
Vulnerability in Ivanti Connect Secure, Policy Secure, and Neurons for ZTA Exploited (CVE-2024-21888, CVE-2024-21893)
[Update] March 11, 2024: “Rapid Exploitation of CVE-2024-21888 and CVE-2024-21893 by Magnet Goblin”, “Indicators of Compromise (IOCs)”
[Update] March 1, 2024: “CISA and Partners Issued Joint Advisory on Exploitation of Ivanti Vulnerabilities (CVE-2023-46805, CVE-2024-21887, CVE-2024-21893)”
[Update] February 29, 2024: “UNC5325 and UNC3886 Exploit Ivanti Connect Secure VPN Vulnerabilities to Deploy Malware”
[Update] February 13, 2024: “Ivanti’s CVE-2024-21893 Exploited to Install the New DSLog Backdoor on Nearly 700 Assets”
[Update] February 6, 2024: “Increased Exploitation Attempts Targeting CVE-2024-21893 in Ivanti”
Ivanti has disclosed that as part of their ongoing investigation into previous Ivanti Connect Secure vulnerabilities, they discovered two new vulnerabilities.
The Cybersecurity and Infrastructure Security Agency (CISA) has already added one of these vulnerabilities to its Known Exploited Vulnerabilities (KEV) Catalog, demanding Federal Civilian Executive Branch (FCEB) agencies to remediate it by the near deadline of February 2, 2024.
Details of the Newest Ivanti Vulnerabilities (CVE-2024-21888 and CVE-2024-21893)
The vulnerabilities with high severity ratings are identified as CVE-2024-21888 and CVE-2024-21893. Both vulnerabilities affect all supported versions, 9.x and 22.x. See their details below:
CVE-2024-21888 (CVSS score: 8.8): A Privilege Escalation vulnerability in the web component of Ivanti Connect Secure and Ivanti Policy Secure. It could enable a user to gain administrative privileges.

Vulnerability intel card for CVE-2024-21888 (SOCRadar Vulnerability Intelligence)
CVE-2024-21893 (CVSS score: 8.2): A Server-Side Request Forgery (SSRF) vulnerability in the SAML component of Ivanti Connect Secure, Ivanti Policy Secure, and Ivanti Neurons for ZTA. It could enable an attacker to gain access to some restricted resources without authentication.

Vulnerability intel card for CVE-2024-21893 (SOCRadar Vulnerability Intelligence)
You can easily access vulnerability information and updates through SOCRadar. The platform provides comprehensive Vulnerability Intelligence that includes the most recent updates on known vulnerabilities, such as available exploits, repositories, exploitability risks, and hacker trends.

SOCRadar’s Vulnerability Intelligence
Are Patches Available for the New Vulnerabilities?
Ivanti made the patches accessible via the standard download portal. Patches are currently available for the following versions:
Ivanti Connect Secure:
- 9.1R14.4
- 9.1R17.2
- 9.1R18.3
- 22.4R2.2
- 22.5R1.1
ZTA:
- 22.6R1.3
According to the company, the remaining supported versions will be patched on a staggered schedule, and a new mitigation is also available for download.
“CVE-2023-46805, CVE-2024-21887, CVE-2024-21888 and CVE-2024-21893 can be mitigated by importing mitigation.release.20240126.5.xml file via the download portal.”
Refer to the official advisory for further details.
Exploitation of CVE-2024-21893: Ivanti Expects a Surge in Attacker Activity
At the time of the disclosure, Ivanti stated that there was no evidence of CVE-2024-21888 affecting customers, whereas CVE-2024-21893 did affect a limited number of customers.
Ivanti also stated that the exploitation of CVE-2024-21893 appears to be deliberate. Once the details of the vulnerability are made public, the company expects the exploitation attempts to increase. In the meantime, CISA has added CVE-2024-21893 to its KEV Catalog to warn agencies about exploitation and urge them to remediate it.
With SOCRadar’s Attack Surface Management module, you can monitor digital assets and identify vulnerabilities that are affecting your organization. Additionally, ASM’s Company Vulnerabilities page includes a CISA KEV Check feature that allows you to quickly identify KEV Catalog-listed vulnerabilities that affect your systems.

