
Top 10 Supply Chain Monitoring Platforms
In today’s globalized business environment, nearly every organization is part of a complex web of interdependencies. This interconnectedness, while enabling collaboration and efficiency, also introduces significant vulnerabilities.
With supply chains often extending beyond the organization’s boundaries, the potential for security breaches through third-party vulnerabilities can have far-reaching consequences.

AI illustration of a supply chain (Bing Image Creator)
In a recent blog post titled “Third-Party Vendor Breaches,” we examined the specifics of such breaches, including their causes, related statistics, notable incidents from recent years, and the most effective mitigation strategies. We highlighted incidents such as the Ongoing Operations ransomware attack and the AT&T breach, both resulting from third-parties. In yet another blog post, we elaborated how organizations could track their “Supply Chain’s Dark Web Activities,” and provided key insights and solutions.
Building on our previous discussions, this post will explore platforms specifically designed to prevent vendor breaches or mitigate their causes and effects. Additionally, we will showcase many features offered by our platform, SOCRadar XTI, designed to enhance your organization’s security posture and strengthen your supply chain’s security with advanced monitoring solutions.
Why is Supply Chain Monitoring So Important?
As we previously highlighted in the “Third Party Vendor Breaches” blog post, 98% of organizations globally are connected to at least one third-party vendor that has experienced a breach.
A single vendor’s cyber exposure can ripple through the entire supply chain, leading to significant risks such as data breaches, financial losses, and operational disruptions. The potential for supply chain attacks to escalate into severe consequences for all connected entities is a critical concern that demands vigilant monitoring and proactive risk management.
Risks Stemming from Vendor Cyber Exposure
When a vendor’s systems are compromised, the impact is not isolated. It can lead to unauthorized access to sensitive information, interruption of services, and in severe cases, complete operational shutdowns.
The compromised vendor may inadvertently become a conduit for attackers to infiltrate other organizations connected within the supply chain, amplifying the potential damage exponentially. This interconnected risk is why monitoring supply chains and understanding the cyber exposure of vendors is not just beneficial but essential.
Case Study: Impact of MOVEit Breaches
A stark illustration of the dangers posed by third-party vulnerabilities is the mass exploitation of MOVEit Transfer by the Cl0p ransomware gang in May 2023.
Widely used for secure file transfers, MOVEit Transfer became a target for Cl0p, who leveraged several vulnerabilities throughout the year, affecting over 2,500 organizations and compromising the data of more than 77 million individuals worldwide.
Even though the vulnerabilities were patched, the ransomware gang used previous infiltrations and took advantage of unpatched instances to cause widespread disruptions. The case of MOVEit clearly illustrates how the exploitation of one vendor can lead to doom.
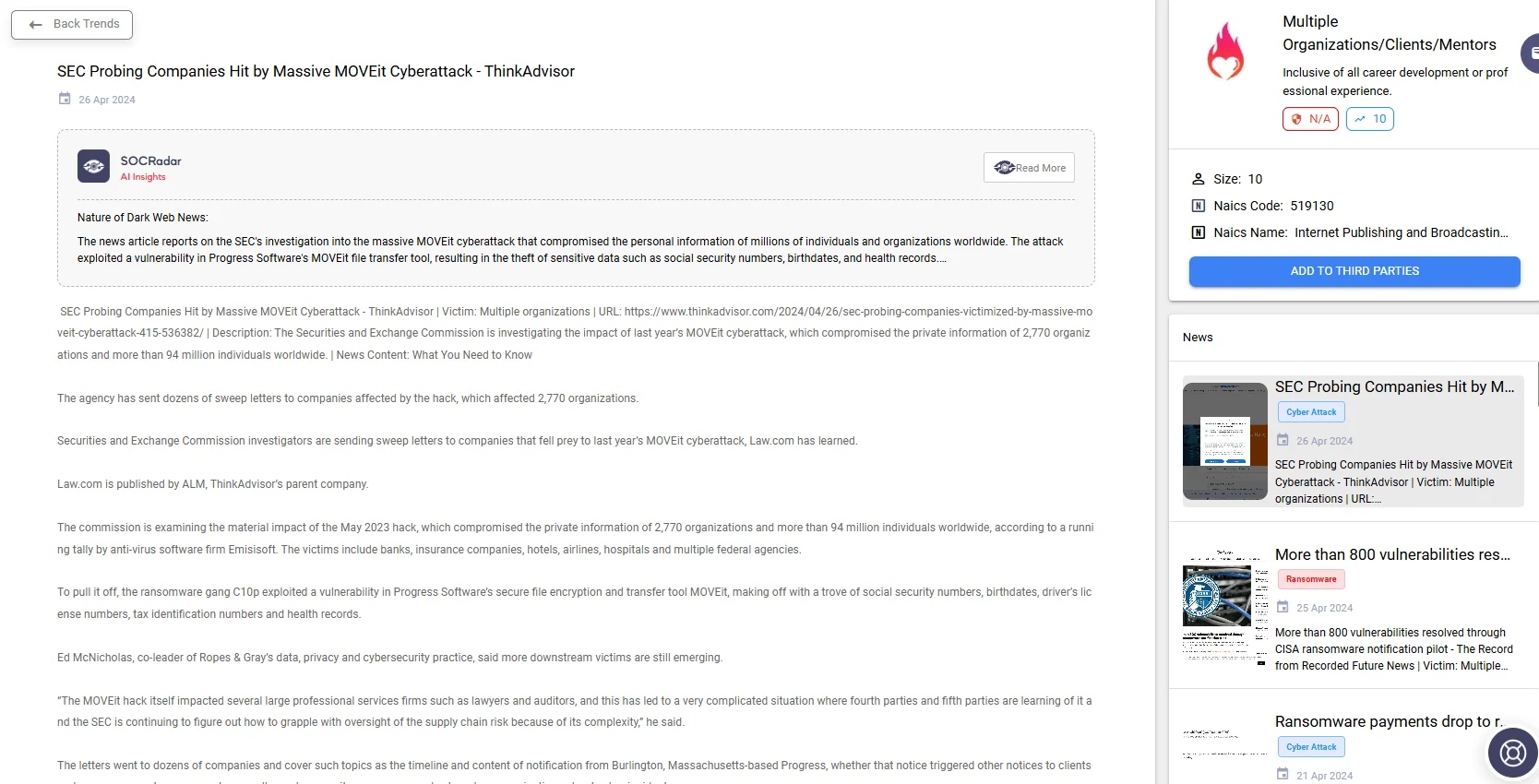
Details of a supply chain attack using the MOVEit vulnerability; the page provides access to related news and reports. (Source: SOCRadar Supply Chain Intelligence)
The Solution: Supply Chain Risk Management
Effective monitoring strategies enable organizations to detect vulnerabilities early, assess potential threats in real-time, and implement corrective measures before attackers can exploit exposed weaknesses.
Regular assessments and updates, combined with an understanding of each vendor’s security posture, are crucial to mitigating risks and protecting both the organization and its extensive network of partners.
Supply chain monitoring platforms can essentially provide the tools required for managing and mitigating the risks associated with vendor cyber exposure, ensuring that organizations can maintain operational integrity and trust in an increasingly digital world.
Benefits of Supply Chain Monitoring Platforms
A supply chain security strategy must involve multiple components. Thus, supply chain monitoring platforms are expected to do more than simply monitor recent incidents; they are expected to help organizations mitigate risks associated with third-party vendors, ensure regulatory compliance, and maintain customer and partner trust.
