
VMware Security Alert: Active Exploitation of Zero-Day Vulnerabilities (CVE-2025-22224, CVE-2025-22225, and CVE-2025-22226)
[Update] March 7, 2025: “37,000 VMware ESXi Servers Still Vulnerable to CVE-2025-22224”
Virtualization technology is a backbone of modern enterprises, but it also presents a lucrative target for cybercriminals, such as ransomware actors. Recently, multiple zero-day vulnerabilities have been discovered in VMware products, posing a severe security risk to businesses relying on virtualized infrastructure.
The Microsoft Threat Intelligence Center initially discovered and reported these vulnerabilities, which Broadcom has since confirmed are being actively exploited. Identified as CVE-2025-22224, CVE-2025-22225, and CVE-2025-22226, these flaws impact widely used VMware solutions such as VMware ESXi, vSphere, Workstation, Fusion, Cloud Foundation, and Telco Cloud Platform. Given their critical nature and real-world exploitation, organizations must act immediately to secure their environments.
Key Details on the Latest VMware Threats
These security flaws allow attackers with administrator or root privileges on a virtual machine to escape the VM sandbox and gain unauthorized access to the hypervisor:
- CVE-2025-22224 (Critical, CVSS 9.3) – A VCMI heap overflow vulnerability that enables local attackers with administrative privileges to execute code as the VMX process on the host.
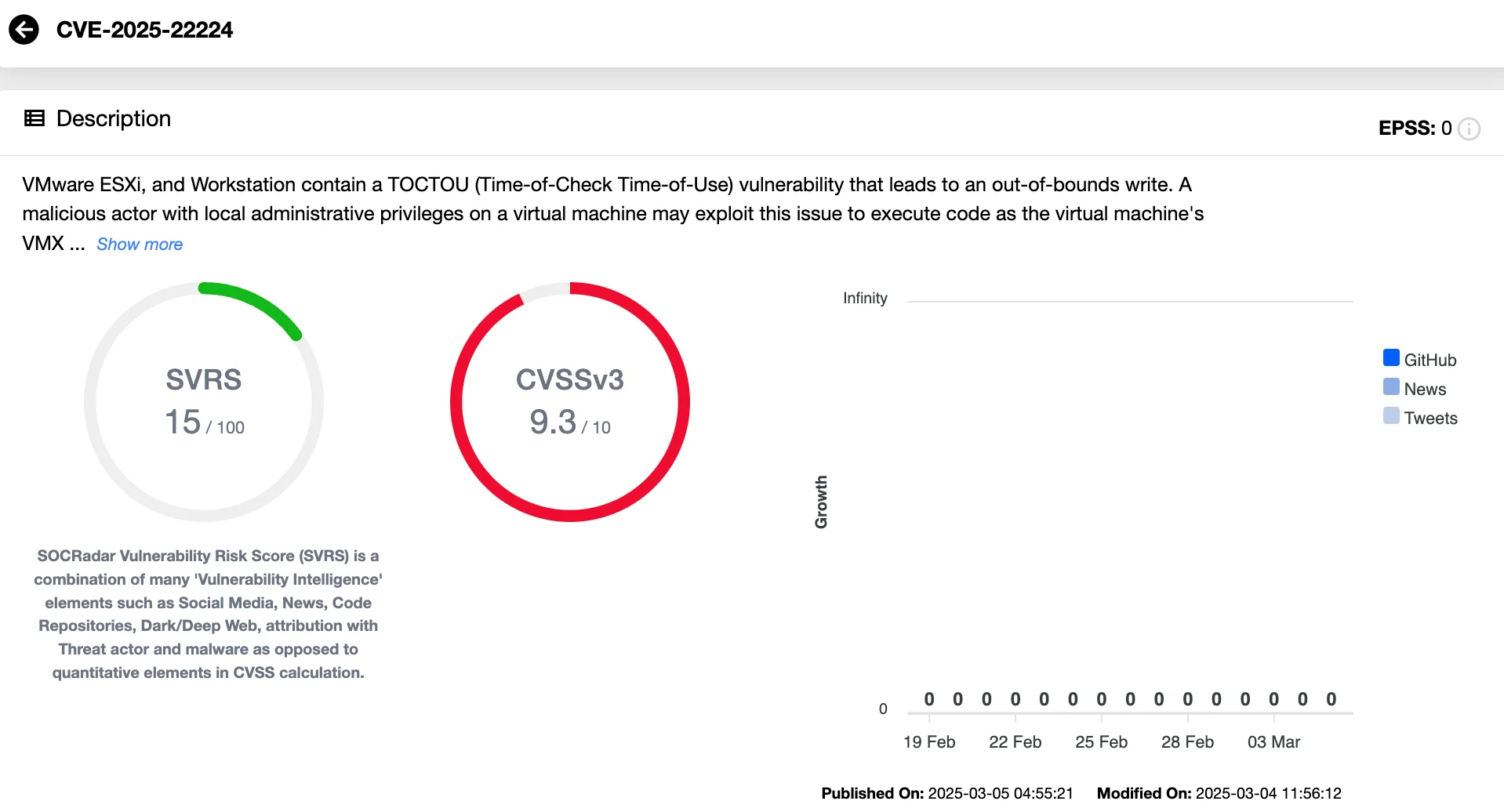
Vulnerability card of CVE-2025-22224 (SOCRadar Vulnerability Intelligence)
- CVE-2025-22225 (High, CVSS 8.2) – An ESXi arbitrary write vulnerability, which allows the VMX process to trigger arbitrary kernel writes, leading to a sandbox escape.
