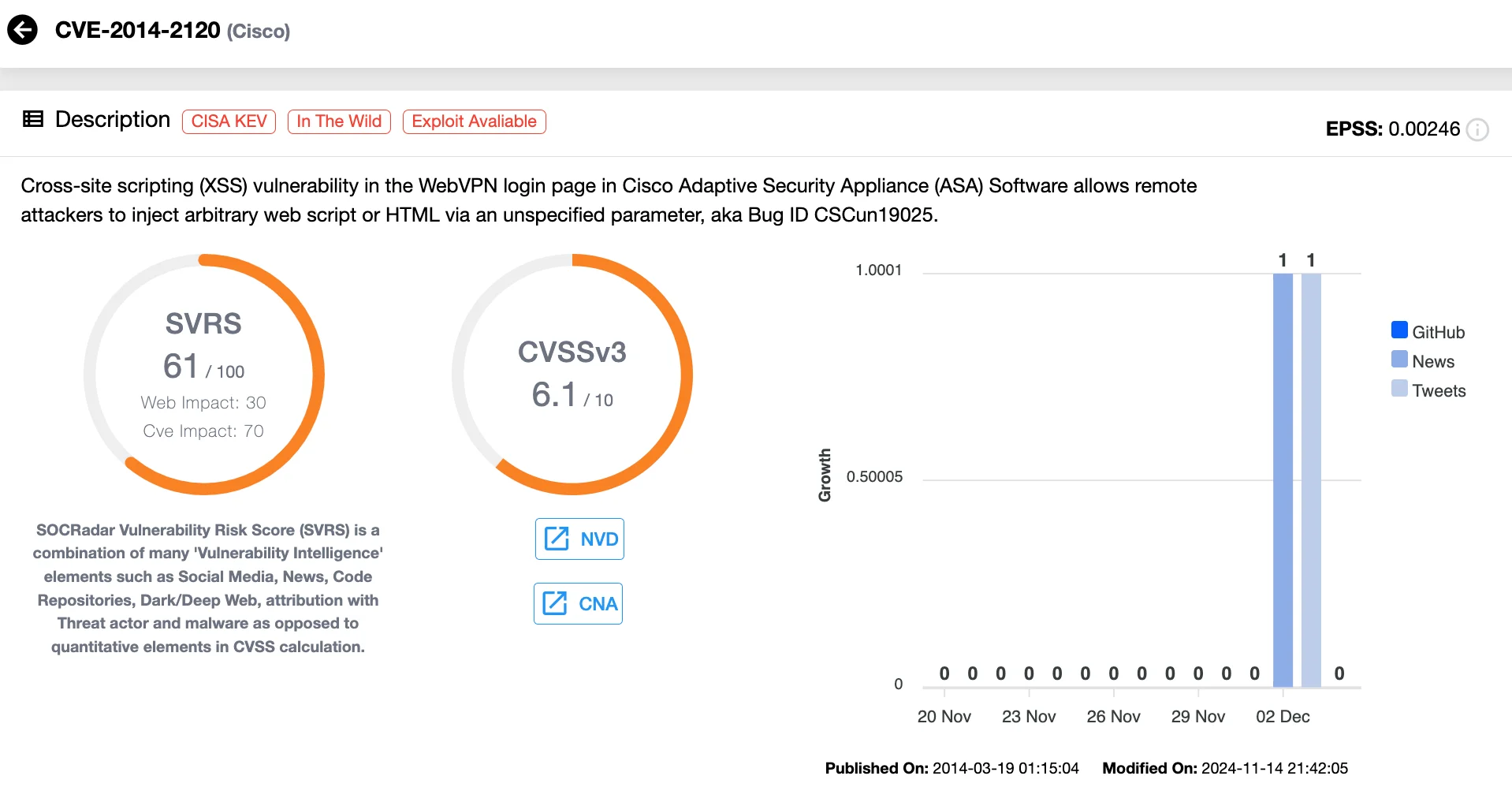
Vulnerability card of CVE-2014-2120 (SOCRadar Vulnerability Intelligence)
Cisco updated its advisory on December 2, 2024, after researchers linked CVE-2014-2120 to the Androxgh0st botnet, which has been leveraging the flaw for malware distribution and Remote Code Execution (RCE). Active since January 2024, Androxgh0st has expanded its capabilities, integrating IoT-focused payloads from the Mozi botnet. These adaptations have broadened its target scope, making it a formidable threat across diverse environments.
