
Severe Vulnerability in Palo Alto Networks PAN-OS Exposes Firewalls to Denial of Service (CVE-2024-3393)
[Update] December 31, 2024: CVE-2024-3393 has been added to the CISA KEV catalog*
Palo Alto Networks recently identified a significant vulnerability, CVE-2024-3393, in its PAN-OS software. The flaw affects the DNS Security feature, enabling unauthenticated attackers to send malicious DNS packets, resulting in a Denial of Service (DoS).
Palo Alto Networks has acknowledged reports from customers who have experienced these disruptions when the firewall attempts to block the malicious DNS packets. Alarmingly, repeated attempts to exploit this vulnerability could push the firewall into maintenance mode by rebooting, severely impacting network operations.
What is CVE-2024-3393?
The newly discovered vulnerability, CVE-2024-3393, in PAN-OS has a CVSS 4.0 score of 8.7, signaling its high severity. This vulnerability poses significant risks to organizations as it can be exploited remotely, with no user interaction or elevated privileges required. Attackers can send malicious DNS packets through the firewall’s data plane, causing it to crash and reboot, potentially leading to Denial of Service (DoS).
For exploitation to occur, DNS Security logging must be enabled, which allows the malicious packets to trigger the issue. Palo Alto Networks has confirmed that attackers have successfully exploited this vulnerability, causing DoS disruptions.
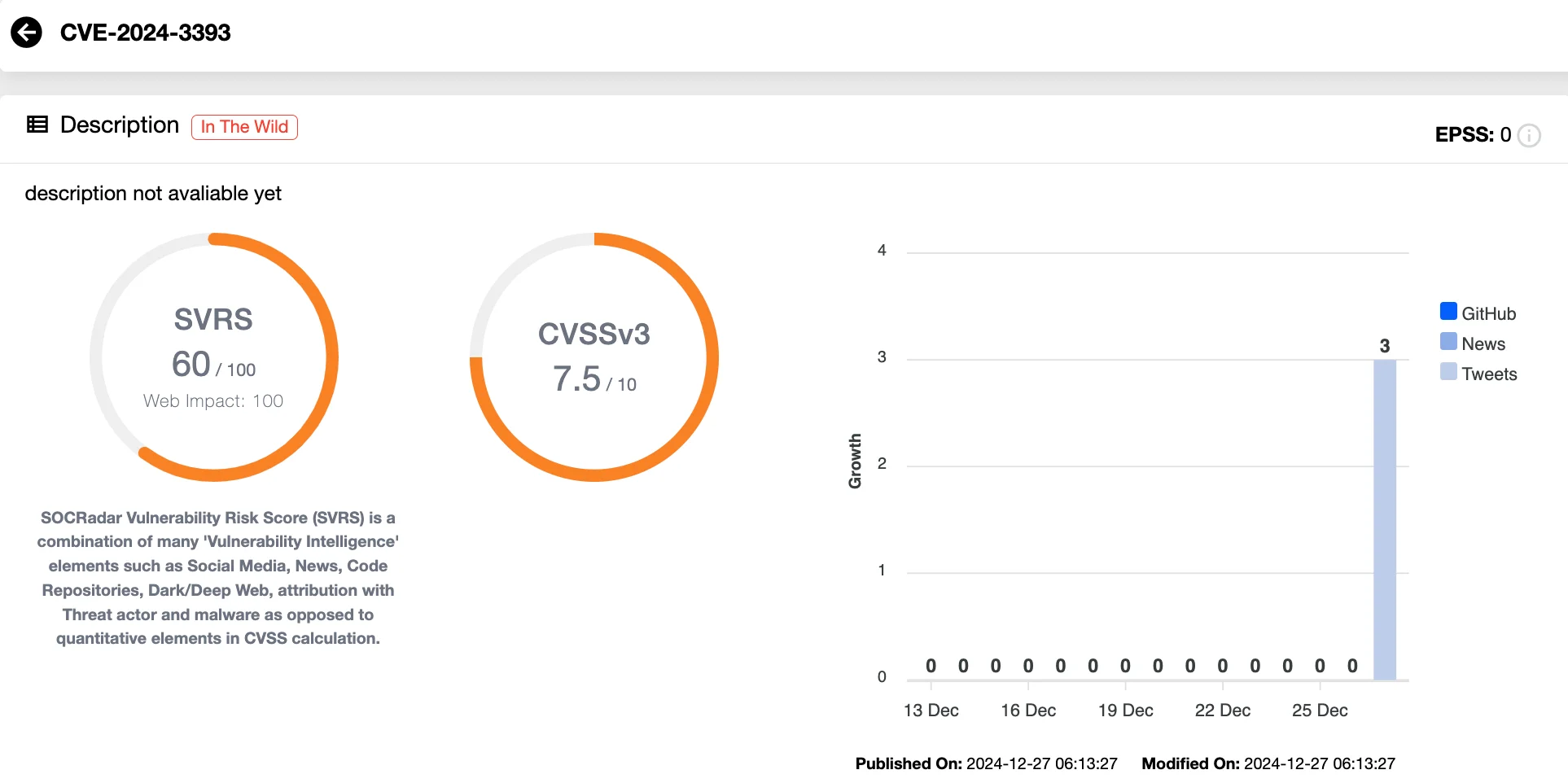
Vulnerability card of CVE-2024-3393 (SOCRadar Vulnerability Intelligence)
To address this issue, Palo Alto Networks recommends applying patches or workarounds immediately. The advisory states a “high severity” and “moderate” urgency for organizations to act.