- CVE-2025-22226 (Medium, CVSS 7.1) – An HGFS information disclosure vulnerability, allowing attackers to leak memory from the VMX process.
These vulnerabilities present a significant risk, particularly for enterprises that depend on VMware infrastructure for cloud environments and critical workloads.
Who Is Affected?
The issues affect VMware ESX as well as any products that involve ESX, such as VMware vSphere, VMware Cloud Foundation, and VMware Telco Cloud Platform. Therefore, organizations using any unpatched versions of these products are at risk.
VMware vCenter, SDDC Manager, NSX, and Aria Suite are not impacted. It is further clarified in FAQ of the vulnerabilities that Live Patching is not an option. Additionally, disabling VMware Tools does not eliminate the risk, as attackers with privileged access can re-enable it. Organizations unsure about their ESX version should assume vulnerability and update immediately.
It is advisable to check the latest VMware Security Advisory VMSA-2025-0004 for further information on affected products, versions, and necessary patches.
SOCRadar’s Vulnerability Intelligence
SOCRadar’s Vulnerability Intelligence provides your security team with insights into newly disclosed vulnerabilities, helping you assess risks, track exploits, and prioritize remediation efforts. Leverage the Cyber Threat Intelligence module to quickly evaluate the severity of vulnerabilities with real-world threat intelligence, receive timely notifications, and take action to mitigate risks before they impact your operations.
How Are These Vulnerabilities Exploited?
The flaws require attackers to have already gained administrator or root-level privileges on a virtual machine. Once inside, they can break out of the VM environment and gain control over the hypervisor, posing severe security implications for multi-tenant environments.
37,000 VMware ESXi Servers Still Vulnerable to CVE-2025-22224
Shadowserver Foundation reports that 37,000 internet-exposed VMware ESXi instances remain vulnerable to CVE-2025-22224, a critical flaw that allows local admin users on a virtual machine to execute code on the host.
It appears that despite ongoing patching efforts, a large number of systems remain exposed, particularly in China, France, and the United States.
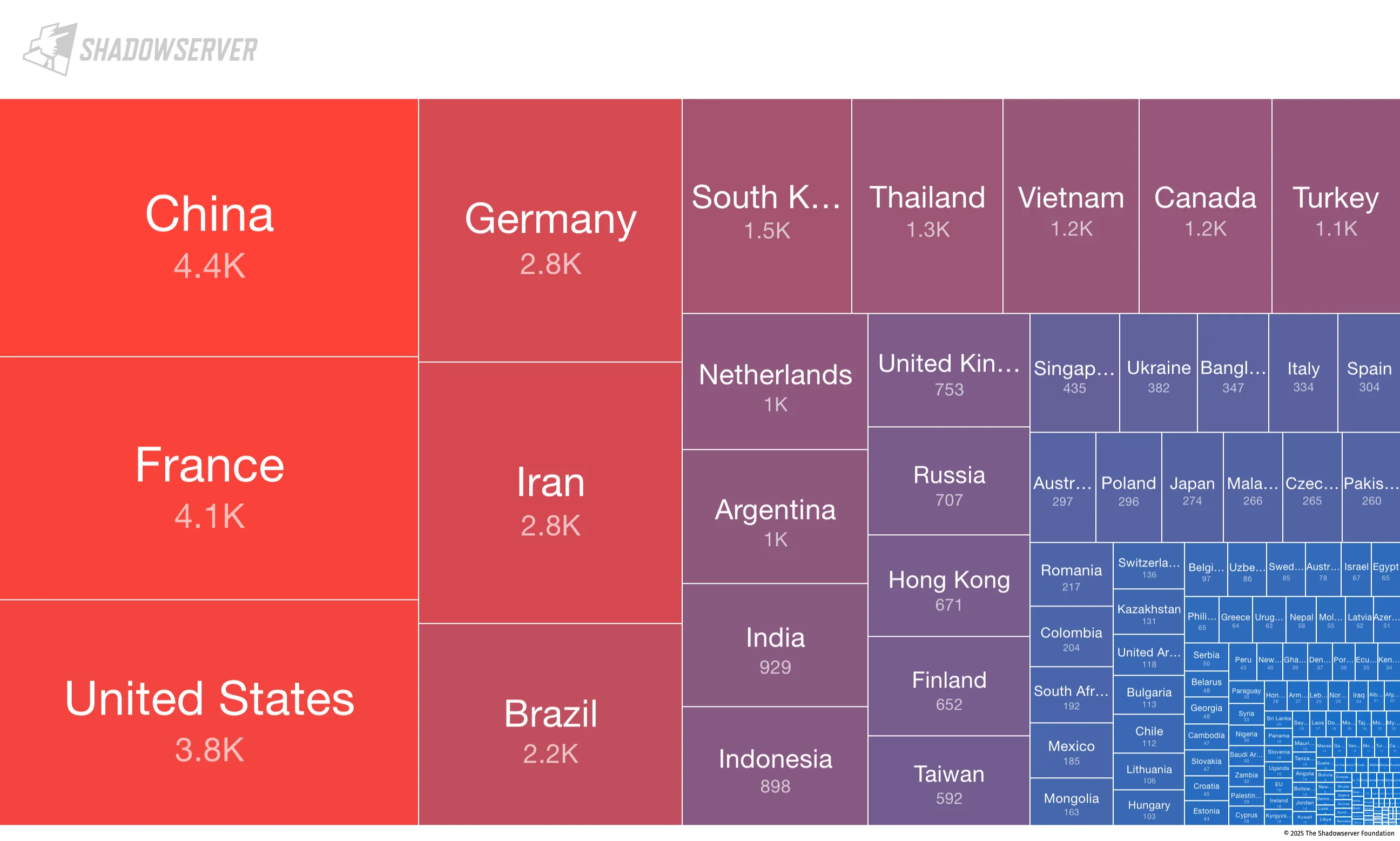
A tree map on exposed instances (Shadowserver)
Although the identities of the attackers and their targets remain unclear, CISA has mandated federal agencies to secure their systems by March 25, 2025, adding CVE-2025-22224, CVE-2025-22225, and CVE-2025-22226 to the Known Exploited Vulnerabilities (KEV) Catalog.
How to Protect Your Organization