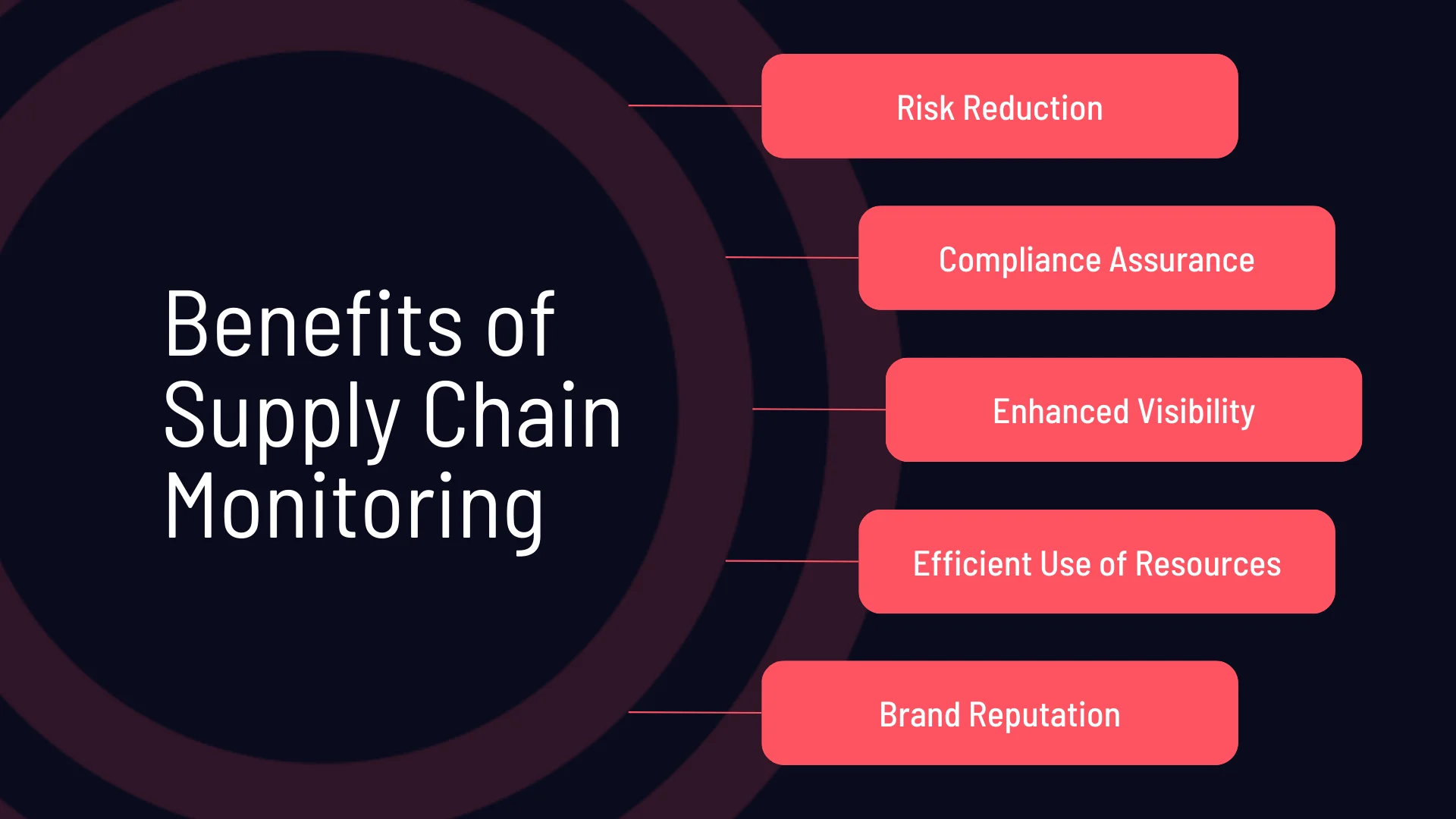
What are the benefits of supply chain monitoring platforms?
Here’s a closer look at the significant benefits that supply chain monitoring platforms offer:
- Risk Reduction: Supply chain monitoring platforms play a critical role in identifying potential risks that third-party vendors might pose. By continuously monitoring their security postures, these platforms can detect vulnerabilities and potential threats early. This proactive approach allows organizations to address risks before they escalate into security incidents, significantly reducing the likelihood of data breaches, financial losses, and operational disruptions.
- Compliance Assurance: Many organizations prioritize compliance due to strict regulatory requirements in various industries. Supply chain monitoring platforms help them by providing continuous oversight of vendors’ security practices. This ensures that all parts of the supply chain adhere to industry standards and regulatory frameworks, helping organizations avoid hefty fines and legal repercussions associated with non-compliance.
- Enhanced Visibility: One of the key advantages of using these platforms is the increased visibility they provide into the security practices and weaknesses of third-party vendors. Visibility into vendors’ practices and weaknesses allows organizations to make informed decisions about their supply chain partnerships, assess security risks accurately, and prioritize remediation efforts.
- Efficient Use of Resources: Managing the security of multiple third-party vendors can be resource-intensive. Supply chain monitoring platforms can streamline this task by automating risk assessments, tracking compliance, and providing actionable insights.
- Trust and Brand Reputation: In today’s market, trust is a valuable currency for every business. Maintaining a secure supply chain is vital in protecting brand reputation. By ensuring that all security measures are in place and that third-party risks are effectively managed, organizations can build and maintain trust with their customers and partners.
In conclusion, supply chain security monitoring platforms offer a comprehensive suite of benefits that help organizations navigate the complexities of modern supply chains safely and effectively. By leveraging these tools, businesses can ensure the security and integrity of their operations, fostering a secure and resilient supply chain ecosystem.
SOCRadar’s Supply Chain Intelligence is a key module in this context; it tracks vendors, breaches, and the most recent trends and delivers summaries of threats, including from the dark web and the surface web. By leveraging SOCRadar’s refined Supply Chain Intelligence capabilities, organizations can significantly enhance their defense mechanisms against third-party security breaches, ensuring robust protection for their assets and maintaining operational resilience in a complex cyber threat landscape.
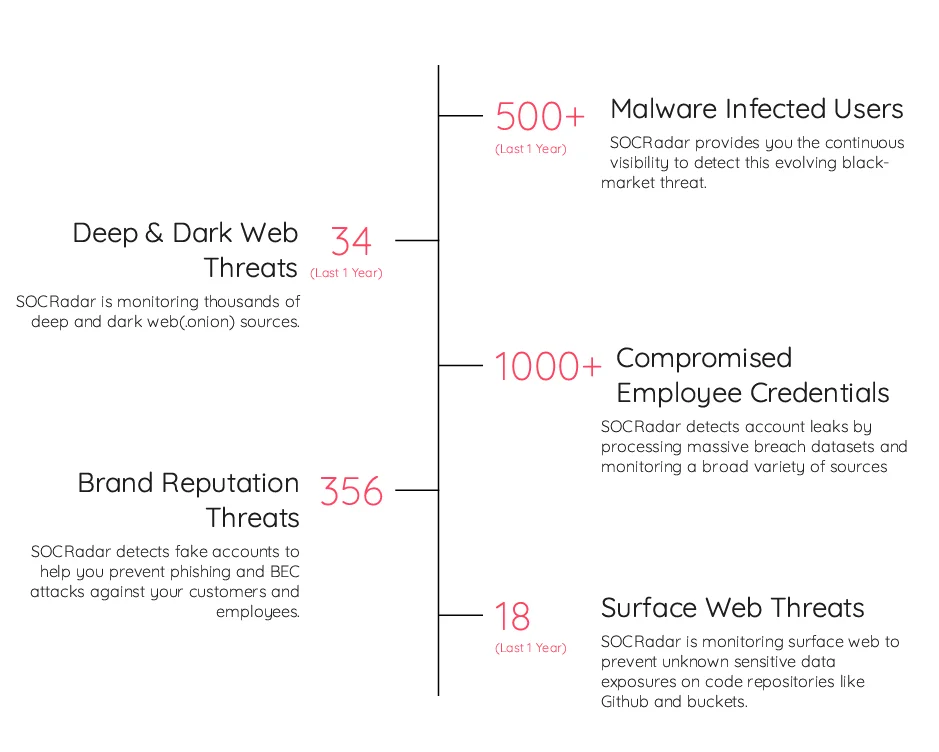
First page of a sample third-party company report (SOCRadar’s Supply Chain Intelligence)
Top 10 Platforms to Monitor Your Supply Chain
In this section, we will examine the leading platforms designed to help organizations manage and mitigate the risks associated with third-party vendors.
Our selection of these top supply chain monitoring platforms is based on a combination of their features and market reputation. These platforms have been chosen from Gartner’s IT vendor risk management category and are presented in no particular order.
1. SecurityScorecard
SecurityScorecard offers a rating technology widely used for self-monitoring, third-party risk management, and more.
The platform provides instant cyber risk ratings relevant to current threats, like ransomware, in order to help organizations align vendor cybersecurity practices with their own, facilitating a clearer understanding of potential threats.