*CISA recently added the CVE-2024-3393 vulnerability in Palo Alto Networks PAN-OS to the Known Exploited Vulnerabilities (KEV) catalog. This flaw, caused by malformed DNS packets, is currently being exploited by cybercriminals. Organizations are urged to apply patches for CVE-2024-3393 by the compliance deadline of January 20, 2025.
Leveraging real-time threat intelligence, SOCRadar’s Vulnerability Intelligence module provides organizations with up-to-date insights on emerging vulnerabilities, including their exploits. By monitoring and analyzing threats, SOCRadar helps teams prioritize vulnerabilities that matter most, ensuring timely and informed responses to mitigate risks effectively.
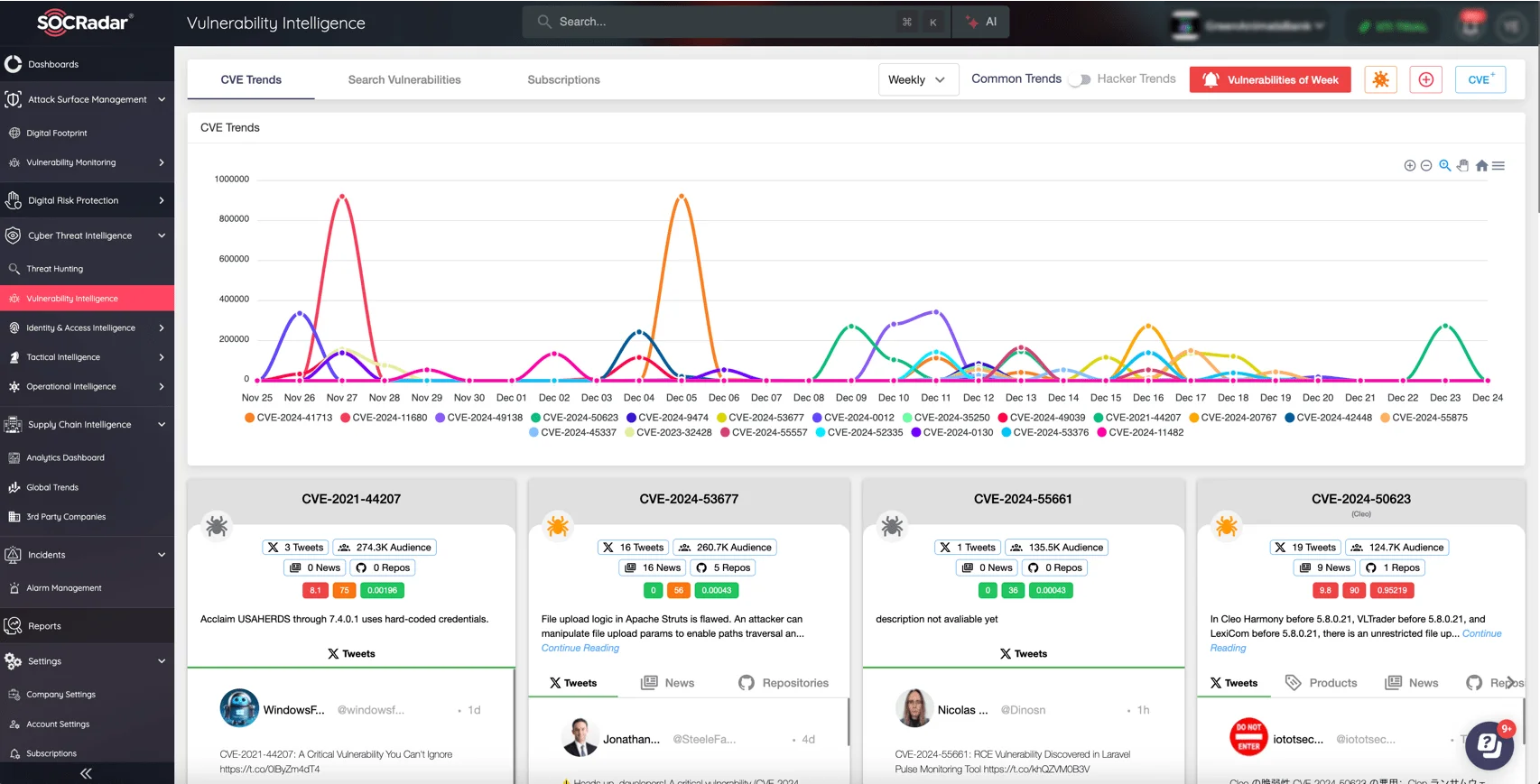
SOCRadar’s Vulnerability Intelligence module page
Key capabilities of the Vulnerability Intelligence module include:
- Continuous Monitoring: Real-time vulnerability alerts.
- Risk Prioritization: Focus on critical vulnerabilities first.
- Actionable Insights: Clear guidance for patching and remediation.
- Extensive Coverage: Access vulnerability details and the latest updates on hacker trends, as well as emerging exploits.
- Seamless Integration: Easily integrates with your existing security tools.
Which PAN-OS Versions Are Affected?
The CVE-2024-3393 vulnerability impacts the following PAN-OS versions:
- 11.2: All versions prior to 11.2.3
- 11.1: All versions prior to 11.1.5
- 10.2: >= 10.2.8 and < 10.2.10-h12, < 10.2.13-h2
- 10.1: >= 10.1.14, < 10.1.14-h8
Customers using Prisma Access with any of the vulnerable PAN-OS versions are also at risk. Organizations must take immediate action to assess their systems and address these vulnerabilities.
How Should Organizations Address This Vulnerability?
To effectively mitigate the risks posed by CVE-2024-3393, Palo Alto Networks has issued critical patches for the affected PAN-OS versions. Customers are strongly encouraged to upgrade their systems to the patched versions listed below to eliminate the vulnerability.
- 10.1.14-h8,
- 10.2.10-h12,
- 11.1.5,
- 11.2.3,
- And all later PAN-OS versions.
In parallel, PAN-OS 11.0 has reached its end of life (EOL) on November 17, 2024, and the vendor has stated that no fixes will be provided for this version.
