
Veeam Service Provider Console Affected by Severe RCE Vulnerability: CVE-2024-29212
Veeam has recently disclosed a significant security vulnerability within Veeam Service Provider Console (VSPC), identified as CVE-2024-29212. This vulnerability poses a serious risk, potentially allowing attackers to execute code remotely on the VSPC server machine.
Veeam is a popular backup and replication tool that is primarily used for data protection and disaster recovery. It provides reliable backup and replication of virtual, physical, and cloud machines.
What is CVE-2024-29212?
CVE-2024-29212 is a high-severity Remote Code Execution (RCE) vulnerability affecting multiple versions of the Veeam Service Provider Console.
It arises from an unsafe deserialization method used in the server’s communication process between the management agent and its components.
This vulnerability could allow an attacker to perform RCE on the server hosting the Veeam Service Provider Console, compromising the sensitive backup data managed by the console.
How critical is the CVE-2024-29212 vulnerability?
Veeam has assigned a severity score of 8.8 for CVE-2024-29212 on the advisory. The National Vulnerability Database (NVD) has not yet assigned it a CVSS score.
Which Veeam Service Provider Console versions are affected by CVE-2024-29212?
The VSPC versions impacted by CVE-2024-29212 are as follows:
- v4.0
- v5.0
- v6.0
- v7.0
- v8.0
Was CVE-2024-29212 exploited?
Currently, there have been no confirmed cases of active exploitation for CVE-2024-29212 in the wild.
Nonetheless, widely used software tools and services for data handling – such as data transfer and backup – are probable targets for attackers, potentially leading to severe consequences.
We previously reported on a Veeam vulnerability (CVE-2023-27532) exploited by the FIN7 APT group, which used it to distribute malware droppers. This breach enabled attackers to access infrastructure hosts and steal encrypted credentials.
A Shodan search currently reveals approximately 300 exposed instances of the Veeam Service Provider Console. Meanwhile, a FOFA search indicates that over 9,000 instances were detected in the past year.
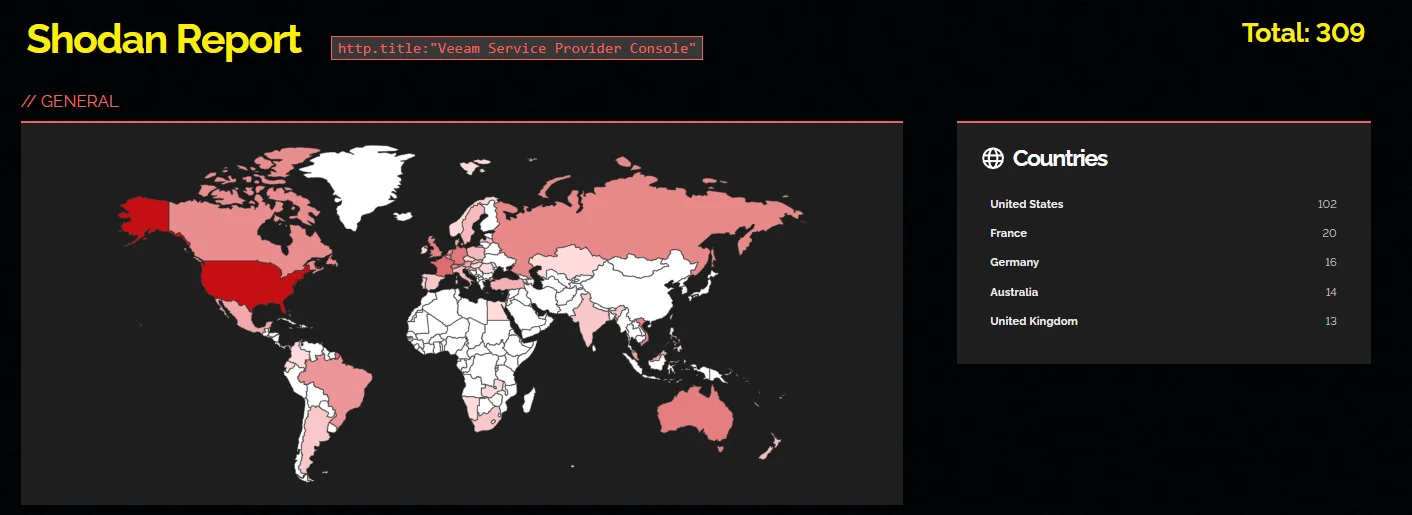
Shodan search results for Veeam Service Provider Console
With SOCRadar’s Vulnerability Intelligence feature, you can efficiently manage vulnerabilities and stay informed about emerging threats and exploit trends. SOCRadar provides actionable insights into security threats, enabling proactive measures and strengthening defenses against potential cyberattacks.