SOCRadar Attack Surface Management/Company Vulnerabilities
CISA Alert and Patches for the Ivanti Connect Secure Zero-Day Vulnerabilities
In addition to the public disclosure of the new vulnerabilities, the company has released fixes for the zero-day vulnerabilities CVE-2023-46805 and CVE-2024-21887, which affect Connect Secure. The most recent updates on these vulnerabilities also include a CISA alert about threat actors developing workarounds for previous mitigations and their exploitation to deploy KrustyLoader malware.
The aforementioned CISA alert was most recently updated to include the new vulnerabilities, CVE-2024-21888 and CVE-2024-21893, and direct organizations to apply updates or mitigation for affected versions.
You can find more information about zero-day vulnerabilities in our other blog post: Attackers Exploit Ivanti Connect Secure Zero-Day Vulnerabilities to Deploy Webshells (CVE-2023-46805, CVE-2024-21887).
Increased Exploitation Attempts Targeting CVE-2024-21893 in Ivanti
Exploitation attempts surge, confirming Ivanti’s previous speculations – threat actors are actively exploiting the latest Ivanti SSRF vulnerability, CVE-2024-21893. Shadowserver reports that they observed at least 170 different IP addresses attempting to exploit the vulnerability.
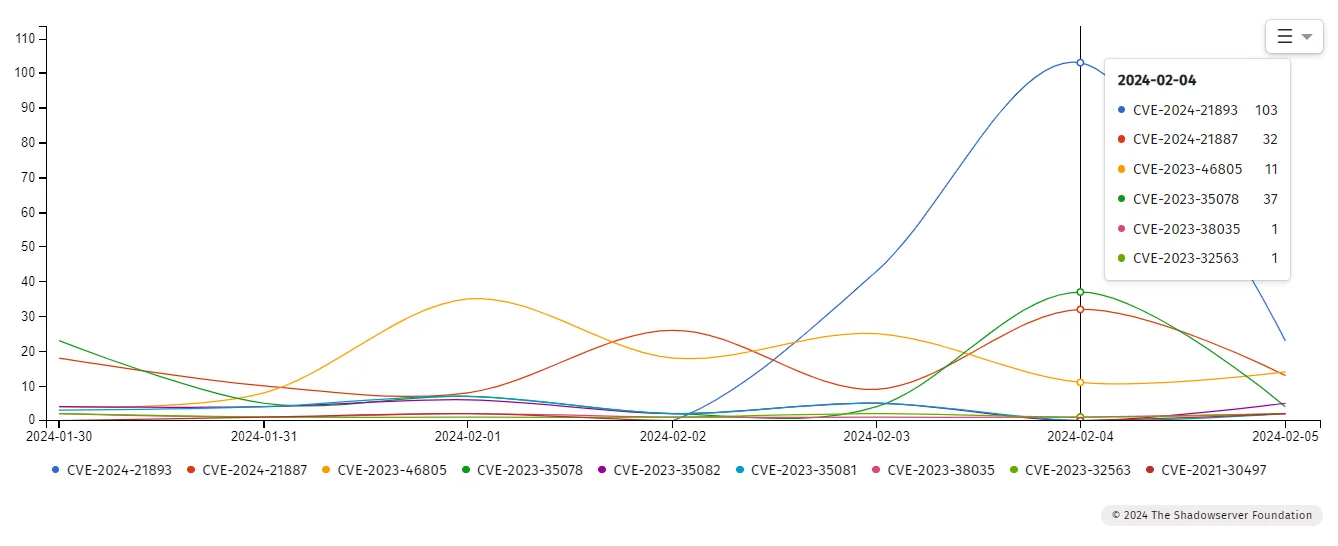
Exploitation attempts by Ivanti CVEs (Shadowserver)
Additionally, it is stated that the attackers employed similar methods mentioned in the Proof-of-Concept (PoC) exploit by Rapid7, just prior to its release.