The Androxgh0st botnet exploits not only CVE-2014-2120 but also vulnerabilities in prominent platforms such as Atlassian JIRA and Sophos Firewall. Using an appending method, it injects malicious code into PHP files, establishing persistence and additional backdoors.
6. Windows SmartScreen Vulnerabilities: CVE-2024-38217 (CVSS 5.4), CVE-2024-38213, CVE-2024-29988, CVE-2024-21351 (CVSS 7.6), and CVE-2024-21412 (CVSS 8.1)
In 2024, multiple vulnerabilities in Windows SmartScreen were actively exploited in cyber campaigns, underscoring significant security concerns. These vulnerabilities primarily enabled security feature bypasses, allowing attackers to deliver malware while evading detection mechanisms.
Threat actors like Water Hydra demonstrated sophisticated techniques, leveraging CVE-2024-21412 to target financial markets via phishing lures on forums and Telegram channels. These campaigns utilized signed malware with Extended Validation (EV) certificates, exploiting user trust to bypass SmartScreen defenses.
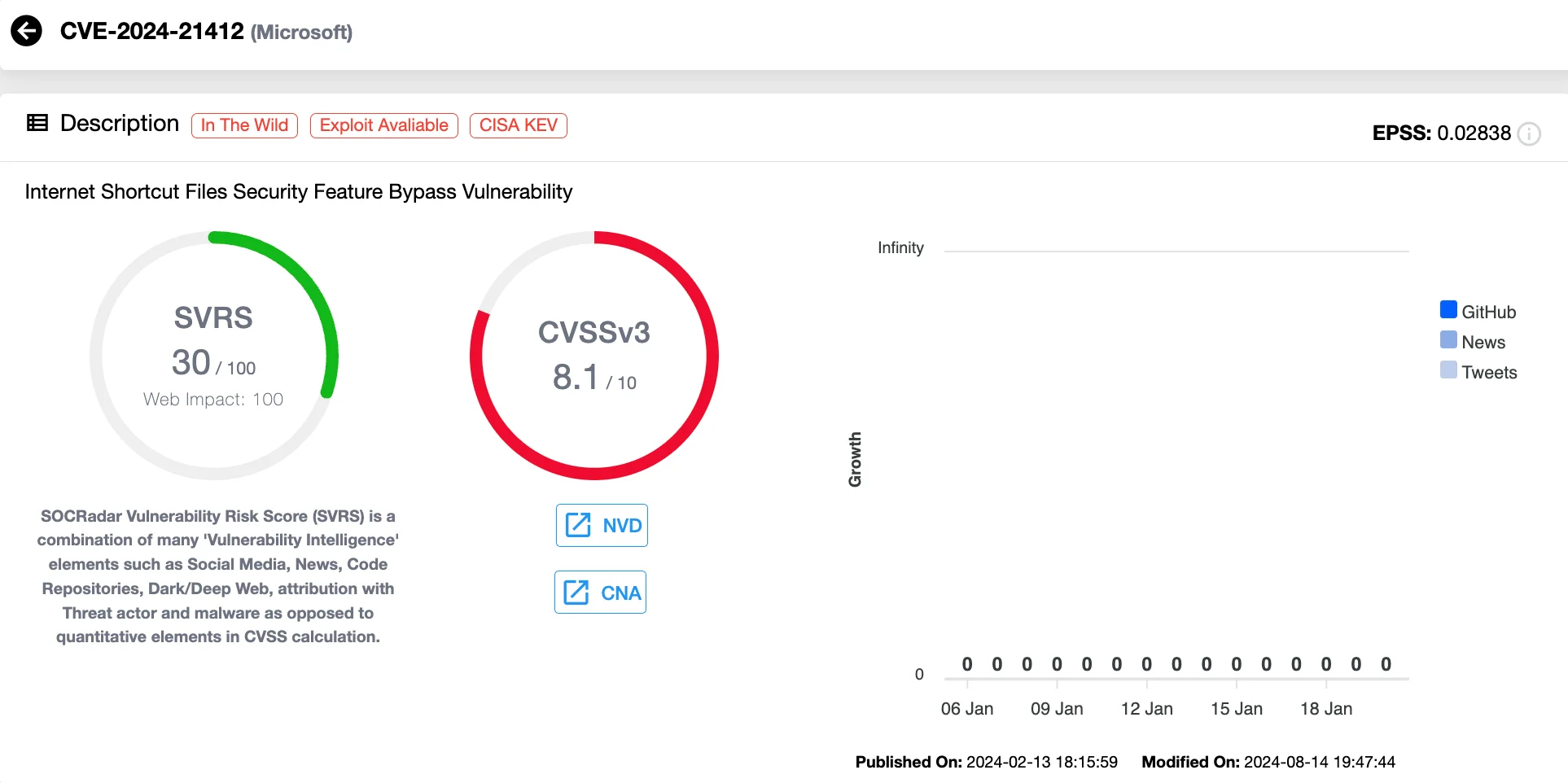
Vulnerability card of CVE-2024-21412 (SOCRadar Vulnerability Intelligence)
The ease of exploitation and reliance on social engineering tactics made these vulnerabilities attractive targets. Attackers bypassed SmartScreen’s reputation-based protections to deploy a variety of malware, including DarkMe, Lumma Stealer, and Meduza Stealer. The vulnerabilities’ low exploitation complexity and potential for significant damage underscored their appeal to cybercriminals.
