
Underground Fully UnDetectable (FUD) Crypter Market
The rapidly evolving threats in the field of cybersecurity are being met with sophisticated methods such as “FUD” (Fully UnDetectable) crypters, which are advanced crypter tools used by cybercriminals. This sophisticated software renders malicious code undetectable, allowing attackers to infiltrate secretly.
In this research paper, we will examine in detail some of the FUD markets operating in the underworld of the deep web and the functioning of fully undetectable crypters offered in these markets, and assess the impact of this cybersecurity threat.
There is a thriving market to meet the FUD Crypter needs of cybercriminals. In this market, FUD Crypter developers offer software that can be customized according to the needs of cybercriminals.Telegram channels in particular have become a serious platform for cybercriminal activities and FUD Crypter services are offered also through forums. Cybercriminals communicate with each other on these forums to exchange information about FUD Crypter services and become customers of FUD Crypter vendors.
Based on recent news reports, it is important to focus on FUD crypters used to circumvent or disable cybersecurity products. For example, “Terminator[.]exe” and “AuKill Malware” have the ability to neutralize antivirus and EDR (Endpoint Detection and Response) systems. Such tools are an important guideline for our research because they allow us to understand the vulnerabilities of traditional security measures and how cybercriminals use privacy-oriented methods to target users.
If you would like to learn more about “Terminator[.]exe” and “AuKill Malware“, please visit the links.
Underground Forums & Telegram Channels
Underground forums are digital communities where cybercriminals come together in anonymity. In these forums, FUD Crypter vendors and users come together to communicate and share information about FUD Crypter services. In this way, it is possible for cybercriminals to find suitable solutions to meet their FUD Crypter needs.
Telegram channels are also a widely used communication tool among cybercriminals. These channels are platforms for cybercrime-related information sharing and sales through private chats, groups and channels. FUD Crypter vendors reach customers by promoting their services on Telegram channels. These channels share information about FUD Crypters, such as detailed specifications, videos, screenshots, and prices.
During our research process, we accessed different underground forums and Telegram channels and carefully analyzed the communications on these platforms. In particular, negotiation conversations with FUD Crypter sellers and customer feedback provided us with important clues about how these platforms operate. We also conducted a detailed analysis on factors such as the features of FUD Crypters offered on these platforms, pricing policies, and customer satisfaction.
Through this research, we gained a better understanding of how underground forums and Telegram channels play an important role in the FUD Crypter market and how cybercriminals communicate through these platforms. We also gained extensive knowledge about the variety of FUD Crypters offered on these platforms and their ability to be customized according to customer demands.
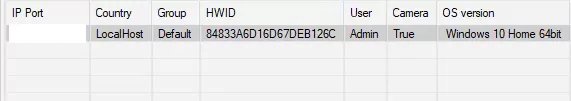
As the screenshot clearly shows, the user named “SpyBoy” creates a Cobalt Strike beacon and provides information on how to circumvent antivirus and EDR (Endpoint Detection and Response) solutions. It is possible to identify this user as the vendor of the EDR killer process called “Terminator[.]exe” mentioned at the beginning of our research paper.
We searched Telegram channels for a FUD Crypter that we could use for testing, and found that pricing was quite erratic with many threat actors. For example, while threat actors selling certain categories of malware can provide average price statistics for monthly or yearly usage, it is not possible to determine such statistics for the FUD Crypter.
Throughout our research process, we were able to identify a number of threat actors and contacted each one individually to inquire about pricing and testing opportunities. We chose to target threat actors who provided constant updates and information. In our discussions with each threat actors, we tried to obtain more details about FUD Crypter services and purchasing options, which will be discussed in more detail in the following sections.
First FUD Crypter
The information we have obtained about Crypter, which offers a $300 monthly usage service, is detailed in the following articles and screenshots.
