
Critical Veeam Vulnerability (CVE-2025-23114) Exposes Backup Servers to Remote Code Execution
On February 4, 2025, a critical security vulnerability identified as CVE-2025-23114 was disclosed, affecting multiple Veeam backup products. This vulnerability, with a CVSS score of 9.0, resides in the Veeam Updater component and allows attackers to perform Man-in-the-Middle (MitM) attacks, potentially leading to remote code execution with root-level permissions on affected servers.
Quick Summary:
- CVE-2025-23114: Critical Veeam vulnerability (CVSS 9.0)
- Impact: Enables remote code execution via Man-in-the-Middle (MitM) attacks
- Affected Products: Multiple Veeam backup solutions
- Risk: Potential full system compromise
- Solution: Veeam has released urgent security patches
- Action Required: Update immediately to mitigate threats
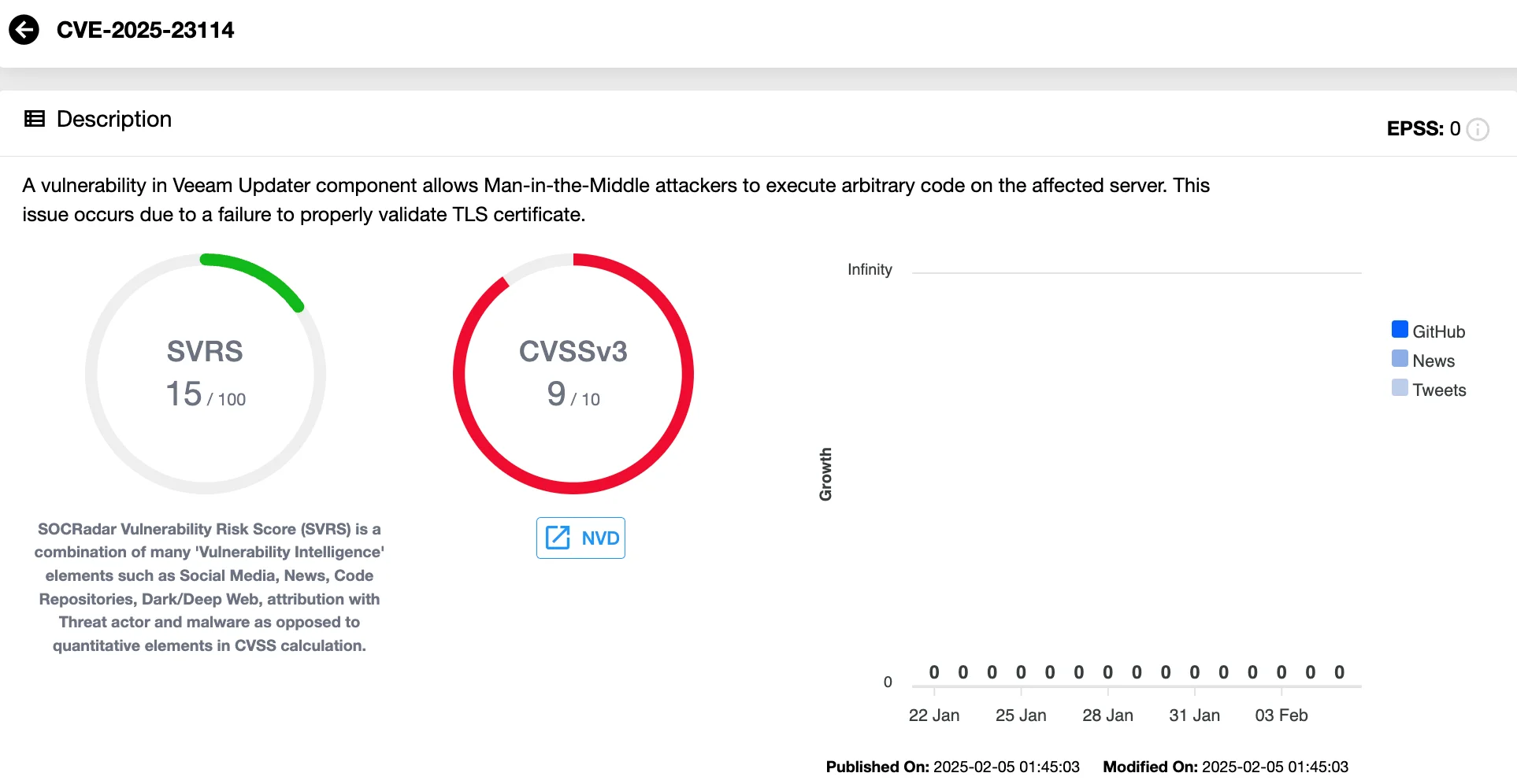
Vulnerability card of CVE-2025-23114 (SOCRadar Vulnerability Intelligence)
Affected Products and Versions:
- Veeam Backup for Salesforce: Versions 3.1 and older
- Veeam Backup for Nutanix AHV: Versions 5.0 and 5.1
- Veeam Backup for AWS: Versions 6a and 7
- Veeam Backup for Microsoft Azure: Versions 5a and 6
- Veeam Backup for Google Cloud: Versions 4 and 5
- Veeam Backup for Oracle Linux Virtualization Manager and Red Hat Virtualization: Versions 3, 4.0, and 4.1
Technical Details of CVE-2025-23114
The vulnerability exists in the Veeam Updater, responsible for managing updates across various Veeam products. An attacker positioned between the vulnerable Veeam appliance and its update server can intercept and tamper with update requests, injecting malicious code into the system. This could lead to complete system compromise, including data theft, ransomware deployment, or persistent access within an organization’s infrastructure.