Stealer malware collect data from infected devices, which is later compiled into stealer logs – a goldmine for cybercriminals. These logs contain sensitive data, including credentials, session cookies, and even payment details – making them a critical risk for businesses and individuals alike. Cybercriminals sell these logs on the dark web, enabling account takeovers, identity theft, and fraudulent transactions.
Monitor black market, PII exposure, and more with SOCRadar’s Dark Web Monitoring
With SOCRadar’s Dark Web Monitoring, you can proactively detect when your organization’s credentials or sensitive data appear on the hacker forums. Furthermore, with the Threat Hunting module, you can search if your sensitive information is exposed through stealer logs.
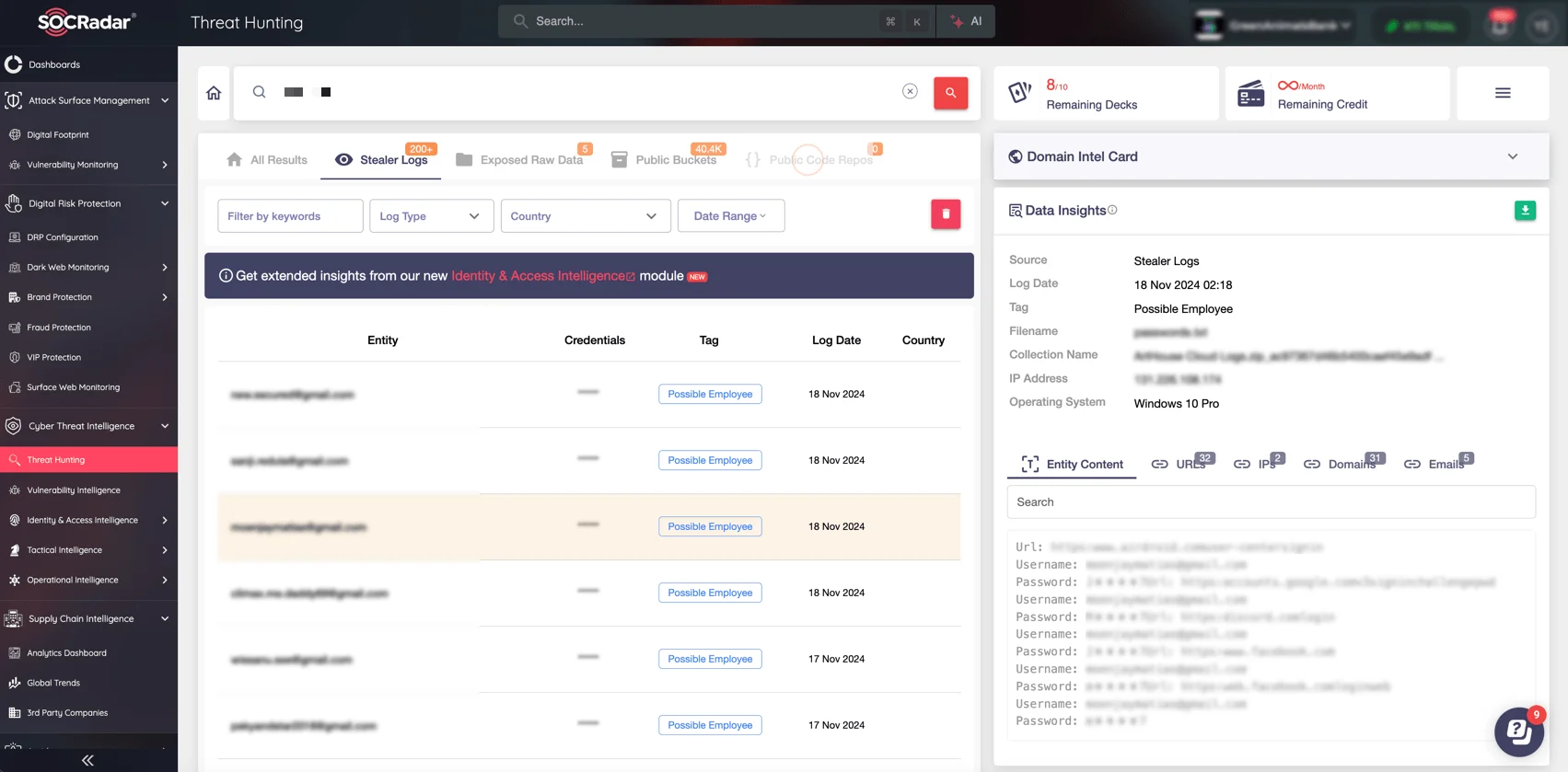
SOCRadar’s Threat Hunting, Stealer Logs
7. Fortinet FortiOS Vulnerability: CVE-2024-21762 (CVSS 9.6)
In early 2024, Fortinet disclosed a critical Remote Code Execution (RCE) vulnerability in its FortiOS SSL VPN, identified as CVE-2024-21762. This out-of-bounds write flaw enables unauthenticated attackers to execute arbitrary code by sending maliciously crafted requests. Despite the availability of patches, this vulnerability has seen active exploitation by advanced threat actors, including Volt Typhoon, a Chinese state-sponsored group.