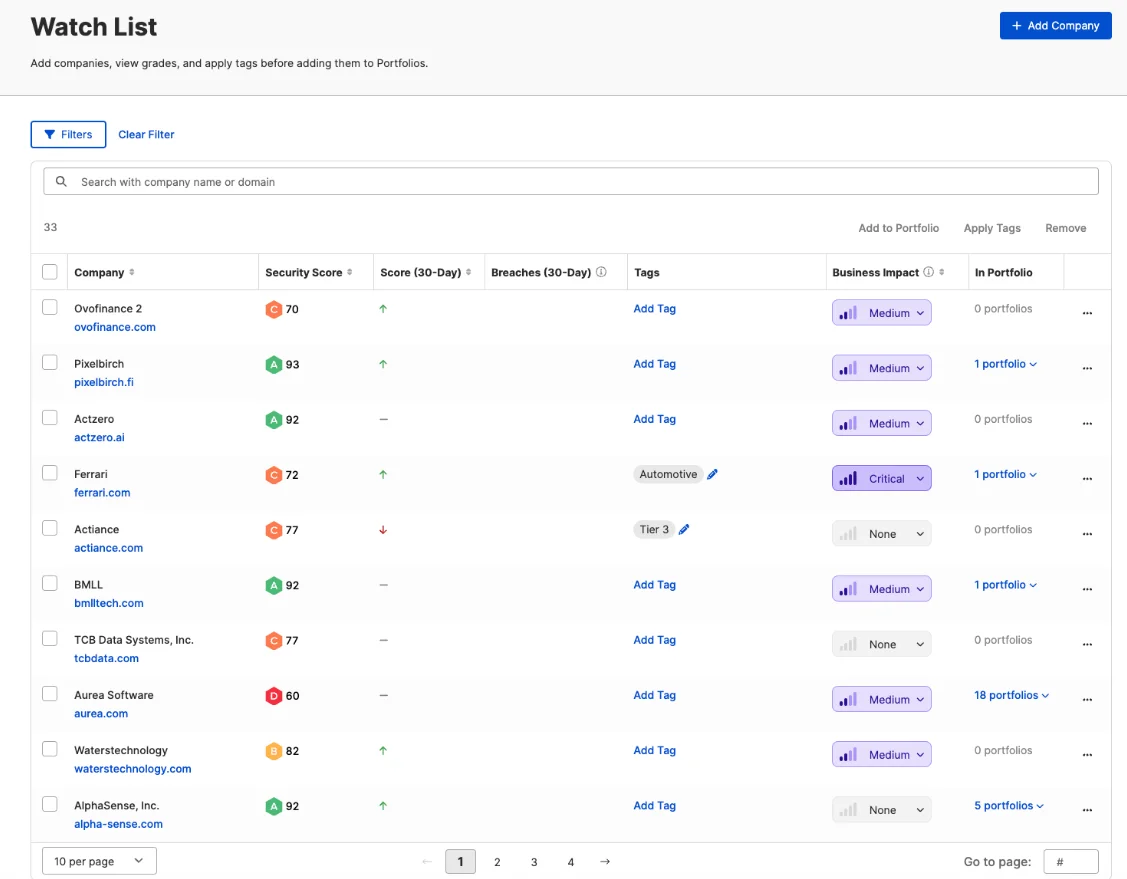
SecurityScorecard’s vendor watchlist (SecurityScorecard)
2. UpGuard
UpGuard combines third-party security ratings, security assessment questionnaires, and threat intelligence to offer a holistic view of cybersecurity risks. It is a popular choice among other supply chain monitoring platforms.
Some of its key features include active monitoring to detect third-parties’ data breaches, attack surface visibility, and security ratings for third-party providers.
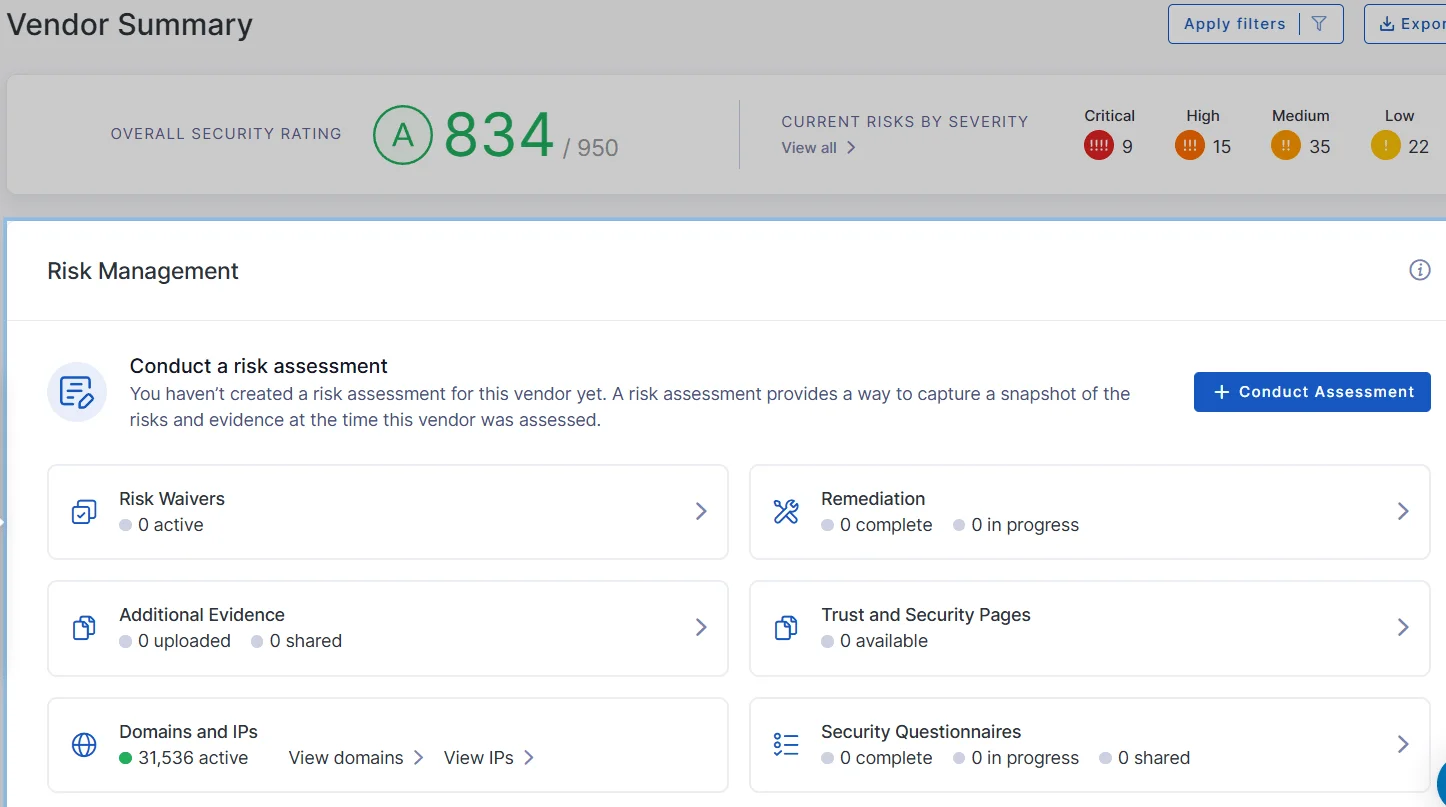
You can review information about vendors, and conduct a risk assessment through the platform (UpGuard)
3. BitSight
BitSight focuses on cyber risk management, offering solutions that help companies manage their cybersecurity performance. It is also one of the well-known supply chain monitoring platforms.
The platform supports businesses in prioritizing cybersecurity investments and building trust within their networks, covering solutions for enterprise security performance, digital supply chains, and more.