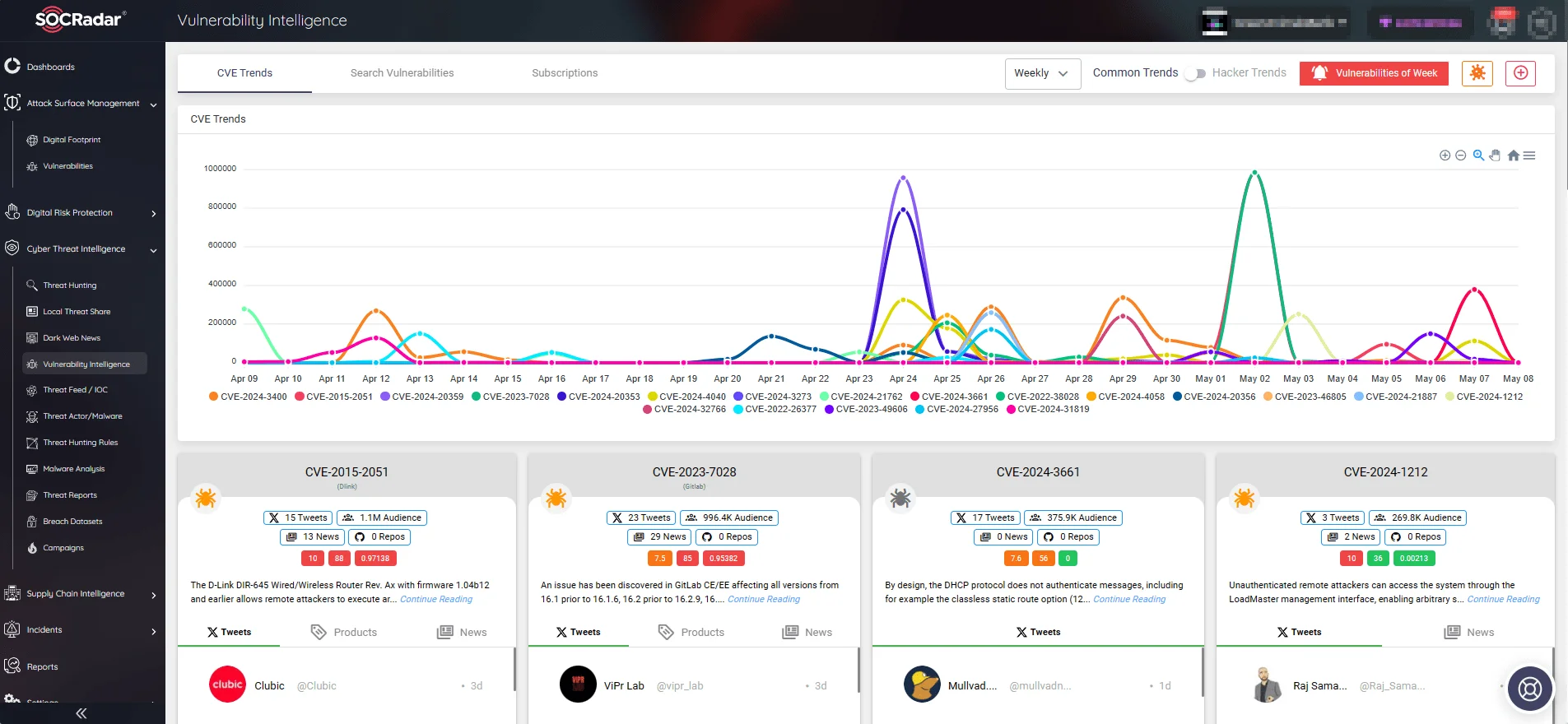
SOCRadar’s Vulnerability Intelligence
On the Vulnerability Intelligence page, you can search for vulnerabilities by vendor or product name and access information about the latest related activities, including exploits.