Volt Typhoon leveraged this vulnerability to deploy custom malware and maintain persistent access, targeting sensitive networks globally. The risk escalated in March 2024, when a Proof-of-Concept (PoC) exploit surfaced on hacker forums, enabling more threat actors to capitalize on the flaw. Researchers detailed its exploitation, with techniques involving payload generation to gain full control of compromised systems.
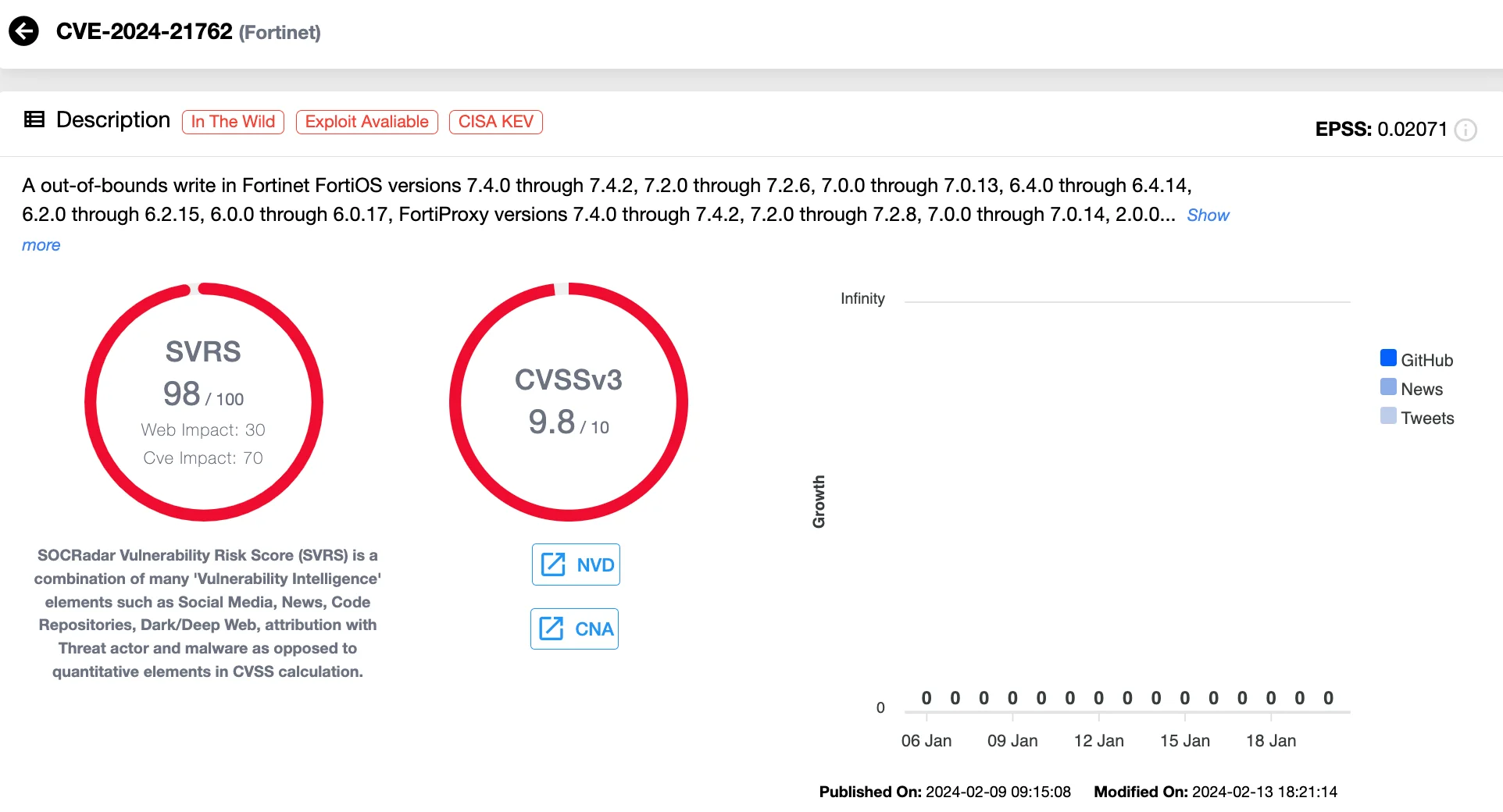
Vulnerability card of CVE-2024-21762 (SOCRadar Vulnerability Intelligence)
8. ConnectWise ScreenConnect Vulnerability Exploited in Diverse Campaigns: CVE-2024-1709 (CVSS 10)
CVE-2024-1709, a critical authentication bypass vulnerability in ConnectWise ScreenConnect, has been exploited by multiple threat actors in 2024. This flaw allows attackers to gain administrative access, extract confidential data, and execute Remote Code Execution (RCE) without user interaction. Despite a patch release on February 21, exploitation continued to target unpatched systems in 2024.
Threat actors such as LockBit, Black Basta, Bl00dy, and Kimsuky have leveraged CVE-2024-1709 for varied objectives, from ransomware deployment to cyber-espionage. North Korean group Kimsuky used the vulnerability to distribute ToddleShark