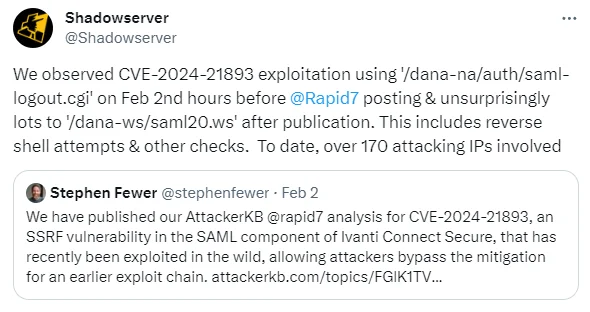
Tweet by Shadowserver (X)
Ivanti’s CVE-2024-21893 Exploited to Install the New DSLog Backdoor on Nearly 700 Assets
While prior reports detailed exploitation attempts against the CVE-2024-21893 vulnerability, recent findings indicate that threat actors are deploying the DSLog backdoor to execute remote commands on compromised Ivanti servers.
The discovery of this new backdoor emerged on February 3, 2024, during the analysis of a compromised appliance. Although the appliance had Ivanti’s initial XML mitigation in place, which blocks all API endpoints, it lacked the second mitigation or patch.
How Did Attackers Inject the Backdoor?
It was discovered that attackers injected a backdoor into a component of the Ivanti
appliance using the CVE-2024-21893 vulnerability, ensuring persistent remote access.
Researchers examined a compromised Ivanti device snapshot and logs and found that attackers injected the backdoor into the appliance’s code base through SAML authentication requests containing encoded commands.
According to the researchers, attackers modified an existing Perl file named ‘DSLog.pm’, a legitimate logging module for authenticated web requests and system logs, and inserted the backdoor.
The commands in the requests indicated the attacker’s intent to conduct internal reconnaissance and confirm root access by performing tasks such as writing system information to a publicly accessible file (index2.txt).
Subsequent SAML requests sought to secure read/write filesystem permissions, detect changes to the legitimate logging script (DSLog.pm), and inject the backdoor if the expected modification string was not present.
The attackers used SHA256 hashes unique to the contacted device as API keys, as required by the HTTP User-Agent header for command execution. Because each hash is unique, it cannot be used to access another device’s backdoor. The method utilized to calculate the SHA256 hashes remains undetermined.
About the DSLog Backdoor
The DSLog backdoor is reported to be able to execute any command on the compromised device, with root privileges. The attackers embed these commands in a query parameter named ‘cdi’ and send them via HTTP requests.
Each HTTP request contains a unique SHA256 hash per targeted device, which is used to authenticate the request to the backdoor. The researchers point out that the webshell does not provide any status or code when contacted, making the backdoor exceptionally discreet in its operations.
Researchers assert that the commands issued by the attackers via the backdoor can be identified within the Ivanti access logs (log.localhostX-DAY-YEAR-XX-XX_XX_XX_XX-(XXX).access), appearing as hex-encoded values; however, the attacker deleted these access logs on several compromised devices in order to hide malicious activity.
Regardless of the challenges, at least 670 compromised Ivanti servers were discovered by examining other files like ‘index.txt’, ‘index1.txt’, and ‘index2.txt’ in the ‘hxxp://{ip}/dana-na/imgs/’ directory.
UNC5325 and UNC3886 Exploit Ivanti Connect Secure VPN Vulnerabilities to Deploy Malware
Amid recent cybersecurity findings, researchers have unveiled significant developments concerning cyber espionage activities linked to China. Two threat groups, UNC5325 and UNC3886, have emerged as key players in exploiting vulnerabilities within Ivanti Connect Secure VPN appliances.
UNC5325, identified as a sophisticated Chinese threat actor, has capitalized on the CVE-2024-21893 vulnerability to infiltrate Ivanti appliances. This exploit has facilitated the deployment of a suite of new malware strains, including LittleLamb.WoolTea, PitStop, Pitdog, PitJet, and PitHook. Notably, researchers suggest a connection between UNC5325 and UNC3886, citing code similarities between their malware variants.
In tandem with its cyber operations, UNC3886 has a history of exploiting zero-day flaws in various platforms, such as Fortinet and VMware solutions, to implant malicious software like VirtualPita, VirtualPie, ThinCrust, and CastleTap. The primary targets of UNC3886 have been entities within the defense industrial base, technology, and telecommunication sectors in the United States and Asia-Pacific regions.