For detailed guidance on the patching process, refer to the official advisory.
The advisory recommends that Prisma Access customers with affected PAN-OS versions implement one of the available workarounds if they cannot upgrade immediately (Workarounds are outlined in the next section). Palo Alto Networks will roll out upgrades in two phases on January 3 and 10.
Mitigation Steps for Vulnerable PAN-OS Firewalls
If you are unable to apply the patches, and are experiencing unresponsiveness or reboots, Palo Alto Networks recommends the following mitigation steps.
For Unmanaged NGFWs & NGFWs and Prisma Access Managed by Panorama:
- Navigate to Objects → Security Profiles → Anti-spyware.
- Select the relevant profile and go to DNS Policies → DNS Security.
- Set the Log Severity to “none” for all configured DNS Security categories.
- Commit the changes.
Remember to revert the Log Severity settings back to their original configuration once you have implemented the necessary fixes.
For NGFWs Managed by Strata Cloud Manager (SCM):
- Option 1: Disable DNS Security logging directly on each NGFW using the above steps.
- Option 2: Disable DNS Security logging across all NGFWs in your tenant by contacting Palo Alto Networks support.
For Prisma Access Managed by Strata Cloud Manager (SCM):
- Open a support case to disable DNS Security logging across all NGFWs in your tenant.
- Mention the need for expedited upgrades in your support case.
By implementing these mitigations, organizations can minimize disruptions while awaiting the necessary upgrades to secure their networks.
Discover Vulnerabilities Before They Become Threats
In today’s threat landscape, visibility across the entire attack surface is critical for security. SOCRadar’s Attack Surface Management (ASM) module helps you continuously monitor and assess your network’s exposure to potential vulnerabilities. The SOCRadar Attack Surface Management (ASM) module can enable your security team to:
- Proactively identify exposed digital assets,
- Track vulnerabilities and potential threats that might impact your security,
- Gain actionable insights and recommendations for addressing security gaps, ensuring your organization stays secure and resilient.
