
Veeam Fixes Critical Vulnerabilities in Backup & Replication Software (CVE-2022-26500 & CVE-2022-26501)
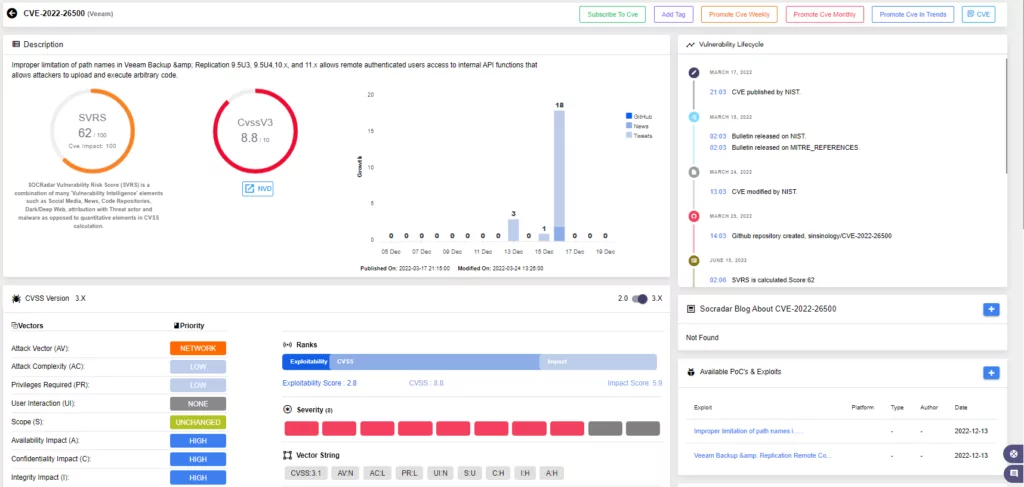
Veeam has recently fixed two security vulnerabilities (CVE-2022-26500 and CVE-2022-26501) in the Backup & Replication software. With critical CVSS ratings of 9.8, the vulnerabilities permit remote code execution, which an attacker could use to take control of a target system.
Affected software versions are:
- 9.5
- 10
- 11
According to Veeam, the vulnerabilities allowed unauthenticated remote attackers to access internal API functions and send malicious input to these functions via the Veeam Distribution Service (TCP 9380 by default).
The vulnerabilities have been listed on Known Exploited Vulnerabilities (KEV) by CISA (U.S. Cybersecurity and Infrastructure Security Agency) due to reports of active exploitation in the wild.
How Critical are These Vulnerabilities?
According to researcher Nikita Petrov, who reported CVE-2022-26500 and CVE-2022-265001, these vulnerabilities pose a serious risk to numerous organizations. It is crucial to install updates immediately or, at the very least, take precautions to detect any unusual activity linked to these products.
The attacks that exploit these flaws have not yet been fully disclosed. Still, in October, several threat actors were seen advertising a “fully weaponized tool for remote code execution” that takes advantage of the two vulnerabilities.
Successful exploitation could result in data loss, ransomware infection, and denial-of-service attacks, among other negative effects.
The Veeamp malware was discovered in the wild being used by the Monti and Yanluowang ransomware groups to steal login information from a Veeam backup management software SQL database. The malicious file is a 32-bit .NET binary that tries to connect to a SQL database.
The username, encrypted password, decrypted password, and description are printed by the credential dumper Veeamp[.]exe following successful decryptions.
Also, researchers found a GitHub repository named veeam-creds. It includes password recovery scripts from the Veeam Backup and Replication credential manager. These 3 files were among those in the repository:
- Veeam-Get-Creds.ps1: A PowerShell script used to retrieve and decrypt accounts from the Veeam database.
- VeeamGetCreds.yaml: A PowerShell Empire module with an adapted Veeam-Get-Creds.ps1 script.
- Veampot.py: A Python script emulates vSphere responses so you can get Veeam stored credentials.
Mitigation
For versions 10 and 11, the vulnerabilities have been fixed with versions 10a and 11a. For users of version 9.5 of Veeam’s software, it is advised to upgrade to a supported version.
If users are unable to update soon, the Veeam Distribution Service should be stopped and disabled as a temporary workaround.
See Veeam’s advisory for patched builds.
Indicators of Compromise (IoCs)
Hashes:
- 9aa1f37517458d635eae4f9b43cb4770880ea0ee171e7e4ad155bbdee0cbe732
- Df492b4cc7f644ad3e795155926d1fc8ece7327c0c5c8ea45561f24f5110ce54
- 78517fb07ee5292da627c234b26b555413a459f8d7a9641e4a9fcc1099f06a3d
Names:
- Veeamp[.]exe
- vp[.]exe
- 9aa1[.]exe
- o_vp[.]exe
IP Address:
- 13.107.4.52




