The recent surge in cyberattacks has underscored the critical importance of addressing vulnerabilities promptly. UNC5325’s exploitation of CVE-2024-21893, which dates back to January 19, 2024, highlights the urgency of maintaining up-to-date security protocols. By combining CVE-2024-21893 with a previously disclosed command injection vulnerability (CVE-2024-21887), UNC5325 bypassed Ivanti appliances’ defenses, paving the way for the deployment of sophisticated malware like BushWalk.
Vulnerability intel card for CVE-2024-21887 (SOCRadar Vulnerability Intelligence)
To evade detection, UNC5325 has leveraged legitimate Ivanti components, particularly SparkGateway plugins, to introduce additional malicious payloads. One such plugin, PitFuel, attempted to load the malicious shared object LittleLamb.WoolTea, enabling persistent access across system upgrades and patches. Despite these efforts, the malware’s inability to adapt to encryption key mismatches has thwarted persistent access attempts.
UNC5325’s tactics underscore the evolving nature of cyber threats, with adversaries demonstrating a keen understanding of network infrastructure and employing sophisticated techniques to circumvent detection. Researchers predict a continued reliance on zero-day vulnerabilities and tailored malware by Chinese espionage actors, emphasizing the need for proactive security measures and ongoing vigilance.
CISA and Partners Issued Joint Advisory on Exploitation of Ivanti Vulnerabilities (CVE-2023-46805, CVE-2024-21887, CVE-2024-21893)
CISA, FBI, and international partners have issued a joint advisory in response to the exploitation of vulnerabilities found in Ivanti Connect Secure and Policy Secure Gateways.
The advisory outlines cyber attacks exploiting CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893. It includes Indicators of Compromise (IOCs), detection methods, and guidance for organizations to mitigate these vulnerabilities.
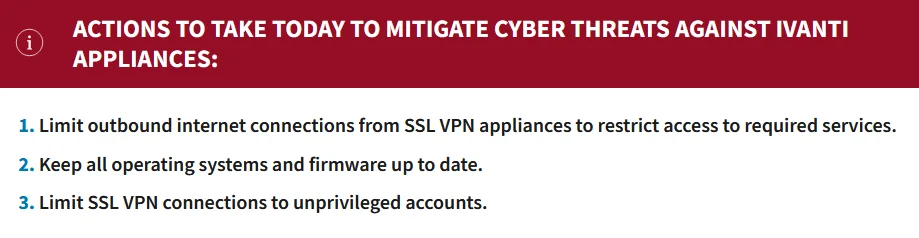
CISA’s alert: Actions to take today to mitigate cyber threats against Ivanti appliances
The advisory highlights two significant findings: First, the Ivanti Integrity Checker Tool (ICT) may fail to detect compromise due to threat actors’ ability to deceive it. Second, despite victims performing factory resets on Ivanti devices, threat actors may still achieve root-level persistence.
The advisory emphasizes the failure of ICT scans in detecting previous compromises, stating that they lead to a false sense of security.
In observed cases, threat actors exploited the CVEs to gain initial access, implant web shells, and harvest stored credentials. After compromising the systems, the threat actors moved laterally into domain environments, utilizing native tools like freerdp, ssh, telnet, and nmap libraries to extend their reach. Some incidents resulted in complete domain compromises.
In incident response investigations, CISA found that Ivanti’s internal and external ICTs failed to detect compromises because web shells discovered on systems lacked detectable file mismatches. Additionally, forensic analysis revealed that threat actors covered their tracks by overwriting files, time-stomping files, and remounting the runtime partition to restore the appliance to a clean state.
In light of these findings, the authoring organizations stress the importance of vigilance and advise network defenders to take several proactive measures:
- Assume that user and service account credentials stored within affected Ivanti VPN appliances are compromised.
- Conduct thorough hunts for malicious activity on their networks using the detection methods and IOCs provided in the advisory.
- Run the latest version of Ivanti’s external ICT.
- Apply available patching guidance from Ivanti as new versions are released.
- Upon detection of a potential compromise, gather and analyze logs and artifacts for malicious activity and follow the incident response recommendations in the advisory.