malware, an evolution of its earlier BabyShark and ReconShark backdoors, targeting government entities and think tanks worldwide. Meanwhile, phishing campaigns exploited ScreenConnect to deliver ransomware and tools like AsyncRAT and XWorm, disguising malware within cryptocurrency-related downloads and healthcare-themed lures.
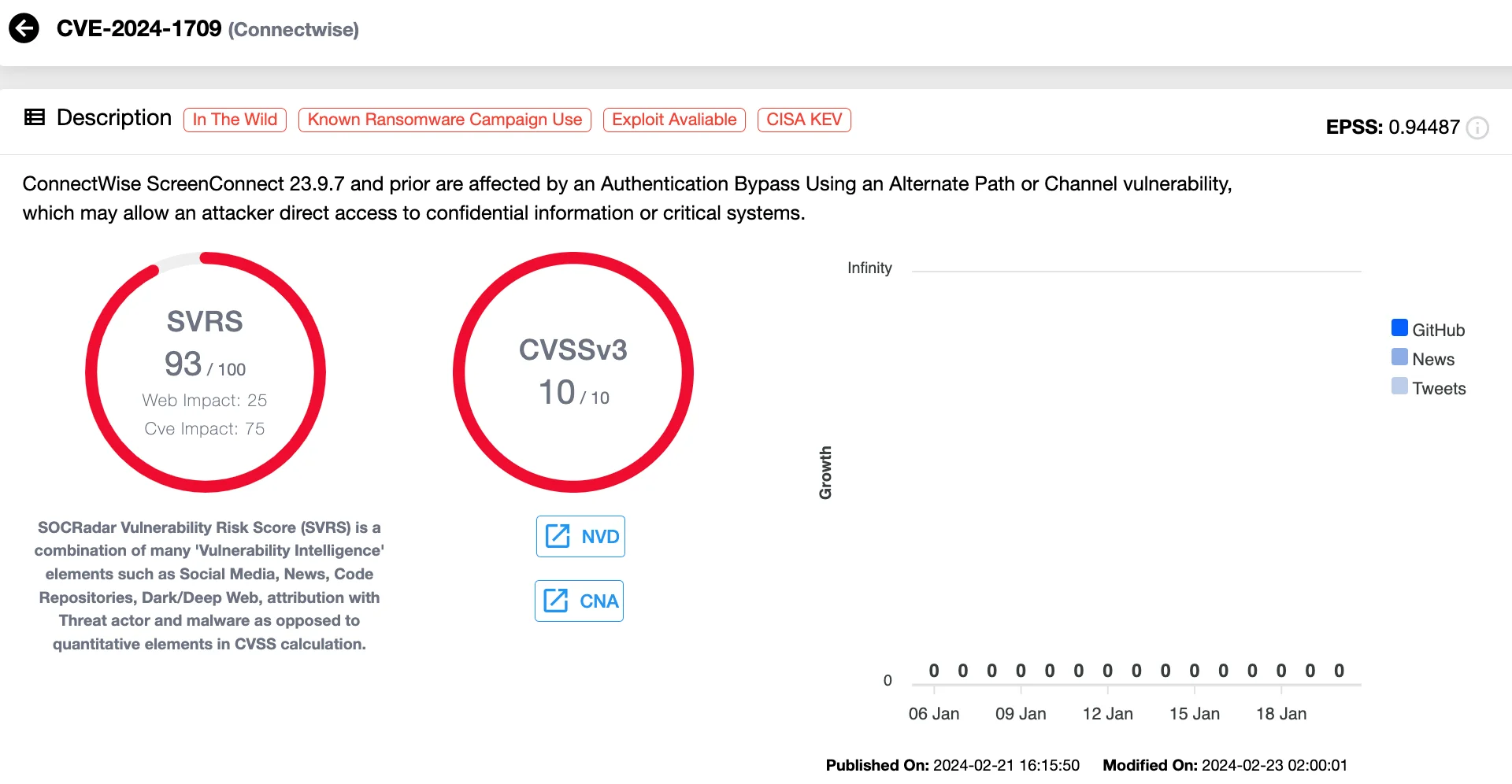
Vulnerability card of CVE-2024-1709 (SOCRadar Vulnerability Intelligence)
9. VMware ESXi Hypervisor Vulnerability: CVE-2024-37085 (CVSS 6.8)
CVE-2024-37085, an authentication bypass vulnerability in VMware ESXi hypervisors, has been actively exploited by ransomware groups throughout 2024. This flaw leverages weak integration with Active Directory, enabling attackers to create an “ESX Admins” group, granting administrative privileges over ESXi hypervisors and hosted virtual machines.
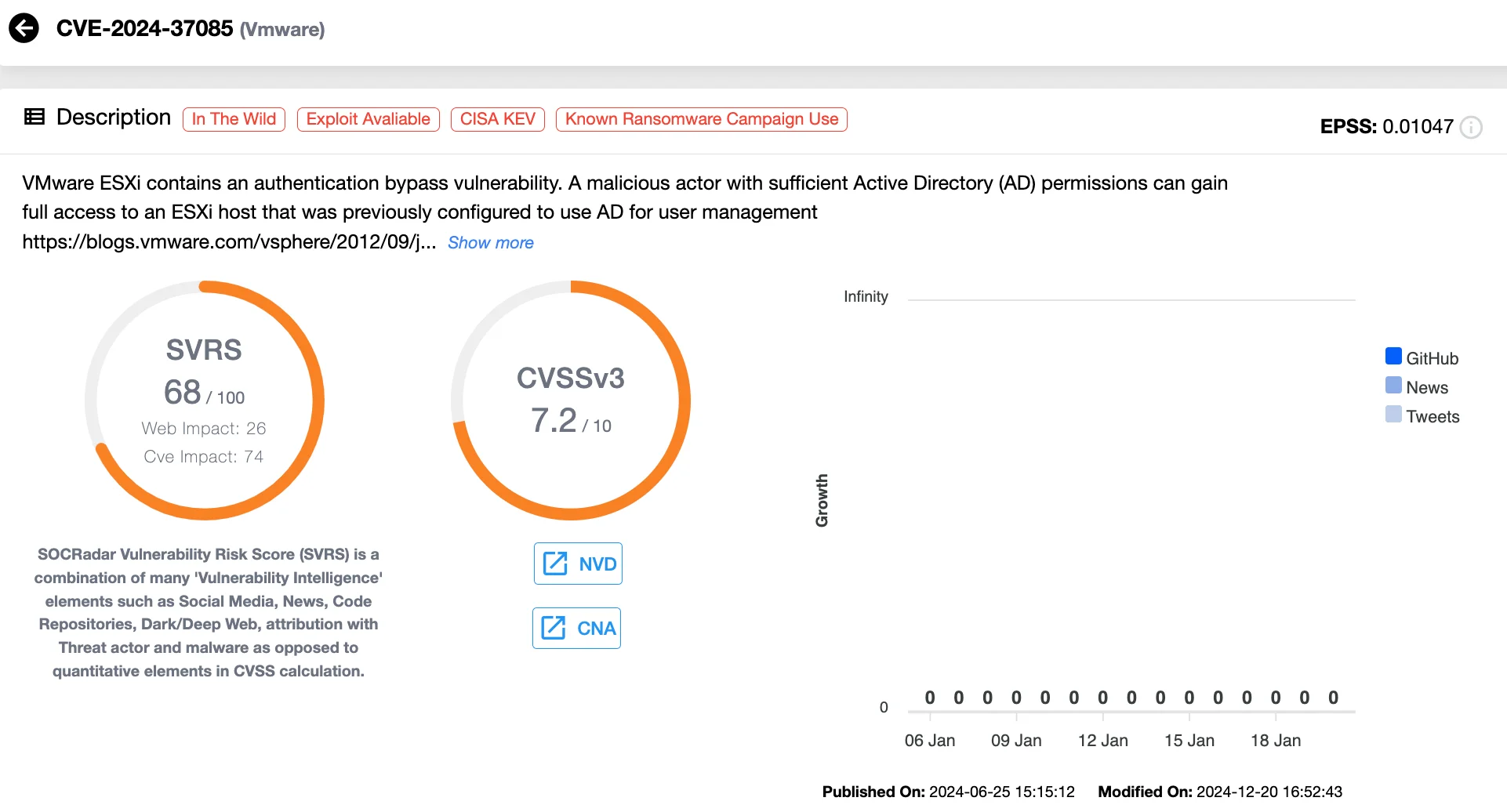
Vulnerability card of CVE-2024-37085 (SOCRadar Vulnerability Intelligence)
The vulnerability, disclosed by Broadcom, allows privilege escalation and full hypervisor control, leading to devastating impacts on network infrastructure. Microsoft has highlighted ransomware campaigns, including attacks by Storm-0506 and Octo Tempest, that exploited this vulnerability. In one case, Black Basta ransomware attackers used CVE-2024-37085 to encrypt ESXi file systems, disrupting operations at a North American engineering firm.