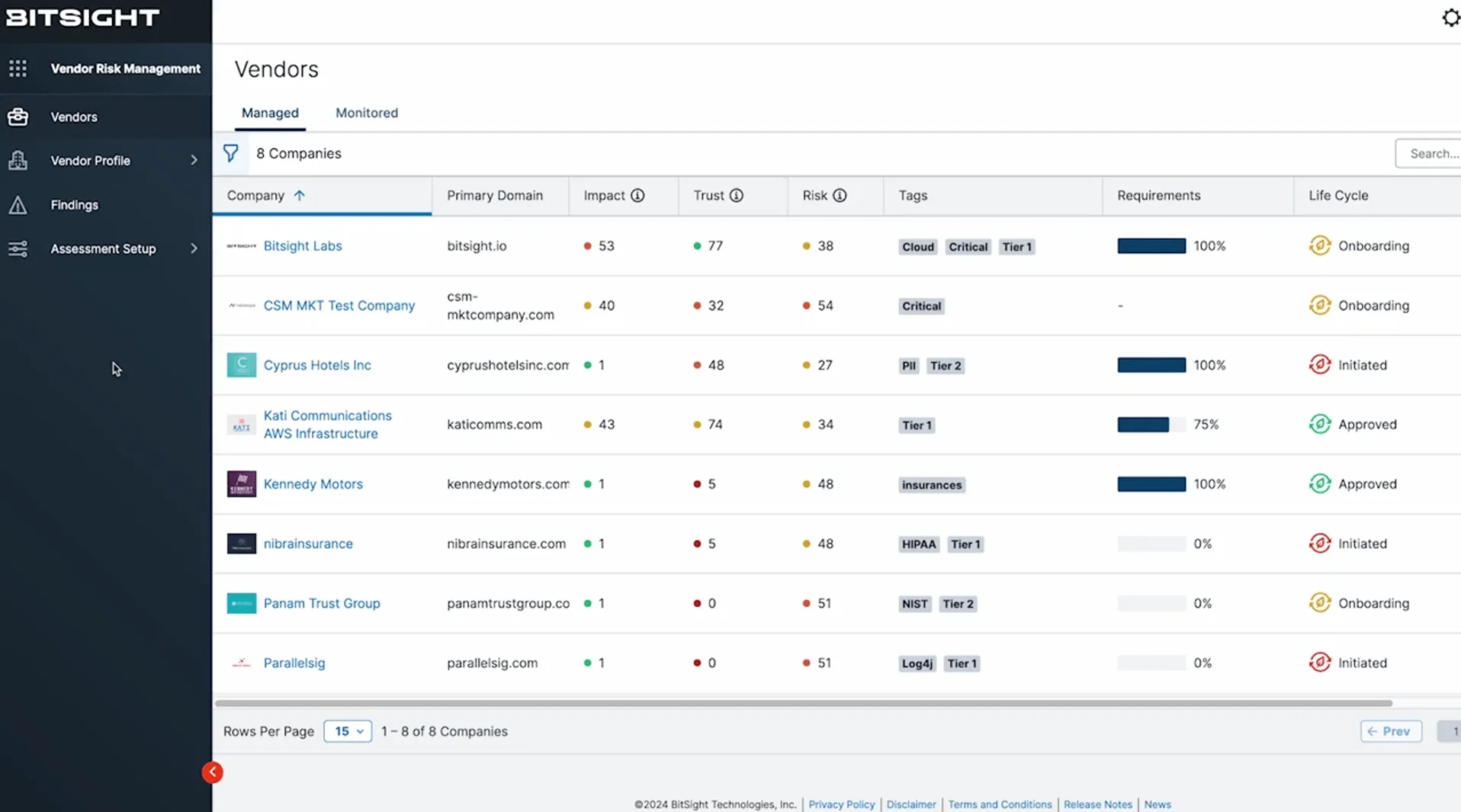
The platform’s vendor management page, with various ratings on impact, trust, and risk (BitSight)
4. Venminder
Venminder is widely used to execute third-party risk management programs. Its core offerings include tools for vendor onboarding, lifecycle management, and performing risk assessments, making it a valuable asset for managing vendor risks.
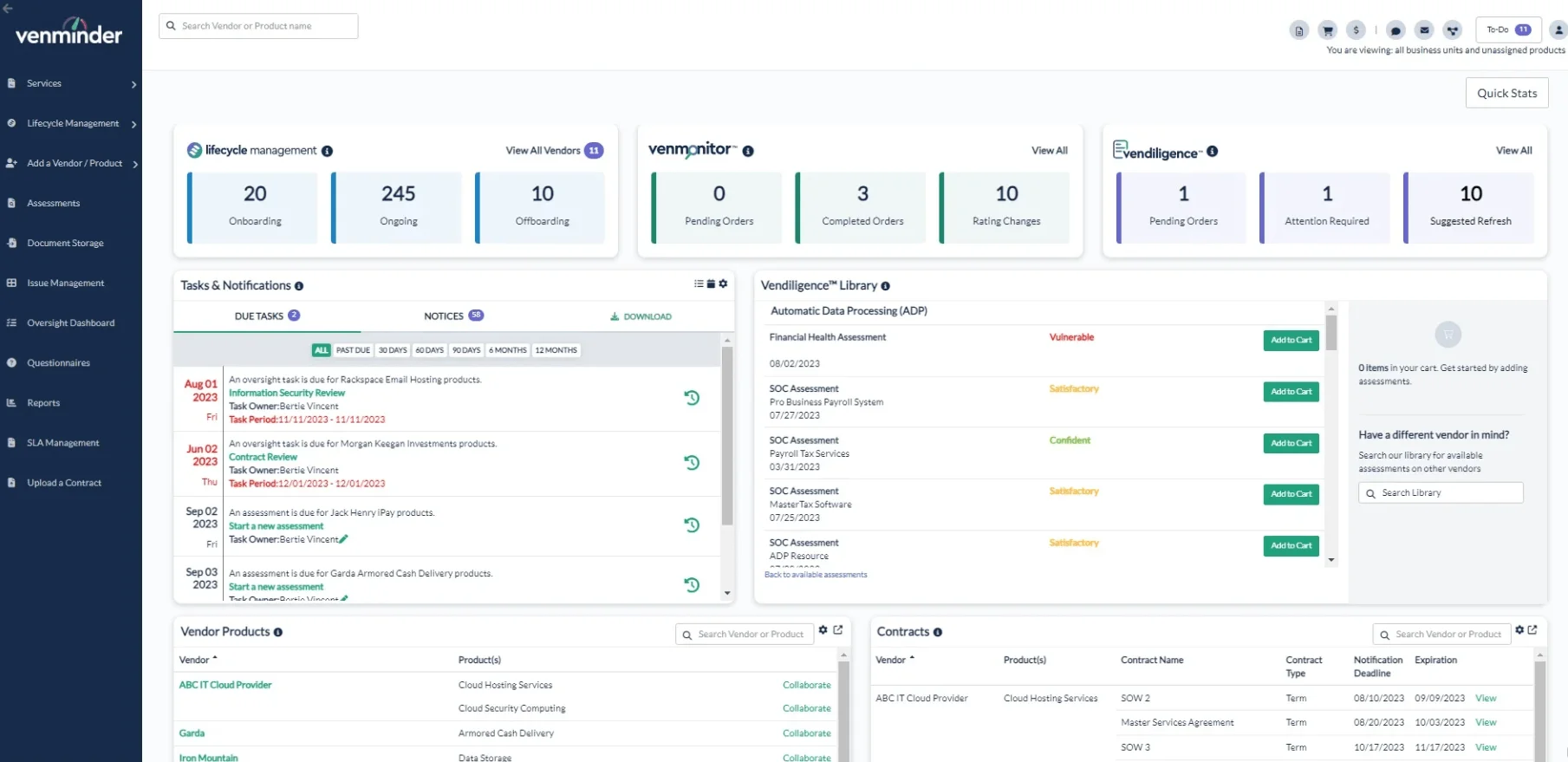
The platform offers vendor monitoring and lifecycle management capabilities (Venminder)
5. OneTrust
OneTrust helps organizations manage data responsibly while complying with privacy regulations and fostering a culture of trust.
Its features for supply chain monitoring include customizable workflows and proactive risk mitigation strategies.
