
Unpatched RCE Vulnerability in Zimbra Actively Exploited
Threat actors actively exploit Zimbra Collaboration Suite in the wild due to an unpatched vulnerability. Tracked as CVE-2022-41352 (CVSS score: 9.8), the vulnerability allows remote code execution.
The vulnerability is initiated when Amavis, Zimbra’s antivirus engine, employs the cpio method to scan received malicious emails. It affects Zimbra’s Linux distributions that enable the vulnerable cpio method.
Affected Linux distributions are listed as:
- Oracle Linux 8
- Red Hat Enterprise Linux 8
- Rocky Linux 8
- CentOS 8

How Is It Exploited?
Amavis scans the attacker-sent email that contains .cpio, .tar, or .rpm for malware and extracts files using the cpio method. This will enable the attacker to write to any path on the filesystem and possibly insert shell to acquire remote code execution.
Steps followed in one incident:
- The attacker sends malicious attachments via email.
- Amavis scans and extracts the file into the target folder (/opt/zimbra/jetty/webapps/zimbra/public) using the cpio loophole.
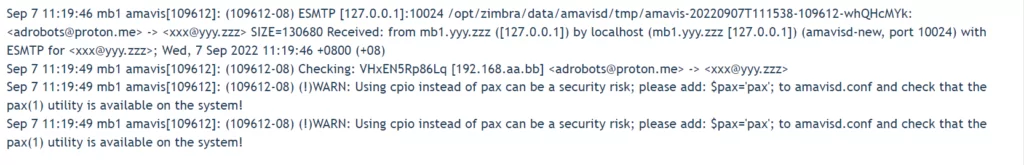
3. The attacker uses the path to access webshell and executes “zmprov gdpak” to create preauth for logins.
4. To leave no trace, they log into the [email protected] account and delete the malicious file they sent for initial access.
It is claimed that in this incident, the attacker was able to upload jsp files into the Web Client.
900 Zimbra Servers Affected
According to Kaspersky, several threat actors and APT groups actively exploited the vulnerability soon after Zimbra made it public, and at least 876 servers were already compromised before the announcement.
44 Zimbra Collaboration Suite servers in Turkey and India were affected in the first wave of attacks in September. Threat actors stepped up their attacks as soon as the vulnerability was made public and launched widespread attacks.
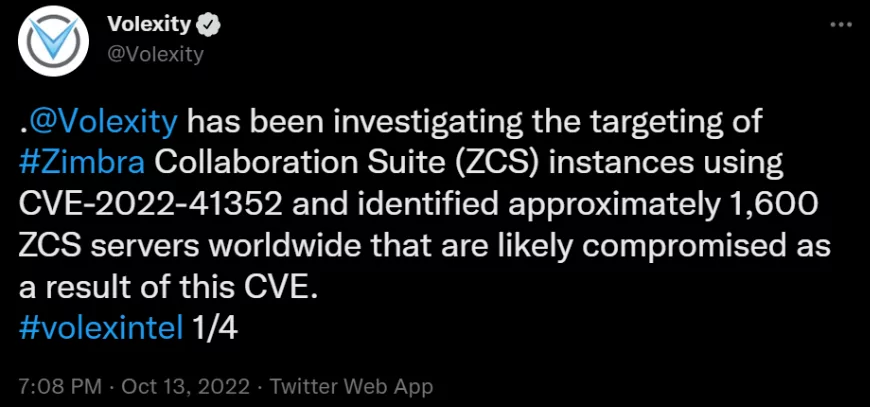
Volexity also notes that about 1,600 servers may have been compromised worldwide.
Mitigation
Pax utility is Amavis’ preferred method before cpio, and is not vulnerable. If it is not already installed, installing the pax archive utility for used Zimbra services and doing a restart will mitigate the issue. Check out Zimbra’s blog to learn how to install the pax utility on affected Linux instances.
Zimbra has released ZCS version 9.0.0 P27 to completely replace the vulnerable component. Applying the update is critically advised.



