While CVE-2024-37085 is unlikely to serve as an initial access vector, attackers often pair it with other exploits, such as Qakbot infections or Windows vulnerabilities, to gain system access before leveraging this flaw.
10. Windows Kernel Vulnerability: CVE-2024-21338 (CVSS 8.7)
The last vulnerability on our list is CVE-2024-21338, a Windows Kernel Elevation of Privilege vulnerability in the appid.sys AppLocker driver. It has been actively exploited by the Lazarus Group as a zero-day to deliver an updated version of their FudModule rootkit. Microsoft confirmed the vulnerability’s active exploitation on February 28, 2024.
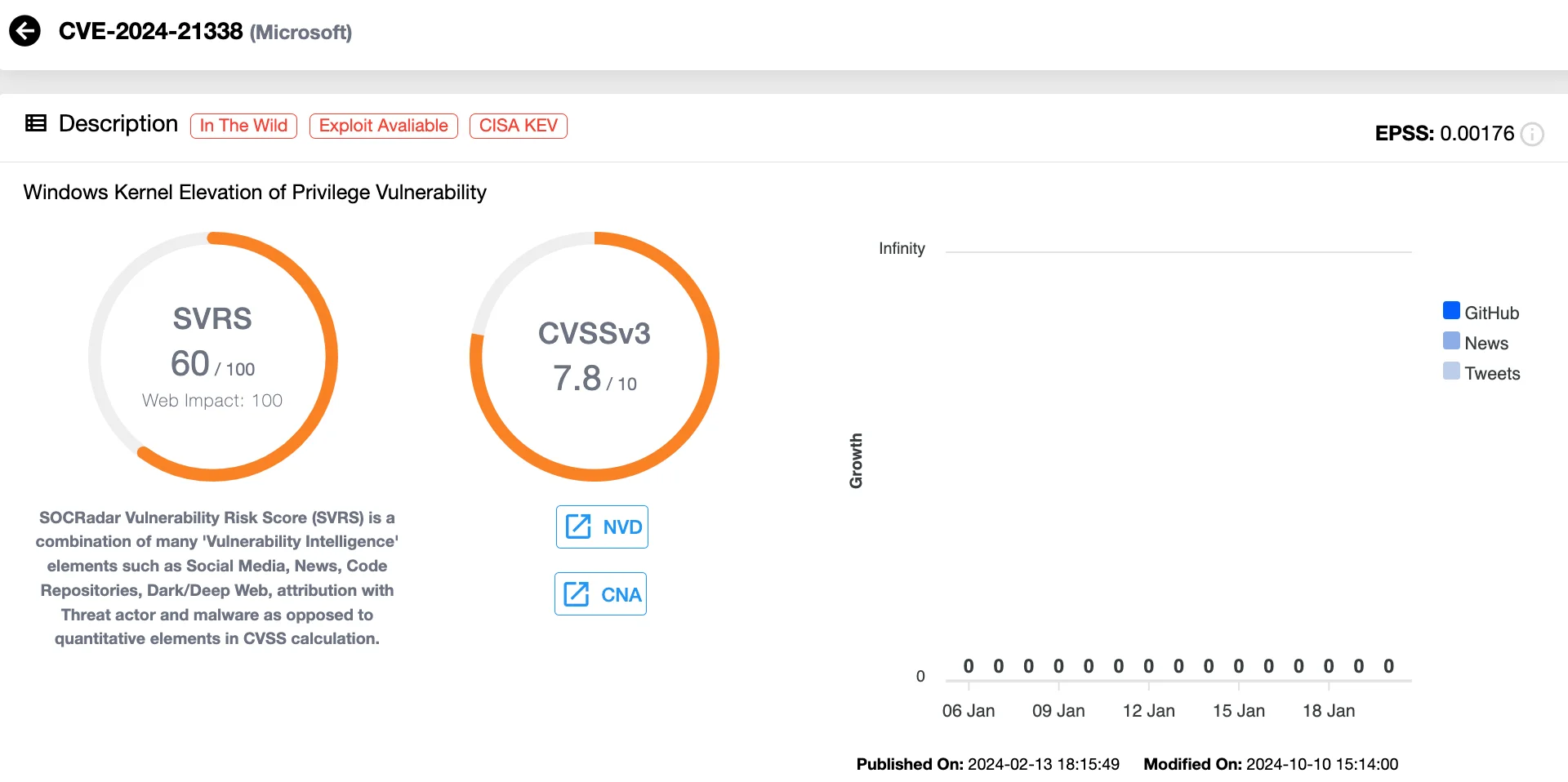
Vulnerability card of CVE-2024-21338 (SOCRadar Vulnerability Intelligence)
The flaw allows attackers with initial system access to launch specially crafted applications, gaining SYSTEM privileges and kernel-level control. Lazarus used the vulnerability to establish a read/write kernel primitive, enabling direct manipulation of kernel objects. This updated FudModule rootkit includes advanced features to evade detection and disable prominent security tools like Microsoft Defender, CrowdStrike Falcon, and HitmanPro, representing a strategic evolution from the group’s prior Bring Your Own Vulnerable Driver (BYOVD) techniques.