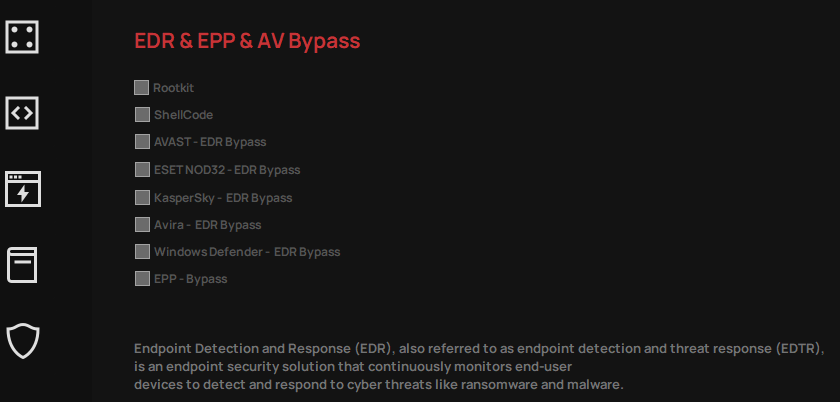
- Rootkit
- ShellCode
- AVAST – EDR Bypass
- ESET NOD32 – EDR Bypass
- Kaspersky – EDR Bypass
- Avira – EDR Bypass
- Windows Defender – EDR Bypass
- EPP – Bypass
It is supported by constant updates and tries to gain the trust of potential buyers by sharing video content with each new update. This is a logical approach and important for FUD Crypter to serve its purpose, given that the signatures of the files will be detected by many security firms within a few days. However, as cybersecurity researchers, we always pay attention to the details on these points. It is important to verify that updates have actually been made and to focus on where updates have been made. We will go through the details of each update. In his Telegram channel, the seller shares videos and results from several malware testing addresses.

In the video content, a virtual machine with Windows 10 operating system was created and Kaspersky Antivirus software was installed. The virtual machine was configured with full protection and FUD (Fully Undetectable) was performed using the DcRAT malware as an example. Then, the FUD DcRAT sample file was uploaded to the virtual machine and executed. As a result, the malware was able to successfully establish a connection and no alarms were generated by Kaspersky. Among the FUD Crypters we scrutinized, the first Crypter was the most remarkable in terms of its shares and capabilities. In our subsequent review, we went through a lot of negotiations with the seller of the second Crypter we obtained, but he indicated that he would not be offering anything for testing and suggested that we watch videos on his Telegram channel in the current situation. However, there were a few points that caught our attention during the conversations. When we asked the vendors questions about EDR, we could tell from their answers that there was a serious lack of knowledge.
Second FUD Crypter
After we started the conversation, the vendor said he would make a video for testing and sent us a video showing Crypter in action. The vendor sent us a video as a PoC (Proof-of-Concept) and said he would post it on his YouTube channel.
While we would like to know about average prices, free testing is not usually offered and quotes are usually around $100 with a time limit for testing. However, after a successful negotiation with the first Crypter vendor, we were able to obtain a FUD Crypter with a 12-hour time limit for testing.
Third FUD Crypter
In our conversation with the third Crypter vendor, we learned that testing is not offered. Unlike other FUD Crypter vendors, this vendor has its own website and GitHub profile. It also differs from other similar vendors with its $100/month pricing policy. Details on pricing are as follows:
| Crypter | Price | Duration of use |
| First Crypter | 100$ | 12 Hour |
| Second Crypter | 30$ | 1 Week |
| Third Crypter | 100$ | 1 Month |
It contains the same content on its website and GitHub address, and we can say that the vendor keeps it up to date for the third FUD Crypter by constantly updating it. In Underground, we know that sellers make transactions such as buying and selling over cryptocurrencies. After this stage, we will share the results of our research on the movements in and out of the crypto wallets of the sellers.
Blockchain Transactions Analysis
As part of our research, we decided to analyze the transactions for the LTC (LiteCoin) address used by the first Crypter seller and the BTC (Bitcoin) address used by the third Crypter seller. The second Crypter seller stopped responding to our messages after a while, so we were unable to find any addresses. For our research, we used Blockchain.com and Litecoin explorer, as well as a data analysis and exploration tool called Maltego. Maltego is a tool that can visualize information from different data sources, understand relationships and follow connections, helping us understand complex network structures.