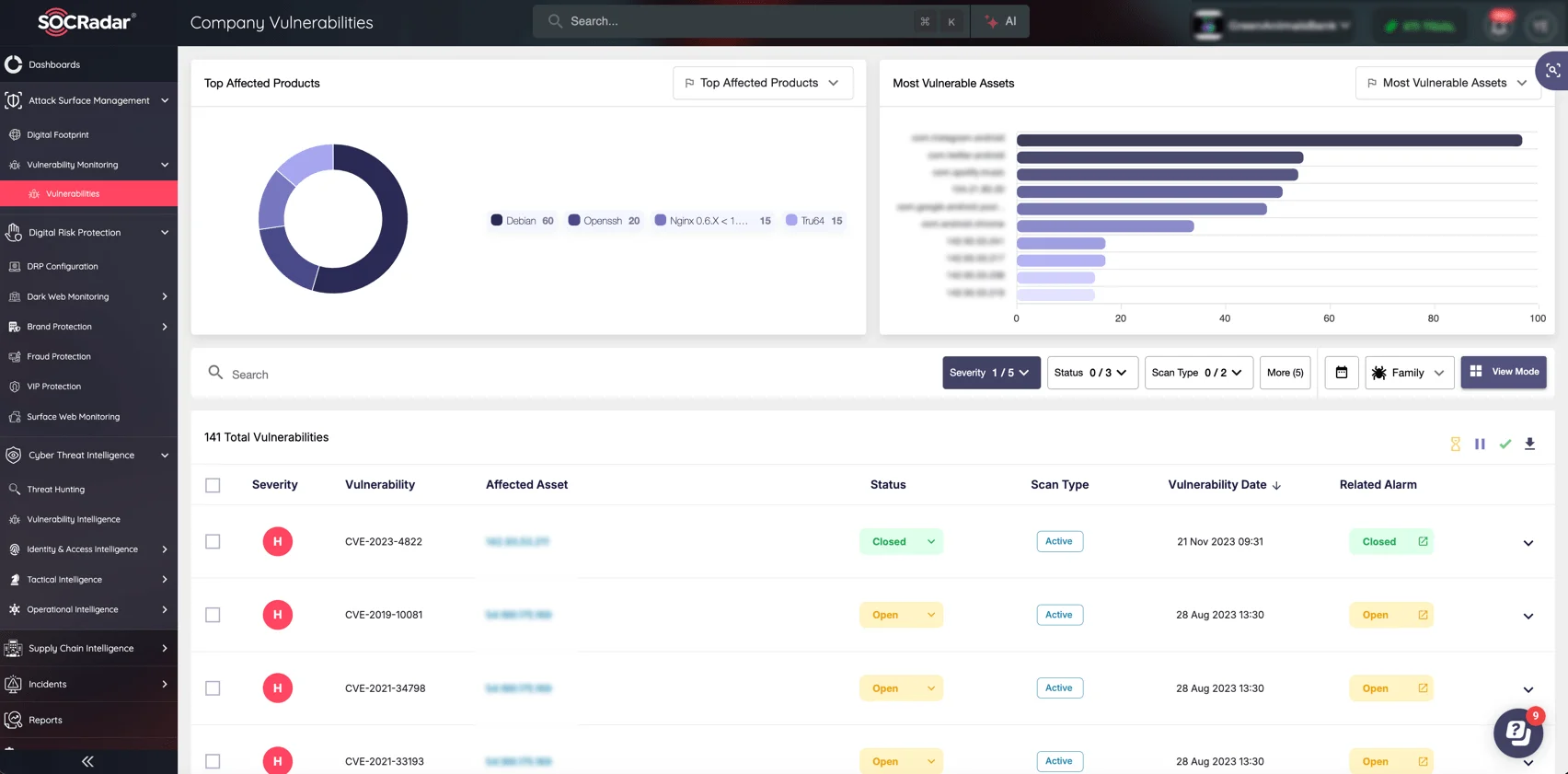
SOCRadar’s ASM module, Company Vulnerabilities page
With SOCRadar ASM, gain better control over your network’s security posture and protect against emerging threats like the one outlined here.



