The attack also featured a previously undocumented Remote Access Trojan (RAT), showcasing Lazarus’s broader strategy to maintain persistence and conduct espionage.
Track company assets and vulnerabilities with SOCRadar’s ASM module
Unmonitored and misconfigured systems can expose your organization to devastating attacks, from data breaches to ransomware. SOCRadar’s Attack Surface Management provides complete visibility into your organization’s digital footprint, identifying exposed assets and vulnerabilities before attackers exploit them.
SOCRadar’s ASM module maps your entire attack surface, including shadow IT and third-party risks. It continuously monitors for misconfigurations, exposed ports, and critical vulnerabilities, providing your security team with actionable insights to minimize your attack surface effectively.
Conclusion
The vulnerabilities exploited in 2024 highlight a grim reality for organizations: the rapid pace of exploit development and the sheer volume of vulnerabilities leave little room for complacency. From critical zero-day flaws to overlooked legacy vulnerabilities, each case underscores the importance of proactive cybersecurity strategies.
Cybercriminals target technical weaknesses, exploiting gaps in patch management, resource allocation, and organizational awareness. The alarming reduction in the average time to exploit – from weeks to mere days – further emphasizes the need for vigilance. Left unaddressed, these vulnerabilities can lead to devastating consequences, including financial losses, operational disruptions, and reputational harm.
As threat actors grow more sophisticated, organizations must adopt advanced solutions to secure their digital environments. SOCRadar’s suite of cybersecurity tools offers end-to-end protection:
- Vulnerability Intelligence empowers teams to prioritize and mitigate threats in real time.
- Attack Surface Management (ASM) ensures complete visibility of exposed assets and vulnerabilities.
- Dark Web Monitoring provides insights into stolen data and emerging threats from underground markets.
Staying ahead of attackers requires not just addressing vulnerabilities but also anticipating and adapting to evolving threats. With solutions like SOCRadar, organizations can strengthen their defenses, reduce risks, and build resilience against future cyber challenges.



