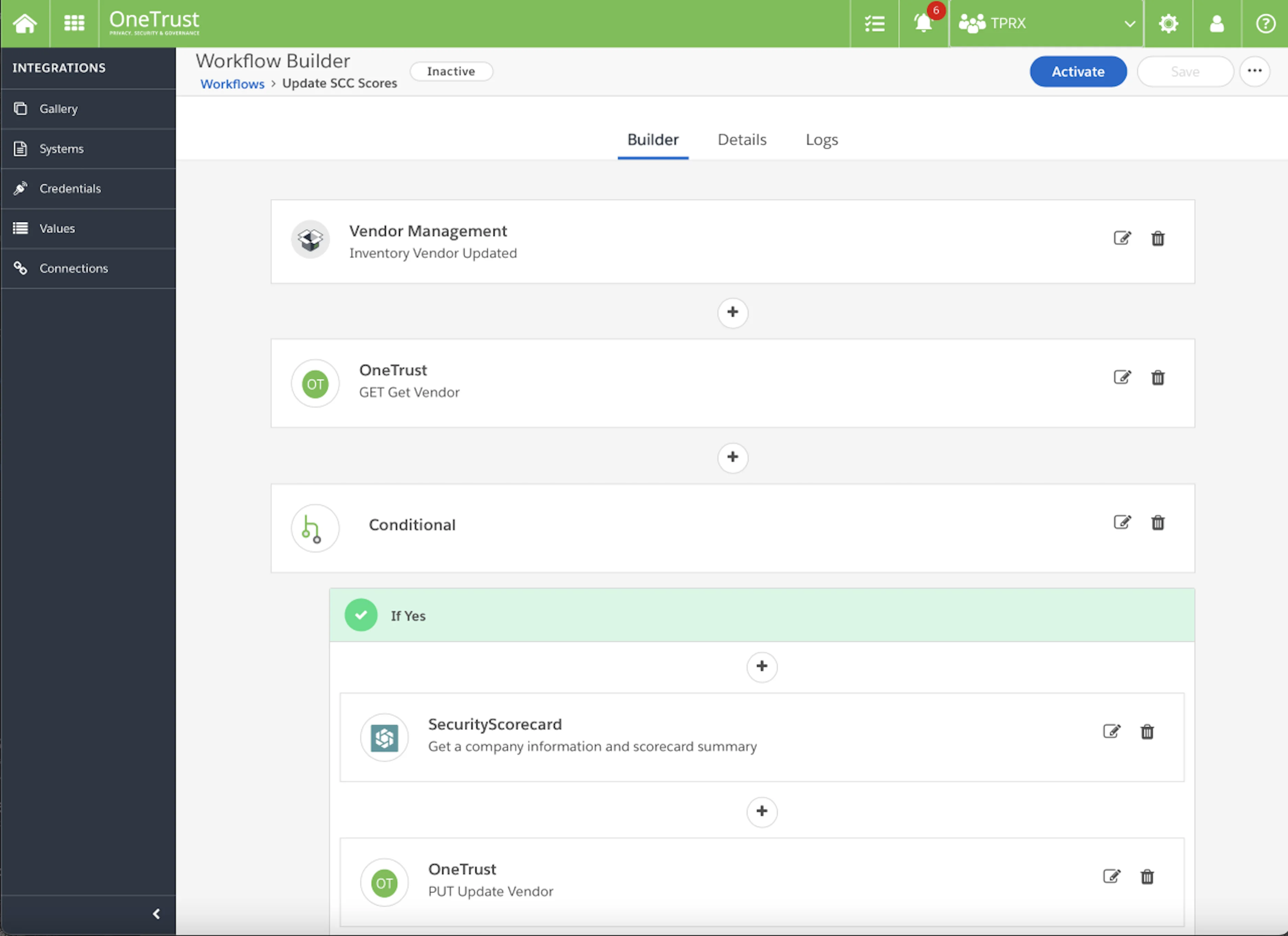
The platform features collaboration with third-parties and risk assessments (OneTrust)
6. VendorPoint
VendorPoint offers capabilities for monitoring and managing vendor-related risks. It includes features such as automated risk rating and compliance with industry regulations to simplify the management of third-party relationships.

VendorPoint is one of the TPRM solutions offered by Fortrex
7. Prevalent Third-Party Risk Management Platform (TPRM)
The Prevalent Platform automates the workflows needed to manage and remediate risks across the entire vendor lifecycle.
It is designed to enhance third-party risk management programs through continuous monitoring and automation.
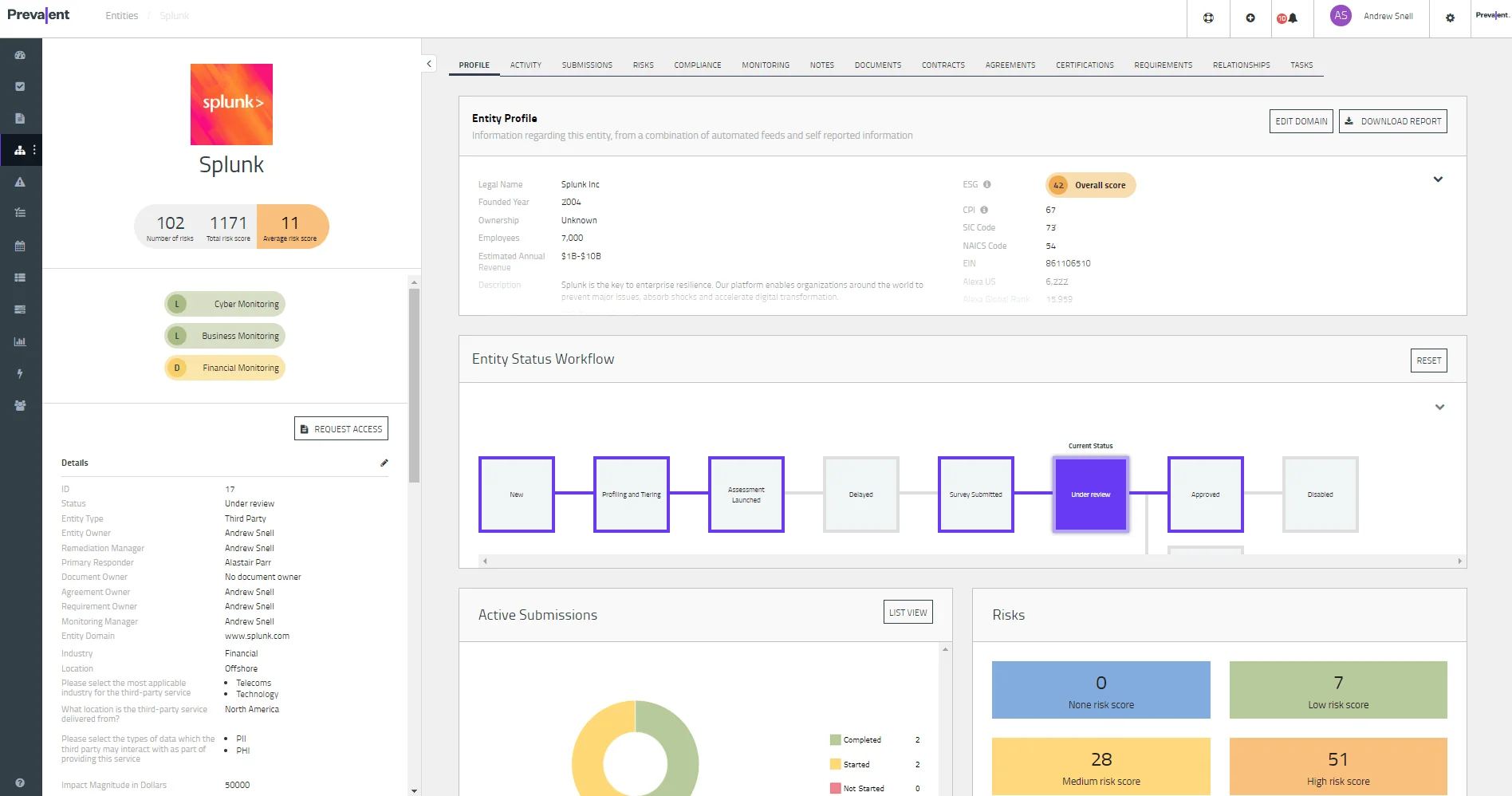
A vendor profile on Prevalent TPRM (Source)
8. ServiceNow Vendor Risk Management (VRM)
ServiceNow VRM provides a suite of tools for enhancing third-party risk monitoring and management. It offers visibility into the assessment status and integrates risk scoring, and IRM (Integrated Risk Management) portfolio to provide a holistic view of third-party risks.