Rapid Exploitation of CVE-2024-21888 and CVE-2024-21893 by Magnet Goblin
Threat group Magnet Goblin, which has been active since January 2022, is using 1-day vulnerabilities to deliver their custom Linux malware, Nerbian RAT and MiniNerbian. These exploits are primarily used to breach edge devices and public-facing services, facilitating the group’s financially motivated campaigns.
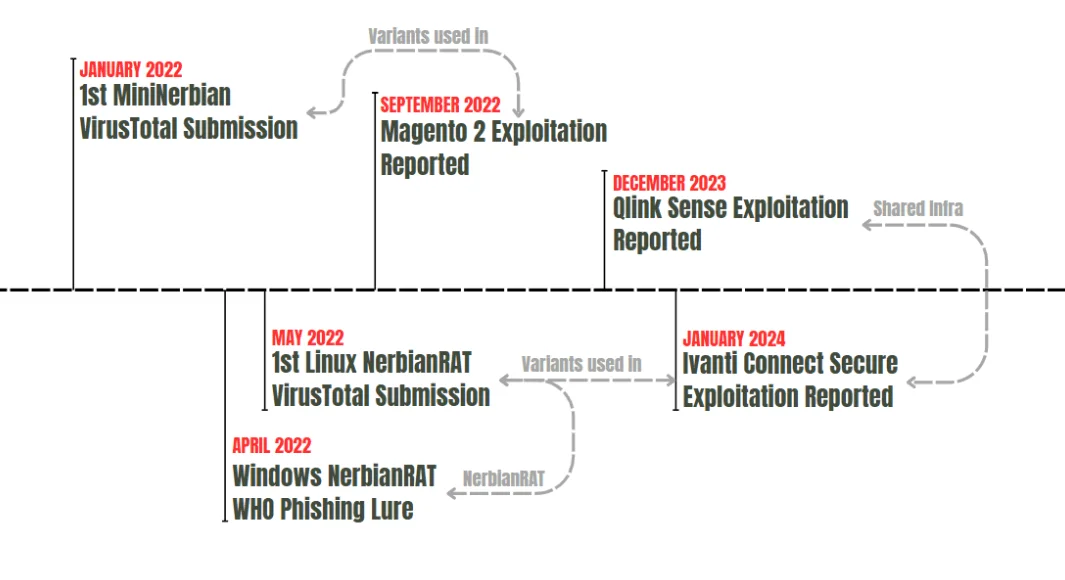
Campaigns that have been attributed to the Magnet Goblin threat group (Source)
The distinguishing feature of Magnet Goblin is its ability to rapidly deploy exploits within a day of a Proof-of-Concept (PoC) exploit being published. This group has leveraged several 1-day vulnerabilities, including Ivanti Connect Secure vulnerabilities CVE-2024-21888, CVE-2024-21893, CVE-2023-46805, and CVE-2024-21887, along with CVE-2022-24086 in Magento, and CVE-2023-41265, CVE-2023-41266, and CVE-2023-48365 in Qlik Sense.
The group targets unpatched Ivanti Connect Secure VPN, Magento, Qlik Sense, and possibly Apache ActiveMQ servers for an initial breach. Subsequently, they deploy the cross-platform Remote Access Trojan (RAT) known as Nerbian RAT, first disclosed in May 2022, together with its simplified variant, MiniNerbian.
The payloads for this campaign are downloaded from specific URLs and, after execution, the Linux NerbianRAT variants connect back to the IP 172.86.66[.]165. Both Nerbian RAT and MiniNerbian allow for the execution of arbitrary commands received from a Command and Control (C2) server, with results then exfiltrated back to the C2 server.
Magnet Goblin’s recent Ivanti Connect Secure VPN campaign revealed the Linux version of the malware NerbianRAT, alongside a JavaScript credential stealer called WARPWIRE. In addition to these tools, the group also utilizes the Go-based tunneling software Ligolo, and remote management solutions such as AnyDesk and ScreenConnect.
The group’s swift adoption and effective use of 1-day vulnerabilities underscore the growing threat landscape posed by such financially motivated actors. Researchers continue to monitor Magnet Goblin, emphasizing the necessity for organizations to promptly patch identified vulnerabilities and heighten their security measures to deter such exploits.