For First Crypter, the coin transferred to the account is not kept in a single wallet, but is transmitted to different addresses. There are 52 transfer transactions in total and it is observed that 26 transactions were entered. There were 26 transaction entries and 26 transaction exits, and the transactions entered into the account were transferred to different addresses. You can examine the details at Litecoin-explorer, and you can also view the results of our research in the image below. In total, 14.82376836 LTC (1382,76 USD) was entered and it was observed that the same amount was transferred to different addresses. The table below shows the results for the amounts entered in 2023.
When we looked at the addresses shared on the third seller’s website, we were able to make direct inquiries without requesting account information.
In the research we conducted through Maltego on the BTC address, we examined the transactions made to the seller’s account. We observed that money was transferred to two different addresses through these transactions. This reveals that the seller does not keep money in a single account and transfers between different addresses.
As you can see from the diagram in the image, there are 9 logins and they transfer the money in the main wallet to two different addresses. See more detailed results on Blockchain.com
You can view it by visiting our website. In total, 0.06161425 BTC (1866,79 USD) was debited and the same amount was debited from the account.
FUD Test & Analyze
Through our research and discussions with vendors, we came to a successful conclusion with the first FUD Crypter, which we were able to test for a limited period of time. The vendor provided us with an installation file called “Build[.]exe” for testing and stated that Windows Firewall must be turned off during the installation and program run.
Following these steps, we started the testing process with QuasarRAT, an open-source RAT, by installing the “Build[.]exe” file in the virtual machine environment. Below are the images of Crypter.
In the screenshot of the “Options Encryption” section, we observed that there are many options and that Windows legal processes targeted for Process Injection can be listed. We also noticed that we have the option to use this Crypter tool as a Downloader. While the presence of the “Anti-Sandbox” and “Anti-VMWare-VBox” options is interesting, we found that they were only available as “Check-Box” in the vendor’s videos and in the virtual machine environment we used for testing. However, when we activated these options during the analysis and ran the malware on a Windows 10 virtual machine, we did not encounter any problems and were able to analyze the malware successfully. In this case, we observed that the Anti-Sandbox and Anti-VMWare-VBox features did not work.
As seen in Crypter, there are bypass options for several security products. As an example we have examined the Avast related function in Crypter. In the screenshot below you can find the list of functions for the checkbox sections.
The general antivirus operating logic today uses behavioral analysis and updated malware signature bases. Therefore, newly created FUD Malware will be detected by many security vendors after a few days. For these reasons, security vendors have to keep their applications up to date to avoid problems with their long-term users.
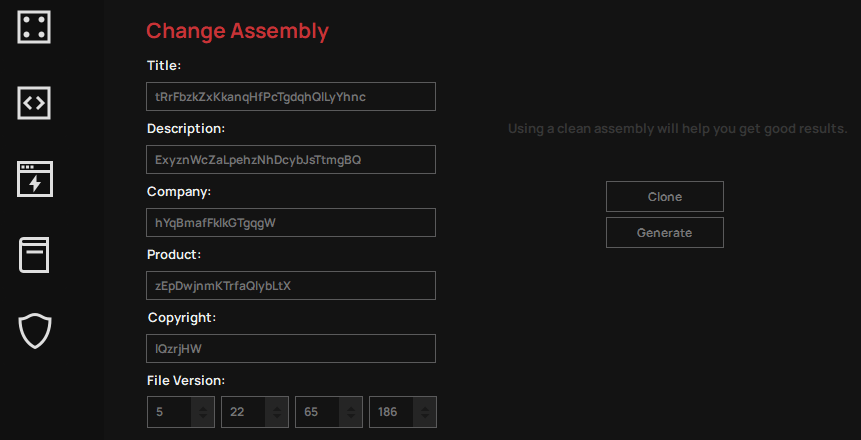
Finally, changes can also be made to the checkbox in the “Change Assembly” section. The interfaces for Crypter are as above and we tested QuasarRAT, the open-source RAT we created in these interfaces. The reason we chose QuasarRAT is that it is among the most used RATs by APT groups in our previous research titled “Open-Source RATs Leveraged By APT Groups“.