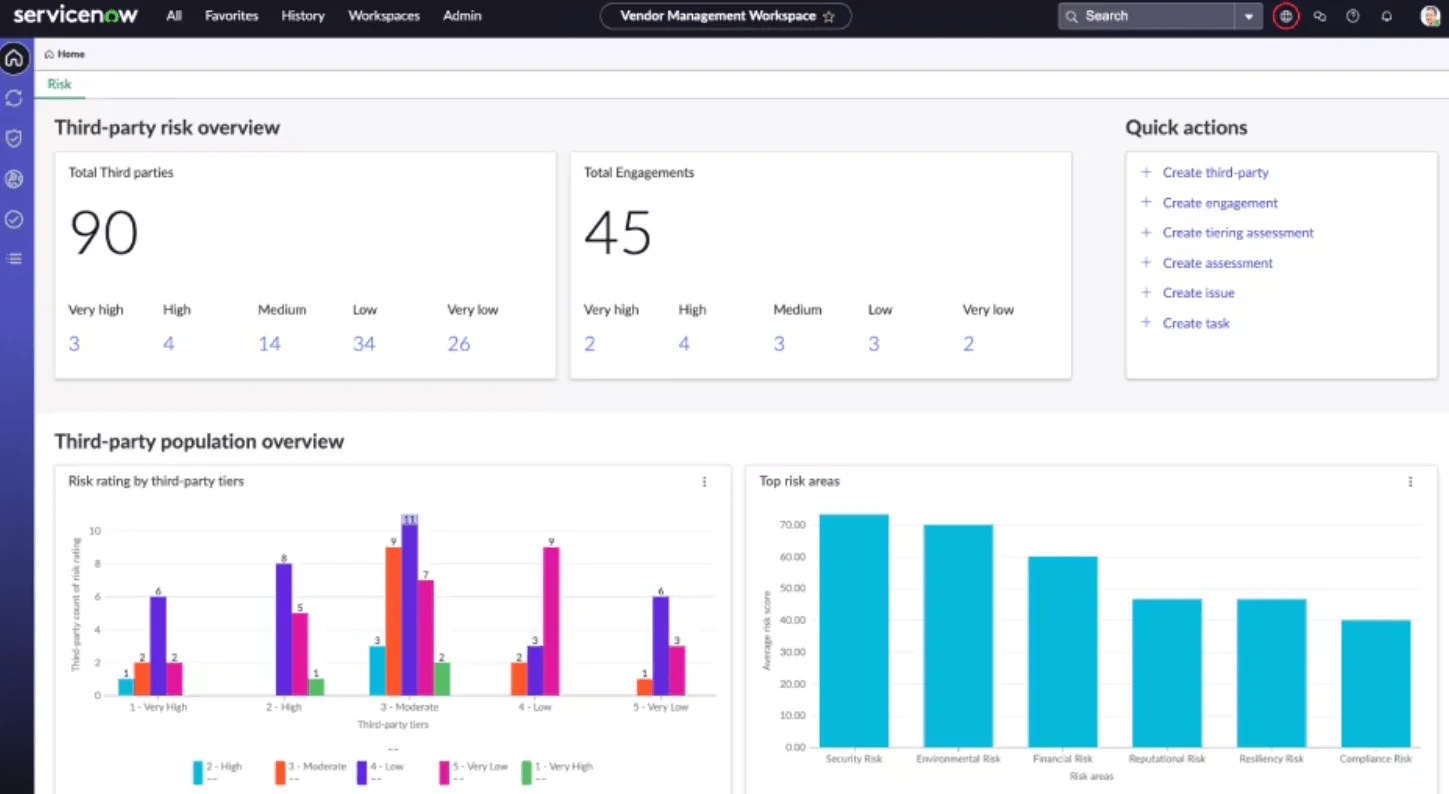
Third-party risk overview page of the platform (ServiceNow)
9. ProcessUnity Third-Party Risk Management (TPRM)
ProcessUnity offers a cloud-based solution that automates risk and compliance programs. It is offered via a Software-as-a-Service (SaaS) model, known for its user-friendly interface and minimal IT requirements, making it an efficient choice for managing third-party risks.
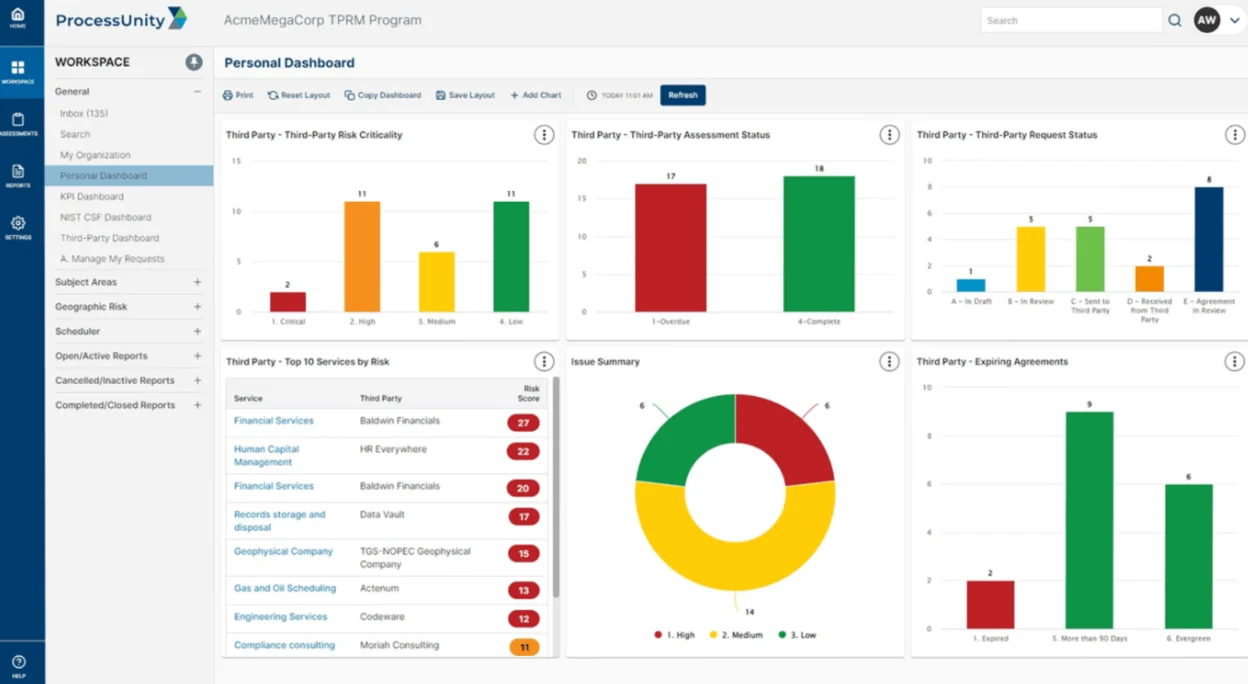
ProcessUnity dashboard
10. 3rdRisk
3rdRisk provides a platform for third-party and vendor risk management, internal control, and compliance management.
It emphasizes a personalized and innovative approach, offering a user-friendly platform that adapts to the evolving needs of risk, audit, and compliance professionals.
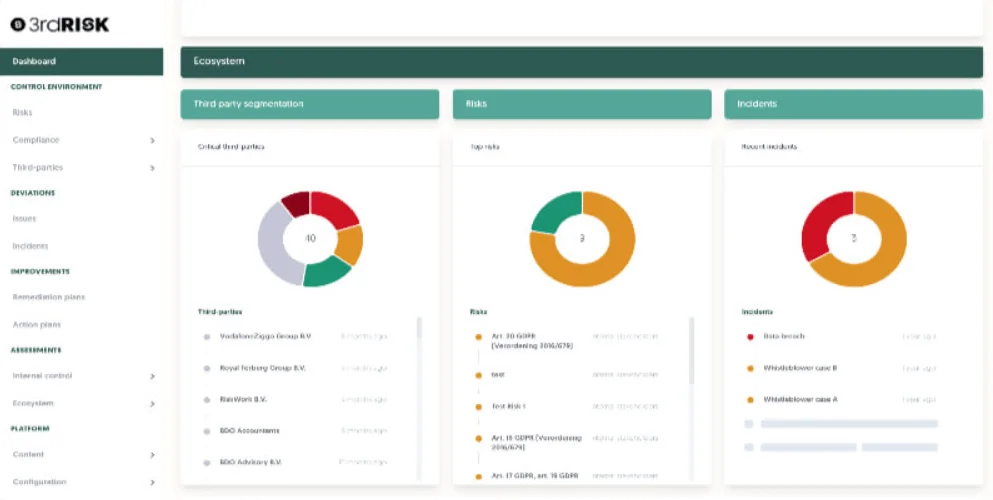
3rdRisk dashboard
These platforms represent some of the most effective tools available for organizations looking to safeguard their supply chains against third-party risks, strengthen their operational integrity, and maintain trust with their partners and customers.
Bonus: Monitor the Cyber Posture of 3rd Parties with SOCRadar
As the market becomes increasingly intertwined, SOCRadar continues to deliver critical capabilities across several fronts, including supply chain security.
The platform brings several benefits that facilitate immediate response to security incidents and aid in decision-making, such as alerts, reporting, and a user-friendly interface that simplifies the complexity of cybersecurity management.