Indicators of Compromise (IOCs)
Below are the IOCs related to Magnet Goblin’s exploitation of the 1-day vulnerabilities, according to CP Research.
IP Addresses:
91.92.240[.]113
45.9.149[.]215
94.156.71[.]115
URLs:
http://91.92.240[.]113/auth.js
http://91.92.240[.]113/login.cgi
http://91.92.240[.]113/aparche2
http://91.92.240[.]113/agent
http://45.9.149[.]215/aparche2
http://45.9.149[.]215/agent
http://94.156.71[.]115/lxrt
http://94.156.71[.]115/agent
http://94.156.71[.]115/instali.ps1
http://94.156.71[.]115/ligocert.dat
http://94.156.71[.]115/angel.dat
http://94.156.71[.]115/windows.xml
http://94.156.71[.]115/instal1.ps1
http://94.156.71[.]115/Maintenance.ps1
http://94.156.71[.]115/baba.dat
**http://**oncloud-analytics[.]com/files/mg/elf/RT1.50.png
http://cloudflareaddons[.]com/assets/img/Image_Slider15.1.png
MiniNerbian C2:
mailchimp-addons[.]com
allsecurehosting[.]com
dev-clientservice[.]com
oncloud-analytics[.]com
cloudflareaddons[.]com
textsmsonline[.]com
proreceive[.]com
NerbianRAT C2:
172.86.66[.]165
45.153.240[.]73
NerbianRAT Hashes (SHA256):
027d03679f7279a2c505f0677568972d30bc27daf43033a463fafeee0d7234f6
9cb6dc863e56316364c7c1e51f74ca991d734dacef9029337ddec5ca684c1106
9d11c3cf10b20ff5b3e541147f9a965a4e66ed863803c54d93ba8a07c4aa7e50
MiniNerbian Hashes (SHA256):
d3fbae7eb3d38159913c7e9f4c627149df1882b57998c8acaac5904710be2236
df91410df516e2bddfd3f6815b3b4039bf67a76f20aecabccffb152e5d6975ef
99fd61ba93497214ac56d8a0e65203647a2bc383a2ca2716015b3014a7e0f84d
9ff0dcce930bb690c897260a0c5aaa928955f4ffba080c580c13a32a48037cf7
3367a4c8bd2bcd0973f3cb22aa2cb3f90ce2125107f9df2935831419444d5276
f23307f1c286143b974843da20c257901cf4be372ea21d1bb5dea523a7e2785d
f1e7c1fc06bf0ea40986aa20e774d6b85c526c59046c452d98e48fe1e331ee4c
926aeb3fda8142a6de8bc6c26bc00e32abc603c21acd0f9b572ec0484115bb89
894ab5d563172787b052f3fea17bf7d51ca8e015b0f873a893af17f47b358efe
WARPWIRE Hashes (SHA256):
1079e1b6e016b070ebf3e1357fa23313dcb805d3a6805088dbc3ab6d39330548
e134e053a80303d1fde769e50c2557ade0852fa827bed9199e52f67bac0d9efc
Compromised Servers:
www.fernandestechnical[.]com/pub/health_check.php
biondocenere[.]com/pub/health_check.php
****www.miltonhouse[.]nl/pub/opt/processor.php
https://theroots[.]in/pub/media/avatar/223sam.jpg
Hashes of Other Tools and Scripts (SHA256):
7967def86776f36ab6a663850120c5c70f397dd3834f11ba7a077205d37b117f
9895286973617a79e2b19f2919190a6ec9afc07a9e87af3557f3d76b252292df
bd9edc3bf3d45e3cdf5236e8f8cd57a95ca3b41f61e4cd5c6c0404a83519058e
b35f11d4f54b8941d4f1c5b49101b67b563511a55351e10ad4ede17403529c16
7b1d1e639d1994c6235d16a7ac583e583687660d7054a2a245dd18f24d10b675
8fe1ed1e34e8758a92c8d024d73c434665a03e94e5eb972c68dd661c5e252469
fa317b071da64e3ee18d82d3a6a216596f2b4bca5f4d3277a091a137d6a21c45



