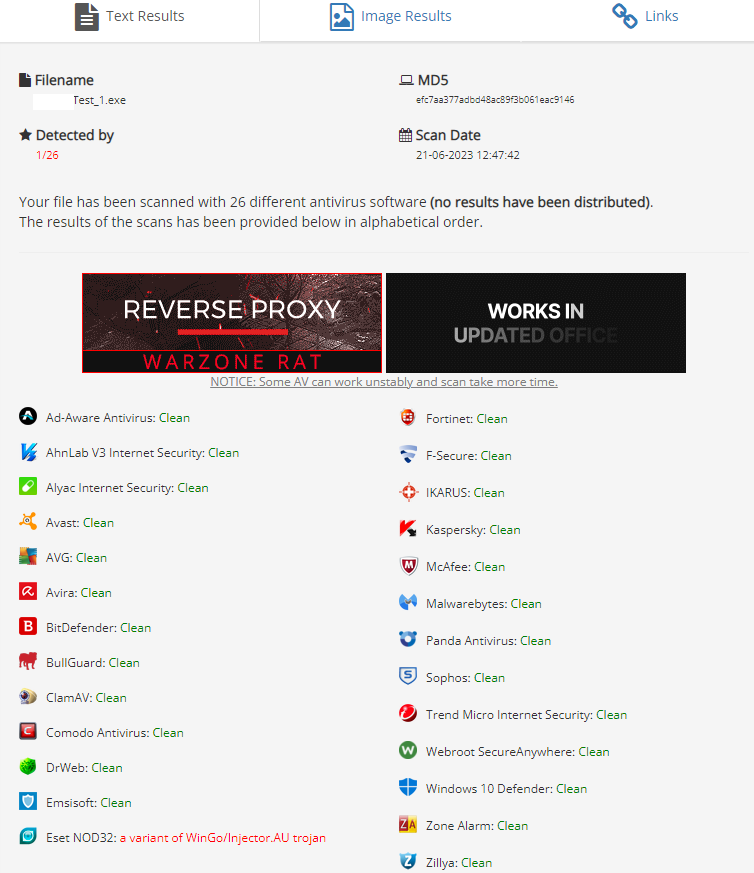
Our test file submitted to Antiscan.me received only ESED NOD32 malware matches among 26 security products.
After the signature-based query, we dynamically tested on our virtual machine by installing Avast and Kaspersky antivirus applications, which have free versions on our virtual machine. Although there was no capture by Avast Antivirus, we started to receive warning notifications for taking necessary precautions by Kaspersky Antivirus.
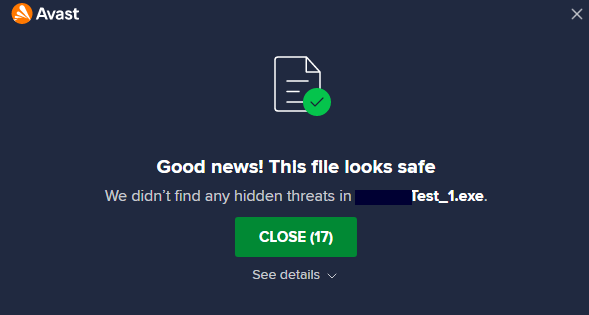
Our crypted file was not caught by Avast Antivirus free version during execution. This is the result for the Avast free version, but not for the Kaspersky free version. The Kaspersky free version reports both files as malicious and gives us warnings to delete them.