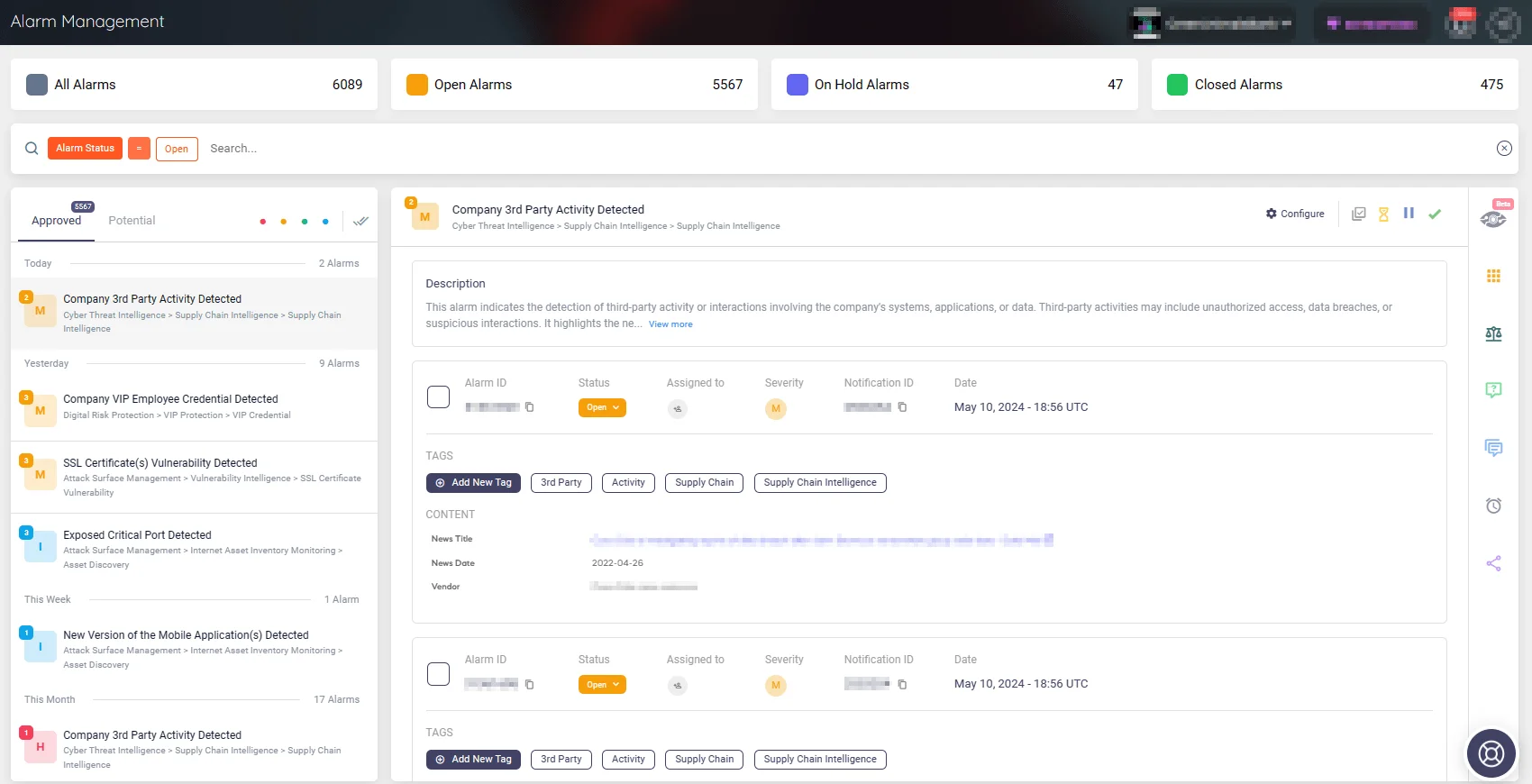
Alert: 3rd Party Activity Detected (SOCRadar Alarm Management)
While the SOCRadar XTI platform’s key features cover Vulnerability Intelligence, Attack Surface Management, Threat Actor Tracking, and Dark Web Monitoring, it has also recently introduced its 3rd party risk management services under a separate category: Supply Chain Intelligence.
SOCRadar’s Supply Chain Intelligence module enhances third-party risk management by enabling continuous and advanced vendor assessment. The platform allows for the continuous monitoring of third-party vendors’ security practices, ensuring they meet the organization’s standards.
The module provides a dynamic and detailed analytics dashboard that offers real-time updates and comprehensive reporting. This functionality enables organizations to stay ahead of emerging threats and vulnerabilities targeting their supply chains.
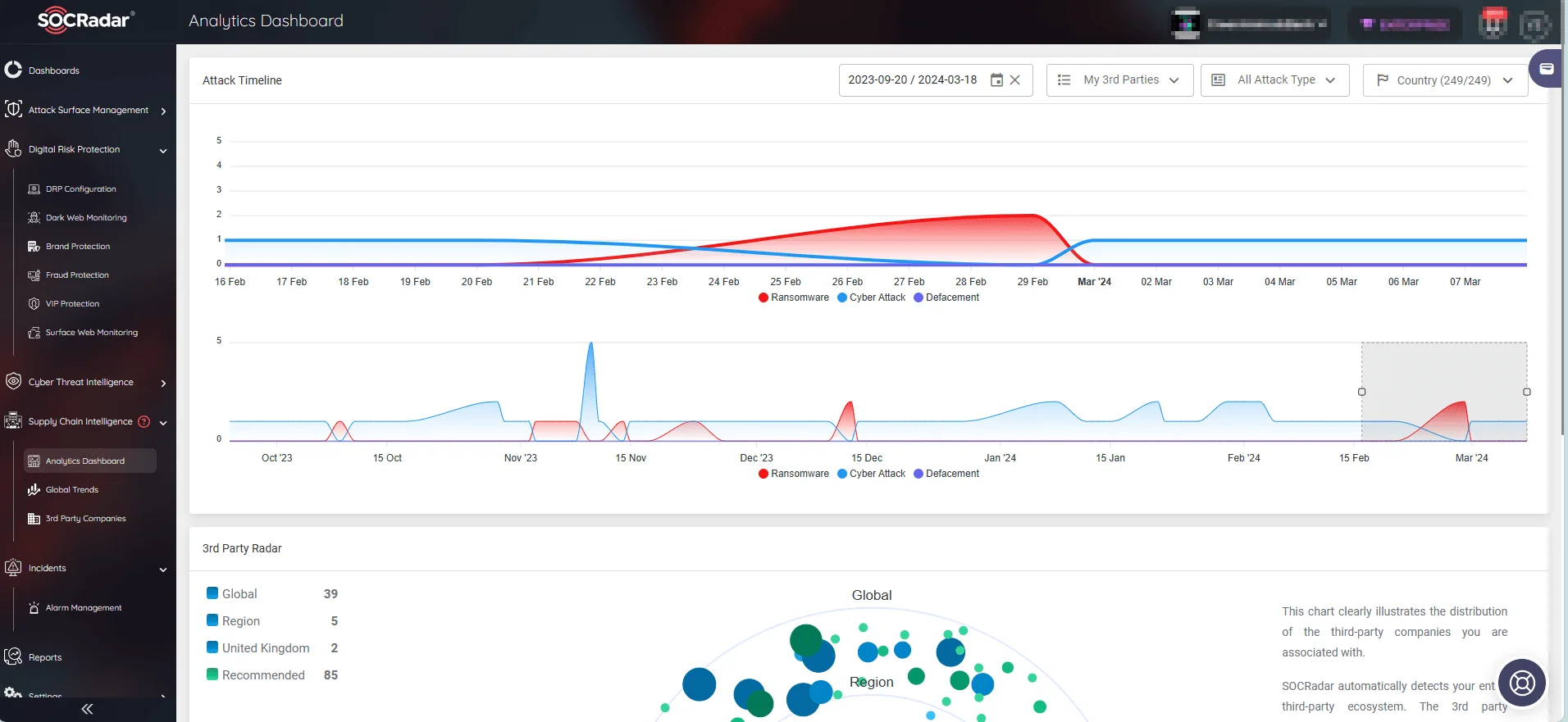
Security teams can use the analytics dashboard to monitor their company’s third-party distribution and view a timeline of previous cyber attacks involving third parties. (SOCRadar’s Supply Chain Intelligence)
By automating the detection and mapping of third-party environments, SOCRadar allows for an extensive overview of potential security events, providing organizations with the tools necessary to effectively address threats originating from the dark web, including ransomware attacks and data breaches.