Broadcom has confirmed that there are no viable workarounds for these vulnerabilities. Organizations must apply the patches to secure their VMware environments.
While security layers like privileged access management and host-based defenses can provide additional protection, they are not substitutes for patching.
All in all, to mitigate the risks, take the following actions:
- Apply Patches Immediately – Install the latest security patches listed in the VMware Security Advisory.
- Assess the Risk – Security teams should conduct an immediate risk assessment to determine exposure.
- Monitor for Suspicious Activity – Organizations should analyze logs and system activity for any indicators of compromise.
- Strengthen Access Controls – Limit administrative access and enforce strong authentication measures.
- Implement Network Segmentation – Restrict lateral movement within virtualized environments to minimize risk.
Gain Complete Visibility Into Your Attack Surface with SOCRadar’s ASM
With SOCRadar’s Attack Surface Management (ASM), you can proactively monitor your attack surface, uncover vulnerabilities, and identify potential threats before they can be exploited.
Key Capabilities:
- Continuous Monitoring: Track external-facing assets, third-party services, and shadow IT.
- Risk Assessment: Understand the full extent of your exposure with real-time risk analysis.
- Comprehensive Visibility: Gain a clear view of all vulnerabilities across your organization’s digital landscape.
- Early Detection: Identify threats like exposed credentials and weak spots before they become active risks.
Take control of your digital security with SOCRadar’s ASM platform. Ensure you’re always one step ahead of emerging threats and minimize your attack surface effectively.
Cisco Warns of Webex for BroadWorks Security Flaw
In other important news, Cisco has identified a security vulnerability in Webex for BroadWorks that could allow unauthenticated remote attackers to access credentials.
While no CVE ID has been assigned yet, the flaw affects Cisco BroadWorks (on-premises) and Cisco Webex for BroadWorks (hybrid cloud/on-premises) instances on Windows, due to sensitive information being exposed in SIP headers. Additionally, authenticated users could retrieve credentials in plain text from logs, potentially enabling impersonation attacks. Fortunately, there is no evidence of active exploitation at this time.
The company has already deployed a configuration change to address the issue and advises users to restart their Webex app to apply the fix. As a temporary workaround, administrators should enable secure transport for SIP communication and rotate credentials to prevent unauthorized access.
Visit Cisco’s advisory here for full details.




