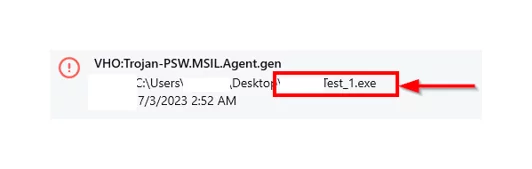
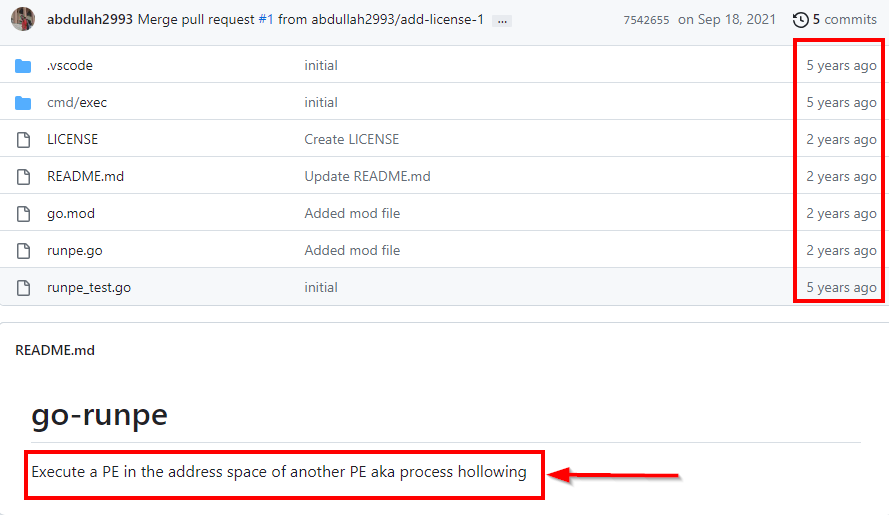
Furthermore, when Real-Time Protection was enabled, the Windows Firewall experienced a limitation in capturing data. As we further investigated the source code, we discovered two notable outcomes. One of the noteworthy findings was the presence of a GitHub address within the string references.
When we examine the profile and the “go-runpe” repo used, we can understand that he tried to use the Process Hollowing technique.
How SOCRadar is Responding
This research has clearly revealed the methods applied as a result of the three Crypters we sampled as a result of our research on the FUD Crypter market. As a result of our research, it was understood that the Bypass methods were the common for the Crypters we examined. We were able to observe that new methods were not used as in “Terminator[.]exe”. As SOCRadar Threat Research team, we continue conducting researches in order to increase our security awareness and take more effective measures against cybercrimes in the ever-changing threat environment.
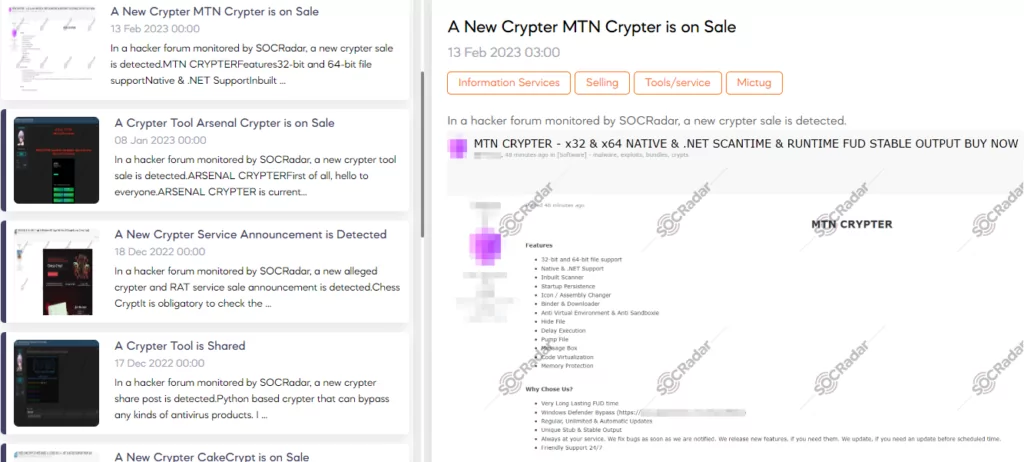
Thanks to the monitoring service we provide on underground, we are able to detect such activities. We inform our customers about these detections and make it easier for them to track them through our platform. Our goal is to ensure the security of our customers and enable them to act in an informed manner against potential threats. In this way, our customers can feel safer and minimize risks by taking the necessary precautions.
Conclusion
This security investigation led us to a remarkable conclusion after testing and analyzing the Underground FUD Crypter marketplace. Our analysis revealed that the FUD Crypters were not built with original efforts, but instead utilized pieces of code from open source platforms such as Github that could be used for bypassing.
The findings draw attention to the issues of authenticity and reliability in the FUD Crypter market, and it appears that developers have adopted a less labor-intensive approach by leveraging existing source code. In a world where technology is constantly evolving, it is important to continuously conduct similar studies and provide constant updates to understand and prevent threats.





