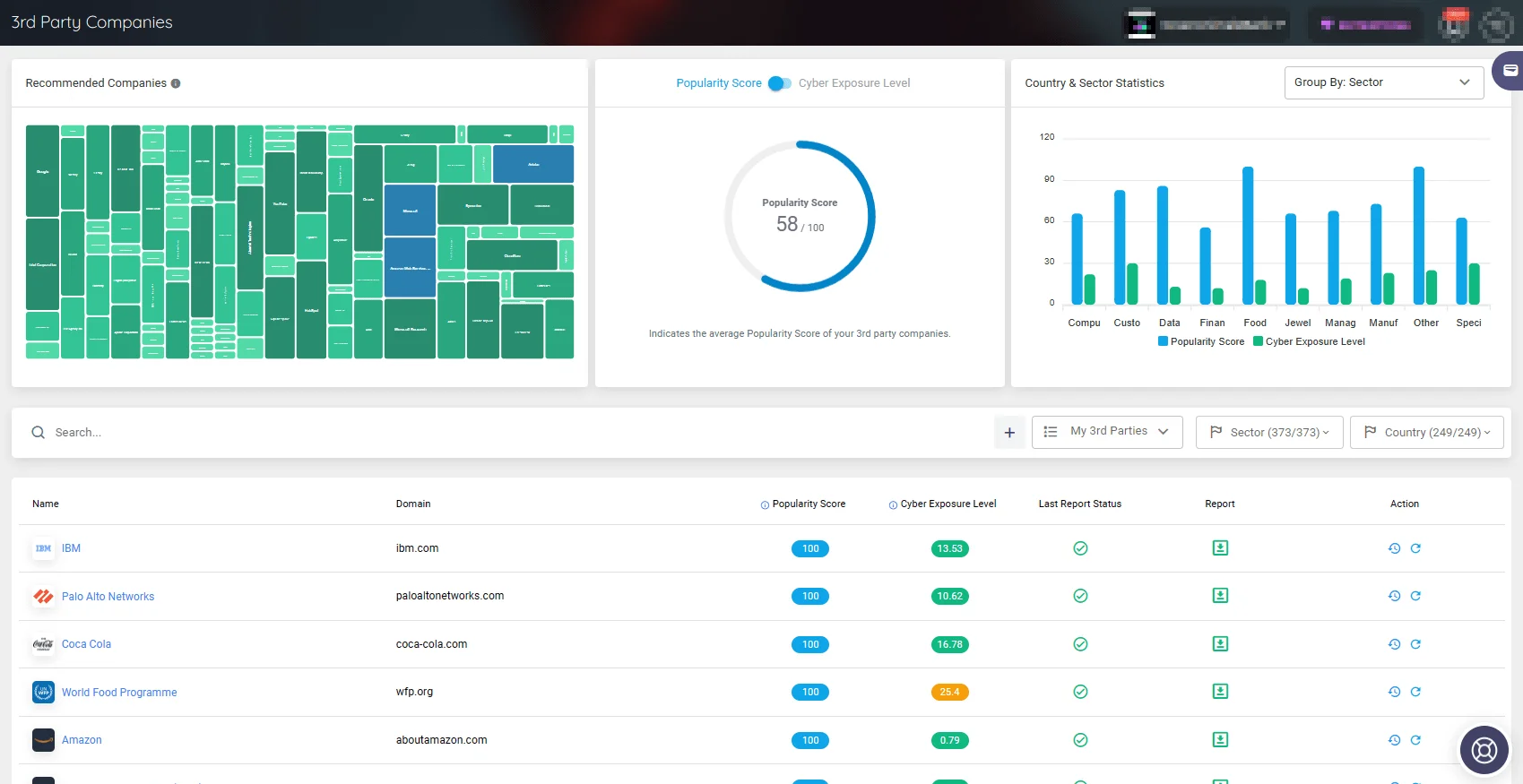
View the third-party companies associated with your business; track popular vendors and their popularity, as well as cyber exposure levels. (SOCRadar’s Supply Chain Intelligence)
With the ability to monitor digital activities across an expansive network of entities and monitor trends over various countries and industries, SOCRadar empowers organizations to proactively manage and respond to risks.
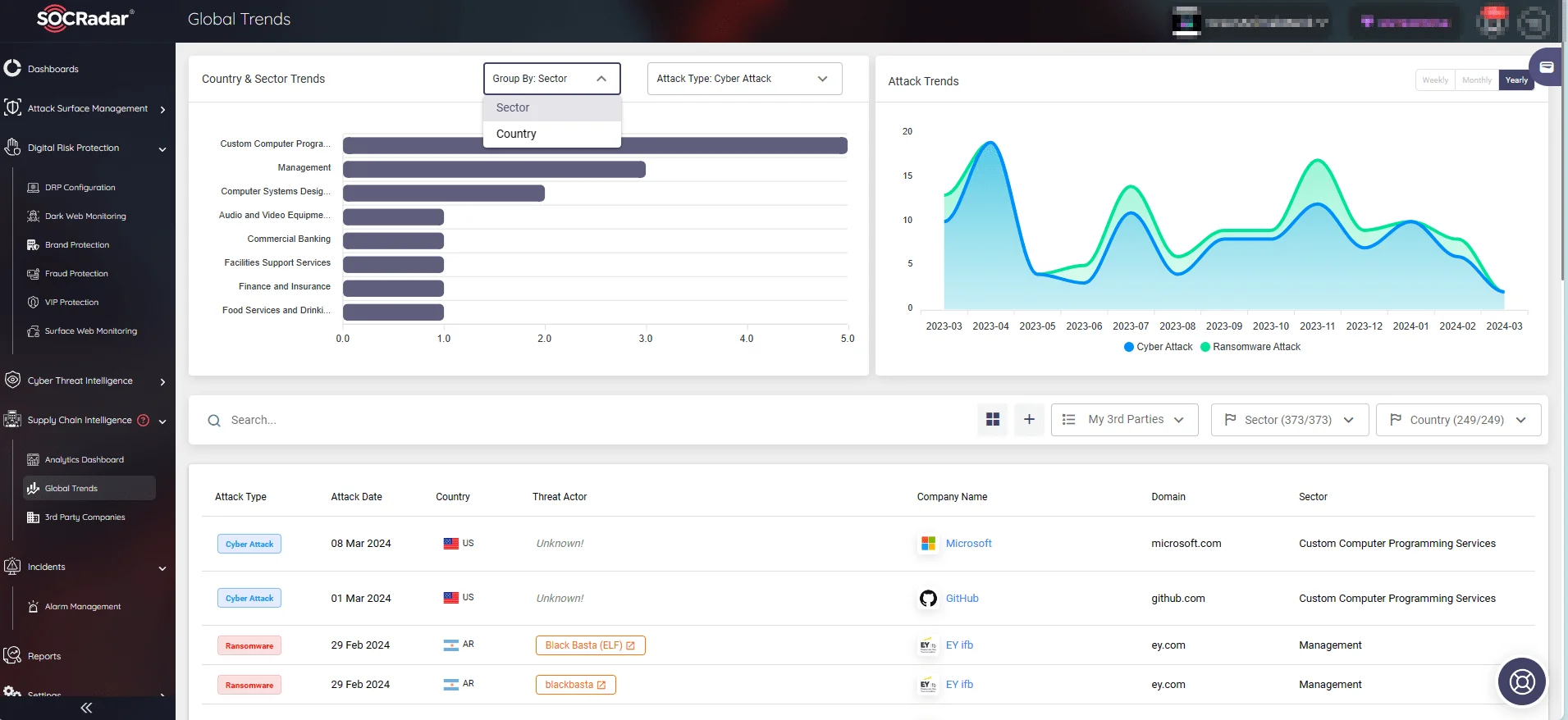
Stay current on global trends, whether by country or industry. Follow the latest cyber attacks on companies and access detailed information about supply chain incidents. (SOCRadar’s Supply Chain Intelligence)
Conclusion
As we conclude our exploration of the top supply chain monitoring platforms, let’s remind again that nearly every organization is linked to a complex web of third-party vendors. One weakness harbored in the systems of only one organization could lead to data breaches, operational disruptions, and significant financial losses for many other businesses.
The supply chain monitoring platforms discussed here provide crucial capabilities that help organizations manage and mitigate these risks. They offer a range of benefits, from reducing the likelihood of security incidents to ensuring compliance with regulatory standards, enhancing visibility into third-party vulnerabilities, and streamlining resource management.
Meanwhile, SOCRadar equips organizations with comprehensive tools to monitor and manage their entire cyber posture, including risks related to their supply chain, by monitoring the security status of third-party vendors. Its features, such as real-time alerts, vulnerability intelligence, dark web monitoring, and Supply Chain Intelligence, aid in proactive risk management.

SOCRadar XTI is an all-in-one Threat Intelligence platform. It features multiple modules tailored to protect your organization’s digital presence.
Secure your supply chain today; explore the many capabilities of the SOCRadar platform. Start your Free Trial now to see how it can enhance your organization’s security.




