Mitigation and Updates
Veeam has addressed this vulnerability by releasing updated versions of the Veeam Updater component for each affected product. Users are strongly urged to update their systems immediately. The following table outlines the specific versions that resolve the vulnerability:
| Product | Updater Version |
| Veeam Backup for Salesforce | 7.9.0.1124 |
| Veeam Backup for Nutanix AHV | 9.0.0.1125 |
| Veeam Backup for AWS | 9.0.0.1126 |
| Veeam Backup for Microsoft Azure | 9.0.0.1128 |
| Veeam Backup for Google Cloud | 9.0.0.1128 |
| Veeam Backup for Oracle Linux Virtualization Manager and Red Hat Virtualization | 9.0.0.1127 |
Users can update their systems using the built-in Veeam Updater to update the Veeam Updater component itself. To verify the current Updater version, users should check the update history within their respective Veeam product.
Conclusion
Given the critical nature of CVE-2025-23114, it is imperative for organizations utilizing the affected Veeam products to apply the necessary updates promptly. Failure to do so could result in severe security breaches, including unauthorized access and potential data loss.
Cyber threats are growing more sophisticated, putting every organization at risk. Basic defenses are no longer enough to stay ahead. SOCRadar’s Attack Surface Management (ASM) module provides continuous visibility into your digital assets.
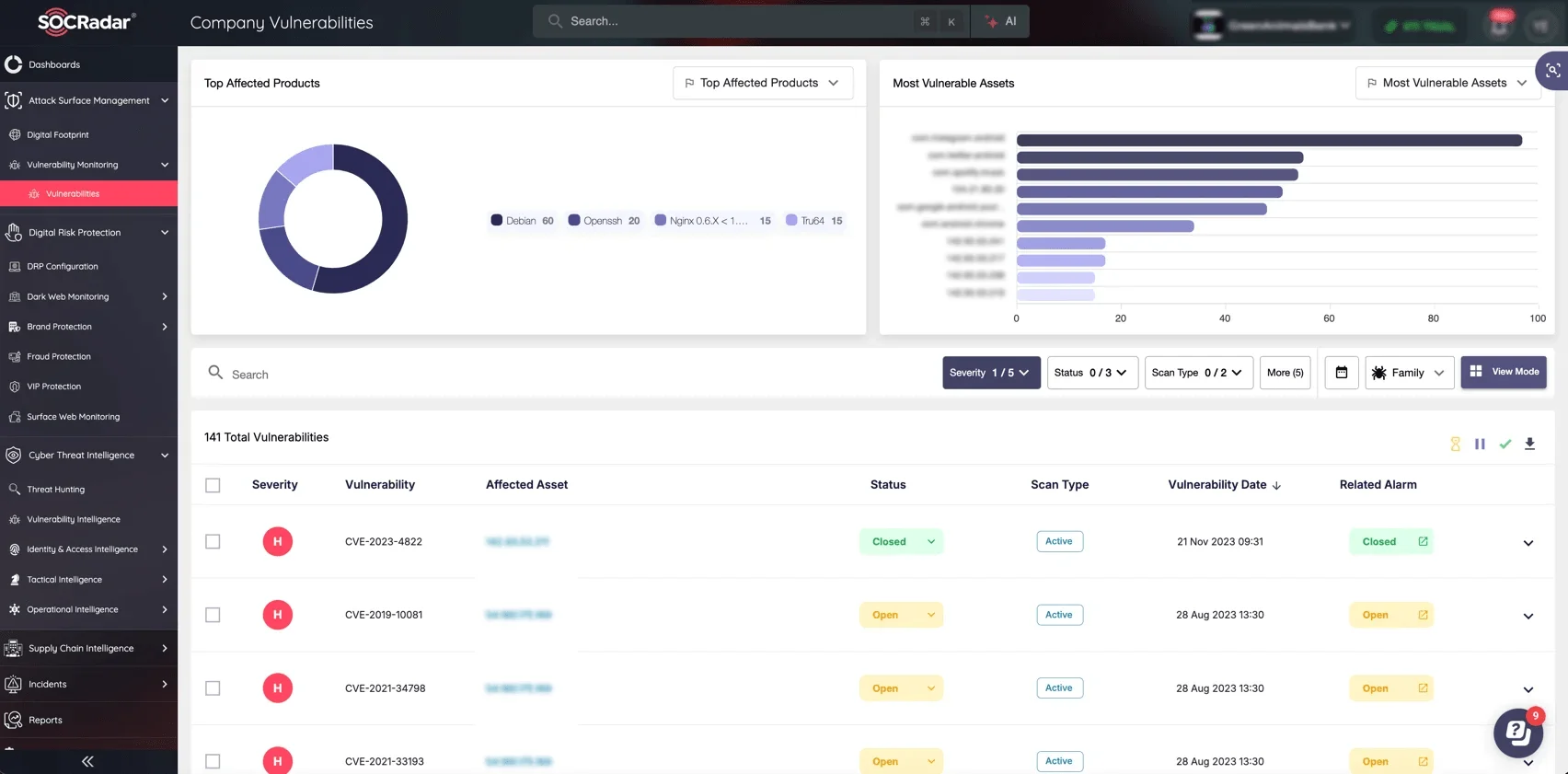
Monitor your digital assets and company vulnerabilities with SOCRadar’s ASM module
With advanced monitoring, the ASM module detects vulnerabilities, malicious activities, and potential exploits targeting your systems. It strengthens your network security, allowing you to proactively mitigate threats before they cause damage.
For more detailed information, please refer to Veeam’s official advisory.


