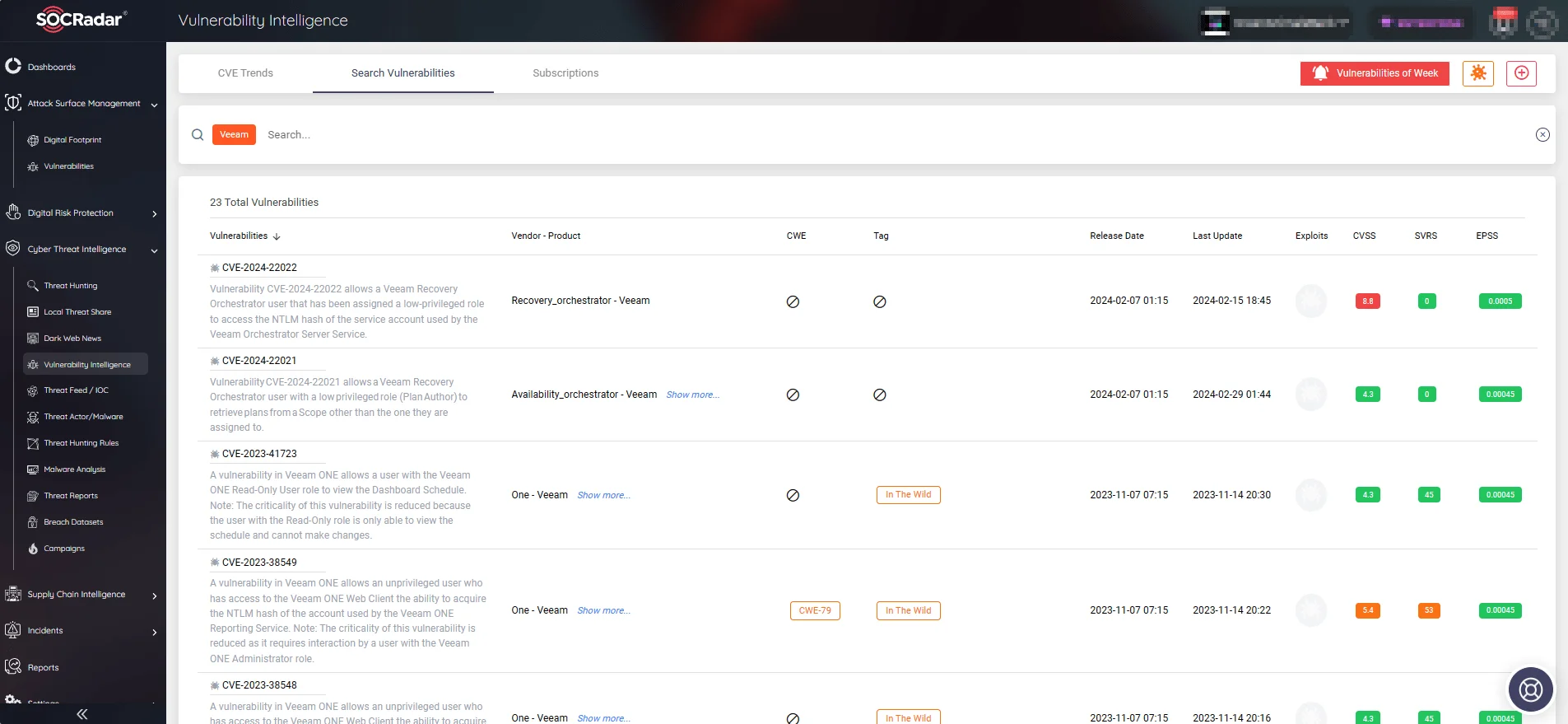
Veeam vulnerabilities (SOCRadar Vulnerability Intelligence)
How to Address CVE-2024-29212?
Veeam has already taken steps to mitigate this vulnerability by releasing patches. The fixed versions are:
- v7.0.0.18899
- v8.0.0.19236
Organizations utilizing Veeam Service Provider Console are urged to apply these updates immediately.
It is important to note that these updates apply to the recent versions of VSPC (versions 7 and 8), and users of older, unsupported versions (versions 4, 5, and 6) should first consider upgrading to a supported release.
To access the updates and related release information, visit the Veeam advisory page.
Secure your systems and safeguard your data by staying updated with the latest cybersecurity developments and quickly addressing disclosed vulnerabilities. Use SOCRadar’s Attack Surface Management (ASM) module to stay ahead of security vulnerabilities and exploitation, and receive timely alerts about threats to your digital assets.
SOCRadar’s Attack Surface Management




































